
DECRYPTION
CYBER CRIMINAL NETWORK DISMANTELING
The last 6 months, large-scale coordinated international actions have dismantled several of the biggest cybercriminal networks such as Emotet, Netwalker, Egregor or even Cl0p. Let’s have a closer look at some of them.
What is Emotet?
Emotet was originally a banking trojan, stealing emails and contact list, retrieving passwords on navigators and systems, spreading within the infected network. In 2019, Emotet lost its banking module and became a dropper of malwares. The trojan used a botnet of 1.6 million machines to realize phishing campaign and install itself on victims’ machines.
Why is Emotet called the “king of malware”?
At the end of 2020, Emotet was identified as one of the most dangerous malwares. Additionally, being a dropper as well as a botnet, Emotet also served as a front door to many other malwares. It was used to drop malicious payloads directly onto the victims’ assets: for example, TrickBot was dropped onto the targeted machine which in turn, would drop Ryuk or Conti ransomware. According to Checkpoint Research, Emotet was at the top of the Global Threat Index in October 2020 and was linked to a wave of ransomware attacks. According to CISA, the U.S. Cybersecurity & Infrastructure Security Agency, Emotet infections cost is estimated at $1 million per incident.
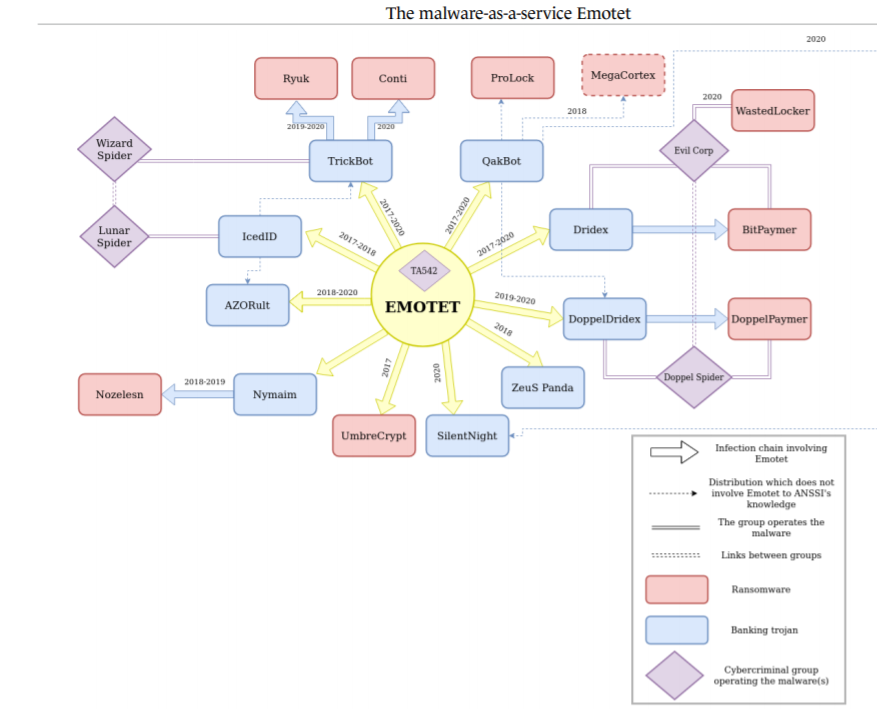
Main TA542’s customer base, “The Malware As a Service EMOTET”, ANSSI 2021
During several months, Europol used the help of Eurojust, France, Germany, United States of America and announced their successful dismantle of the Emotet network in January 2021.
Does this dismantling mean the end of the malware?
The end of one botnet actually led to the rise of several others, such as TrickBot, which even though existed since 2016, replaced Emotet as one of the most well-established MaaS (Malware as a Service) not long after the events on January.
This turn of events might not be so surprising, as threat actors often pivot and change their tools along the way, whether by choice or by necessity as it was the case here. Taking one malware down would only force them to use another one. Yet, what is interesting is that TrickBot also suffered a dismantlement of its own, back in October 2020. In an attempt to disrupt one of the most used distributors of ransomware, Microsoft joined forces with other security teams to take down TrickBot servers. As you may have noticed, this was months before law-enforcement took down Emotet, and now TrickBot or other versions of this malware, still lives on. These actions only disrupted TrickBot activities for a few days, before going back to what it was and even overtaking Emotet dominance.
