On July 6, 2016, the NIS (Network and Information Security) directive went into effect. With only a short time to go until the deadline for transposition (May 9, 2018), discussions about the directive are picking up steam. But what exactly are the directive’s requirements?
The NIS directive: a major piece of legislation
At a national level, the directive requires the establishment of a cybersecurity strategy and the establishment of a CSIRT, along with an authority figure to oversee these matters. For companies, it introduces two new areas of responsibility for two different types of players:
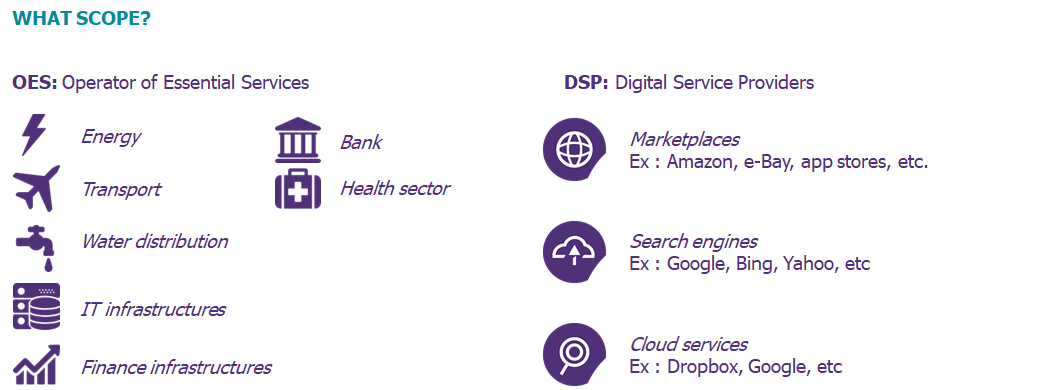
- Operators of Essential Services must implement technical and organizational measures to manage network and information system security risks
- Digital Service Providers are required to notify the appropriate authority of security incidents
The need for a robust and standardized approach
The NIS Directive is the security counterpart to the European Digital Single Market strategy, which was launched in 2015 and aims to turn digital systems into an engine of growth. Business and consumer trust is essential to this project: because without trust, there will be no growth!
European countries are becoming increasingly dependent on digital and information systems while their networks are becoming ever-more interconnected. This interconnectivity is both a strength and a weakness because an information system’s level of security is only as good as its weakest link.
However, there are marked differences when it comes to Member States because to date, cybersecurity issues have been handled at national level.
It is this inherent systemic risk that Europe is seeking to remedy with the NIS Directive, which is the first piece of European legislation to govern cybersecurity practices in a cross-sectoral manner.
The NIS Directive differs from regulations designed to deal with specific issues, such as the GDPR. Though often associated with the NIS Directive, the GDPR does not have the same objectives – its scope is solely about the protection of personal data. Conversely, the directive aims to ensure a base level of cybersecurity through the implementation of security standards and a requirement to give notice when incidents occur (whether they are personal-data related or not). Having said that, a cyber-attack often involves both areas, and it doesn’t make sense to not(?) consider the two pieces of legislation when thinking about compliance.
A transposition process already in motion
As the text is a directive and not a regulation, each Member State has to transpose the directive’s provisions into its own national legislative framework.
Many countries have already announced their first steps:
- The UK has confirmed that it plans to transpose the text, despite Brexit; the levels of penalties provided for in the text, which are particularly heavy, have recently been announced;
- Poland has announced the opening of a new national center dedicated to cybersecurity (NC Cyber);
- Belgium has set out six flagship measures to strengthen cybersecurity: a reaction to WannaCry, a global cyber-attack that paralyzed many businesses in recent months;
- The Czech Republic (Czehia) has amended its cybersecurity laws to take account of more critical sectors and comply with the directive’s requirements;
- Italy has revised its National Plan for Cyber Protection and Digital Security to align with the directive’s provisions;
- Croatia has set up a working group to determine how the directive will be transposed;
- Sweden has already revealed some of the details of its transposition, such as the levels of penalties and the bodies responsible for implementation.
In several respects, the text is very “non-directive” – setting out objectives but not specifying how they should be achieved. It will be up to each country to work out its own interpretation and draw up the concrete measures that will meet the objectives.
The challenge, therefore, is to reduce the degree of difference between European countries, while standardizing the levels of cybersecurity to a greater extent by avoiding large differences so that players operating in several countries don’t face undue complexity..
To achieve this goal, collaboration is taking place at the EU level:
- A review of the remit of ENISA (the European agency in charge of network and information security) is being considered with the aim of, among other things, giving it the powers needed to carry out directive-related activities.
- A Cooperation Group made up of national representatives, ENISA, and the European Commission, will provide strategic direction;
- A network of CSIRTs will also be active and able to ensure that good practice is communicated and exchanged, as well as supporting Member States on directive-related matters.
How should you prepare for the directive coming into effect ?
Or, more specifically, how can you prepare for this new legislation now and what plan of action will you need to have in place? In practice, that depends on the type of entity in view (an OES or DSP).
For Digital Service Providers (DSPs), a standardized approach is needed: Member States cannot impose additional security or notification requirements and, therefore, for this type of player the directive is closer to an EU regulation. This particular treatment, compared with OESs, arises from the cross-border nature of their activities and the fact that many are foreign companies without bases in Europe. DSPs will have to appoint an entity which is based in a member state to be their official representative on NIS-related issues (as required by Article 18 of the directive). Thus, it is essential that each Member State has the same requirements, ensuring that future decisions to enter an EU country are not influenced by uneven interpretation of these criteria.
The obligations for DSPs are somewhat less onerous. For example, they are obliged to notify regulator about an incident only in cases where they have access to the information needed to assess its impact against the criteria defined in the directive (Article 16).
It is already time for DSPs to begin the process of compliance since the implementing acts were published In August of 2016.
For the Operators of Essential Services (OESs) in France, there are two main scenarios.
First, let’s consider the operators already identified as VIOs—Vitally Important Operators—under the French Military Programming Act. For them, the issue of compliance is less significant given that the Act already introduces numerous obligations. The directive probably will not impose more onerous requirements. Some elements such as reporting may be adapted, but there are no major changes in sight.
However, the scope of the directive is likely to be wider than that of the Act, and some operators within the critical sectors defined by each state under the directive will need to begin complying. Member States have until November 2018 to designate operators as “OESs” based on the criteria defined in the text. This list will then be reviewed by the European Commission in May 2019.
Those involved will then have to ensure that they monitor legislation in order to follow developments in the transposition process, which is important because Member States have the power to impose measures that go beyond the common, base-level requirements set out in the directive.
Much of the development of the directive’s provisions must now be carried out by Member States: the specification of the security measures to be put in place, the definition of notification procedures, the penalties to be applied—not to mention the designation of critical sectors and OESs in each country.
The upshot of all this is a genuine renewal of the European cybersecurity legislative landscape, with the primary aim of increasing standardization of IS security levels between Member States—a process that will prove interesting to follow.


