The internet of Things (IoT) is a rapidly growing sector, with increasing adoption across a wide range of domains. From production plants (industry 4.0) to homes (smart home systems) and even the devices we wear (such as smartphones and smartwatches), connected objects are becoming omnipresent in our daily lives.
The Radio Equipment Directive (RED) establishes a European framework for regulating all equipment that communicates via radio waves. This includes any device using technologies such as Wi-Fi, Bluetooth, LoRaWAN, or cellular networks like 4G and 5G.
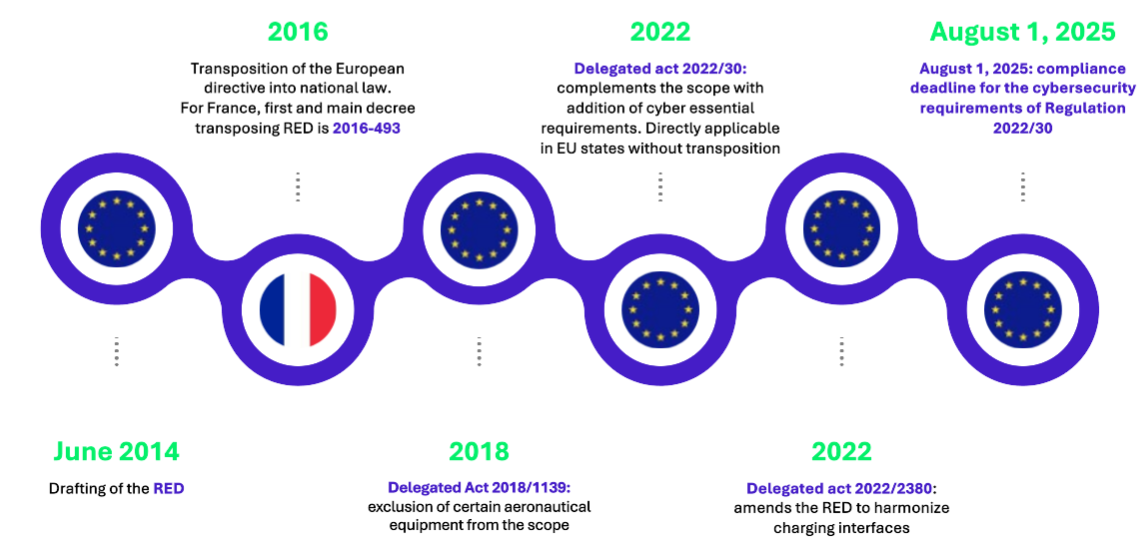
In this context, August 1st 2025, marks a key milestone: from that date onward, the RED’s cybersecurity requirements will become mandatory! Economic operators (including manufacturers, importers and distributors) who fail to comply with these obligations may face sanctions ranging from the withdrawal of their products from the EU market to significant administrative fines, depending on the applicable legislation in each member state.
This article aims to break down the directive and highlight the key takeaways. If you are behind in your compliance efforts, you will also find guidance here on how to get started!
RED explained: What you need to know
Adopted in June 2014, the RED (2014/53/EU) aims to standardize the marketing of radio equipment within the EU. Its primary objective is to ensure that devices that transmit or receive radio waves (such as smartphones and Wi-Fi routers) comply with health, safety, electromagnetic compatibility, and efficient use of the radio spectrum requirements.
However, it was not until 2022 that cybersecurity was integrated into the RED, nearly eight years after its creation. The introduction of delegated act 2022/30 marked a new phase by adding specific requirements aimed at enhancing the resilience of radio equipment against digital threats.
Scope of application of RED
Definition of radio equipment
According to Article 2.11 of the RED, radio equipment is defined as:
“An electrical or electronic product that intentionally emits and/or receives radio waves for the purpose of radio communication and/or radio navigation”
Specifically, this includes any device that uses wireless communication protocols such as Wi-Fi, Bluetooth, Zigbee, LTE, 5G, NFC, or LoRa to transmit or receive data via the radio spectrum.
