Quantum computing threatens today’s asymmetric cryptography and would render current algorithms obsolete, both RSA and ECC. As for symmetric cryptography, (AES, hash functions) doubling the key size ensures maintained security guarantees. To address the threat, the NIST has standardized three post-quantum (resistant to quantum computers) asymmetric algorithms in August 2024.
Fortunately, quantum computers are not performant enough yet to conduct such attacks. Estimates vary as to when this will be a reality, though most expect it between 2033 and 2037. Furthermore, regulators have begun outlining end-of-life timelines for existing algorithms, with Australia’s ASD planning to designate them as obsolete by 2030 and the NIST drafting its own retirement schedule for 2035. We expect such announcements to pick up during the coming months from other nations.
As such, regardless of the exact date of emergence of quantum computers capable of breaking current cryptographic algorithms, a transition will be obligatory from a regulation standpoint.
Migrating a complicated IT infrastructure is no trivial feat: in a 2022 memorandum, the Biden administration expected the migration of all U.S. Federal Agencies to cost more than $7 billion. Such a complex endeavor entails a plethora of aspects from assessing risks, to executing the technical migration, with many intermediary steps. Solutions exist to accompany or accelerate those stages.
Wavestone’s 2025 Post-Quantum Migration Migrations radar offers a first visual panorama of market leading cybersecurity solutions for this migration. This radar has been and will continue to be updated in the coming months. Any company that feels it should be part of the radar is encouraged to reach out.
The goal of the radar is not to inventory solutions that completed their PQC migration, but rather solutions that help and accelerate the PQC migration.
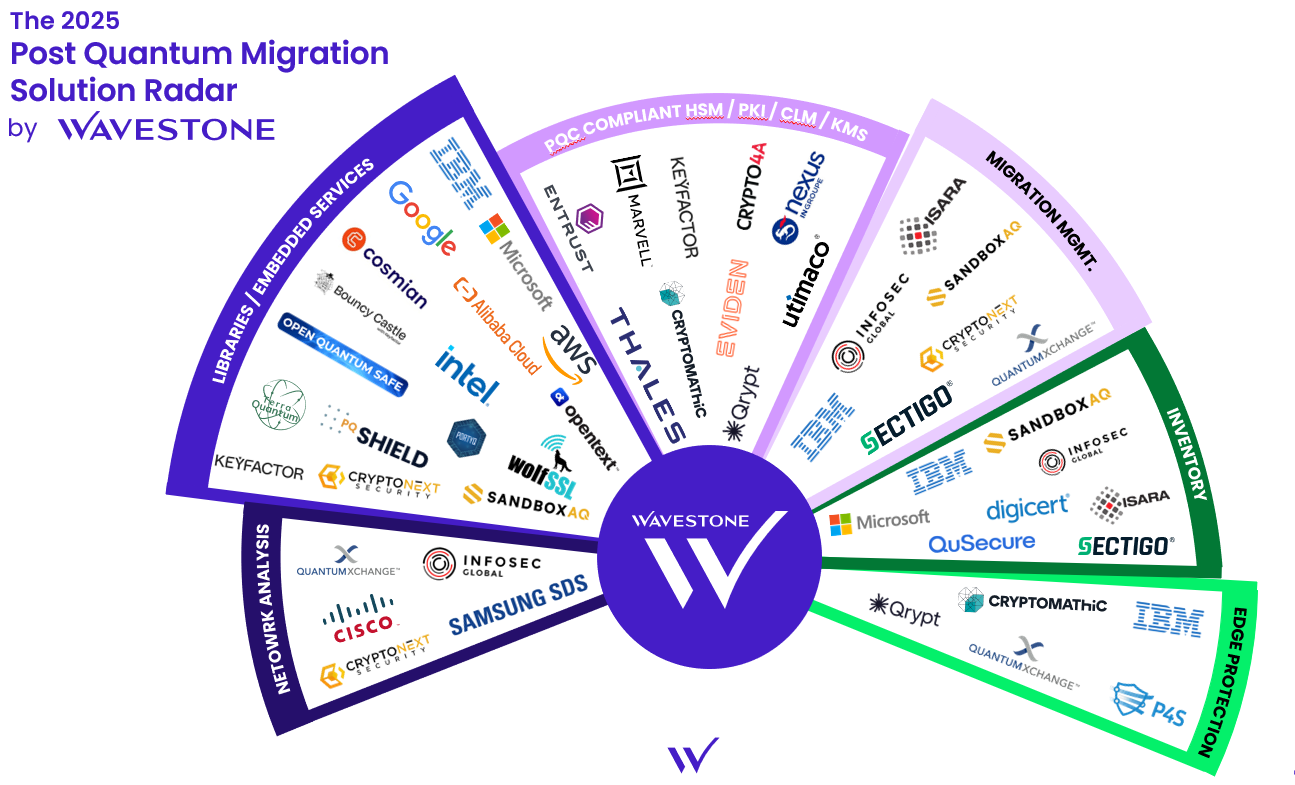
Categories
- Inventory: Automatically inventory the type and locations of all cryptography in use
- Migration Management: Provide the big picture view of the post quantum transition, often based on inventory outputs
- PQC Compliant HSM / PKI /CLM: Provide quantum resistant core trust components necessary for most company services
- Libraries / Embedded Services: Encrypt and sign data with polyvalent libraries or directly integrated cloud solutions
- Edge Protection: Protect against quantum computing attack by providing an extra layer of security, be it at network or application level
- Network Analysis: Detect network flows which use obsolete cryptography with probes
Key Market Trends
Size disparities
The market landscape for post-quantum security solutions exhibits significant disparities in the size and maturity of players. On one end of the spectrum, tech giants and established cybersecurity firms leverage extensive resources to develop and promote robust solutions. On the other end, niche start-ups and pure players are driving rapid advancements in specialized areas. We expect this diversity to foster:
- Innovation: Diversity in the market landscape, with contributions from both tech giants and pure players which enhances the pace and quality of innovation.
