A new guide amid growing attention to industrial cybersecurity
As cyber threats become more targeted, sophisticated and persistent—particularly against industrial systems and critical infrastructure—the ANSSI (French Cybersecurity Agency) has strengthened its cybersecurity framework by publishing a revamped version of its guide for the classification of industrial systems, originally released in 2012.
This guide is intended for all stakeholders involved in industrial system security: operators, operators of vital importance (OIV), essential service operators (OES), integrators, and service providers responsible for aligning technical requirements with business imperatives.
Its aim is to provide a methodology for determining the criticality of industrial systems, classifying them into one of four cybersecurity levels—minor, moderate, major or catastrophic—based on the maximum severity of potential impacts on: the population, the economy, and the environment. This classification helps identify the appropriate level of security needed and guides the implementation of cybersecurity measures.
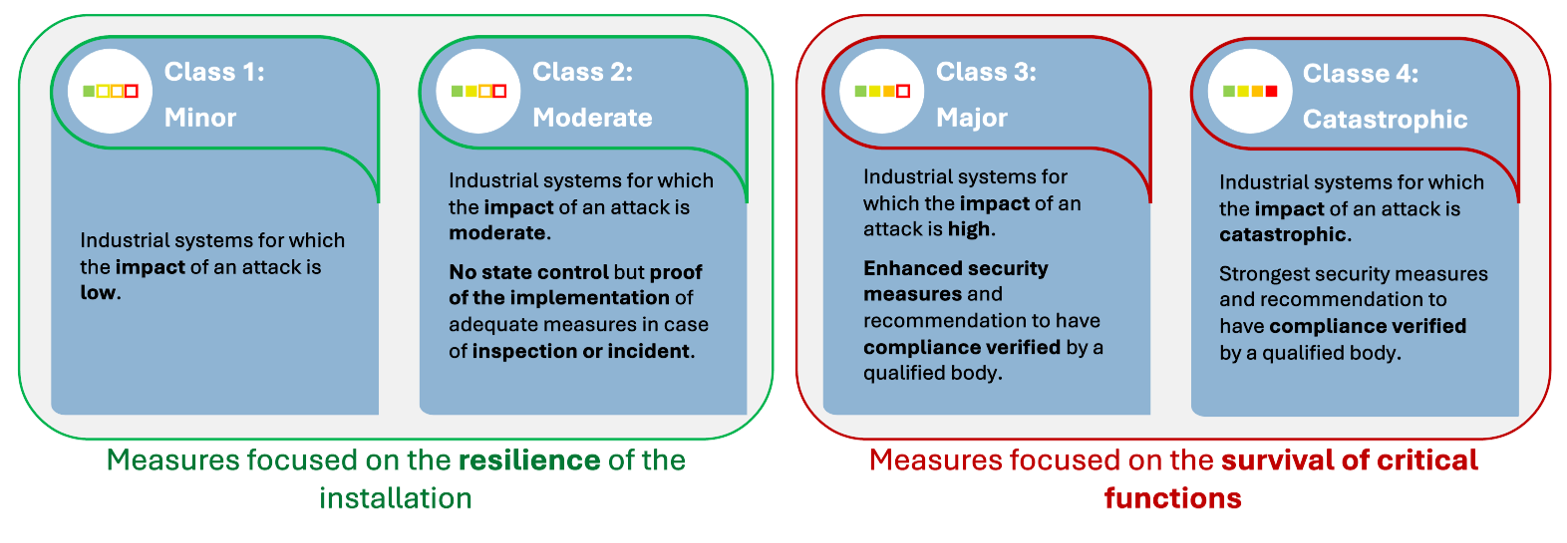
Figure 1: The 4 cybersecurity classes of the guide
Why revisit the existing framework?
The first edition of the classification guide, published in 2012, laid the foundation for a tiered security approach by introducing a three-class segmentation model based on risk (impact × likelihood).
