Faced with an ever-increasing number of sophisticated cyber threats, the industry has been hard hit, and it is expected to become the 2nd most affected sector by ransomware in 2024. Industrial information systems, the very nerve centres of production, have become one of the most attractive and preferred targets for attackers seeking to paralyse or degrade their operation. There is no shortage of examples of business stoppages caused by ransomware: The paralysis of Colonial Pipeline in 2021 in the United States, the shutdown of the DSB rail company in Denmark, which had to stop all its trains in 2022, or the cybersecurity incidents affecting the London transport network in 2024.
Beyond the simple interruption of operations and financial loss, the consequences on the physical integrity of people and the environment are major HSE (Health, Safety and Environment) impacts that imply critical risks to be considered for the industrial sector.
Faced with these growing threats and impacts, manufacturers have, until now, invested in protecting their industrial information systems. Resilience is now being taken into account, and resilience projects are being incorporated into cyber IoT roadmaps. Depending on the sector and industrial entity, investing in effective recovery may be more worthwhile than excessive protection. By combining resilience and protection, businesses can safely resume most of their industrial activities as quickly as possible, reducing damage and financial losses
In this context, cyber-resilience is an absolute necessity.

What are the keys to building this resilience and meeting the challenges of tomorrow? Let’s find out together.
Cyber-resilience challenges for organizations
Cyber resilience is now a strategic priority for industry. The stakes go far beyond the simple security of systems:
- Ensuring the safety of people and the environment: In some sectors (hospitals, energy, nuclear, water treatment, etc.), the priority is to secure installations, even at the detriment of production. The human and environmental impact of a cyber-attack can be far more serious than simply stopping production.
- Protecting critical installations: The security of critical production installations must be assessed. An impact on these systems will have major repercussions on the company’s activity and turnover.
- Preserving sensitive data: Some industrial information is crucial for competitiveness and security. Any leak or alteration can seriously harm the company and, in some cases, national security.
- Resuming operations quickly and safely: Cyber resilience aims to restart operations quickly, while guaranteeing the safety of installations and people.
The challenges also extend beyond the organization’s internal security, with increasing geopolitical and regulatory impacts:
- Geopolitical risks: Cyber-attacks on critical infrastructures, such as those in the energy or water sectors, have significant political and societal consequences.
- Regulatory pressure: Legislation such as the NIS Directive, the LPM and the Cyber Resilience Act impose strict requirements, forcing businesses to continuously strengthen their cybersecurity.
What are the main resilience activities?
The main activities of cyber resilience are based on three main areas, each of which is essential for guaranteeing the continuity of operations in the face of incidents.
- Maintain critical activities in downgraded mode:
- Identify critical activities to be restored as a priority
- Industrialising operations in degraded mode to enable partial business continuity pending full recovery
- Contain the spread of incidents to limit their impact
- Test its crisis management:
- this includes setting up regular exercises to identify areas for improvement and strengthen the organization’s resilience against cyber-attacks.
- Industrializing reconstruction: rebuilding and restoring a healthy IS
- This is not simply about restoring services, but about checking and reinforcing each component of the system to ensure its long-term security. This phase helps regain stakeholders’ confidence and ensure a robust infrastructure, ready to prevent future threats.
Setting up an Industrial IT Disaster Recovery Plan: the cornerstone of IT recovery
The IIRP (Industrial IT Disaster Recovery Plan) is the key element of the cyber-resilience strategy for industry. This document brings together all the technical, organisational and security procedures needed to rebuild and restart an IoT information system after a disaster or major incident. The IIRP is activated during or after a disaster or crisis. Its role is to ensure the rapid and reliable resumption of industrial activities.
The IIRP generally contains the following elements:
- Clear responsibility matrix
- Schedule for efficient reconstruction
- Detailed procedures for restoring information systems and IoT IS assets
- Information on appropriate means of communication
- Recommendations on the frequency of tests to validate the resumption of activities
The main objective of the IIRP is to minimize recovery time while ensuring a high level of confidence in its IIS. It also protects sensitive data and helps limit the financial losses associated with business interruptions. By guaranteeing a high level of security, the IIRP minimizes physical, environmental and legislative impacts, while preserving the company’s image and facilitating the work of operational teams.
The recovery documentation architecture must be adapted to the size and structure of the company. It is essential to correctly choose the reconstruction granularity and the appropriate format for each information system (IS) and industrial entity.
