Smart City, a possible answer to today’s challenges
“A smart sustainable city is an innovative city that uses information and communication technologies (ICTs) and other means to improve quality of life, efficiency of urban operation, and services and competitiveness, while ensuring that it meets the needs of present and future generations with respect to economic, social, environmental and cultural aspects.», International Telecommunication Union (ITU) – United Nations Specialized Agency for Information and Communication Technologies.
Increase in the urban population, ecological emergency and energy transition, constraints on public finances, need to reinvent the link between the public service and the user, increase in the living comfort of the inhabitants, etc. All of these issues are challenges that the Smart City could help respond to and which are pushing communities to invest in this direction.
In order to meet these challenges of today and tomorrow, the Smart City will have to create a synergy between different areas such as intelligent traffic management, the development of new modes of transport, the optimization of energy consumption and waste management, the protection of goods and services, home automation, etc.
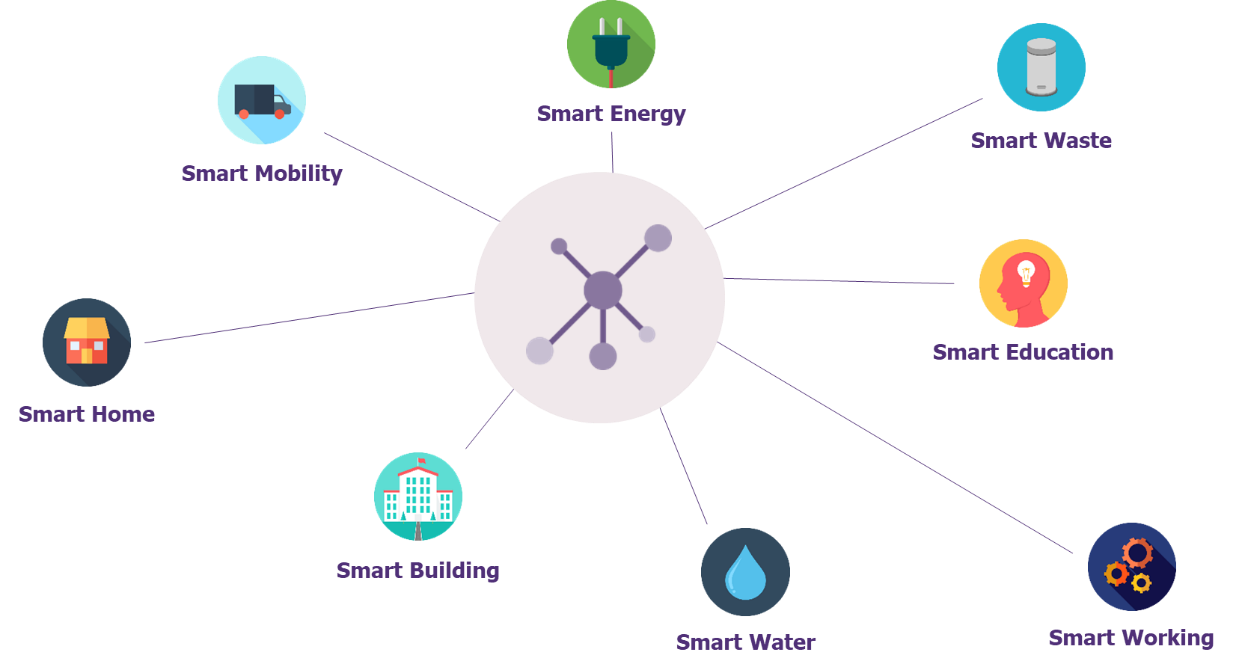
All these services can be federated around a single control center which will provide an uplink and downlink, giving the possibility of collecting information on the state of the services and/or acting directly on the infrastructure.
A new target for cyber attackers
Many cities in France and around the world have taken up the subject of the Smart City to meet the challenges set out above: large metropolises of course, but also smaller cities.
In parallel with these initiatives, it is becoming more and more frequent to observe cyberattacks targeting cities. As an illustration, in 2019, 22 US municipalities were victims of cyberattacks. The losses amount to millions. The governor of Louisiana went so far as to declare a state of emergency following attacks on several cities in the state. But these attacks are not limited to the United States, as evidenced by the attacks in France on the cities of Sarrebourg (Moselle), Sequedin (Nord), Huez (Oisans), La Croix-Valmer (Var) or even Nuits-Saint-Gorges (Côtes-d’Or).
So, the question now is why Smart Cities present a new playground for Cyber Attacks and how to protect oneself from them.
The Smart City induces a paradigm shift
Conducting a Smart City project requires changing the usual ways of proceeding by implementing a new kind of information system (IS), mixing many issues and generating new risks in terms of Cybersecurity.
A complex architecture
The Smart City is partly characterized by the new structure of its architecture. Its atypical IS compiles the constraints of a management IS, those of an industrial IS and those of an IoT IS.
