OT, lower exposure but higher vulnerability
Operational Technology, while overall less impacted than IT, is not exempt from cyberthreats & not immune to cyberattacks. Let’s take a closer look at a simplified view of the threat landscape for industrial environments:
- Hacktivism: Increased geopolitical tensions in 2025 have led to low-level attacks by groups like CyberArmyofRussia_Reborn and CyberAv3ngers.
- Cyber Crime / Ransomware: There has been an 87% increase in ransomware attacks on industrial groups in 2025 according to Dragos in its annual report.
- Nation-State: Notable campaigns include Voltzite OT information theft and the IOControl campaign.
This threat landscape was notably depicted by Chris Sistrunk, ICS/OT Technical Leader at Mandiant, Google Cloud Security, at Black Hat 2025:
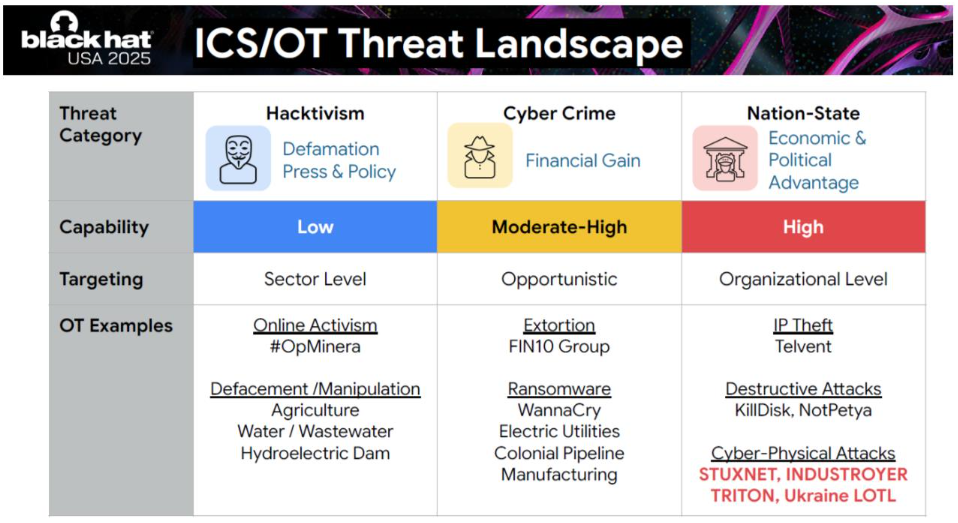
Given this increasing threat landscape targeting OT, continuous monitoring is essential. So, we know why industrial information systems need to be closely monitored, and we also know that our clients are actively working toward that goal. But one key question remains: how do we measure the effectiveness of detection? And how can we improve it?
