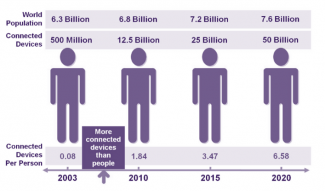
By 2020, the Internet will depend upon an ever-growing universe of connected objects and personal data, and will play an omnipresent role in our daily lives. These new technologies and possibilities are naturally attracting the attention of both regulatory bodies and cyber criminals alike. Security is a major challenge in view of the new threats expected to accompany the Web 3.0 as it evolves.
Changing Internet thechnologies and uses
At the user end, the uses that have emerged over the last decade will simply become more prevalent and will further expand by 2020. The growth and diversification of social media will make it possible to further accelerate the sharing of personal data with increases in technical efficiencies and the numbers of users. This phenomenon, profoundly generational in nature, might well continue to develop and therefore raise numerous questions relative to trusting in information and the limits of freedom of expression.
At the company end, as part of the ongoing virtualization of the workstation, teleworking is becoming an issue in the strategic roadmaps of many groups who see it as an opportunity to reduce property overheads that generally constitute their second highest budget item. Cloud Computing is growing and is leading to the integration of an ever greater share of the information capital of businesses by specialized service providers, especially in the security of infrastructures.
Finally, the IoT and Machine Learning will cause major upheavals to the business models and the positioning of historical players in all fields. 3 new societal needs will have to be taken into account in order to remain competitive: mobility, knowledge and trust.
A regulatory framework yet to be defined
The recent demonstrations of the power of the GAFA, capable of combining gigantic databases of users with leading edge artificial intelligence methods, are ushering in a new era devoted to the ultra-personalization of services, but also to mass monitoring. In fact, the immense opportunities opened up in the area of marketing through the ultra-personalization of services and mass monitoring hide a more alarming reality: a regulatory framework that provides less than adequate protection for Internet users confronted with the abusive and discriminatory practices of public and private players alike.
Given the situation, “intelligence acts” are emerging in many western countries in an attempt to impose standards on the already widespread practices of these services. Begging the question of the individual freedoms being under threat because of the pretext of the fight against terrorism, these laws are regularly adopted despite the protests voiced by civil society.
After a number of revelations about the activities of the NSA in Europe, the European Union decided, in October 2015, to overturn the Safe Harbor agreement that had until then allowed the United States and Europe to freely exchange data, considering that its partner across the Atlantic was no longer able to guarantee a sufficient or adequate level of data protection. To fill the legal void surrounding the use of personal data, the GDPR is the new benchmark law for personal data protection in Europe, applicable by the 28 member states as of spring 2018. The law will actually protect users to the detriment of companies who will at best see their potential usage reduced to a need to seek “explicit and positive” consent. Similarly, the European NIS Directive for the security of digital services, will gradually be transposed into national legislation, including in France in connection with the military programming law.
Finally, the recent tussles between the giants of the web and the American administration have proved the government’s inability of imposing on Apple and Google the enforcement of the Patriot Act. This has enabled these players to claim a certain primacy in the respect for individual freedoms and a certain autonomy from political bodies, which had previously been the sole arbitrators in these types of situation. There is a slow but definite shift in the historical balance of power, with state authorities losing out to the major players in the economy, and it is as yet very difficult to say where this will all lead.
Therefore, two factors will have become decisive by 2020, and even after that, in adapting to the technological age: innovating and surviving beyond the rapid evolution of the rules of competition. On the one hand, a comprehensive knowledge of the regulatory limits and constraints, and on the other hand, an ability to make the most of the available data without crossing the legally authorized limits. The whole challenge in the future environment based on the Web 3.0 will therefore be to build and maintain a relationship of mutual trust with both customers and stakeholders, particularly government.
New threats in cyberspace
As part of a forward-looking study aiming to establish how cybercrime might evolve by 2020, a committee of experts has announced the types of recurrent threats to be expected by private enterprise and individuals. The primary threat to businesses will be attacks on the availability of their systems, such as denial of service, the theft of strategic data for sale to the highest bidder, and attacks on the corporate image (disinformation and denigration campaigns). For individuals, the most important threats to consider are scams and misappropriation, to which must be added attacks on alarm and home automation systems in support of physical intrusions.
