Detection within industrial environment
In a previous article: Cybersecurity monitoring for OT, Current situation & perspectives we have seen that OT, while overall less impacted than IT, is not exempt from cyberthreats & not immune to cyberattacks. But, due to the difficulty in updating legacy Industrial Control Systems (ICS), cybersecurity measures are often added after deployment. Continuous monitoring is seen as a practical substitute for built-in, cyber-by-design protection.
When it comes to monitoring tooling, we observed that 100% of our clients have detection tools deployed on the IT side of industrial sites. But only one-third extend monitoring down to the lower layers of the industrial environment:
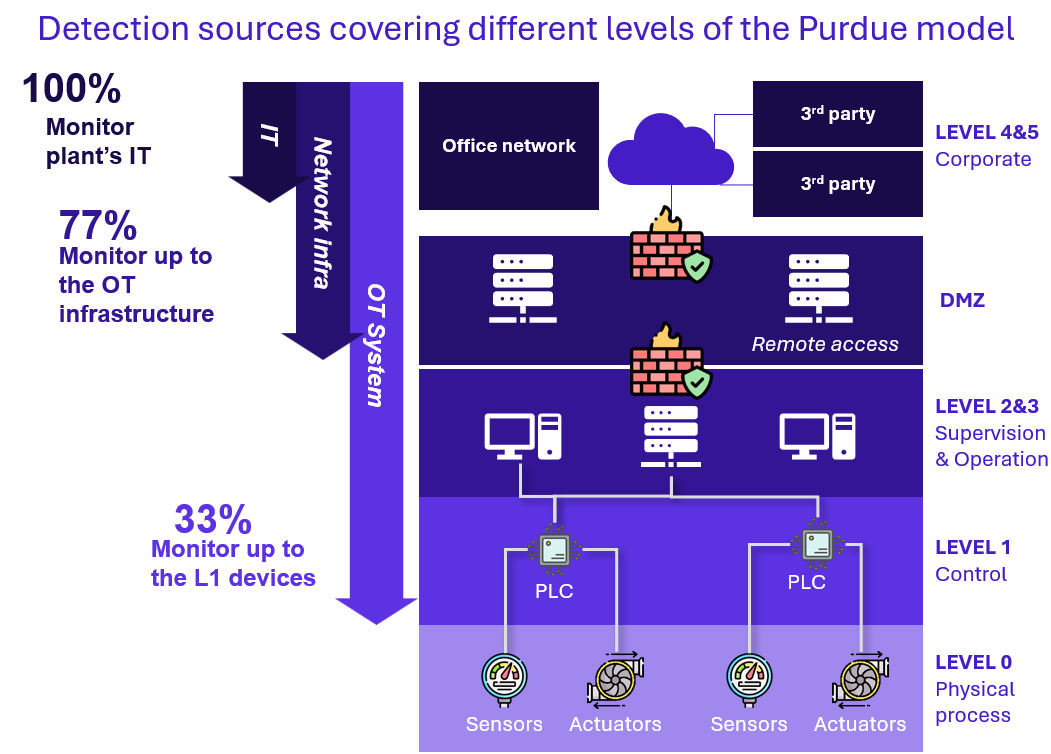
There is a large variety of detection sources allowing monitoring across different levels of the Purdue model:
- Firewalls (including industrial firewalls)
- Endpoint protection (AV, application whitelisting, EPP, EDR etc.)
- Authentication and access logs (e.g., Active Directory, local authentication)
- Remote access logs (e.g., VPN, jump servers, bastion)
- Deceptive technologies (e.g., honeypots or decoys)
- Network detection and monitoring probes (listening industrial networks)
- Logs from media sanitization or data transfer stations (e.g., USB kiosks)
- Industrial logs (from SCADA, HMI, PLC … when available)
Traditionally, these logs are collected and analyzed by SIEM and/or SOAR solutions, with or without specific OT detection patterns, and should enable the SOC team to detect, investigate, and respond to security events.
Building a consistent detection strategy for OT environments does not require collecting data from every possible source. In fact, a few well-chosen, properly configured, and actively monitored sources can provide strong visibility and early detection capabilities. The key is to focus on data sources that are both relevant to the specific OT architecture and feasible to monitor without disrupting operations. Prioritizing quality and operational relevance over quantity ensures a more effective and sustainable cybersecurity posture.