How to assess the effectiveness and improve detection on industrial perimeter?
To answer that question, we developed a methodology aimed at evaluating detection capabilities within industrial SOCs.
The evaluation was built around the core activities of a SOC, structured into four pillars:
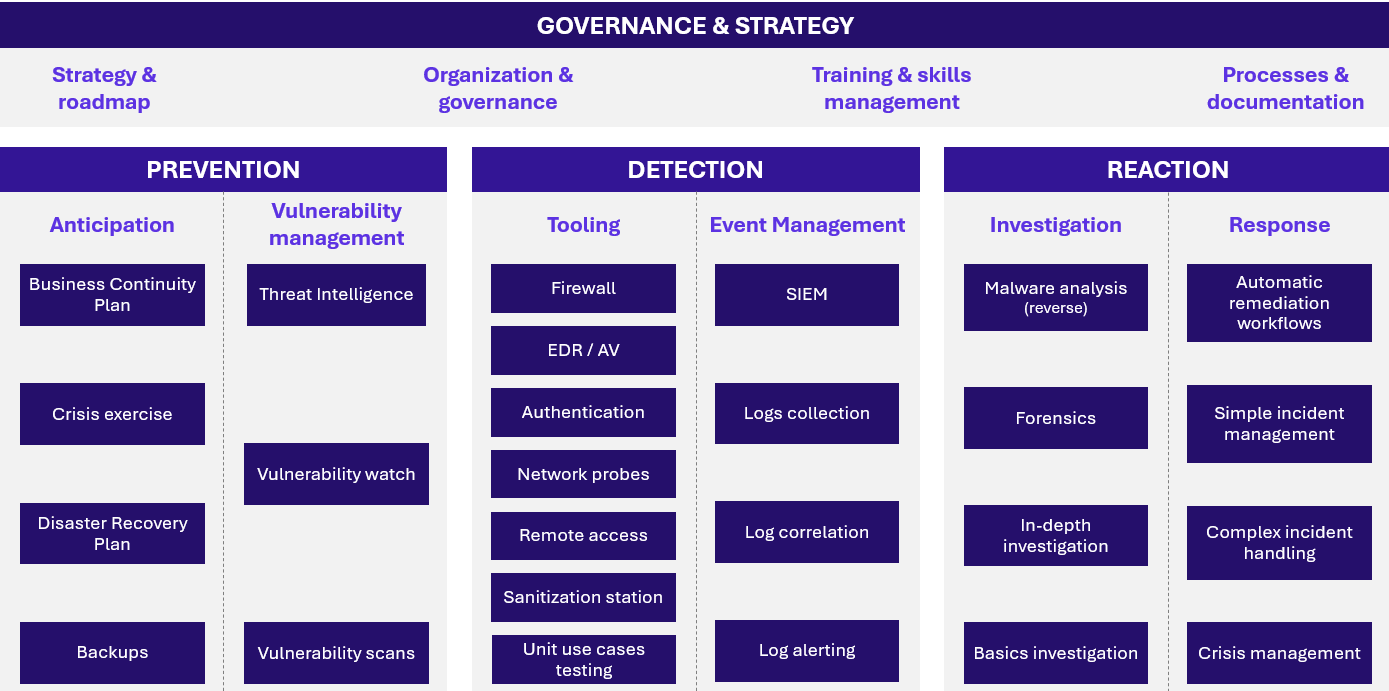
Using this framework, we assessed ~15 industrial clients to better understand their level of maturity. In this article, we’ll share the key trends and insights that emerged, focusing specifically on detection-related questions. Two follow-up articles will be published: one delving into the effectiveness of various detection strategies and solutions, and another explaining how to test detection capabilities in industrial environments with purple teaming and the custom modules developed for that purpose.
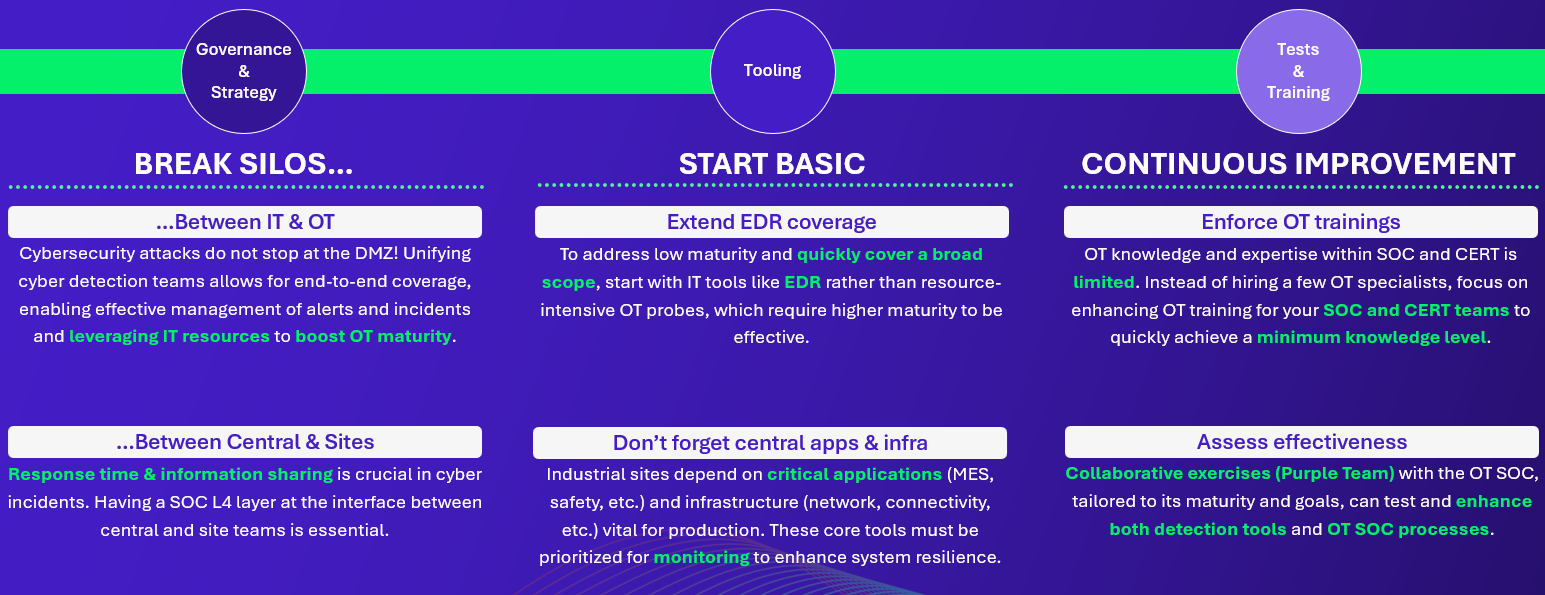
Governance & Strategy
The first question we focused on was whether industrial sites monitoring is handled by a dedicated team using specialized tools — or if, on the contrary, it’s integrated into a broader, centralized SOC approach.
