IAM on the cusp of change
In the context of IAM, organisations have traditionally focused on managing identities and controlling who accesses what (and how).
In terms of identity management, organisations first focused on automation of provisioning tasks and other low value tasks. The focus then gradually turned to access rights request and approval processes. More recently, organisations have turned their attention to accounts and access rights review and recertification.
In terms of access control, organisations have migrated from centralised authentication (e.g. in a shared directory) to delegated authentication (e.g. to a Web Single Sign-On (SSO) solution). We are now at a stage where authentication is standardised with identity federation protocols (e.g. SAML) equally applicable to SaaS applications as internally hosted applications.
In recent years, information systems have opened up to the Internet while at the same time their authentication has become more standardised: organisations must now contend with SaaS, IaaS, external Information Systems (IS) access by partners and clients, a mobile workforce and mobile applications. And IAM professionals have devised solutions for these new use cases without necessarily challenging the fundamental principles of the existing paradigm. In effect, the market has witnessed a gradual evolution. And whilst we are currently experiencing a relatively calm state of affairs, major change is brewing.
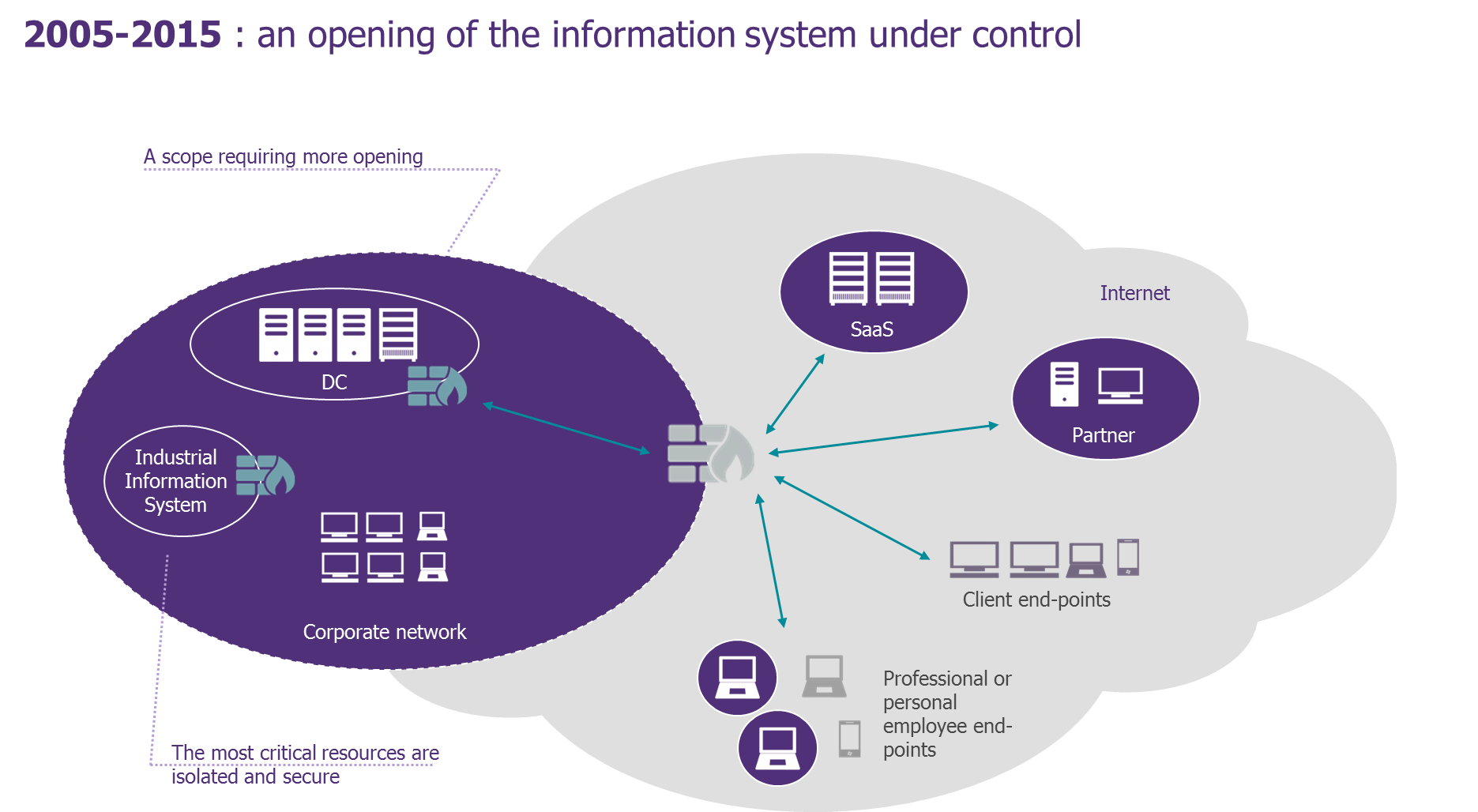
Figure 1: 2005-2015 – an opening of the Information System under control
The evolving ‘IS’ landscape influencing IAM
The IS landscape is undergoing a new wave of transformation;
Driven by Cloud adoption, we are heading towards further adoption of SaaS, majority use of IaaS relative to historic datacentres, real adoption of PaaS (in the form of containerised applications and server-less apps), and ever increasing remote access by employees. There is also a surge in the number of end-points accessing information systems (more customers whose interactions are digitalised, Internet of Things, OpenData, etc.).