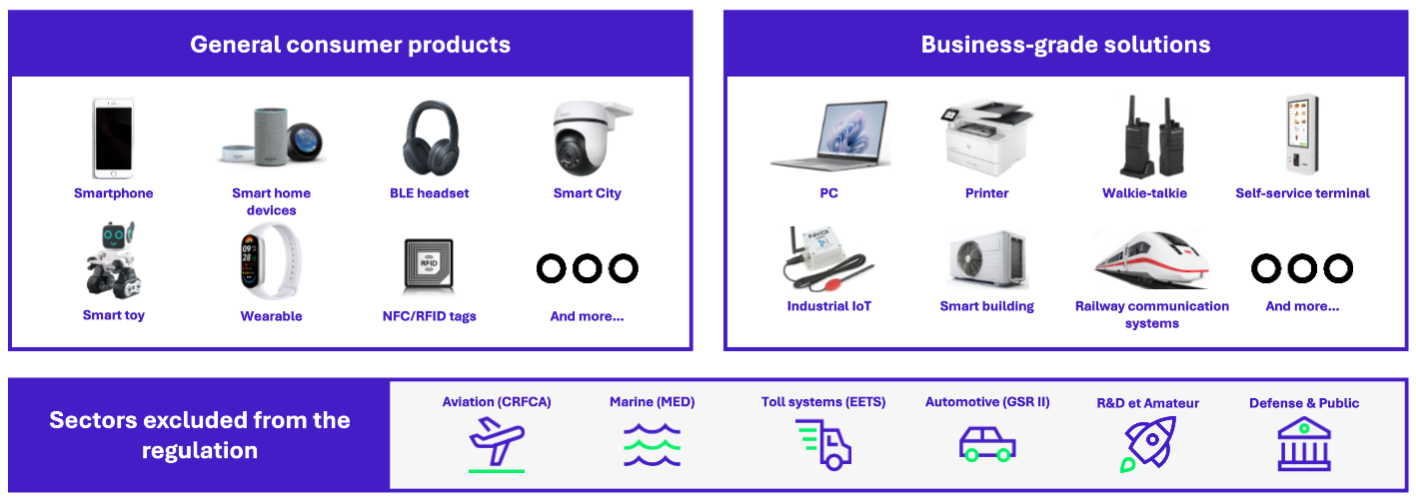
These technologies form the basis of many everyday devices, particularly in the fields of home automation and the Internet of Things (IoT). The RED directive therefore covers a very wide range of products.
Sectors excluded from the scope
The RED directive does not apply to all radio equipment. Some categories are explicitly excluded from its scope, particularly for reasons of sovereignty, specific regulatory frameworks, or usage contexts.
Sectors subject to their own regulations:
- Marine equipment: excluded are devices already covered by the Marine Equipment Directive (MED)
- Aeronautical equipment: excluded are devices already regulated under the Common Rules in the Field of Civil Aviation (CRFCA)
- Automotive equipment: excluded are devices already subject to the New General Safety Regulation (GSR II)
- Defense and public security: devices used by national authorities within the scope of national defense or any public security activity
Equipment for non-commercial purposes:
- Customized research equipment (R&D): tailored for experimental purposes, not intended for commercial use
- Amateur radio equipment: when not commercially available but built and used by amateurs in a non-commercial setting
Economic operators subject to the directive and their responsibilities
The RED directive does not concern only manufacturers of radio equipment. It applies to the entire supply chain, from design to market placement. Each economic operator plays a key role in ensuring product compliance, safety and reliability. To this end, RED defines separate requirements for three main categories of actors: manufacturers, importers and distributors.
It is important to emphasize that the same company may fulfil several of these roles at once, and that this may vary for the same company from one product range to another.
Manufacturers
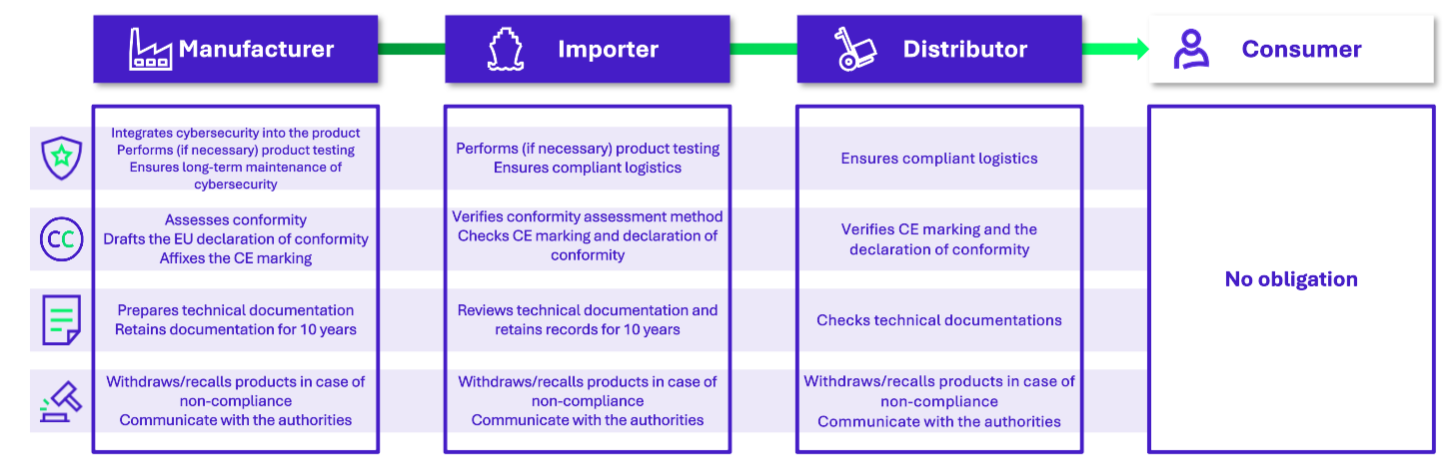
The manufacturer is on the front line. They are the ones who design, produce or brand an eligible product. They are therefore responsible for most of the actions required to bring products into compliance with RED. They must:
- Ensure that the product complies with the essential requirements of the RED
- Ensure that the product remains compliant in the event of modifications
- When appropriate given the risks, carry out sample testing, keep a test record and keep distributors informed of the test history
- Carry out or have carried out a conformity assessment
- Provide an EU declaration of conformity