Responses are unanimous:
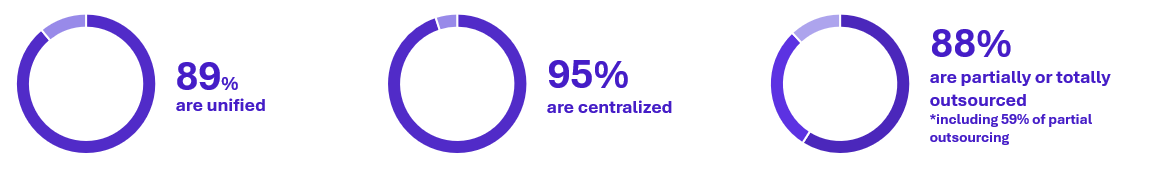
These figures can be explained by several factors. One key reason is financial rationalization. Maintaining two separate teams with similar skill sets: managing alerts, configuring tools, duplicating capabilities… is costly. However, a unified SOC implies an extended scope to cover OT, but not the presence of OT-specific tools or expertise and in the end, OT detection capabilities.
Even if this approach does not guarantee effective detection and response across the OT scope, a unified SOC can manage OT incidents efficiently, under the right conditions:
End-to-end monitoring
If we look closely at the simplified threat landscape, cyberattacks might not be IT or OT-specific. Cybercrime such as ransomware, the dominant threat today, is not limited to IT or OT alone. It often spreads across both, making it essential for alerts to be followed from end-to-end.
In the end, unifying the detection teams & tools make sense as attacks are not necessarily exclusively IT or OT.
Link with industrial sites
Response time & information sharing is crucial in cyber incidents. As most security teams are centralized in a unique location, there is a need for a link between central security teams and local industrial sites in cyber incident response process:
- This relay is familiar with industrial sites, their specific characteristics, operational context, and modes of functioning
