>>Editorial: What to remember from 2017?
Industrial Control Systems (ICS) are complex systems that aim to control industrial processes. ICS can be found in several sectors: energy, nuclear, transport, chemistry… In brief these systems control many of the critical productive assets of companies or states making their compromise by adversaries a high risk on the environment or people’s lives.
Thus, the cybersecurity of these systems is crucial. Moreover, securing these systems may be challenging due to their complexity (mainly because ICS are a mix of technologies and their lifetime is longer than usual information systems’).
In order to meet our clients’ needs and answer to their future concerns, Wavestone has been conducting an ICS cybersecurity watch where every recent study, attack or incident and report regarding the security of Industrial Control Systems are studied. In 2017, more than 80 news were reported from which we can retrieve a lot of teachings.
So, what did we notice this year?
First of all, ICS had its share of attacks. However, this year’s attacks, more than the other years’, had an unusual worldwide impact. Indeed, while ICS attacks were usually localized on a device (for instance on health devices), factory (for example a cryptomining malware found in a water utility – for more information see below) or a region (Dallas emergency sirens ignition in April 2017), 2017’s attacks started locally and spread quickly impacting several production lines in the world (WannaCry and NotPetya).
During 2017, many attacks have been reported in the news. Moreover, we noticed that several national agencies, governments or political figures alerted on ongoing attacks or attempts on critical infrastructure. The sector that was the most targeted seems to be the Energy sector. Indeed, several news were reported from Turkey (in January), USA (in March, July), Baltic States (in May), UK (in July) and Ireland (in July) showing that this sector was a privileged target by hackers (state sponsored or not).
The energy sector wasn’t the only hot topic of the year, as a matter of fact, autonomous cars cybersecurity hit many times the headlines (even if that topic may or may not be considered as related to industrial control systems). This is mainly due to the fact that cars’ cybersecurity is a new market. Therefore, cybersecurity experts and researchers try to find vulnerabilities and exploits (for example vulnerability found in airbag control units), while car manufacturers launch partnerships and initiatives showing that cybersecurity is now one of their main concerns (for example GM invited ethical hackers to try and hack its cars).
Finally, the ICS cybersecurity market tends to grow as demonstrated by the several fundraisings and partnerships signed during this year. In a broader perspective, we can notice three kinds of actors in the ICS cybersecurity market:
- ICS cybersecurity companies: usually small-sized companies or start-ups. They are pure-players that develop and put in the market ICS-dedicated solutions (Sentryo, CyberX, Nozomi …);
- ICS vendors: we noticed last year, some vendors that conceive ICS launched partnerships with ICS cybersecurity companies to improve their systems’ security (for example Siemens-PAS partnership in September, Schneider-Claroty partnership in August);
- IT security companies: these companies (well known in the IT world) tailor their solutions for industrial context. They show a growing interest for ICS by publishing reports and attack analysis (for example Kaspersky, McAfee).*
So, what is coming next?
It may be easy to say that the ICS cybersecurity will still (unfortunately) hit the headlines. Especially with alerts of attacks targeting life threatening system such as the safety instrumented systems controllers. But, we may see more and more news on specific sectors such as maritime, transport, health… that weren’t somehow as exposed in the media as the energy or nuclear sector. The ICS cybersecurity market may continue to grow especially with partnerships and acquisitions. Industrial Control Systems will continue to face new threats, challenges and changes.
>>Latest news:
 |