Example
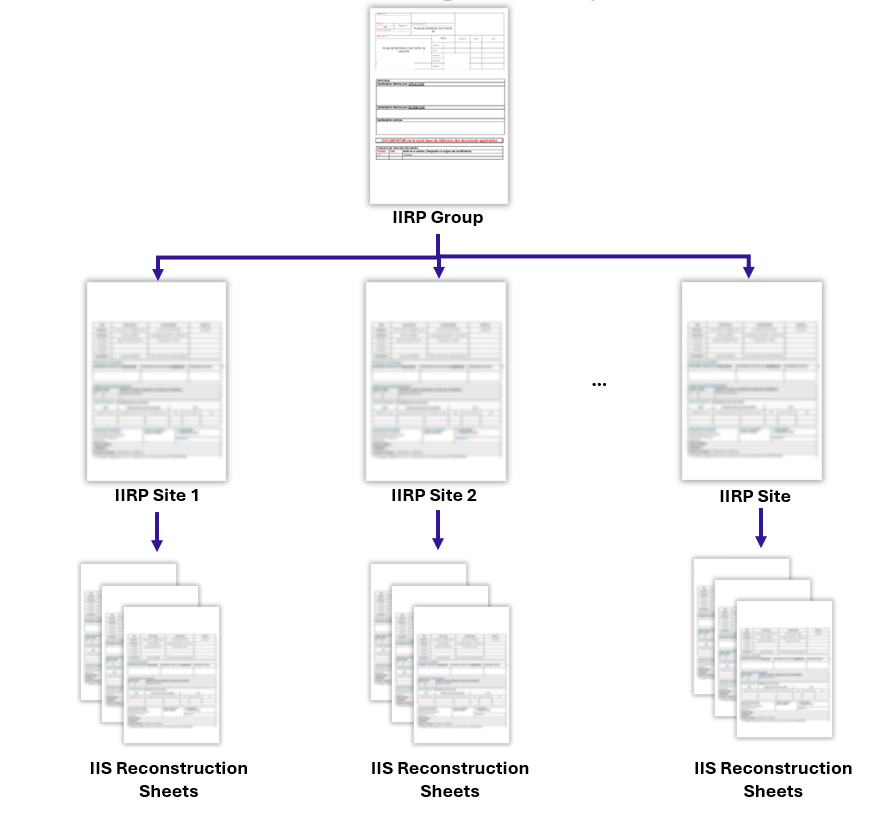
- IIRP Group (Group Industrial IT Recovery Plan): Main document defining the principles, responsibilities and processes for business resumption at the group level. It refers to the specific IIRP for each site. Review: Every 5 years or in the event of a major change.
- IIRP Site (Site Industrial IT Recovery Plan): Document detailing the recovery principles and responsibilities for a specific site. It also defines the recovery order of systems in the event of an incident affecting multiple IS and refers to the IIS reconstruction sheets. Review: every 5 years or in the event of a major change.
- Plant/IIS rebuild sheets: Operational documents detailing the scheduling and actions required for the recovery of each IIS, including architecture diagrams and asset inventories. Review: annually or when there are changes to the IIS.
The keys to a successful takeover: the importance of properly framing your takeover project
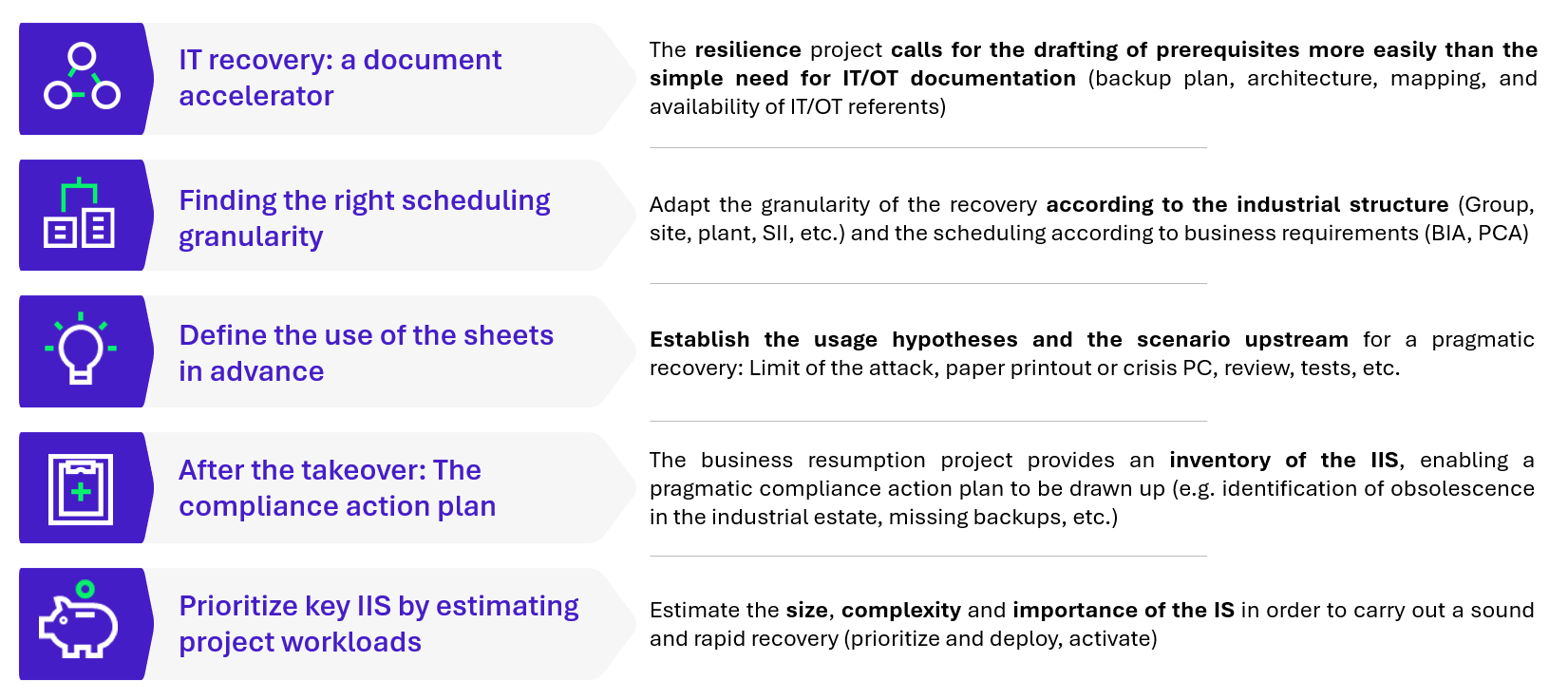
Focus | Defining the use of files upstream for optimum recovery
Before going on to write and implement the IIS reconstruction sheets, it is important to take several aspects into account in order to facilitate their drafting and ensure that they reflect the reality and requirements of the business.
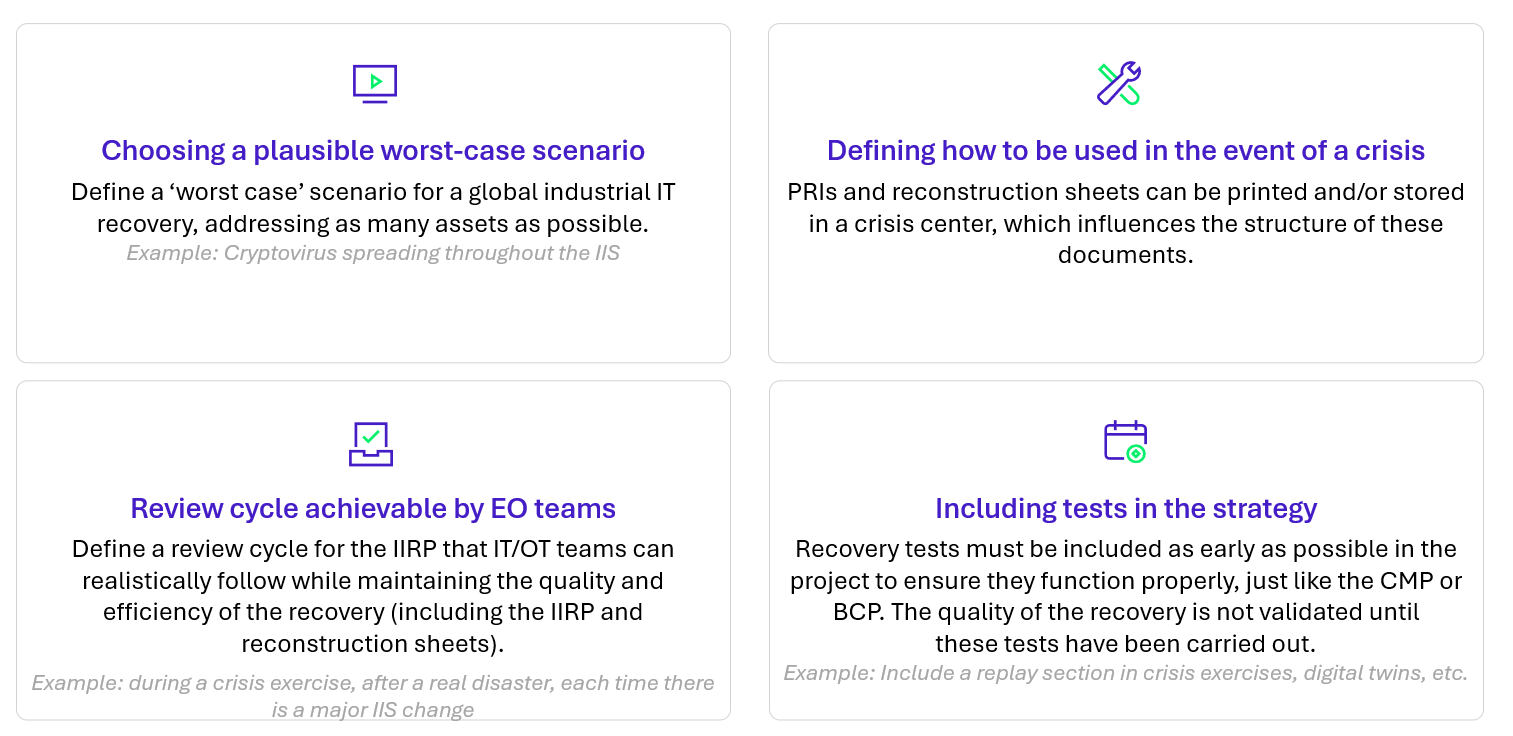
The essential prerequisites for writing an industrial IT recovery plan: why well-structured IIS documentation is crucial
It is necessary to formalise the essential documentary prerequisites for guaranteeing the effective recovery of the industrial IT system (IIS), focusing on the following key elements:
