This year again, we were delighted to be able to share our knowledge during Hacker Summer camp (cybersecurity conferences that happen roughly at the same time in Las Vegas each year: BlackHat, BSides Las Vegas, and DEFCON).
(Thomas is missing in this picture as he already left DEFCON to attend SANS DFIR Summit in Houston, TX).
In this article, we share the materials used for our talks, workshops, and tool demos.
CI/CD security
CI/CD pipelines are increasingly becoming part of the standard infrastructure within dev teamsand with the rise of new approaches such as Infrastructure as Code, the sensitivity level of such pipelines is escalating quickly. , with the rise of new approaches such as Infrastructure as Code, the sensitivity level of such pipelines is escalating quickly. In case of compromise, it is not just the applications that are at risk anymore but the underlying systems themselves and quite often the whole information system.
We feel that those infrastructure, while not targeted by attackers for now, will become a prime focus point for attackers in the years to come. Both because of the credentials handled by the pipelines and the usual lack of monitoring on those environments.
During Hacking Summer Camp, we explained how attackers are beginning to exploit those weaknesses both for supply chains attacks but also to escalate their privileges within the victim IS. We started with a talk at BSides Las Vegas which illustrated an attack path that we had already exploited in a real operation. Then, we conducted two workshops, at both BSides Las Vegas and at DEFCON, to allow students to exploit these attacks on a full-scale lab.
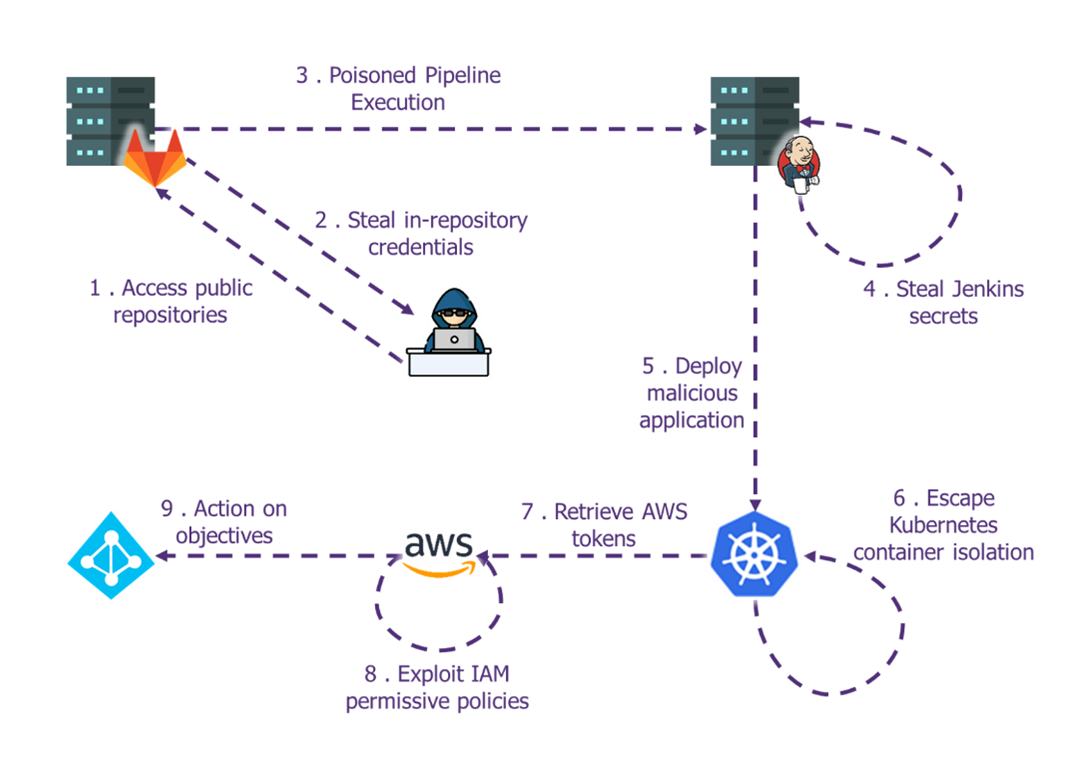
The lab & slides will soon be published on the GitHub (wavestone-cdt/DEFCON-CICD-pipelines-workshop (github.com).
The replay of the talk at Bsides Las Vegas is available on YouTube (https://youtu.be/a3SeASgtINY).
By Rémi ESCOURROU (@remiescourrou), Gauthier SEBAUX (@zeronounours) and Xavier GERONDEAU (@reivaxxavier1).
Industrial Control Systems
This year, we taught 2 workshops on ICS cybersecurity at DEFCON:
An updated version of our very popular “Pentesting ICS 101” workshop
We covered the basic of ICS and shared some feedback on the state of ICS cybersecurity. Then, using pre-configured virtual machines we learned how to exchange data with PLCs. This was then put into practice on real hardware with our model train setup:

A whole new workshop on PLC code security
We also started with an introduction to ICS, then dived into programming a software PLC, and demonstrating how applying practices from the PLC TOP20 can prevent attacks and/or help detect them.
To do this, we also created a very simplified process simulation that connects to the PLC simulator, that we also release. This could be used and adapted for ICS awareness and training.
GitHub – wavestone-cdt/plc-code-security: Experiments with the Top 20 Secure PLC Coding Practices
You can find our process simulation here : https://github.com/arnaudsoullie/simple-process-simulation
DEFCON30 demo lab: EDRSandblast
We shared a new and improved version of EDRSandblast during Demo Lab sessions at DEFCON 30. It was the occasion to introduce and detail the detection mechanisms employed by EDRs (user-land hooking, kernel callbacks, ETW Threat Intelligence provider …), to show how to get around them, as well as to showcase the new features of our tool. On the list of updated features: a new detection mechanism is recognized and bypassed by the tool, multiple vulnerable drivers are now supported, EDRSandblast can now be included as a library in a third-party project, and much more!
You can find the full list of updates, as well as the presentation on GitHub: https://github.com/wavestone-cdt/EDRSandblast/blob/DefCon30Release/DEFCON30-DemoLabs-EDR_detection_mechanisms_and_bypass_techniques_with_EDRSandblast-v1.0.pdf
By Maxime MEIGNAN (@th3m4ks) and Thomas DIOT (@_Qazeer).
SANS DFIR Summit 2022
In this talk, we gave a brief overview of an AD forest recovery procedure and focused on different means of persistence leveraged by threat actors in Active Directory, some well-known, other less so. Some features of the newly released FarsightAD PowerShell toolkit were also demoed, such as the detection of fully or partially hidden objects using the Directory Replication Service protocol. More techniques are covered in the slides than what was presented during the talk, so check the deck out!
You can find the slides and FarsightAD here: https://github.com/Qazeer/FarsightAD
By Thomas DIOT (@_Qazeer).
Happy reading, happy testing, hack the planet 😊


