Who hasn’t already felt lost looking for information on Office 365 licensing? In this article, I will help you decipher the existing plans, as well as provide a few tips and reminders on recent announcements from the publisher.
In today’s modern workplace, it is essential for security and compliance teams to know the native capabilities of collaboration and communication platforms. This knowledge will enable them to define a coherent strategy that takes into account data protection needs as well as regulations, the urbanization of the information system and the unavoidable subject of user experience.
For companies using the highest licensing plan, Microsoft 365 E5, there is no problem: all functionalities are available. For others, the subject is much more complex.
This article is oriented for companies with more than 300 employees. For other organizations (education, associations, small and medium enterprises) the license plans are slightly different, but the information below is still applicable for most of them.
1/ Understand the security and compliance services available
Historically focused on office automation services (with Microsoft Office) and collaboration services (with Exchange and SharePoint on-premise), Microsoft’s offering has evolved strongly by integrating not only codeless application development services (with the Power Platform), but also security and compliance bricks.
These can be grouped into seven categories:
- Security: Identity and Access Management, Endpoint Management and Threat Management;
- Compliance: Information Protection, Governance, Service Control, and Cloud Control.
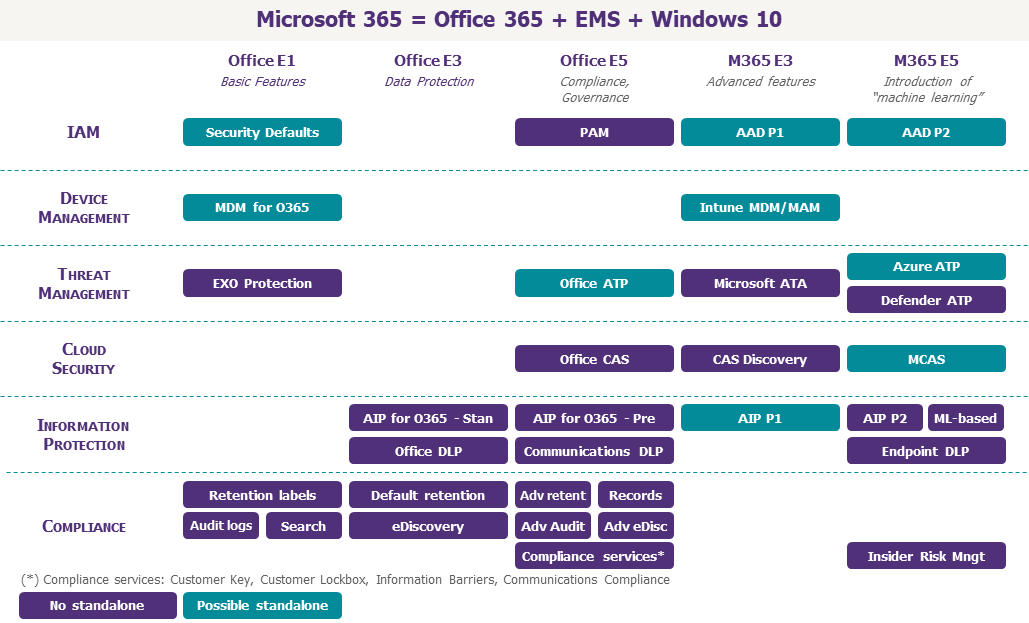
Identity and access management
Azure Active Directory is the fundamental building block of Microsoft Cloud Services (Office 365, but also Azure IaaS and PaaS). It is not just a simple domain controller of the on-premises identity source in the Cloud; it is also an IAM service in its own right. Several licensing plans are available for Microsoft 365 use, whose main features are listed below:
- Azure Active Directory Basic for Office 365: Single Sign On, Manual Management of Users, Groups and Applications, Endpoint Registration, Security Defaults (basic security policies for users and administrators);
- Azure Active Directory Premium Plan 1 (or AAD P1): Azure MFA, Conditional Access, Proxy Application (exposure of on-premise applications on the Internet), Group Lifecycle (expiration, dynamic groups, classification), Advanced Password Protection (Cloud and on-premise), Integration with a third-party MFA or Identity Governance Solution;
- Azure Active Directory Premium Plan 2 (or AAD P2): Azure AD Identity Protection (assessment of connections and accounts at risk), Risk-based Conditional Access, Azure PIM (Privileged Account Management with Just-in-Time Access), Access Review, Entitlement Management (assignment of predefined rights on collaboration spaces to internal or external users).
Experience has shown that the Azure AD Premium P1 license is now a must for a number of companies. At a minimum, these companies must have the following two features: conditional access and group classification. Azure AD Premium P2 is intended for administrative populations in the first instance.