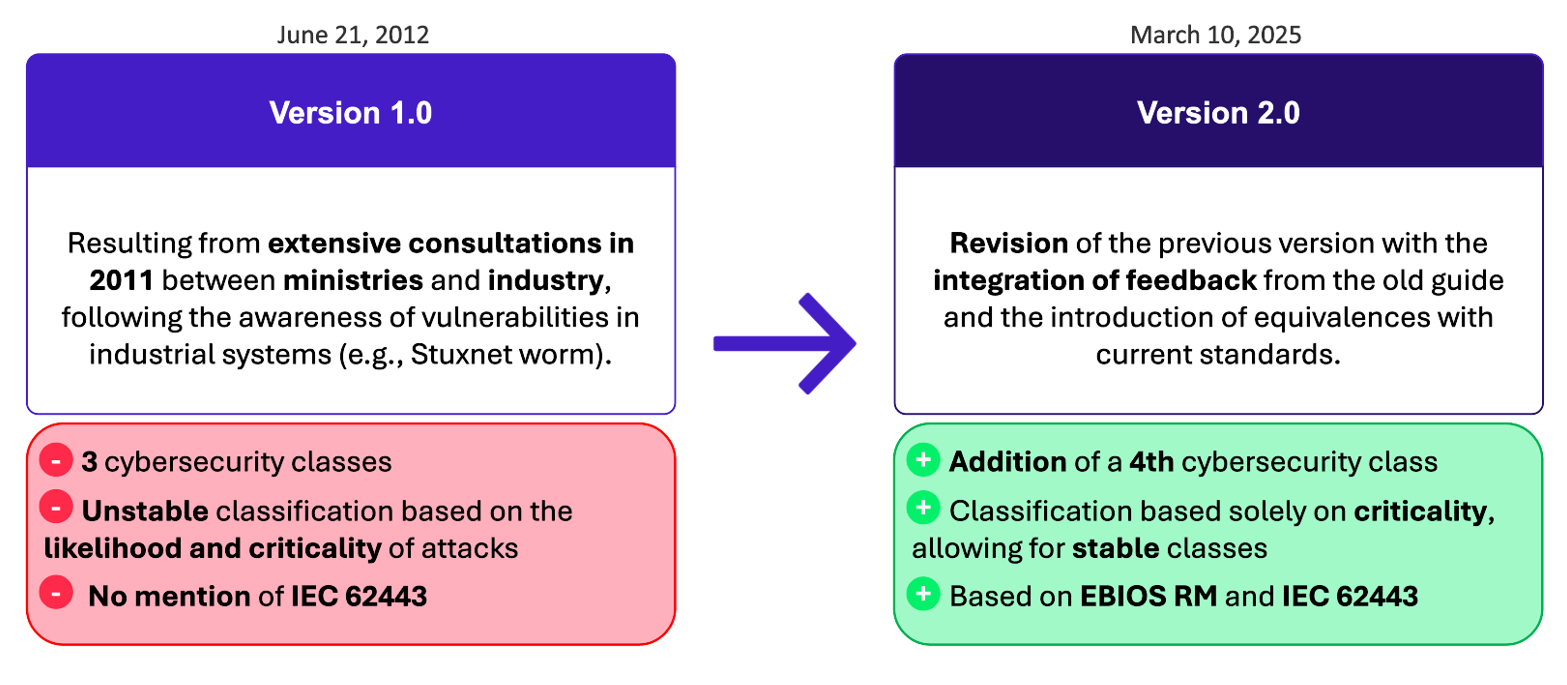
Figure 2: Key differences between the first and second versions of the guide
While this initial version played a key role in fostering a culture of industrial cybersecurity in France—at a time when sector-specific references were still scarce—it encountered several limitations over time.
Firstly, the integration of likelihood into the classification process led to a so-called “looping effect“, as described in the new guide. As security measures were implemented, the likelihood of an attack was considered to decrease, which in turn could lower the system’s classification level. This phenomenon compromised the stability of classification over time, making it difficult to maintain consistency between classification and actual protective measures.
Moreover, the initial guide proposed only three classes, which resulted in systems being assigned to the highest one too often. There was also a lack of granularity in perimeter definition and limited alignment with international standards such as IEC 62443.
The new version addresses these challenges by basing classification exclusively on impact, ensuring more stable classifications, consistent comparisons between zones, and better integration with structured risk analysis frameworks like EBIOS RM. This evolution also makes the approach more adaptable to the diversity and complexity of modern industrial systems.