And driven by new agile methodologies and DevOps, information systems no longer evolve in the same way. Development and deployment cycles have been considerably shortened and interactions between business lines and IT are less confrontational than they used to be. These new methods are increasingly the norm and it is difficult to resist them.
Although IAM’s primary goal has not changed much, namely controlling who accesses what in the IS, there will be many more variants of “who” and “what” in the future. Core IS will be merely one “bubble” among others (refer to diagram below) interacting with its wider environment and remotely controlling interactions between decentralised components.
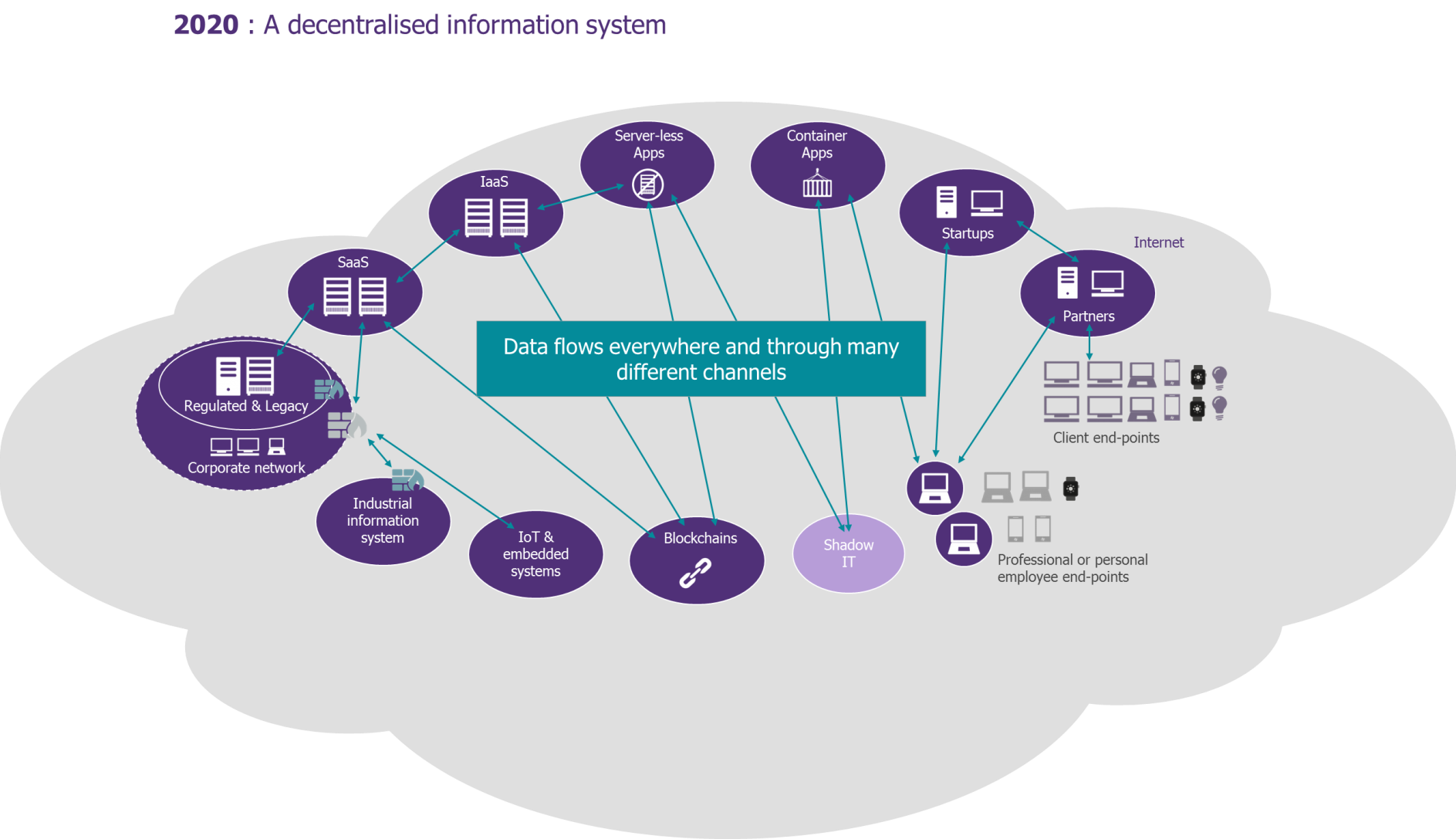
Figure 2: A decentralised Information System
7 factors shaping the future of IAM
IAM must find its sweet spot in a new environment where the requirements of business lines drive technology innovation. The business lines might even impose technology solutions onto IAM teams.
In predominantly cloud-based architecture, IAM must demonstrate control over this dynamic and bring added-value to this new world.
There are seven key factors that will shape the future of IAM; three of which relate to the needs of the business lines and four of which are new IAM challenges.
Agility
Business lines now expect to offer new products and services in ever-shorter timeframes. This poses two parallel challenges for IS:
- Maintaining quality of service for existing business line products, and
- Adapting to meet the need of new business line products.
This is an opportunity for IS to move away from a monolithic IAM framework that is often complex to implement and very difficult to handle by embracing a lighter architecture to support the new business demands (e.g. micro-services).