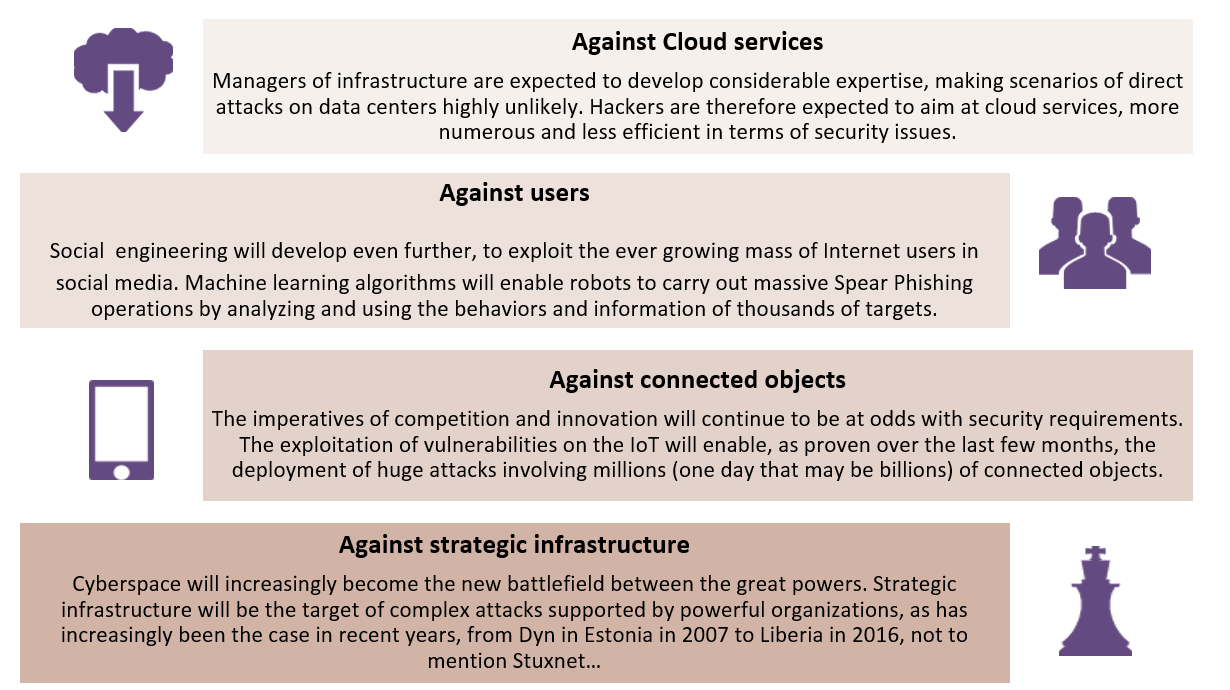
Two scenarios will become widespread and will feed into each other to become characteristic of the overall landscape of threats in 2020:
- The “attack as a service” The rapid and continuous growth of the number of connections to the Web will lead mathematically to the opening up of a very broad area to attack. Non-targeted attacks, or those based on networks of slave machines (machines controlled remotely by a hacker and used in large numbers to saturate web services, for example) could be deployed on massand achieve such a level of firepower that we cannot currently even begin to imagine it. A study conducted by university academics in Israel has estimated that 6,000 smartphones would be enough to destroy an emergency call system such as 911 in the United States; what then, might not be achieved with a network of millions, or even billions, of objects infected by Botnet malware (malware that allows a hacker to remotely control the infected machines)? These attacks are of low complexity, but massive impact.
- Economic warfare A context of extreme competition between the major economic players in industrialized countries will lead to higher levels of “geostrategic” threat. The Internet will become a new battlefield on which will be played out the economic and political interests of nations. The threats will be targeted and will range from acts of sabotage, as was the case with the Stuxnet virus, to industrial espionage. These offensives could reach high levels of complexity and will be implemented by teams of professionals with the benefit of various forms of protection and extensive, or even unlimited, financial and operational resources.
With Cloud Computing and connected objects becoming more widespread, the digital uses currently emerging will be commonplace by 2020. New threats are expected to accompany this evolution, less targeted at businesses and individuals and more at governments . The legislative framework, subject to major change, is currently designed as much to protect Internet users as to support businesses, and where the balance of power will end up is anybody’s guess.