Moreover, TrickBot seems to be somehow connected to the Bazar malware (BazarLoader and BazarBackdoor), as some part of its infrastructure is shared with TrickBot and both show code similarities. This new toolset is now the most seen malware used to deploy Ryuk ransomware instead of the previous Emotet-TrickBot-Ryuk or TrickBot-Ryuk chain of infection. These changes might have to do with the previously mentioned dismantlements, or due to a new collaboration between threat actors.
What about the people behind these groups?
More recently, on June 4th, Alla Witte was charged on multiple counts for participating in TrickBot criminal activities. Is this arrest, serving as a warning with several hundreds of years of prison if convicted, going to change cybercriminals’ operations? A few months before that, the Ukrainian authorities cooperated with the French law enforcement to conduct an arrest against Egregor members, while a Canadian tied to Netwalker ransomware was charged by the police for distributing the malware. Last year was also marked by several other arrests of cybercriminals around the world. For instance, the arrest of members of the Infinity Black website selling user credentials, lead to the end of the website and the group altogether. On the other hand, the arrests mentioned regarding Netwalker and Egregor seem to concern ransomware affiliates. And as the operators are still free and collaborate with other affiliates, their ransomware continues being deployed around the world. Alla Witte’s case is different since she is suspected to be a malware developer for the TrickBot Group. While her possible conviction might slightly disrupt TrickBot, it seems like their operations still go on, as according to the any.run website and its malware trend tracker, the trojan was last seen on June 16th, 2021. Last but not least, some mid-tier members of the Cl0p gang may have been arrested mid-June in Ukraine even though it seems no core actor behind Cl0p were apprehended.
What could be the long-term consequences of these takedown for the cybercriminal activities?
It’s still early to draw meaningful conclusions on the consequences for cybercriminal activities with the recent arrests. Yesterday, June 16th, at the Geneva summit, U.S. President Joe Biden met with Russian President Vladimir Putin. One of the hot topics of discussions was the ransomware attacks on U.S. entities from Russian soil. Biden warned Putin that United States would not tolerate any other cyber-attacks, especially on 16 critical sectors. The G7 and the NATO also stated that in order not to consider cyber-attacks as armed attacks, Russia should try to identify and disrupt ransomware organizations within its borders.
Even with the arrests of criminal gang members and cybersecurity talks at the presidential levels, some experts say there would be no or little impact on ransomware groups that will still operate with impunity. The near future will give hints about the possible evolution of the cyber-attacks landscape. On one hand, the rising of a broader international collaboration against cyber-criminal gangs which could lead to less opportunistic and lucrative attacks. On the other hand, growing tensions between two blocks: U.S.-Europe and Russia-China with possible sanctions from either side and more cyber espionage, supply-chain or state-sponsored attacks.
CERT-W: FROM THE FRONT LINE
The First Responder Word
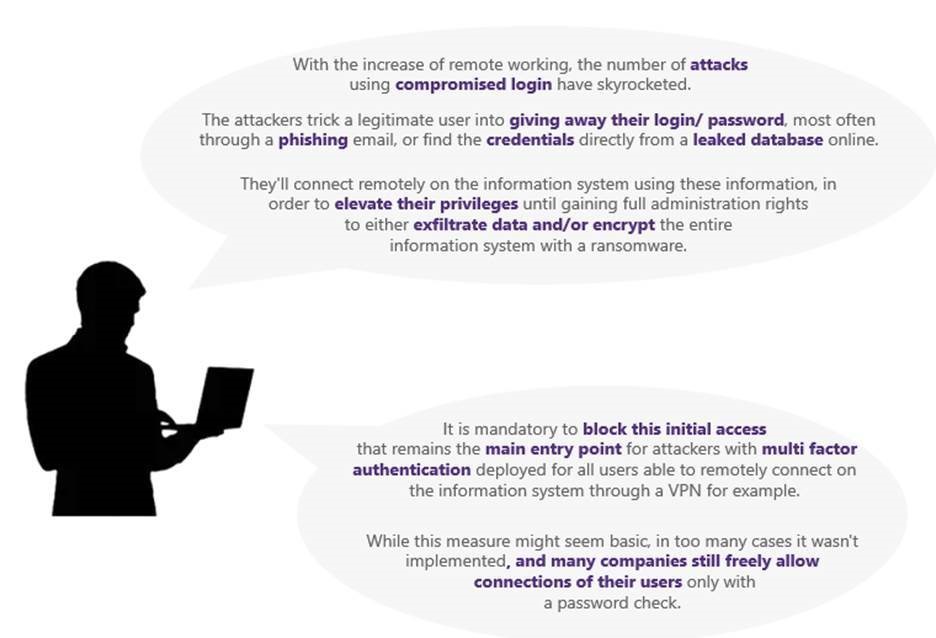
FOCUS TECH
Phishing
Think like a cybercriminal and understand how a spear phishing campaign is built to avoid them!