Client Identity Management (Customer IAM or CIAM)
Digital transformation is driving the business lines to interact with their customers in many new ways and through ever more channels.
A flawless user experience and the simplification of the customer journey are required. Optimisation of customer acquisition and churn rates become key indicators for CIAM to address.
Internet of Things (IoT)
Whether an organisation is building connected objects or offering services on top of them, a number of questions will become unavoidable:
- How to ensure that the object I am communicating with is the one it purports to be? Is it important to be absolutely certain?
- How to scale the IS to manage the growing volume of deployed objects?
- How to ensure end-to-end security?
- What object lifecycle should we anticipate?
These are fascinating questions which force us back to the drawing board to consider different hypothesis beyond the usual IAM framework.
Identity as a Service (IDaaS)
As we predicted a few years ago, the criteria for exporting IAM to the cloud is no longer restricted to security considerations. Equally important questions are: do I really need to do it? how will I benefit?
Although the IDaaS market is still in its infancy, with current offerings only partially covering the IAM spectrum, all indicators suggest the IAM offering of the near future will plug the gaps in the form of on-premises provisioning, rights requests and approval, identities governance, and more. What remains to be seen is whether identity management and access control will be packaged together or offered by separate providers and which provider(s) will be the most reliable.
Application Programming Interface (APIs)
APIs already represent a vitally important communication medium for any company committed to the digital transformation journey: exchange with partners, mobile applications, client-side applications, OpenData, etc.
