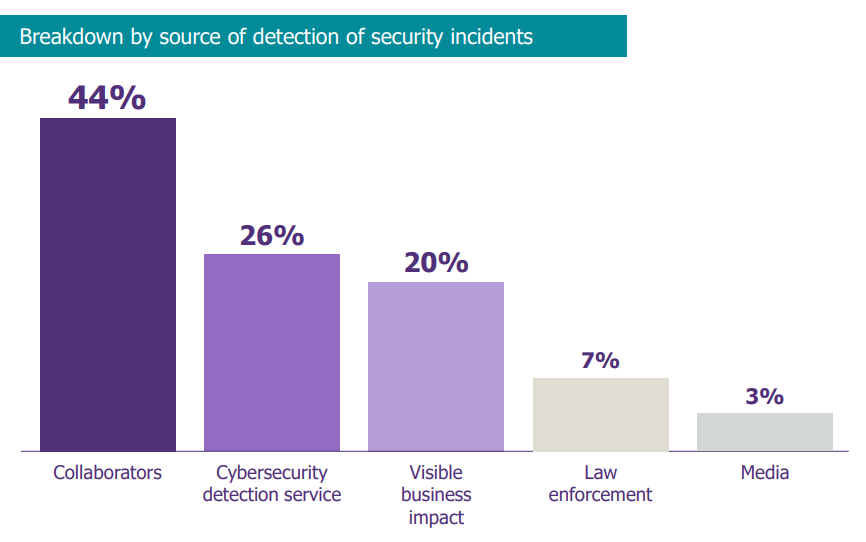
Out of the 40 major incidents managed by CERT-Wavestone last year, only 26% of security incidents were identified by the organisation’s cyber detection team (the SOC in most cases). It is therefore quite logical that the ANSSI mentioned a collective weakness in detection at the last French major security conference “les Assises de la Sécurité”.
But how to strengthen the detection of an intrusion into one’s company? Penetration testing allows us to evaluate the level of protection/hardening on a precise and supervised perimeter, which does not necessarily represent the reality experienced during a real situation. Crisis management simulations help to improve the response… Red Team operations can be a good element of response, allowing the information system and detection capabilities to be evaluated (and therefore improved) from the beginning to the end of a cyberattack.
What is a Red Team operation? It is simply a realistic attack without the negative effects. The objective is to determine, today, what malicious actions a group of attackers can carry out on my company and when am I able to detect them?
In this article, we will see what the key steps are in such an operation and how to ensure that we reap the benefits.
STEP 1: DEFINE THE CORE TEAM AND IDENTIFY THE TROPHY
Defining a restricted control team is essential to limit the leakage of information to the Blue Team (detection team, i.e. SOC), to make communications more fluid and to facilitate decision-making by the client. The control team must therefore be clearly separated from the Blue Team. Often the choice is made between the CISO or a representative of the ExCom, with whom the limits of the perimeter and the operating mode (as wide as possible) will have to be set, in order to avoid any unfortunate incident!
“That’s out of scope” – Said no attacker ever
Then, a particularity of a Red Team operation is to define a “trophy”, the final target of the operation. Indeed, an attacker is often motivated by an objective (gain, destruction, data theft, …) and it is advisable to copy the Red Team’s objectives on it. The Red Team generally already has some good ideas but the best trophies (i.e. the strongest impact during the restitution) are closely linked to the business stakes of the company and its current events.
The target must be the scenarios that are the most chilling for the managers: a remote takeover of the SWIFT infrastructure? A compromise of the payment terminals? The leakage of the VIP customer list? Positions taken in recent months abroad? The ideas may be numerous, but it is necessary to restrict oneself to one or two targets to keep the most critical ones visible. It will always be possible to identify another trophy for the next operation: it is even advisable to modify the trophies from one year to the next in order to test different parts of the information system.
During our latest operations, ExComs have chosen scenarios that have already taken place during real cyber attacks they have been subjected to. This also enables them to assess the effectiveness of the new security measures implemented.
