For several years now, we’ve been supporting the far-reaching changes affecting industrial information systems which are being increasingly forced to open up to the broader market and corporate IS technologies. As levels of exposure and threats increase, carrying out security maintenance, in coordination with a company’s business functions, is becoming critical. What can we learn from experience in the field and what are the good practices for the protection and security maintenance of industrial ISS?
Opening things up to corporate ISS is now a necessity… but it also carries risks
Historically, industrial ISs were not connected to corporate ISs, either because there was no need or as a way of limiting the risk of exposure. The majority of interventions were local, with work taking place directly on equipment, or remotely, using specific methods. The management of this work and the operations themselves were mostly local too.
Business functions’ changing needs and the optimization of production processes have brought with them new and less localized requirements (such as remote supervision, remote maintenance, the emergence of the IoT1, the standardization and rationalization of technologies and skills, cyber threats, etc.), which are designed to improve performance and facilitate operations. These challenges have led to a need to digitalize and interconnect industrial and corporate ISs.
Although this is now essential for a company’s business functions to operate effectively, our discussions with operational staff highlight the fact that such changes have also led to risks of intrusion and the propagation of threats between these interconnected ISs. These affect:
- Operations and quality – with potential shutdowns and modifications to production lines resulting in financial, reputational, and even people impacts;
- The security of facilities, where production equipment being seriously compromised can have impacts on both people and the environment.
Mitigating these intrusion and propagation risks and their consequences means implementing security measures in several different stages:
- Industrial IS mapping;
- Putting in place secure network architecture;
- The hardening and security maintenance of the various systems over time;
- And, lastly, putting in place the measures to detect incidents and respond to them.
Regulatory authorities have also been considering these risks. For the most sensitive installations, they are now mandating these types of measures and others too.
Interventions (such as patch management, account audits, integrity control, etc.), sometimes done remotely and often frequently, may now need to be carried out by teams more distant from site operations. These quickly come up against a traditional operating model designed to prioritize the continuity and integrity of operations, quality, hygiene and safety – while minimizing disruptions to production.
How can these measures be implemented without losing sight of the industrial IS’s core purpose – to operate a physical process in the way designed?
Mapping, a prerequisite for dealing with cybersecurity risks on industrial ISS
To assess the risks and control the potential impacts of implementing any new measures, the first step is the IS mapping of your industrial installations, which enables you to:
- Know the systems that need to be administered and kept up to date;
- Identify the users (operators, maintainers, etc.), and therefore those who need to be involved when a change takes place, to manage the operational impacts;
- Evaluate the potential impacts of new vulnerabilities and security breaches in terms of safety, operations, and quality.

Once the mapping process is underway, you will also need to develop formal procedures for updating the map. This means defining the update frequency, according to the level of criticality, and then actively managing the risks.
This is a substantial piece of work requiring dialog and close collaboration with automation and other engineers involved with the installation.
Mitigating risks on an industrial IS by putting in place security architecture
Security isn’t a new concept and it makes sense to follow the established principles for corporate IS architecture and security – adapting them to the particularities of industrial ISs:
- Reducing the risks of propagation and intrusion by clearly partitioning the industrial IS and restricting access to it;
- Securing the administration of the IS by putting in place dedicated administration architecture;
- Equipping administrators with appropriate tools that enable them to make interventions across the entirety of the industrial assets;
- Integrating from the start (as far as possible) interventions made by external maintainers.
These four principles form the cornerstones of securing industrial IS architecture.
Partitioning, the first step in reducing exposure
Corporate and industrial ISs have essentially different goals: one is designed to facilitate the operation of a business (by providing messaging, management systems, collaborative tools, etc.), while the other is used to operate physical processes. In theory, these should be separated, and only certain types of information should be allowed to flow between them. However, feedback from the field tells us that this is rarely the case.
As in any work on IS security, the strict necessity principle should be adopted to limit exposure to cyber threats. Any interconnection between an industrial and corporate IS should serve a specific purpose; for example:
- Sending production orders to SCADA[1];
- Transferring CAM[2] files to digitally controlled machines;
- Collecting production data to enable the control of operations.

An industrial IS must also be internally partitioned to reduce the risk of threat propagation. To do this, you can use the principle of zones and conduits described in the IEC 62443 standard.
In practice, this partitioning has to be carried out in several steps:
- The listing of relevant business activities according to their different levels of sensitivity;
- Grouping activities requiring the same security level into zones (with, potentially, a ”legacy” zone and associated sub-zones);
- Putting in place security rules for each zone according to their needs, as described in standard IEC 62443;
- Checking that the interconnections (conduits) between the different zones comply with security rules;
- Migrating the applications. Ensuring applications are compliant can be a long and difficult task, and it’s best to use a risk analysis to prioritize and manage the work, as well as documenting the nonconformities and associated remediation plans. In addition, the migration process itself may be complex, if you are to avoid an impact on operations.

The particularity of safety ISS
Safety ISs are industrial ISs that enable industrial production systems to be put into a safe state. Before the advent of today’s digital systems, such systems had long been used in mechanical, pneumatic, and electrical forms. The particular importance of ensuring their integrity is therefore well understood. A final partitioning step can be considered to achieve this. However, field observations often tell us that existing arrangements act as a brake that complicates the work. When done rigorously, such separation reduces the risks of propagation and enables distinct levels of security to be implemented for the production IS and safety IS according to their risk levels. However, a disadvantage is that doing this requires a dedicated SCADA system, which is both expensive and not operationally friendly.

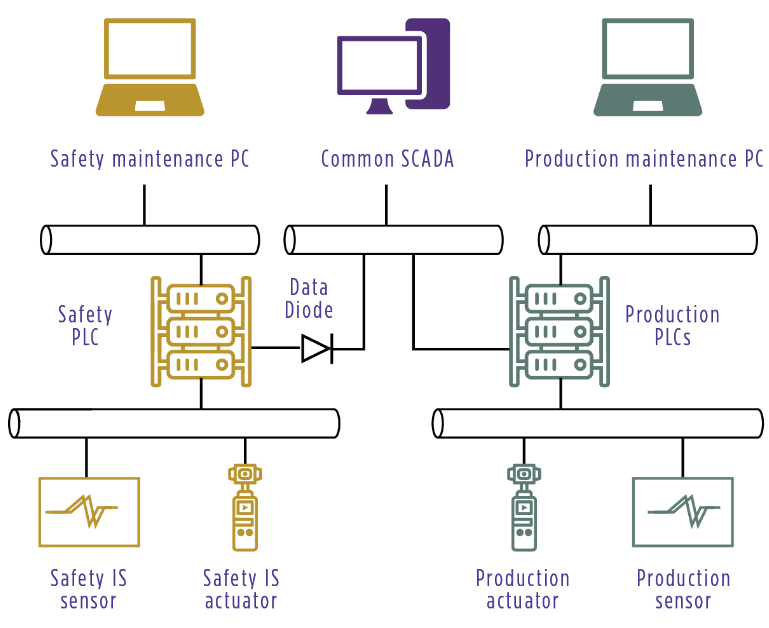
Diagram of Industrial IS / Safety IS partitioning scheme
After having launched this process of identifying and partitioning industrial IS, it is time to deal with their administration. How to reconcile security, operational gain and availability of the production tool? We will tell you about it very soon.
[1] SCADA i.e. Supervisory Control And Data Acquisition system
[2] CAM i.e. Computer Aided Manufacturing
[3] DMZ i.e. Demilitarized Zone.


