The development of connected cars – and eventually autonomous cars – requires the presence of more and more software-driven electronic components in vehicles, as well as new interfaces allowing them to be connected to other devices and infrastructures. In a way, modern vehicles are becoming real computers on wheels.
Therefore, vehicles attack surface is becoming ever wider. They are then exposed to more and more risks which can jeopardize passengers’ safety but also the safety of people around vehicles under attack. Indeed, several researchers have already managed to perform different attacks on recent vehicles, and sometimes shown how to take full control of them.
What kinds of cyberattacks have been performed so far? What are the possible attack vectors? What could be the motives behind such cyberattacks?
A wide range of cyberattacks already performed on connected and autonomous cars…
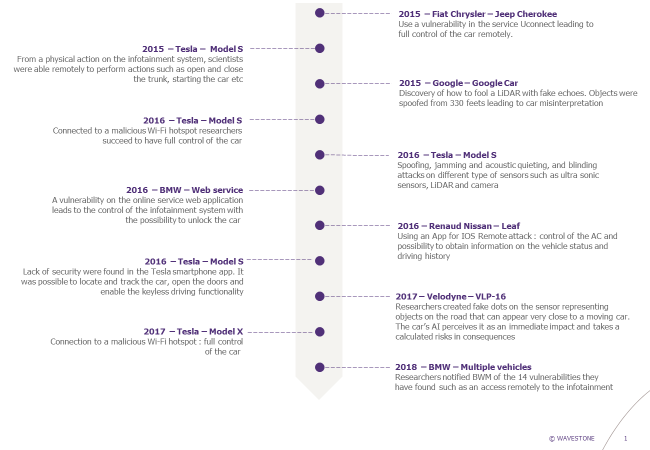
Over the last few years, several vulnerabilities have been discovered by researchers on connected vehicles. In particular two events gave rise to an important media response in 2015, bringing the topic to the forefront.
The first one was performed by American researchers Charlie Miller and Chris Valasek, who managed to remotely hack a Fiat Chrysler car and take control of many functionalities, from radio volume tuning to brakes activation. Their entry point was the Internet-connected feature Uconnect that was used in the car to control the vehicle’s entertainment and navigation system, enable phone calls and offer a Wi-Fi hot spot. By attacking this feature, they managed to reach an adjacent chip in the hardware used for the car’s entertainment system, and silently rewrite the chip’s firmware to plant their code. With this rewritten firmware, they were then able to send commands through the car’s internal network, known as CAN bus, to its physical components like the engine and wheels. Once this attack was presented by the researchers, Fiat Chrysler had to patch 1.4 million vehicles by sending USB sticks to all concerned customers so that they can manually fix the vulnerability in their vehicles.
© ANDY GREENBERG/WIRED
Apart from cyberattacks that were made possible thanks to initial physical access or remote connection, others were also performed on sensors used in some cars to detect their surroundings. For instance, in 2016, Chinese researchers showed how to attack the Tesla Model S through its different sensors: Millimeter Wave Radars (MMW Radars), LiDAR, cameras, ultrasonic sensors, etc. They presented different kinds of attacks such as:
- Jamming attack on MMW Radars: use of a transmitter tuned to the same frequency as the car’s receiving equipment, and with the same type of modulation, to override any signal at the car’s receiver. Thus, no signal is received by the car, meaning that if the sensor is used to detect obstacles for example, these ones can no longer be detected during the attack (“obstacle evaporation”).
- Spoofing attack on ultrasonic sensors: use of a transmitter to create at a specific timing ultrasonic pulses with similar pattern as the ones of the car’s ultrasonic sensors to change the time of propagation. Thus, the distance between the car and the objects around it that is calculated by the sensors is no longer the real one during the attack.
- Blinding attack on cameras: use of an LED spot or lasers to blind, or even cause permanent damage on cameras (permanent dead pixels).
To sum up, researchers all around the world already managed to perform various cyberattacks on modern vehicles from different manufacturers, some of which are listed on the timeline below:
 6 main vectors to attack connected and autonomous vehicles…
6 main vectors to attack connected and autonomous vehicles…
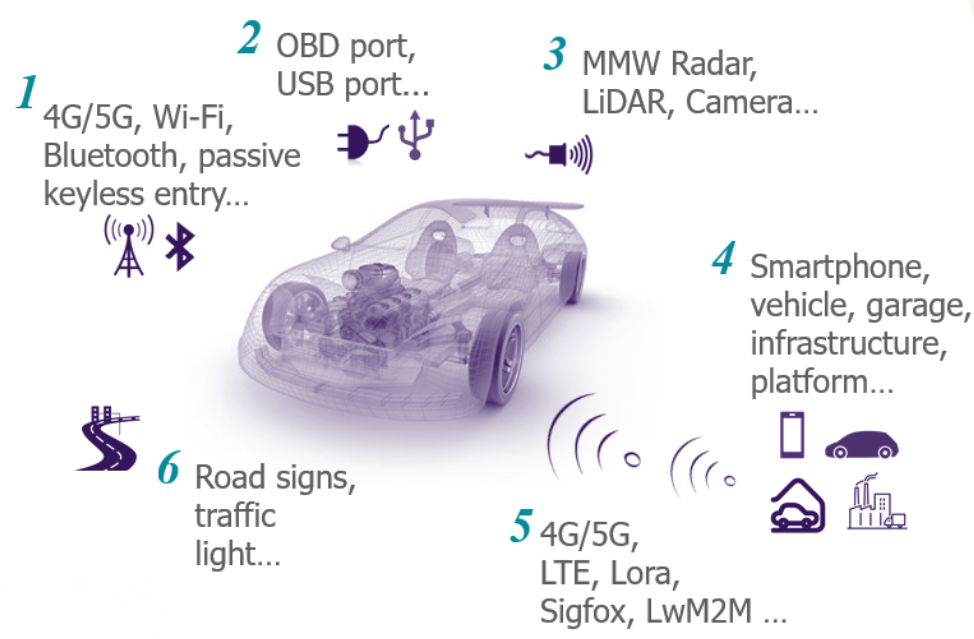
Today’s vehicles can connect to 3G/4G networks and can provide Wi-Fi and Bluetooth access. These technologies are standard and present vulnerabilities: many different types of attacks on these networks are well known. One can easily imagine an opponent penetrating remotely the local network of the vehicle using these canals or performing a “Man-In-The-Middle” attack, in order to steal personal data, to alter some services or even to take control of the commands as shown previously.