STEP 2: PREPARE AND LAUNCH THE ASSAULT BY MIXING EFFICIENCY AND STEALTH
The credibility of the attack is one of the key factors in the success of the operation, particularly during the restitution phase. Once the trophy has been arrested: we build an approach based on the techniques used by the attacking groups.
It is at this point that field returns are particularly useful! At Wavestone, we rely heavily on our Incident Response Team (CERT-W) and its Threat Intelligence capacity to identify the latest trends, on the technical know-how of our audit team and the creativity of our CTF (Capture The Flag) team.
Thus, the Red Team will use all possible and necessary means to penetrate the IS (phishing campaign, telephone phishing, physical intrusion, compromise of components exposed on the internet…) and then bounce back to the trophy. This phase is the most creative and exciting for the listeners (as well as for the attackers), and can potentially last several weeks, just like the most high-profile cyber-attacks.
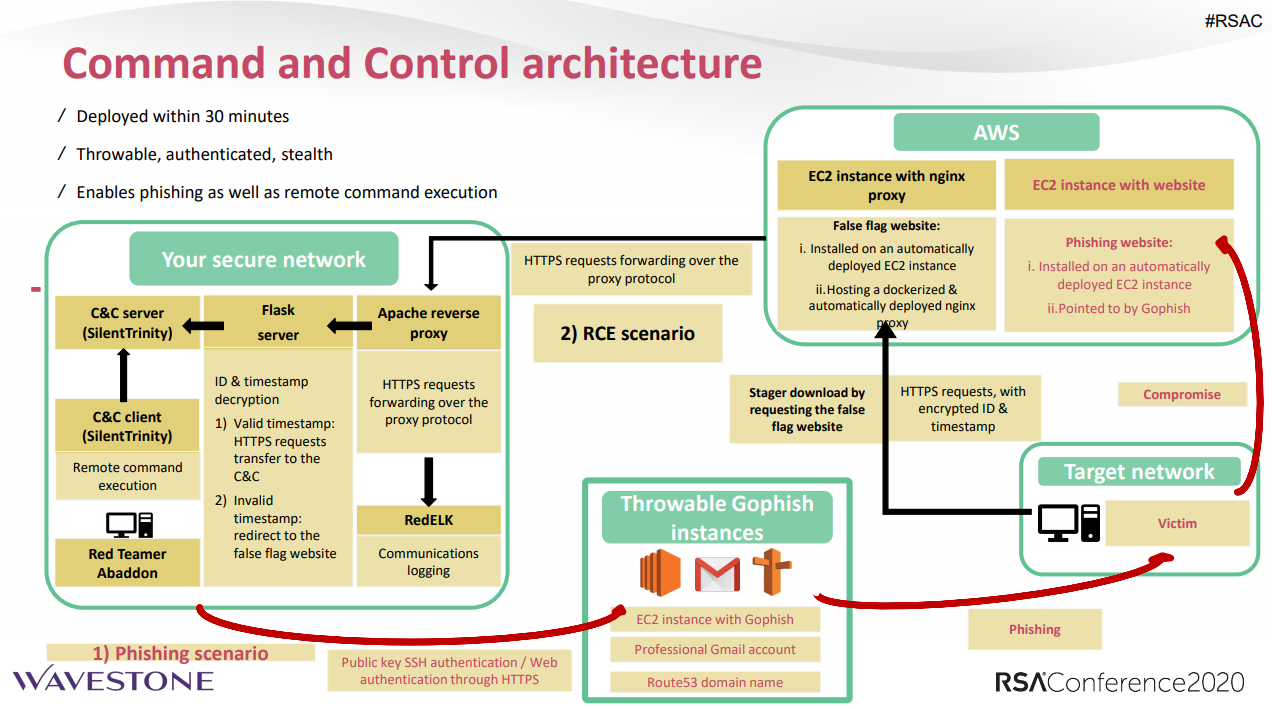
However, the key word must remain: “stealth”! Indeed, the slightest detection by the Blue Team can totally derail or set back the operation. Particular attention must be paid to customised attack tools and infrastructures to avoid panicking the detection systems. For the first point, we have developed internally the Abaddon tool, now open-source, which allows us to build and deploy the necessary infrastructures in just a few clicks.