How to get the most of detection sources?
Start with logs you already have
A pragmatic and cost-effective way to approach OT detection is to start by leveraging the logs and detection patterns already available within the industrial environment, particularly those already exploited for your IT environments. For example, firewall logs, especially those monitoring IT/OT boundaries, can provide valuable insights into network traffic patterns, segmentation breaches, or suspicious remote access attempts. Similarly, Active Directory (AD) logs can reveal abnormal user behavior, failed authentication attempts, or privilege escalations — all of which are critical signals in both IT and OT contexts. Leveraging these existing sources allows organizations to build initial detection capabilities without heavy investment, while laying a solid foundation for more advanced monitoring in the future.
Rather than starting with deploying complex OT-specific detection tools, organizations should build initial detection capabilities using what is already deployed, configured, and understood. This not only reduces costs but accelerates implementation across industrial sites. The goal is to ensure a consistent baseline of visibility across critical applications, systems, and infrastructure before diving deeper.
By starting with what you already have, and focusing on coverage, not complexity, organizations can address OT detection with speed, relevance, and operational realism, while setting the stage for more advanced capabilities down the line.
We will now focus on the two detection tools most widely adopted and discussed in industrial environments today: EDR solutions and OT network detection probes.
In the following sections, we will examine how to leverage these solutions effectively and outline our recommendations.
EDR
Endpoint Detection & Response solutions provide continuous monitoring and analysis of endpoint activities to detect, investigate, and respond to cyber threats in real time. EDR collects detailed data such as process execution, file changes, network connections, and user behavior. By leveraging behavioral analytics and threat intelligence, EDR tools can identify suspicious activities like malware infections, lateral movement, or privilege escalation.
This detection tool, widely used and popularized in IT environments, is now being adopted by most of our clients for deployment within their industrial environments, driven by the evolution of deployment models, the broader coverage of operating systems, and the improved performance of detection models in increasingly complex environments.
However, this does not mean that 100% of OT devices are compatible with EDR solutions. In fact, EDR compatibility varies significantly across different industrial systems due to their diversity and operational constraints. EDR deployment is generally straightforward on higher levels of the Purdue model, such as Layer 3 and Layer 3.5, where systems resemble traditional IT environments like servers and workstations. At Layer 2, implementation requires careful evaluation with vendors support and testing, as devices and protocols become more specialized and resource constrained. Finally, at the lowest levels, controllers, PLCs, and field devices, EDR is generally not viable due to limited processing capacity, proprietary operating systems, and real-time performance requirements.
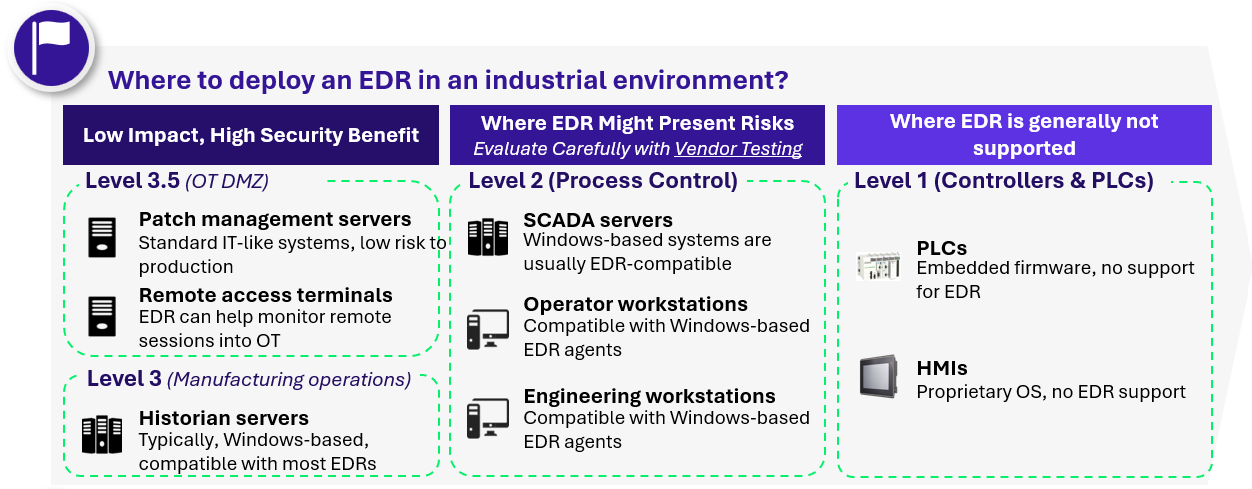
For environments that support it, extending EDR coverage allows to:
- Address low maturity: Start with tools that are easier to implement and require less maturity.