- Mastery of IIS: In-depth knowledge of IIS is essential. This includes a clear view of the systems, a detailed inventory of assets, as well as mapping and architecture diagrams (logical and physical). It is also crucial to identify the IIS referents who hold the key knowledge of these systems and to ensure that their information is regularly updated.
- Backup plan: A comprehensive backup plan, including data critical to the plant’s smooth operation, is essential to ensure a rapid and complete resumption of activity. This includes elements such as the backup of PLC programs and configurations, administrative PCs, SCADA systems and historians.
- Business knowledge: The presence of a Business Continuity Plan (BCP) or business correspondent is a major asset in defining effective scheduling. It ensures that the recovery plan is not only applicable, but also operational and in line with the specific needs of the business.
These three fundamental elements are essential if we are to initiate an effective IT recovery process that is aligned with the real needs of the business. The project cannot get off the ground without them, and without adequate funding for the site.
Further information | Recovery: A major stage in IIS compliance
The business recovery project provides an in-depth inventory of the IIS, which serves as the basis for drawing up a pragmatic action plan to bring it into compliance. This process includes identifying obsolescence in the industrial estate, missing backups and other points of weakness. Thanks to the recovery tests, numerous recommendations and improvements can be put in place to strengthen the security of the IIS and make it more resilient in the face of crises.
The resulting action plan highlights several key points (not exhaustive):
- Obsolescence management: The obsolescence of IT infrastructures must be taken into account in the disaster recovery strategy. Aging equipment can seriously compromise the effectiveness of recovery plans.
- Unmaintained software on obsolete PCs: The use of monitoring software not maintained by the publisher, installed on obsolete PCs (hardware and operating system), and difficult to replace, presents a major risk. In the event of a crisis, this could prevent the plant from operating properly due to a lack of supervision.
- Lack of back-up for critical data: The absence of back-up for a key server, essential for the resumption of activity at several sites, jeopardises the continuity of the entity’s operations.
- Lack of documentation and failure to comply with contracts: The lack of documentation on certain equipment (configurations, installation procedures) and the absence of architecture diagrams for certain IS show a failure to comply with contractual requirements. These shortcomings will complicate the reconstruction of the IS in the event of a crisis.
In conclusion, the success of an industrial disaster recovery project depends on rigorous preparation, including defining the sizing and requirements of the plants, drawing up a roadmap prioritising critical activities, and setting up a project team with the necessary dedicated resources. These steps ensure a smooth recovery, on time and on budget, while strengthening resilience in the face of cyber risks.


