Post-Quantum Cryptography (PQC) has fueled debates for years, but since the European Commission’s June 2025 communication on the PQC transition roadmap, the acceleration is undeniable. It is no longer a question of “if” but rather “when”, quantum computing will disrupt our cryptographic foundations. As the Wavestone RiskInsight article « Quantum computing and post-quantum cryptography: what strategy should companies adopt to deal with these issues? » reminds us, this subject shifts from a long-term perspective to a strategic imperative for CISOs, CTOs and product teams. How does that change your industrial environments as well as your smart products, and how to act as of now?
Quantum Threats: a new era for industrial cryptography
Quantum computing represents a threat to traditional cryptographic algorithms which guarantee integrity, authenticity and confidentiality of communications, including those of OT systems and products. Even if “Q-Day” (the day quantum computers will break current cryptography) is still several years away, the risk is already present: threat actors can already use « Harvest Now, Decrypt Later » attacks by storing encrypted data today to decrypt them as soon as current cryptographic algorithms are broken. Another risk, just as critical, is already appearing: « Trust Now, Forge Later ». Digital signatures or certificates seen as reliable today could be falsified tomorrow, allowing transparent deployment of malwares or even compromising supply chains. Unlike progressive data breach, this attack triggers an immediate collapse of trust and integrity, with massive impacts on industrial environments and smart products. With the European roadmap, structuring 2026, 2030 and 2035, the question hinges on the sequencing of the transition.
Within the industrial sector, where assets are used for multiple decades, this represents a major concern: OT environments and embedded products depend on critical cryptographic usage that will be directly impacted by the arrival of post-quantum algorithms.
Key OT and product use cases include:
- Secure administration of OT systems and products: guarantee the integrity and confidentiality of operations.
- Digital signatures and firmware integrity: guarantee the reliability of software updates (secure boot, code signing, X.509…).
- Secure remote access to industrial assets and products: protect VPN, SSH, RDP connections as well as other protocols from future attacks.