The technical zoom of the month:
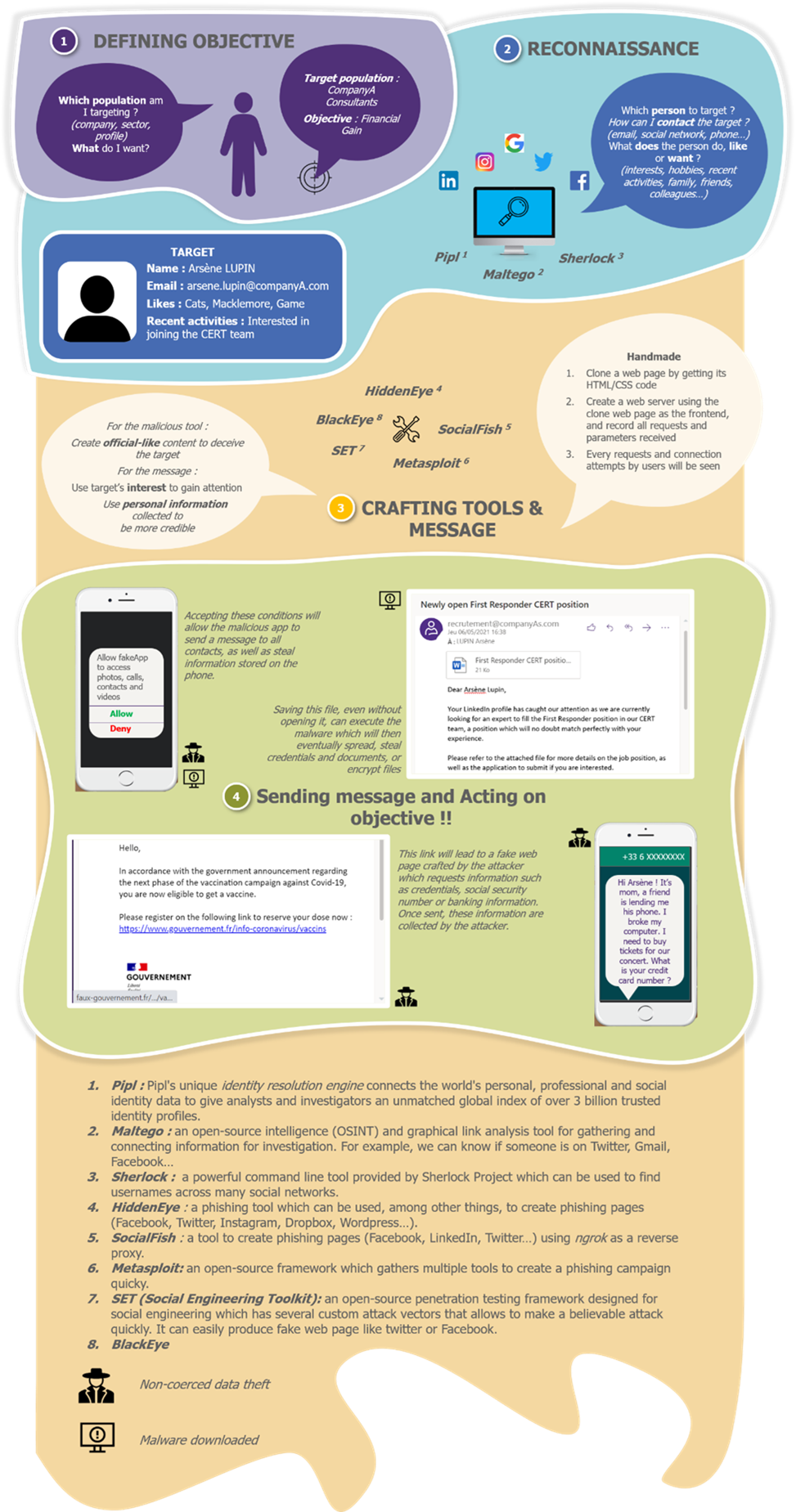
To learn more about this:

Reading Of The Month
We recommend the short report “APT trends report Q1 2021”, which reviews the highlight events and findings observed by the Global Research and Analysis Team at Kaspersky during the Q1 2021 around the world.