- Fragmentation: smaller players may struggle to achieve the scale required to implement their solutions broadly
- Partnerships: we are already witnessing how Thales and IBM are leveraging innovation in specific areas of pure players with their own resources and expertise.
As the market matures, it will be exciting to follow how its landscape evolves.
Several open-source libraries… with Big Tech support
Already, several open-source libraries propose post-quantum cryptograph. The most high-profile libraries, such as OpenSSL, are not the most advanced on this, with their own implementations currently ongoing, while Open Quantum Safe’s liboq is already ready. Nevertheless, it is a promising sight for the cybersecurity ecosystem that a topic as crucial as post-quantum security has solutions deeply rooted in open-source principles.
Yet, Big Tech companies play a pivotal role in supporting open-source libraries for post-quantum cryptography, recognizing their potential to accelerate adoption and innovation. Initiatives like Open Quantum Safe’s liboq has supporters that include Microsoft, Amazon and IBM; Bouncy Castle’s PQC was developed with Keyfactor’s sizeable participation, and Tink, Google’s open-source library offer PQC as well. However, most of the implementation has not been fully formally verified, though the process is underway.
A lack of certification for HSMs…
Hardware Security Modules (HSMs) play a crucial role in the digital trust chain, but the market for these hardware solutions is not yet ready. Initially, providers resorted to software implementations for experimental purposes while waiting for the new standard to be published by NIST. However, hardware implementations have advanced since then, even though their certification is not expected until Q3 or Q4 2025.
Furthermore, although HSMs are designed to resist tampering and reduce the risks of key exposure, they will have to face challenges related to side-channel attacks due to the still limited maturity of current implementations of these new algorithms.
And a lack of hardware for IoT, embedded devices, and smart cards
The lack of hardware is particularly problematic for connected objects (IoT), embedded devices, and smart cards, which operate under severe constraints – limited power, reduced computing capacity, and restricted storage space – thus requiring efficient algorithms and specialized dedicated hardware for cryptographic operations. Unfortunately, the current absence of dedicated processors remains a major obstacle.
Moreover, the decentralized nature of embedded devices will represent a considerable challenge to overcome, as upgrading legacy equipment will be complex and costly.
A strong market dynamism
Post-quantum security is very much an emerging topic. Yet, today’s market for solutions is extremely dynamic, Companies, governments, and institutions are mobilizing to address emerging risks, fueling a surge in innovative and specialized technological offerings. This momentum will be further accelerated by expected regulatory pressures, such as those from NIST, ASD, and ENISA, compelling organizations to adopt robust and compliant solutions.
An international and sovereign Market: digital sovereignty at stake
The quantum computing market is both global and deeply intertwined with questions of national sovereignty. Quantum computers are considered a strategic issue by the world’s leading nations, which invest hundreds of billions to ensure their sovereignty in that emergent field.
On the other hand, the market for post-quantum security is framed in a much more international prism. Companies in our radar span many nations, with the U.S. being nevertheless the uncontested leader. Moreover, international partnerships have also taken place such as Thales, which partners with IBM, CryptoNext and many more to combine their respective expertise and provide clients with advanced solutions.
A promising but incomplete market coverage
As we have covered, the market is extremely dynamic. The question remains whether the ecosystem’s needs for a post quantum transition are currently met. Currently, there is a lack of true hardware post-quantum solutions, as most of what exists is only a post-quantum layer. Nevertheless, our understanding of the market is very much that it is under development and should be more and more available this year already. Based on how we advise clients in planning and implementing their migration, the market solutions address or will address shortly most of our client’s needs.
Our evolving radar constitutes the first edition in this field. In that sense, we strongly encourage any absent company to contact us to remedy the situation.