Thus, its management IS will have a propensity to collect and process a large amount of data, whereas its industrial IS will have the characteristic of being directly connected to the physical world: water management, traffic lights, variable road signs, retractable bollards, intelligent lighting, autonomous car control, etc. and reconciling the challenges of these two worlds is no easy task: where the industrial world traditionally focuses on availability, the IT world will focus on the integrity and confidentiality of information and processing, considering furthermore that the Smart City will reinforce the existing IT and digital dimension of industrial systems.
Furthermore, the rationale for an IoT IS must be considered, which is to collect data as close as possible to their sources, through the deployment of connected objects, multiple entry points to the IS in potentially hostile environments. As a result, these objects will be individually exposed to physical attacks against which it was not previously necessary or easier to guard against (e.g. physical access to a serial or USB port, replacement of flash memory, etc.).
Finally, the systems that make up the Smart City must be able to evolve rapidly in order to benefit from the innovations of market players. The challenge is to succeed in building a flexible IS with the capacity to respond to uses yet unidentified today while providing systems capable of being maintained over time, on the scale of a Smart City built for decades.
The paradox of interoperability
Moreover, a Smart City approach is intended to be inclusive in order to take advantage of the strengths of all the players in the area. This implies managing heterogeneous systems, mixing new and old technological bricks, and mastering the opening of its IS.
Smart Cities polymorphism complicates the definition of global security policies. Their implementation evolves alongside the development of new technologies, making the security policies of another generation obsolete or inapplicable. This problem has already been present in the industrial world for years, where operational constraints make it sometimes impossible to evolve systems that have become vulnerable.
Beyond security policy, while interoperability between multi-generational systems makes it possible to develop new functionalities that create value for the user, it also implies using disparate protocols that can lead to security breaches. A “security by design” approach would consist in identifying the current need and its potential evolutions, in order to be able to propose specifications integrating both concrete answers to the functional need and minimum security rules allowing the service deployment with a satisfactory level of confidence. However, this is likely to oppose to the principle of inclusiveness of the Smart City.
The importance of data
An operational and political challenge
Information from the field is of paramount importance in driving the Smart City: assisting in decision-making, communicating information to citizens, planning events, and evaluating public policy. While the data itself is not necessarily critical, this is no longer true when it is aggregated into a larger whole. Errors in the collection or processing of data can lead to operational inefficiencies in services or to inappropriate choices in response to changing circumstances.
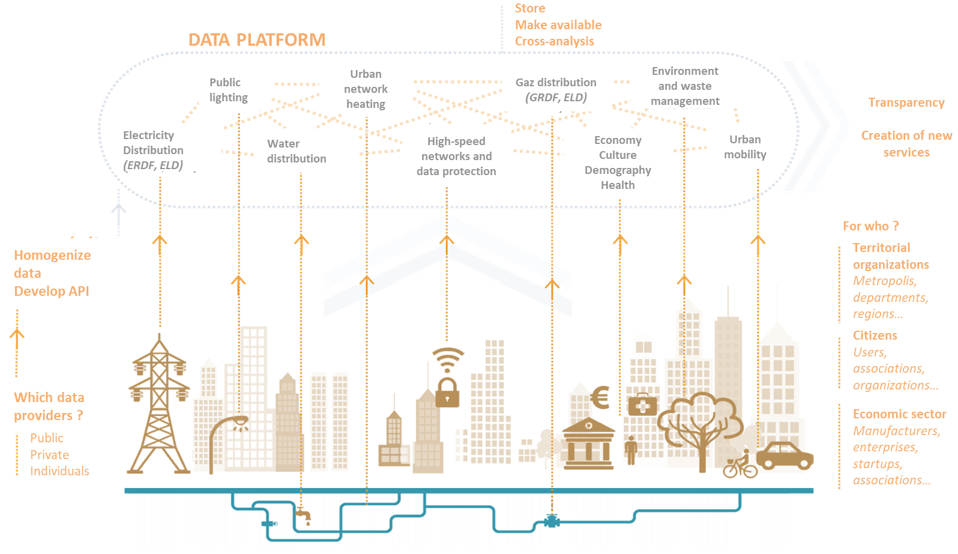
Moreover, the construction of the Smart City is done by layer. Gradually, new services appear and develop. Historically siloed, the trend is to look for synergies between the different services to create ever more added value for the user. These growing interconnections and overlapping induce such complexity that in the event of a failure, there is a risk, if we are not careful, of seeing the whole infrastructure collapse, either because of error propagation or because each service has become dependent on the others.
Security: a request coming from the citizens themselves
Elabe and Wavestone have conducted a survey on the importance of data in tomorrow’s public services, and on the challenges facing stakeholders in such projects.
Among these challenges lies the use made of the user personal data. Overall, citizens are in favor of the idea of digital transformation of public services, and a fortiori of the Smart City as a public service but remain concerned about the purpose of processing their data.