Despite perceived gaps compared to web-service standards from previous years (in particular in the eyes of WS-* suite nostalgics), it is necessary to embrace the REST/JSON wave, to dive into Oauth2 and to bring up the API first topic in all your projects.
Standards
The fight between standards is eternal. Any standard used today is destined to be challenged and replaced later by another. However, this does not prevent good standards from emerging which, if adopted, can enable a correct response to IAM issues.
On the topic of access control, several standards and protocols for authentication, as well as propagation of authentication, are mature and already adopted by a large share of the market.
FIDO (Fast ID Online), U2F (Universal 2nd Factor) and OpenID Connect are amongst the most promising standards in terms of their adoption rate, the maturity of the underlying technologies and the players who have collectively created them.
Identity & Access Intelligence
This is probably the most exciting and fast moving IAM area. Machine learning algorithms, detection of weak signals, neural networks and other emerging technologies can lead to new use cases linked to user (or object) identity and behaviour. Examples include pre-emptive fraud detection and risk anticipation, even “closing the door” before someone attempts to enter. Whilst there is an element of science-fiction to some of the scenarios presented by vendors, this is nonetheless a vibrant and highly promising market.
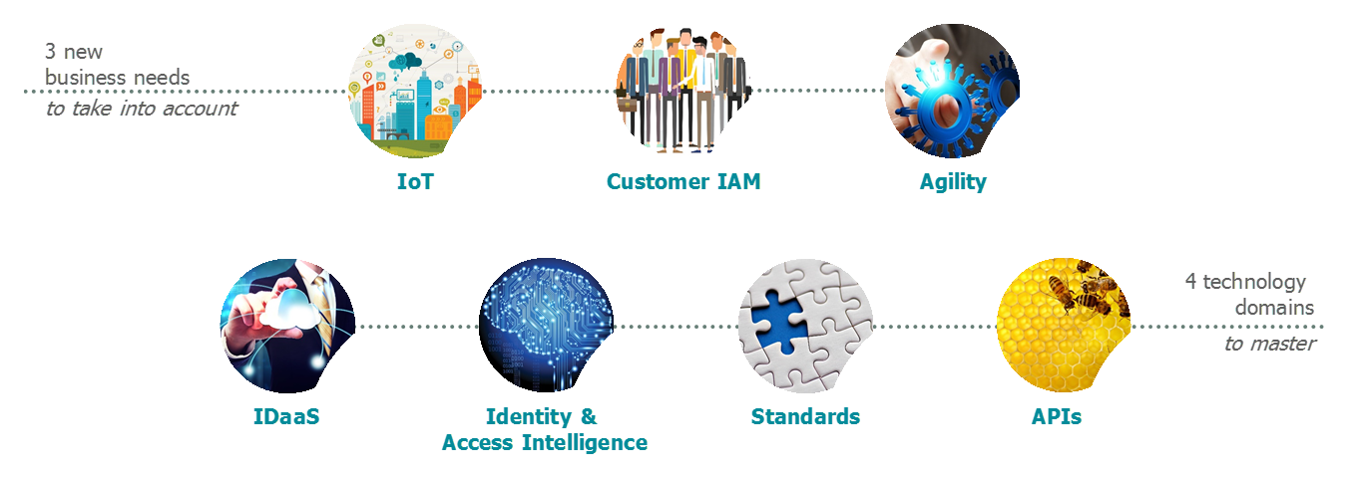
Figure 3: 7 factors shaping the future of IAM
Conclusion
Identity and Access Management (IAM) is developing at a fast pace as a result of new technology developments, digital transformation and the evolving cyber threats. Large organisations need to review their IAM strategy to take into account the current and future requirements of a digitally enabled business. Instead of focusing on “point” solutions to address these challenges one at a time, organisations need to take a more considered and holistic view of developments. An effective strategy can transform your IAM platform into an asset that enables mobility and productivity whilst also helping to overcome security challenges and integrate future IAM demands.