- They also maintain contact on-site to quickly gather the information required for triage, doubt resolution or investigation
- In addition, in global organizations, having resources in the right time zones and ability to communicate in the local language is key, especially in the industrial world
Referred to as Cyber-OT Referents, these relays play an active role in the incident resolution process, particularly during investigation and remediation:
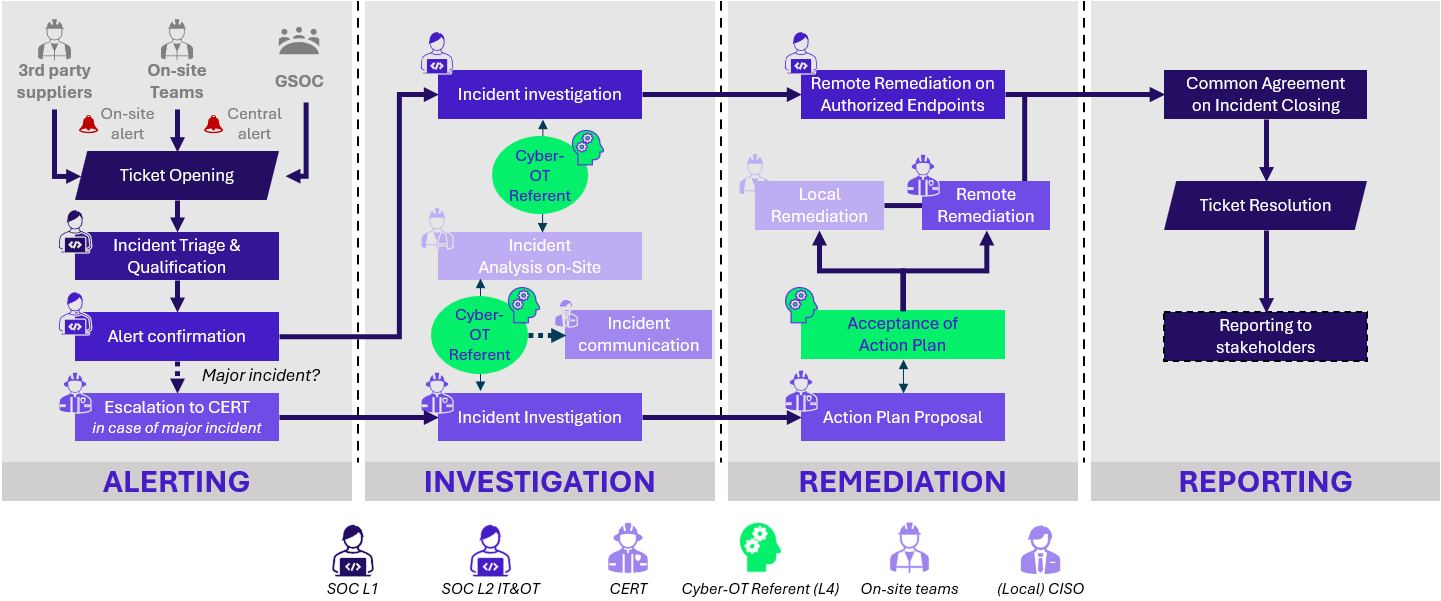
In conclusion, even though unified SOC covering IT and OT are often driven by cost optimization, the model makes sense considering that many threats span both domains. Still, this must not be treated as a simple extension of the perimeter to cover, dedicated OT relays and expertise are essential to properly handle industrial-specific contexts.
Tooling
When it comes to tooling, we observed that 100% of our clients have detection tools deployed on the IT side. However, only one-third extend monitoring down to the lower layers of the industrial environment.
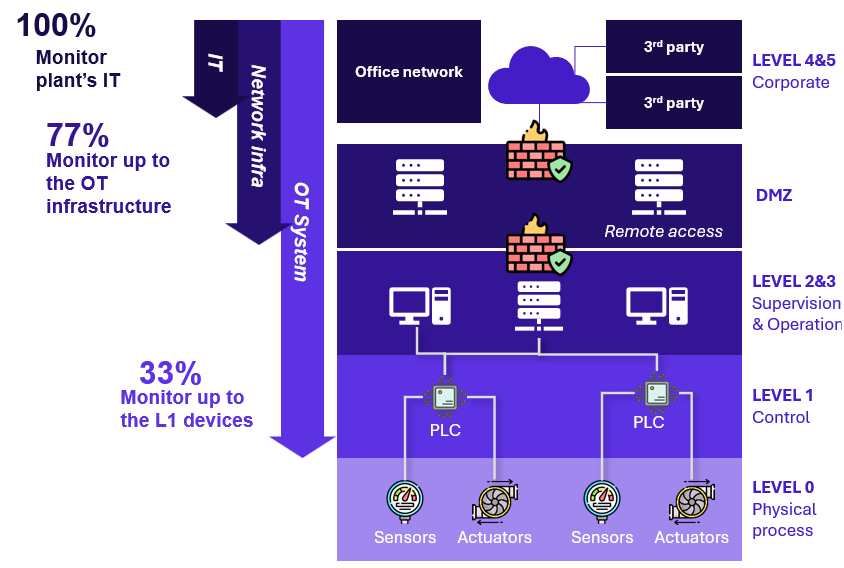
Detection sources covering different levels of the Purdue model
We will focus on popular solutions to address detection in industrial environments: EDR and OT probes.
2.2.1 EDR
Few figures regarding EDR:
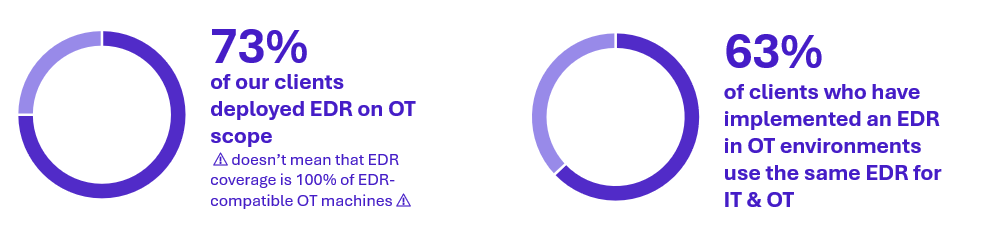
Most of our clients have started deploying EDR in their industrial environments.