CyberX raises $18 million in series B funding to combat rising threats to IIoT and critical infrastructure, bringing total funding to $30 million (CyberX, February 27th)
CyberX announced that the company raised $18 million dollars to develop threat detection in the Industrial Internet of Things (IIoT) and critical infrastructures. The company develops a threat monitoring and risk mitigation platform that includes ICS-specific threat intelligence. Link to the press release |
 |
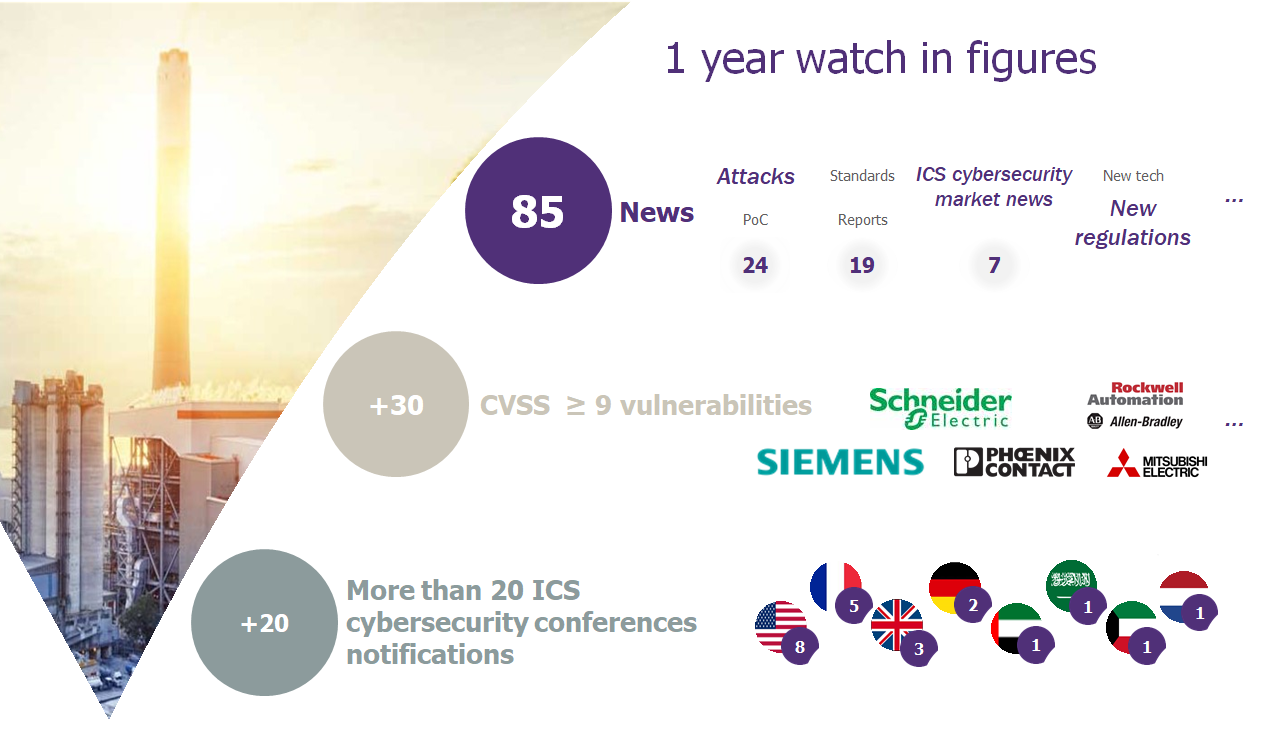
Fun with Modbus 0x5A (Security Insider, February 9th)
During the last edition of Defcon in Las Vegas, Wavestone presented its latest study regarding the ModBus protocol cybersecurity and specifically the function 90. An attacker may thanks to this function start, stop a controller or force it to send a determined output value, Link to the article |
 |
ICS detection challenge results (Dale Peterson, February 7th)
At the S4x18 in January, took place the ICS Detection Challenge. The 4 companies that completed the challenge are: Claroty, Gravwell, Nozomi Networks and Security Matters. The first part of the challenge consists on evaluating the ICS Detection class of 3 products which are: Claroty, Nozomi Networks and Security Matters. It was won by Claroty over Nozomi Networks and Security Matters. The competitors’ products had to detect cyber-attacks and incidents occurring on an oil&gas company. Link to the results The second part which consists in the asset detection phase was also won by Claroty even though Nozomi provided the most details in their asset inventory. Link to the results |
 |
Water utility in Europe hit by cryptocurrency malware mining attack (eWeek, February 7th)
The security firm Radiflow discovered a cryptocurrency mining malware in the network of a water service provider in Europe. The malware was downloaded from a malicious advertising site infecting the Human Machine Interface and then spread to the SCADA network that was still running Microsoft Windows XP OS. The malware degraded the system performance. Tough the degradation wasn’t noticed by the operators. Link to the article |
 |
Ukraine power distributor plans cyber defense system for $20 million (Reuters, February 6th)
Ukraine’s state-run power distributor Ukrenergo, which was a target for cyber-attacks in the past two years (December 2016 and December 2017), will invest up to $20 million in a new cyber defense system. The acting head of Ukrainian state power distributor Ukrenergo, told that the company and international consultants had identified about 20 threats that would be eliminated with the new system. The main goal of this system is to make “physically impossible for external threats to affect the Ukrainian energy system”. Link to the article |
 |
Increasing number of industrial systems accessible from web (study Security Week, February 2nd)
According to a new report published by Positive Technologies, the number of industrial control systems (ICS) accessible from the Internet has increased significantly during the past year. Most of vulnerabilities of these systems could be exploited remotely without needing to obtain any privileges in advance. The most common types of vulnerabilities were remote code execution (24%), information disclosure (17%), and buffer overflows (12%).Most of these systems are accessible via HTTP, followed by the Fox building automation protocol associated with Honeywell’s Niagara framework, Ethernet/IP, BACnet, and the Lantronix discovery protocol. Link to the article | Link to the report [PDF] |
 |
Flaws in gas station software let hackers change prices, steal fuel, erase evidence (Motherboard, January 31st)
Security researchers were able to connect to a web interface that manages gas station thanks to Shodan (search engine of connected devices). After using the default admin login and password, and then a hardcoded username and password, the researchers were able to shut down fuel pumps, hijack credit card payments, and steal card numbers. Link to the article |
 |
Government warns critical industry firms to prepare for cyberattacks (Sky news, January 29th)