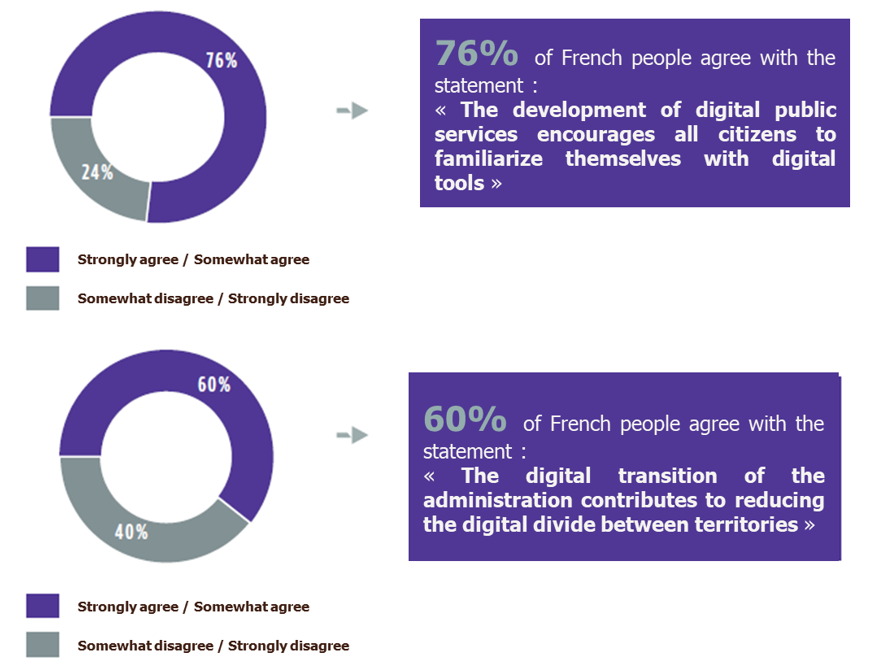
However, a significant proportion of the population, between 30% and 50%, is not in favour of transferring their data even if it could save money, save time or reduce their carbon footprint. This could be due to the fact that 76% of the population surveyed believe that the administration is not currently able to ensure the security of the data it collects.
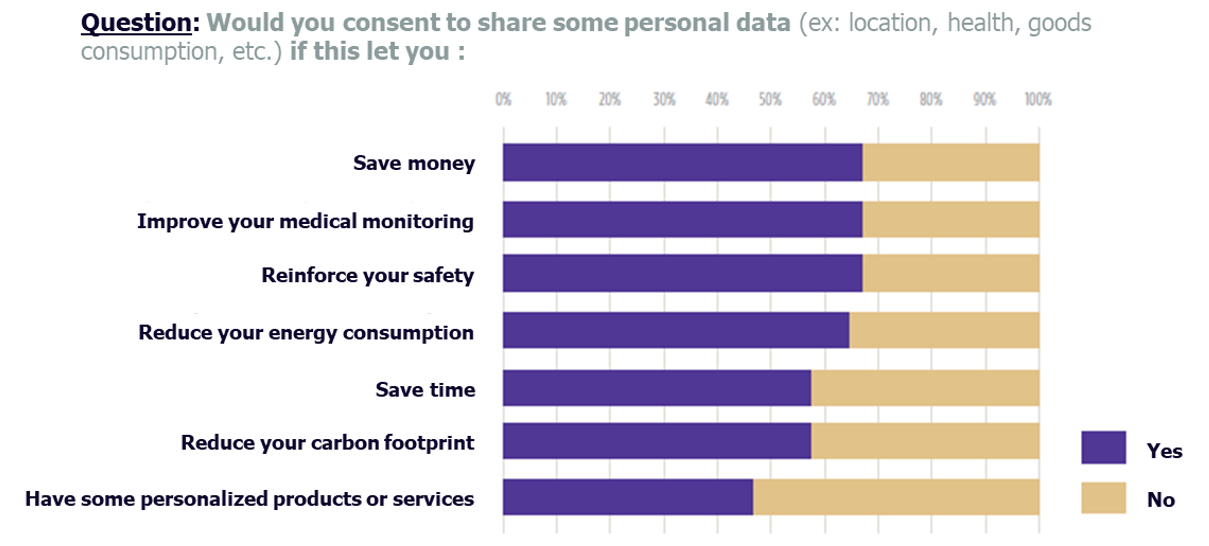
The success of the Smart City therefore also lies in the ability of stakeholders to reassure users about the use and protection of their data.
Thus, we have seen that the Smart City is inducing a paradigm shift which, combined with the high expectations of the general public on the security of its data, required an adaptation of its approach. Indeed, as the Smart City grows, urban activity becomes more and more dependent on its services, increasing its security needs, but also the interest of cyber attackers. Based on these observations, the challenge will therefore be to identify which approach to implement to take into account the risk of cybersecurity and, failing to completely eliminate it, to reduce it. We will talk about it in a second article.