However, this does not mean that 100% of EDR-compatible OT machines are covered.
For environments that support it, extending EDR coverage allows to:
- Address low maturity: Start with tools that are easier to implement and require less maturity.
- Broad coverage: Focus on quickly covering a wide range of systems, sites, and critical applications.
- Leverage IT tools: Use IT-based solutions like EDR for effective detection without heavy infrastructure requirements.
To do so, most organizations opt to use the same EDR solution for both IT and OT environments. It enables faster rollout thanks to a known and already-integrated tool. Depending on needs and available resources, a different solution may be selected to improve resilience and OT-compatibility.
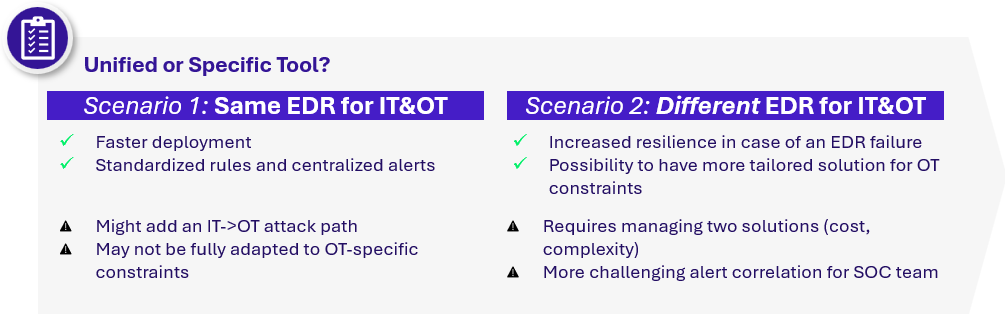
To conclude, with IT/OT convergence, deploying EDR Agents on OT Servers and Workstations is becoming increasingly relevant, and a quick win for OT detection, according to our clients’ feedback.
OT Probes
Few figures regarding probes:
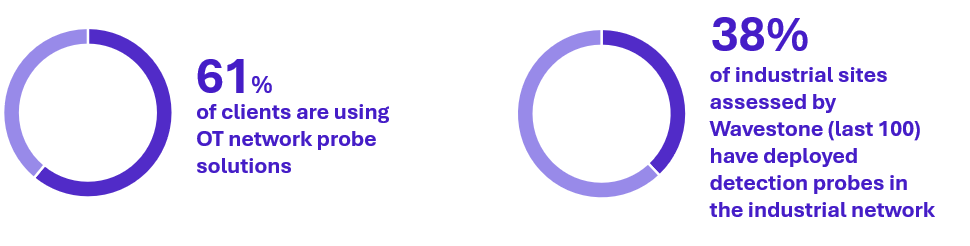
When it comes to probes, the gap between these two figures highlights the challenge of deploying probes at scale and effectively using them for detection in industrial networks.
Indeed, probes collect and correlate information through network traffic capture. To be effective, their deployment requires carefully selecting listening points based on the intended targets. Listening points need to be tailored to each site architecture, often limited by local team’s knowledge and lack of documentation.
Operating these probes also comes with challenges and requires a significant workload. They tend to generate a high number of false positives, which means teams must create tailored detection rules and playbooks to filter and respond effectively.
In the end, OT Probes may be popular, but deployment and tuning costs and resources limit their full utilization.
Start basic with OT detection tools
In the end, for OT detection, we believe in starting basic by leveraging “IT” tools to ensure a first level of coverage across all sites, critical apps, and infrastructure:
- Prioritize critical assets: Focus on key systems (MES, safety tools, network) essential for production, ensuring they are closely monitored before extending deployment to the lower levels of the Purdue model.
- Implement basic detection: Establish foundational detection across sites and infrastructure for early issue identification, before advancing to complex OT solutions.
Training & Testing
Detection does not rely on deploying tools alone; we will focus here on team’s ability to use them effectively.
A need for more OT-specific knowledge
Benchmark figures revealed a limited understanding and adaptation of both teams and processes to industrial environments:

To bridge the gap, teams need training tailored to industrial contexts, basic for all SOC analysts, and in-depth for OT specialists.