In addition, it is possible to directly connect to the vehicle. All cars have ODB port for diagnostic purposes and most of the modern infotainment systems offer a USB port. It represents an open door for attackers to conduct malicious actions with serious consequences: blocking part or all the systems due to a ransomware, malicious frames sent to the CAN bus, alteration of ECUs due to malwares, etc.
With the advent of extended and autonomous vehicles, new types of attacks must also be considered. The automated drive relies on many kinds of sensors that are continuously interacting with the environment to collect information about roads, traffic, etc. Attacks affecting these sensors may have dramatic impacts and malicious people can deflect the primary functions of either the sensors or the road infrastructures to cause an accident. In the past, a fatal accident has occurred, showing that sensors are vulnerable and be a source of misinterpretationOne can say with certainty that the implementation of artificial intelligence within vehicles will result in more and more targeting this vulnerable part.
Finally, the vehicle is becoming a central point of connection with the internet of things. Services will be delivered from smartphones and external devices that will become new vectors to conduct an attack. For instance, authentication may fail or be compromised on the smartphone and can give an unlimited access to services on vehicles, allowing doors unlocking for instance.
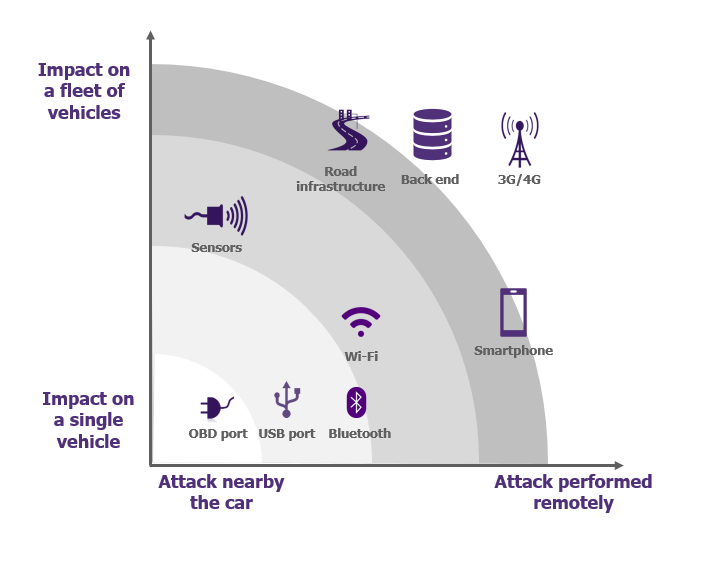
According to the attack vector, attacks may be categorized and:
- Could affect a single vehicle or a whole fleet, which will increase the level of impact
- Must be conducted close to the vehicle or can be realized remotely, which will change opponents’ capabilities and will contribute to increase the complexity of the attack because of the physical presence required or not.
Sensors, IoT, public or private network, the extended vehicle is a concentrate of technologies. It represents a large playground for attacker ready to act! But why a person would attack a vehicle?
What would be the motives behind such cyberattacks?
Motivations for the attackers could be diverse and varied. We have spotted 5 major categories:
- The first one is ideology: In the automotive context, several organization might intend to attack the vehicle. It could be an environmental group that wants to disclose a specific message (about air pollution for example), to cause a service outage, etc.
- It could be simply financial: Some attacks could be very basic: to hack the infotainment system to gain access free of charge to musical streaming services for example.
- Then, a third motivation could be destabilization: A state may want to destabilize another state by attacking a fleet of vehicle; a competitor may try to spoil the brand image of a car manufacturer, etc.
- It could be also killing: The possibilities to take full control of the vehicle and to cause accidents with likely human fatalities could attract criminals or terrorists. It will have a dramatic impact on populations. In a near future, a fleet of vehicles could become a massive state weapon.
- Then, the last one is attack capabilities procurement: Vehicles will become sophisticated systems with a great potential of computation. If a person finds a vulnerability, cars could become a way to spy citizens. Their performances could be also used for brute force attacks. They could be also turned into botnets to realize DDOS attacks.
Current vehicles already offer many ways to connect with external systems which could present vulnerabilities: Bluetooth, Wi-Fi, USB, etc. With the development of autonomous cars, services platforms and connected road infrastructures, the attack surface is going to increase more and more, and impacts will become very serious. Therefore, car hacking will also appeal to many opponents.
It becomes urgent to adopt a granularity approach to secure vehicle vital functions and to guarantee the safety of passengers. Measures and organization are inspired from IT world, but they need to be adapted to the automotive context. For this purpose, start-ups can bring some answers to technical challenges and norms, such as the ISO21434 currently in development, intend to provide a worldwide framework to increase the resilience of connected vehicles. But what are concretely the solutions and how to protect vehicles from cyberattacks? Don’t put the car(t) before the horse, stay tuned, we will soon have a look on it!