Two questions always come up when it comes to the conduct of a Red Team operation.
The first one is “What to do in case of detection? ». That an action may be detected can happen during a Red Team operation: a good SIEM correlation rule, an informed user who shares an abnormal behaviour, etc… First of all, in the basic organisation, the control team must supervise incidents within the SOC in order to avoid an “over-escalation” in crisis of an incident related to the Red Team. The control unit will then be able to request a report from the Blue Team (summary, detected behaviour, timeline of actions, remedial actions, etc.) and then define the recovery scenario with the Red Team: ignore the detection because it is too old, start from the penultimate compromised asset that has not been detected, etc. Moreover, the work will become more complicated for the Red Team, which will have to completely change its C2 infrastructure and henceforth succeed in deceiving a Blue Team on alert.
The second “If the trophy(s) are obtained very quickly, what can be done?” Let’s imagine the worst case scenario: the application administrator of the trophy gets trapped by a phishing email and allows us to take complete control of the application from the very beginning of the operation (Anyone can make a mistake). The point will be shared with the control team and the procedure to be followed will be defined jointly: add trophies to test the robustness of another perimeter, start from scratch and identify another compromise path, … This somewhat caricatural example is there to remind us that the objective of a Red Team operation is to durably improve the level of security via Blue Team training and not just to obtain a trophy.
STEP 3: PROVIDE A CLEAR RESPONSE TO A CRITICAL BUSINESS RISK
The objective remains to provide sponsors with a clear vision of the real security status of their IS, the attack scenarios that will give them access to their critical resources (identified as “trophies” of the operation), as well as their detection capabilities. Quite simply, the Red Team operation must make it possible to answer the question “Is the trophy accessible and with what level of expertise? ». However, it should be remembered that Operation Red Team will highlight an exploitable path that may not be the only or the simplest one.
From then on, we return to the stakeholders (CISO, SOC, COMEX…) with a high-level synthesis in order to present the conclusions of the Red Team operation, the attack scenario followed and the most priority worksites. The results are generally compared with typical attacker profiles (Maze, REvil/Sodinoki…) on the MITRE ATT&CK reference frame to be more meaningful.
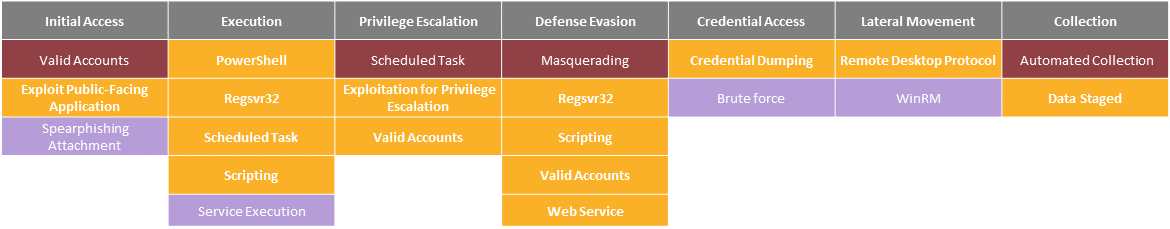
In a second stage, the Blue Team will obviously have to be given a detailed account of the technical stages of the operation, with a view to defining areas of progress on detection.
“If we win, we lose ” Said a good red teamer
This second phase is fundamental for the operation to have the expected added value: pedagogy and clarity are needed to get the right messages across! Let’s not hesitate to hold additional workshops to explain the problems raised by the operation and to find solutions together. A joint interpretation of the findings by the Blue Team and the Red Team allows us to take a step back from the vulnerabilities and identify concrete actions for improvement.
The Red Team operation should not be reduced to correcting a few vulnerabilities on the IS, but should make it possible to obtain the effective level of security (even if it is not exhaustive, as a Red Team will never be an audit).
In a few words, a Red Team operation makes it possible to test its defence strategy on a large scale and to train (improve) its defence team. The very concrete nature of the trophies allows an understanding and awareness of the cyber risk of the decision-makers.