- Broad coverage: Focus on quickly covering a wide range of systems, sites, and critical applications.
- Leverage IT tools: Use IT-based solutions like EDR for effective detection without heavy infrastructure requirements.
To conclude, deploying EDR Agents on OT Servers and Workstations is becoming increasingly relevant, and a quick win for OT detection, according to our clients’ feedback.
OT Probes
A detection probe is a piece of equipment, virtual or physical, connected to the information system in order to map and monitor it. It consists of sensors distributed across the network to collect data. And typically, a central console to aggregate, correlate and analyze this data.
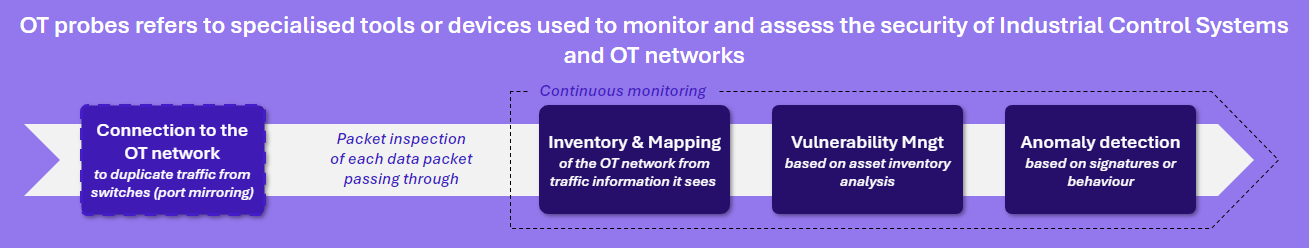
Probes for industrial environments, which we will refer to simply as OT probes here, are characterized by their passive, non-invasive listening on the network, and their understanding of industrial protocols and behavior. All their probe solutions work on the same principle: network traffic is collected using flow duplication (SPAN, ERSPAN …) or physical duplicator like taps, etc. Packets are inspected in real time to provide several types of data: flow inventory and mapping, asset and vulnerability management, and finally anomaly and incident detection. OT probes promises wide detection capabilities and variety of possible cases of these data. The features and types of users involved (operational and business team, cybersecurity team, etc.) is what makes OT probes so popular.
However, our clients often face significant challenges when it comes to deploying these probes and effectively leveraging them for detection at scale.
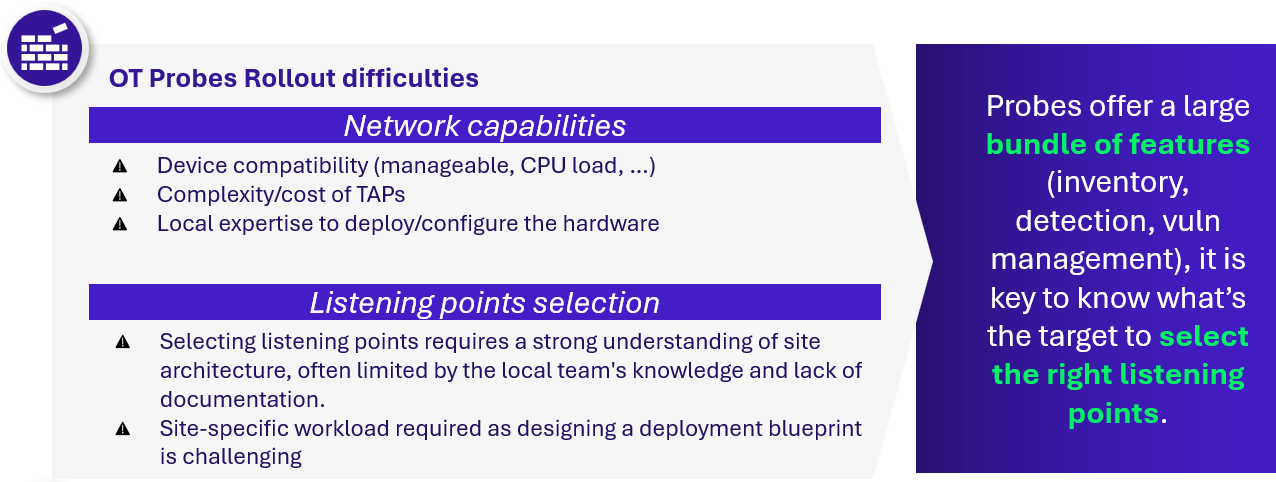
Here are a few common pain points when deploying OT probes:
- Industrial site network capabilities and resources: Deploying OT probes often presents significant challenges due to the limitations of industrial network infrastructure. Network taps and SPAN ports on switches, commonly used for traffic monitoring, are not always manageable or available in OT environments, which limits options for passive traffic capture. Additionally, the costs associated with installing dedicated network taps can be prohibitive, especially across distributed and remote industrial sites. Moreover, deploying and maintaining probes requires skilled resources on-site.
- OT probes collect and correlate information through network traffic capture. To be effective, their deployment requires carefully selecting listening points based on the intended targets. Listening points need to be tailored to each site architecture, often limited by local team knowledge and lack of documentation. Moreover, because industrial environments vary between different sites within the same organization, it is very difficult to establish a one-size-fits-all blueprint. In some architectures, achieving comprehensive asset coverage may require deploying dozens of collection points. As a result, selecting and configuring listening points is a repetitive, iterative process that must be adapted for each location to ensure optimal visibility and detection capabilities.