- Data exchanges IT/OT: secure flows between information systems and industrial environments (TLS, MQTTS, HTTPS…).
- Data confidentiality of industrial processes: preserve the confidentiality of sensitive data in transit or at rest.
- Secure logging and event history: ensure the traceability and integrity of logs and historical data.
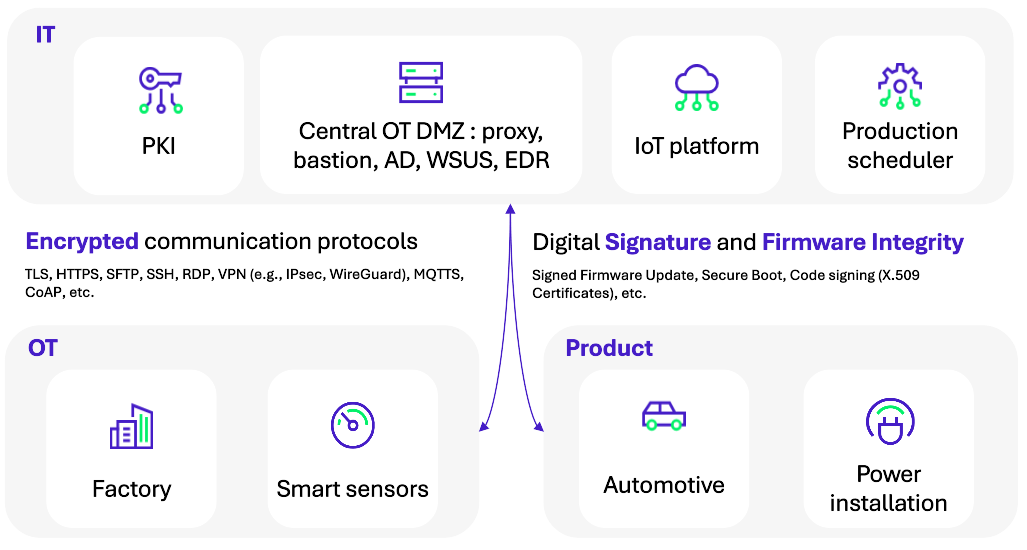
PQC for OT & Products: Address the constraints while preserving crypto-agility
OT & Products context: specific constraints
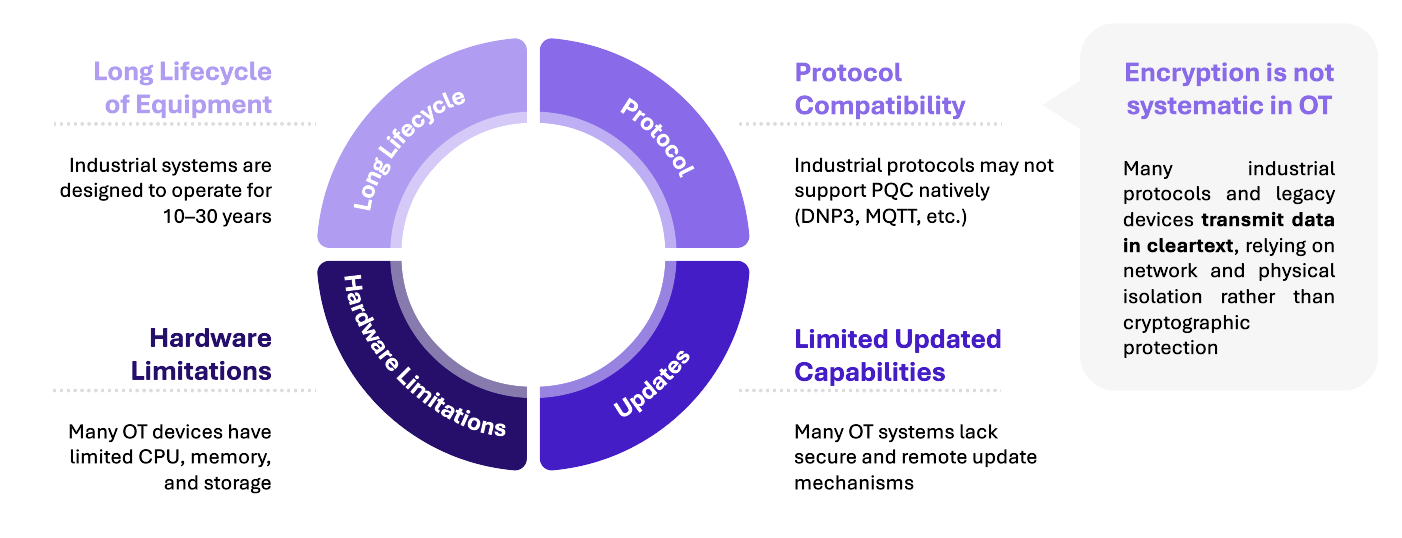
OT systems and products were never conceived for crypto-agility. Numerous industrial protocols, for instance DNP3, Modbus or MQTT, are not encrypted as of today because OT architecture historically depends more on network isolation than on cryptography, thus there is no reason to think they will be encrypted tomorrow with post-quantum algorithms.
Nevertheless, encrypted communications will undergo this cryptographic disruption.
In a second step, multiple OT devices face significant hardware constraints (CPU, memory, storage capacity) and have a very long lifespan, often between 10 and 30 years. Those characteristics make updates difficult and expensive: secure remote update mechanisms are still rare, and firmware signing is not consistently implemented, which is in fact bad practice.
Those constraints explain why OT environments cannot integrate new cryptographic primitives at the same speed as IT, and why PQC isn’t yet natively considered.
Nevertheless, even if current products and OT systems aren’t conceived for post-quantum cryptography, the emergence of PQC standards, the evolution of regulatory obligations and the rise of risks linked to quantum computing make this transition essential in the medium term.
Making crypto-agility operational for the industry and products
The scoping of the PQC project for Products and OT can be broken down into four main components:
1. Conduct the cryptographical inventory and prioritize critical assets
Start the dialogue with your cryptographic platform providers (PKI, KMS, HSM) now, to anticipate the migration.
2. Conceive and deploy crypto-agile architectures
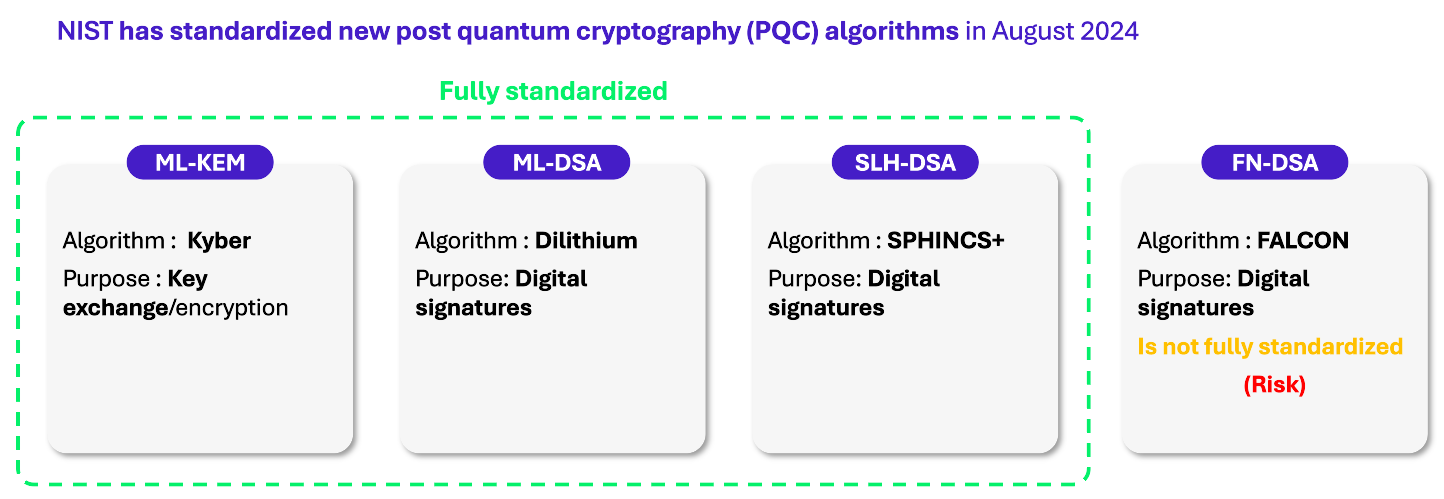
Rely exclusively on NIST-standardized algorithms (for instance: ML-KEM, ML-DSA, SLH-DSA) and prohibit any internal development or non-standard library for cryptographical components; prioritizing validated and proven solutions.