All companies which are involved in critical industry and essential services, such as energy, transport, water, health and digital infrastructure, have been warned by the British government that they face sanctions if they do not include cybersecurity rules in their systems.The fines come as the government implements the Network and Information Systems (NIS) Directive, which would cover events such as the WannaCry attack. Link to the article |
 |
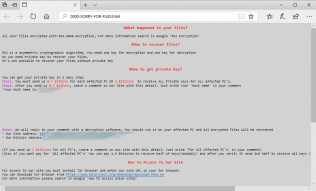
Gemalto licensing tool exposes ICS, corporate systems to attacks (Security week, January 22nd)
Kaspersky Lab researchers found 14 vulnerabilities in Gemalto Sentinel LDK (software) and the associated USB Dongle (SafeNet). The USB dongle is used to activate the software. When connected, drivers are installed and the port 1947 is added to the list of exceptions in the Windows firewall. This port can be exploited to identify remotely accessible devices. Link to the article |
 |
SamSam ransomware hits hospitals, city councils, ICS firms (Bleeping Computer, January 19th)
Samsam ransomware hit several hospitals, city councils and an ICS firm. Hancock Health admitted paying the ransom ($55.000) even though they had backups. The Samsam ransomware spread by brute forcing RDP connections. Link to the article |
 |
Industrial systems scrambling to catch up with Meltdown, Spectre (The Register, January 18th)
Meltdown and Spectre vulnerabilities also had an impact on industrial control systems. Some vendors decided to publicly communicate about their vulnerable products (OSISoft for example), other vendors like Emerson and General electric keep the information only for their customers and finally some vendors are still investigating if their products are vulnerable to Meltdown and Spectre. Link to the article |
 |
Researchers find 147 vulnerabilities in 34 SCADA mobile applications (SC Magazine, January 11th)
IoActive and Embedi researchers found 147 vulnerabilities in 34 mobile applications used in tandem with Supervisory Control and Data Acquisition (SCADA) systems. The top vulnerabilities were: code tampering flaws, insecure authorization, insecure data storage… This security weaknesses could allow an attacker to compromise industrial network infrastructure by exploiting the vulnerable applications. Link to the article |
 |
Industrial Cybersecurity Firm Nozomi Networks Raises $15 Million (Security Week, January 10th)
Nozomi is an industrial cybersecurity firm that has recently raised $23.8 million. Nozomi’s offering which is “SCADAguardian”, consists on using machine learning and behavioral analysis to detect zero-day attacks in real-time. This technology allows rapid response to alerts by ICS incident alerting and notification systems. The company said the additional funding will be used to support worldwide expansion of marketing, sales, support and product innovation. Link to the article |
>>Main ICS vulnerabilities
| Date | CVSS v3 | Equipment | Vulnerability | Advisory |
| Feb. 15th | 9.8 | Nortek Linear eMerge E3 Series | Command Injection | Link |
| Feb. 15th | 9.8 | GE D60 Line Distance Relay | Stack-based Buffer Overflow, Improper Restriction of Operations within the Bounds of a Memory Buffer | Link |
| Feb. 13th | 9.8 | Wago PFC200 Series | Execution of some unauthenticated commands such as reading, writing, or deleting arbitrary files, or manipulate the PLC application during runtime. | Link |
| Feb. 8th | 9.9 | Gemalto Sentinel License Manager | Null Pointer Dereference, Buffer Overflows, Improper Access Control. | Link |
| Feb. 1st | 9.8 | 3S-Smart Software Solutions GmbH Codesys Web Server | Stack-based Buffer Overflow. | Link |
| Jan. 25th | 9.8 | Nari PCS-9611 | Improper Input Validation. | Link |
| Jan. 11th | 9.8 | Phoenix Contact FL Switch | Improper Authorization, Information Exposure. | Link |
| Jan. 9th | 9.8 | General Motors and Shanghai OnStar (SOS) iOS Client. | Cleartext Storage of Sensitive Information, Man-in-the-Middle, Improper Authentication. | Link |
>>Recent and upcoming ICS events
|
Apr. 24-26 |
ICS Cyber security
London, UK |
Apr. 24-26 |
Industrial control systems (ICS) Cyber Security Conference
Singapore |
Apr. 9-10 |
Cyber Security for critical assets MENA
Dubai, UAE |
Mar. 27-29 |
Cyber Security for Energy & Utilities
Abu Dhabi, UAE |
Mar. 13-14 |
Maritime Cyber Security
London, U.K |
Mar. 6-7 |
Cyber Security for critical assets USA
Houston, USA |