- Affix the CE marking
- Prepare the technical documentation and user instructions and retain them for 10 years
- Withdraw or even recall a product from the market in case of non-compliance
- Communicate with the authorities in the event of non-compliance or upon request
Importers
When a product is manufactured outside the EU, the importer is responsible for transporting it from its country of origin to the EU. The importer becomes responsible for its compliance when it enters the European market. The importer must:
- When appropriate given the risks, perform sample testing, maintain a record of the tests and inform distributors of the test history
- Ensure that product storage and transport conditions do not compromise compliance
- Verify that the manufacturer has used an approved certification method
- Check for the presence of the CE marking
- Ensure that the technical documentation, declaration of conformity and user instructions are compliant, and retain a copy for 10 years
- Withdraw or recall a product from the market in case of non-compliance
- Communicate with the manufacturer and relevant authorities in case of identified non-compliance or upon request
Distributors
The distributors is the operator who makes the product available on the market to the customer or end user. They have a duty of care regarding the work carried out upstream by the manufacturer and importer. They must:
- Ensure that storage and transport conditions do not compromise product compliance
- Verify the presence of the CE marking and the availability of an EU declaration of conformity
- Ensure that the technical documentation and user instructions are compliant
- Withdraw or recall a product from the market in case of non-compliance
- Communicate with the manufacturer, importer and competent authorities in case of identified non-compliance or upon request
Key cybersecurity requirements under RED
In 2022, RED introduced 4 essential cybersecurity requirements. These requirements are subject to eligibility criteria based on the characteristics of the product and are therefore not applicable to all devices. Rather than prescribing a fixed list of security measures to implement, the requirements represent broader security concepts to be integrated into product design.
Network security
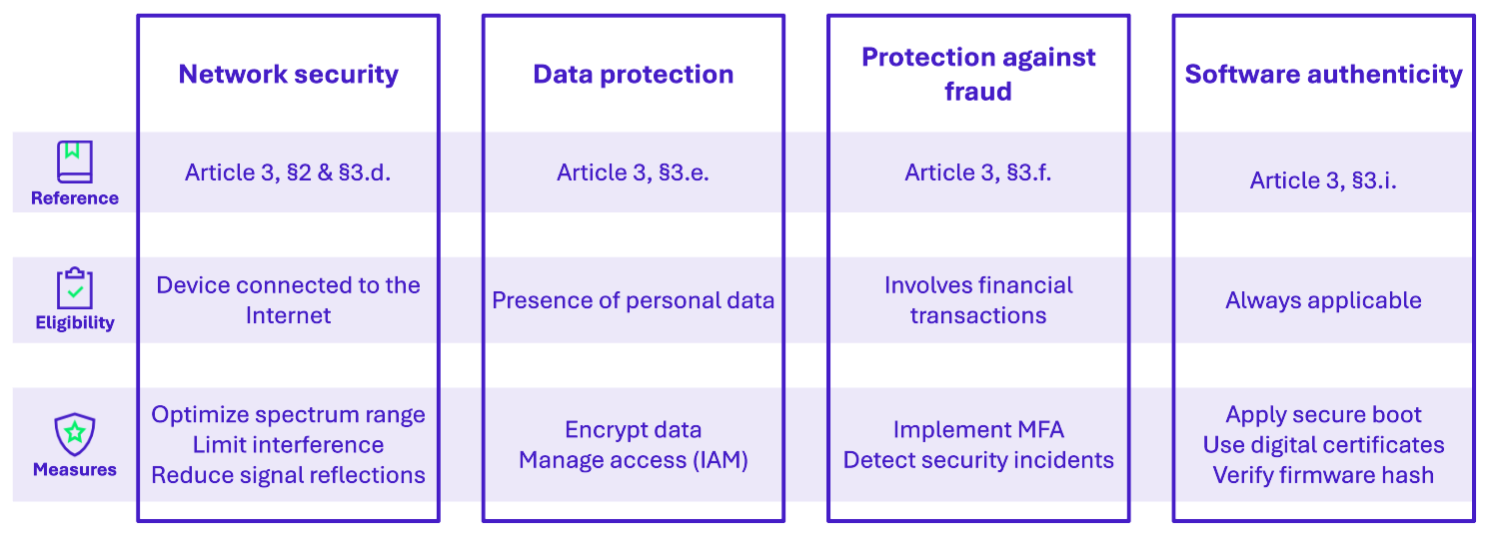
Eligibility criteria: Applies to all devices connected to the Internet, either directly or indirectly. These measures are designed to prevent such devices from compromising network stability or performance.