Conceiving crypto-agile architecture implies accounting for the embedded aspect and its constraints (limited memory, PCBs, energy resources). The implementation of PQC algorithms on those systems remains uncertain. Nevertheless, optimized algorithms for embedded systems are starting to emerge and open the way to its realistic adoption.
3. Progressively migrate through hybridization and iteration
Transition towards post-quantum cryptography cannot be approached as a one-off project or a “one-shot” migration. It is an iterative process that must be managed and governed over time, by starting with hybridization of algorithms: this is explicitly recommended by ANSSI (France’s National Cybersecurity Agency) and the European Commission.
Crypto-agility isn’t an option, but a necessity to ensure resilience and compliance for industrial environments and products from the quantum threat. This depends on a structured approach, driven by inventory, architecture, hybrid migration and governance.
Operational feedback & concrete use cases: stakeholders at different stages
Our field experience reveals a noteworthy maturity gap between two industrial organizations when dealing with post-quantum cryptography:
1. Organizations with a rudimentary understanding
- Observation: In numerous industrial environments, PQC remains an abstract concept, often seen as distant or limited to experts.
- Symptoms:
- Operational and business teams aren’t part of strategic deliberations on cryptography.
- Current roadmaps lack maturity and clarity; the underlying projects costs are often underestimated. Priority remains on service availability; quantum security is therefore deprioritized.
- HNDL & TNFL concepts are poorly understood, if not outright ignored.
- Risks:
- Disruption of industrial production processes and data breaches: vulnerable communications between critical assets, based on outdated algorithms, expose sensitive data and can cause interruptions or major disturbances in industrial operations (loss of integrity of the data).
- Production downtime caused by abrupt migration: A forced transition towards post-quantum cryptography, without preparation nor crypto-agility, can lead to production interruptions, significant additional costs and severe impacts on operational continuity.
2. Product suppliers: pioneers already undergoing industrialization
- Observation: On the contrary, some product suppliers are already ahead (including automotive and smart objects).
- Symptoms:
- PQC projects are prioritized over critical use cases: firmware and update signatures (OTA), device identity management, secure remote access, etc.
- Pilot projects are being launched on product lines or representative environments, with concrete feedback on performance, compatibility and robustness of hybrid solutions
- The process is being industrialized: Integration of PQC clauses in supplier contracts, automation of cryptographic inventory CBOM, team upskilling, and dedicated governance.
Conclusion & Roadmap: Take action to build a quantum-safe future
Quantum threat is no longer a distant prospect: it already demands a significant transformation of industrial and product cybersecurity.
- Plan ahead to protect the future
Demystify quantum concepts and incorporate them in your cybersecurity processes, including your products, your OT environments or your IT systems. Planning ahead is the key to preventing a major disruption.
- Make crypto-agility astrategic vision
Stop viewing it as merely a technical project, but as a pillar of your resilience and of your digital sovereignty. Build a clear roadmap, with milestones in the short, medium and long term.
- Rely on trusted partners
The market is ready: experts and solutions exist to support you through the modernization and securing of your critical infrastructure. Don’t face complexity on your own.
- Industrialize the process
Move from pilot projects to broader rollout:
- Implement a PQC strategy to map out, prioritize and pilot the migration of critical uses (include PQC clauses in contracts).
- Start a transition program to modernize trust infrastructure components (PKI, CLM, HSM), automate the inventory and ensure the operational continuity.
- Rely on peers’ feedback as well as feedback from sectors already engaged in PQC.
Quantum risk is already there: weakened asymmetric encryption, leaving signatures and data exposed.
As mentioned previously, we start from the observation that elements that aren’t encrypted today in OT environments are not meant to be encrypted tomorrow with post-quantum algorithms, because already existing measures ensure a risk level judged acceptable.
In other words, PQC doesn’t aim to transform the entirety of OT, but to protect the uses that really rely on cryptographical components exposed to quantum risk.
However, this observation doesn’t reduce the importance of planning.
The two priorities remain as follows:
- Migrate your assets before 2030 and act today to protect data confidentiality
- Define your perimeter, build your roadmap, and above all, begin the migration process today.