A methodology compatible with existing frameworks
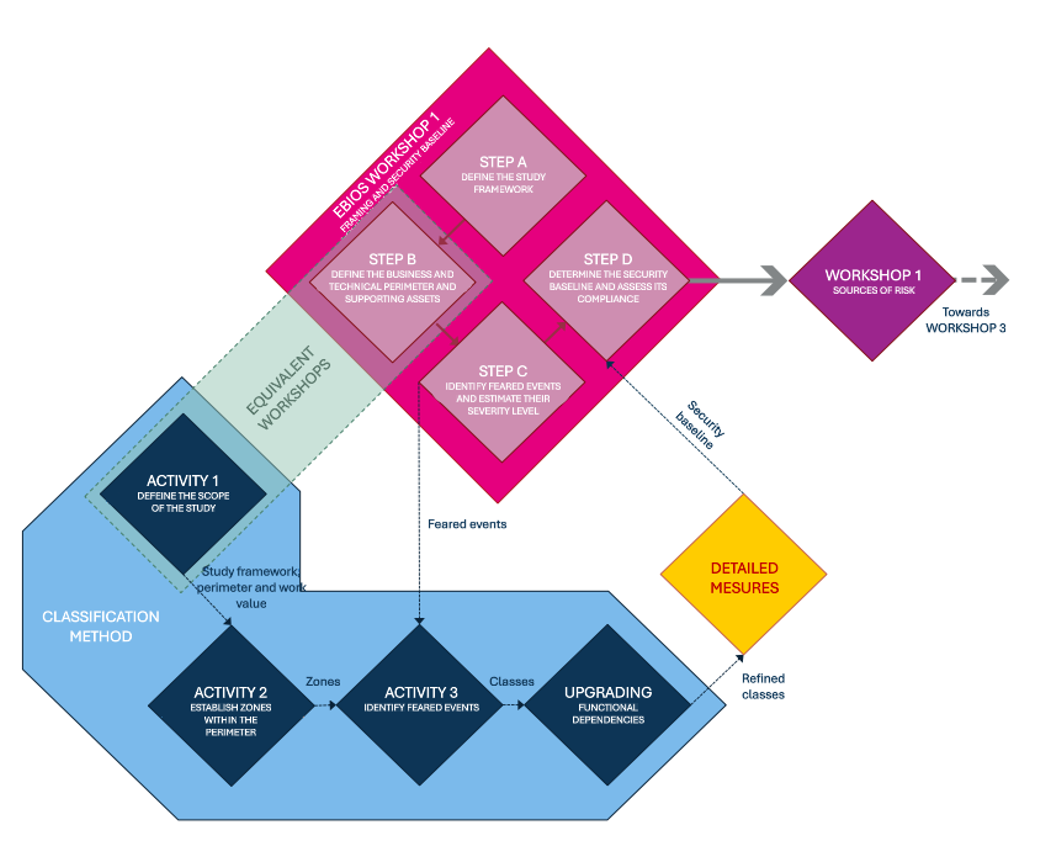 Figure 3: Classification methodology diagram from the new guide
Figure 3: Classification methodology diagram from the new guide
The new methodology is structured around three key activities:
- Definition of the technical perimeter
- Segmentation into coherent zones
- Classification of each zone based on the potential severity of impacts in case of compromise
This approach enables organizations to assign each zone to one of the four cybersecurity classes according to the severity of potential impacts. It provides a rational and scalable understanding of security needs, with a focus on two key criteria: availability and integrity, which align with the core concerns of industrial environments.
The guide does not replace risk analysis frameworks but is designed to integrate seamlessly with them. It was specifically built to feed into EBIOS RM workshops, providing a classification baseline that supports the identification of feared events and associated security measures. This structure eliminates the need to adapt or distort EBIOS RM to accommodate industrial contexts.
The guide also draws on concepts from IEC 62443, such as zones, conduits, and security levels, helping align with international industrial cybersecurity best practices.
This alignment is part of a broader push toward a structured deployment of cybersecurity. The guide provides a practical framework organized around key thematic areas, as illustrated below, to help effectively integrate cybersecurity into industrial environments.