Cyber requirements: On the one hand, equipment must be designed to use the radio spectrum efficiently, without causing harmful interference. This ensures seamless coexistence between different devices without interference or disruption. On the other hand, they must not be capable of degrading, disrupting or hijacking network operations.
Protection of personal data
Eligibility criteria: Applies only to equipment that processes personal data. It aims to ensure user privacy.
Cyber requirements: Devices must incorporate data protection mechanisms such as encryption to prevent unauthorized access. This involves securing information not only in transit but also during storage.
Protection against fraudulent use
Eligibility criteria: Specifically applies to equipment involved in money transfers, such as payment terminals or certain smartphones. This aims to limit the risk of fraud via this equipment.
Cyber requirements: The regulation requires the integration of anti-fraud features, without prescribing a single solution. Among the possible approaches, multi-factor authentication (MFA) can be an effective measure, adding an extra layer of security during transactions. However, other mechanisms may also be considered depending on the context of use and the level of risk identified.
Software authenticity
Eligibility criteria: Applies to all equipment. The goal is to prevent the installation or execution of unauthorized software on a given device.
Cyber requirements: Implement features that verify the software and hardware combination prior to any installation. This may include secure boot, signature/certificate verification, hash checking or any other method ensuring authenticity.
Steps to ensure compliance with RED
Methods for ensuring compliance
Compliance with RED directive can quickly become a complex exercise, particularly when it comes to identifying the applicable cybersecurity requirements. To this end, CENELEC published RED related harmonized standard EN 18031 in early 2025. This standard clarifies the requirements and provides an official framework for RED compliance.
However, it is important to emphasize that the use of EN 18031 is not mandatory. Certifying a product as compliant with EN 18031 is only one of the ways to achieve conformity with RED. A decision tree provided by RED allows for determining (depending on the product), which conformity assessment method is permitted. One of these methods is self-assessment, meaning a self-evaluation of compliance with the essential requirements, provided that the technical measures implemented and the associated justifications are thoroughly documented.
However, these tools (EN 18031 and decision trees), although very useful remain complex to implement due to a margin for interpretation left on some aspects.
Standard procedure for manufacturers
Based on Wavestone’s experience in cybersecurity compliance projects related to regulations and more specifically regulations targeting products, we offer a framework structured around 10 key steps:
- Inventory: Conduct an inventory of radio equipment marketed in the EU that does not fall under excluded sectors
- Requirements: Apply product specific eligibility criteria to identify the applicable essential requirements
- Strategy: Use the decision tree to identify possible certification methods and validate the chosen strategy for each product based on risk
- Framework: Specify (EN 18031) or interpret (legal text) the applicable framework by translating it into concrete, auditable security control points
- Gaps: Compare the current state of products and processes against the control points of the chosen framework to develop a remediation plan
- Remediation: Implement the remediation plan at both the product and cross-functional levels to ensure long-term compliance
- Documentation: Document and justify the decisions made and actions taken with respect to RED and/or EN 18031 requirements
- Instructions: Document best usage practices and safety instructions to ensure operation in compliance with the requirements
- Self-assessment / Third-party certification: Conduct a self-assessment or an audit via a certification body depending on the chosen strategy
- Communication: Affix the CE marking and liaise with authorities and other involved economic operators
Positioning of RED within the cybersecurity regulatory framework for connected products
The RED directive and the Cyber Resilience Act (CRA) clearly operate within a shared regulatory domain. For readers not yet familiar with the CRA a detailed analysis is available here. The scope of application of the RED is included in the CRA and the essential requirements of the CRA go beyond what is established by the RED. In this sense, compliance with the CRA implies compliance with the RED. As the CRA is set to become fully applicable in December 2027, there are ongoing discussions at the European level regarding the possibility that RED’s cybersecurity requirements may only remain in force until that date, with the CRA subsequently taking over. While such a transition would indeed be coherent, no official communication has been issued to that effect as of today.
Nevertheless, achieving compliance with the RED as of now enables companies to effectively prepare for the implementation of the CRA. Both regulatory frameworks are based on similar compliance approaches and the harmonised standards for the CRA are currently being drafted by CENELEC, the same body that developed EN 18031, the harmonised standard under the RED.
While RED compliance will become mandatory as of August 2025, it should also be viewed as a strategic opportunity to prepare for the CRA and future European regulatory requirements concerning product cybersecurity.