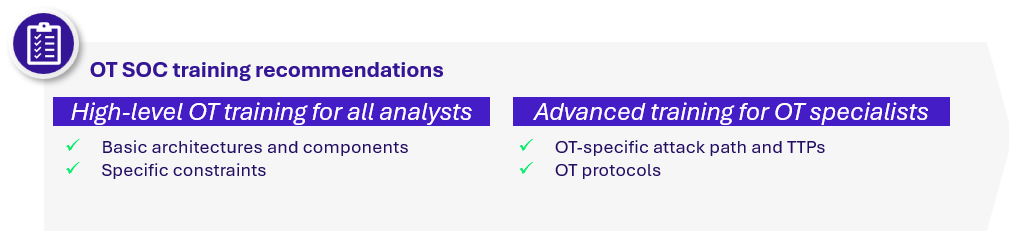
In the same way, investigation and response processes must also be adapted to address the specific needs of industrial environments, where priorities such as availability differ from those in the IT world.

Test your detection!
Finally, improving detection starts with evaluating it but today …
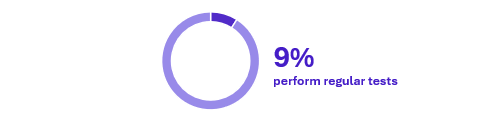
Only a small minority test their real detection capabilities, but we believe that there is room for purple team exercise in OT. These collaborative exercises with the OT SOC, tailored to its maturity and goals, can test and enhance both detection tools and OT SOC processes.
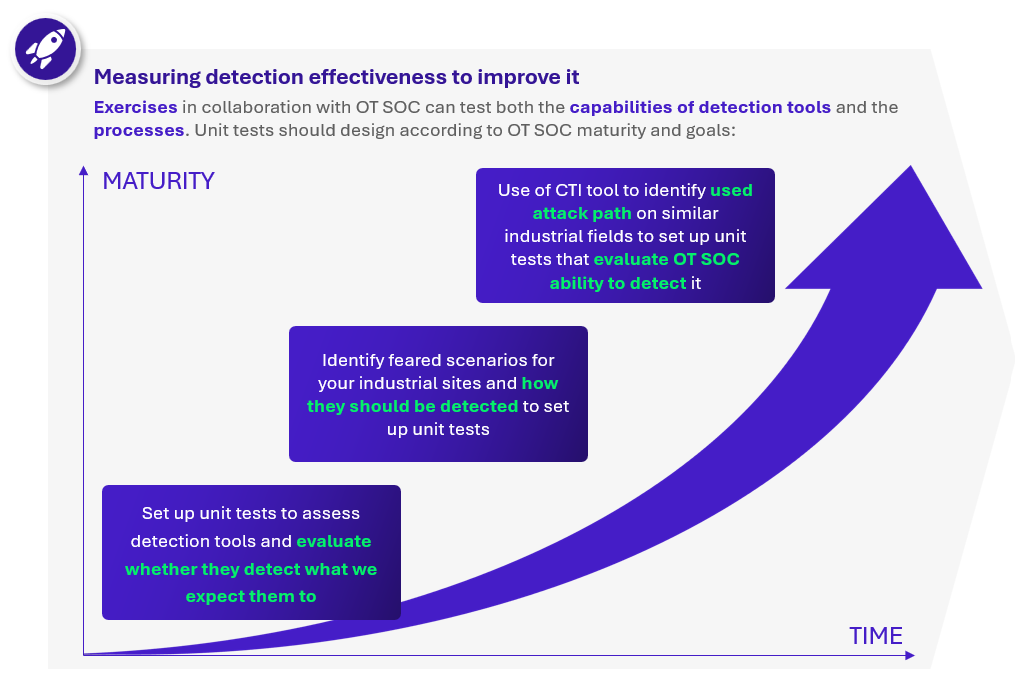
It can start simple: by selecting appropriate production environments and performing a few basic tests like inserting a USB key with a standard malware sample or attempting a couple of privilege escalation actions… we can evaluate whether the EDR deployed on a workstation connected to your SOC will trigger an investigation.
This exercise helps identify the blind spots and adjust tooling, process and playbooks accordingly.
Conclusion: How to enhance the overall low maturity in detection for industrial systems?
The benchmark’s first conclusion is clear: maturity levels are low, and this is a consistent answer across all collected responses. How to enhance this overall low maturity in detection for industrial systems?
Here are the key outcomes regarding the three topics covered in this article:
Do not hesitate to reach out to discuss how you can strengthen your detection capabilities and measure your maturity against the market!