More than deploying, operating these probes also comes with challenges and requires a significant workload. They tend to generate a high number of false positives, which means teams must create tailored detection rules and playbooks to filter and respond effectively. On average, we estimate that one full-time SOC analyst is required to manage the alerts generated by 50 probes.
In the end, OT probes may be popular, but deployment and tuning costs and resources limit their full utilization. Our recommendation is to prioritize deploying OT probes for critical sites or within key network segments that demand advanced industrial and network monitoring capabilities. Deployment should also be aligned with the organization’s capacity to manage the associated tuning and operational workload. This approach helps maximize return on investment while ensuring effective detection where it matters most for our clients.
Consider other solutions?
Regarding detection for industrial perimeter, while this article focuses on key detection sources like EDR and OT network probes, it is important to acknowledge that other solutions such as deceptive technologies (e.g., honeypots or decoys) can also play a valuable role and be relevant in specific scenarios or environment according to your industrial sites architecture or feared compromission scenarios.
Conclusion
To conclude, here are the key recommendations to build an effective detection tooling strategy to monitor industrial environments :
- Leverage existing tools for immediate impact:
Begin by maximizing the value of detection sources already available in your industrial environment: firewall logs, active directory, remote access logs… and EDR, that can be quickly implemented on OT servers and workstations, offering high visibility with minimal effort. Adapting proven IT detection logic to OT use cases enables organizations to rapidly establish a baseline level of visibility without the need for heavy investments or complex integrations. This pragmatic approach ensures faster deployment and broader coverage of your OT assets.
- Deploy advanced solutions where you can manage the workload
When extending your detection capabilities, prioritize the deployment of advanced tools like OT network probes where they provide the most value. For network probes, focus on critical sites or segments, and carefully select listening points to balance visibility, cost, and operational overhead. This targeted deployment approach ensures resources are used efficiently and strategically.
- Prioritize quality and relevance over quantity
Building an effective OT detection strategy does not require monitoring every possible data source. Instead, focus on sources that are both relevant to your environment and technically feasible to collect without disrupting operations. This approach allows reducing log storage and management costs and enable the creation of more relevant, high quality detection rules.
Do not hesitate to reach out to discuss how you can build and improve your detection strategy to monitor your industrial assets!
In our next article, we will look at how to evaluate detection in industrial environments using purple team exercises, a practical way to assess and improve your detection capabilities.