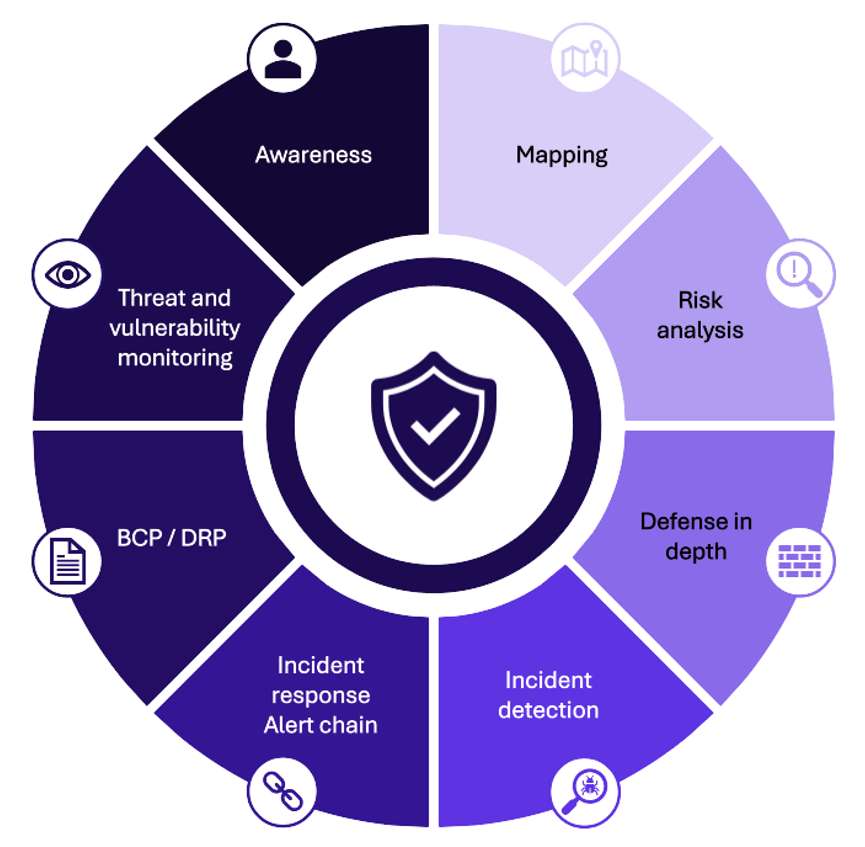 Figure 4: Key themes for deploying cybersecurity (Chapter 3.1 of the guide)
Figure 4: Key themes for deploying cybersecurity (Chapter 3.1 of the guide)
What comes next: a detailed measures guide — bridging the gap between strategy and action
Expected in the coming months, the detailed measures guide is the logical continuation of the classification methodology. It aims to equip industrial stakeholders with practical tools to move from theory to implementation, translating the cybersecurity classes into concrete operational requirements.
Inspired by the 2012 guide, which already proposed a set of baseline measures for each class, this new version promises a more refined, up-to-date approach that reflects current threat landscapes and security practices. It will offer decision-makers and system owners a clear and actionable toolbox, detailing technical, organizational, and human measures adapted to the criticality level of each zone.
Scheduled for publication in 2025, the guide will ensure continuity with risk analysis and compliance efforts already underway, while clarifying expectations regarding the concrete implementation of protective measures.
Securing the present, anticipating the future
Beyond its publication, the real challenge now lies in adopting the methodology and integrating it into the cybersecurity strategies for both existing and upcoming industrial systems.
For existing systems, the new guide naturally fits into the security lifecycle recommended by ANSSI in its EBIOS RM guide. Impacts should be assessed on a case-by-case basis to determine whether modifying current architectures is worthwhile, weighing the cost of change, evolving business needs, and expected security benefits. Integration can occur:
- During the strategic cycle, typically conducted periodically or following a major change, which offers an opportunity to revise perimeter definitions, update functional zones, and reassess system classifications using the new methodology;
- Or during the operational cycle, focused on reviewing feared events, checking whether existing measures align with the defined cybersecurity classes, and adjusting protection strategies as needed.
For new industrial projects, the new guide officially replaces the 2012 version and should be incorporated from the earliest design phases. It provides a framework for building a secure architecture aligned with business priorities, while also easing compliance with current and upcoming regulatory frameworks (NIS2, LPM, etc.) or contractual obligations.
At Wavestone, we are integrating this guide into our industrial cybersecurity maturity evaluation framework and Cyber Benchmark methodology, alongside international standards such as IEC 62443 and NIST SP 800-82. All that remains is to wait for the operational measures guide to complete the picture!