As a reminder, the functionalities available for adding or modifying objects (groups, users or terminals) vary according to the implementation mode chosen: Identity Federation, Password Hash Sync (PHS) and Pass Through Authentication (PTA).
Terminal management
Intune is the Mobile Device Management (MDM) and Mobile Access Management (MAM) solution offered by Microsoft.
The Intune MDM part is historically a mobile device management solution: deployment of applications or certificates on enrolled devices, hardening of parameters, fleet management, etc.
The Intune MAM part represents the functionalities that control the data within applications via apps protection policies. MAM can be used even in a BYOD context. It is important to note that third-party MDM solutions can be integrated with Intune MAM to control Microsoft 365 Apps (such as Office for iOS or Android), but the license will still be required to use the SDK’s functionalities.
In the context of modern management, the Intune MDM part of Intune is positioned as an Enpoint Unified Management (or UEM) solution to manage all devices (mobile or not) in a unified way. The ultimate goal is to replace the SCCM tool, also known as Configuration Manager, by positioning itself in direct competition with other MDM solutions already in place within companies.
Threat Management
The Microsoft Threat Protection suite brings together all the advanced threat prevention, detection, investigation and response capabilities of the Microsoft 365 environment: messaging, collaboration spaces, endpoints and identities.
Although the various components of the suite have historically been considered less efficient than other “pure players” in their respective segments, they have the undeniable advantage of offering unified management and correlation of indicators. However, this gap has been narrowing over the past two years, with Gartner even recognizing several components of the ATP Advanced Threat Protection (ATP) suite as leaders in their segments by the end of 2019.
There are three components:
- Office ATP: Solution to fight threats related to documents, emails and malicious links. While it is possible to add a third-party email gateway, Office ATP is the only advanced protection option for collaborative spaces (SharePoint, OneDrive and Teams);
- Windows Defender ATP: Redmond publisher’s BDU solution;
- Azure ATP: Detection and investigation solution against identity compromise, through the analysis of signals from the local Active Directory. Microsoft announced in February that it will end support for the legacy solution, Microsoft Advanced Threat Analytics (ATA), by January 2021.
Protection of information
Microsoft has recently grouped all data discovery, classification and protection functionalities under the Microsoft Data Protection Framework: Microsoft Information Protection.
At the base is the engine for identifying sensitive data. Microsoft’s engine is based on two elements:
- Sensitive Information Type (SIT): Predefined regular expressions (e.g. social security number or credit card) combined with keywords, document fingerprints (e.g. patent or form) or keyword dictionaries;
- Information Classifiers: Machine learning algorithms, with predefined or constructed models. Introduced this year and still in pre-version, the classifiers can only be used with Microsoft E5 licenses..
The current trend is to classify Office 365 data (emails, documents and now Power BI) using Azure Information Protection (or AIP). The choice of classification level can be done manually or automatically with the engine presented above. AIP has been gradually integrated into the Office 365 service package, under the name Information Protection for Office 365 (or unified classification). Although less necessary today, AIP uses the new solution as well as the non-Office 365 document coverage and classification bar in office applications.
It is also possible to classify a shared space (SharePoint site, Teams or Groups Office 365), but the classification of data and space is still decorrelated.
The actual protection of information consists of data encryption and restriction of rights (DRM). Microsoft’s proprietary protocol is Azure RMS, or Rights Management. Keys can be managed by Microsoft, in BYOK or Double Key Encryption (DKE) (HYOK equivalent for Unified Labeling presented in July 2020).
Azure RMS can be applied to data manually or by inheriting the classification level. The implementation may have a different name depending on the use case involved, but the mechanisms are identical:
- AIP or RMS for documents;
- Information Rights Management (or IRM) for SharePoint: Data downloaded from a list or library inherits protection consistent with the user’s rights;
- Office Message Encryption (or OME) for electronic messaging.
In addition to the above protection, it is also possible to apply shared space protection to harden access according to the chosen classification level, e.g. restricting endpoints or guest users.
In addition to the mechanisms attached to the data (the protection remains even when sharing or copying), it is possible to control the distribution of data through the following tools:
- Office DLP: control of the distribution of e-mails and documents;
- Communications DLP: instant messaging control;
- Cloud App Security: Extension of Office DLP capabilities to integrated SaaS applications;
- Windows Information Protection: equivalent of Intune MAM for Windows 10, aimed at separating business data from personal data;
- Windows Endpoint DLP: new DLP solution for Windows 10 presented in July 2020.
Finally, a discovery of the information can be made afterwards to locate and correct the level of protection if necessary. Again, a different solution must be used depending on the use case:
- AIP Scanner: search and classification of data on on-premises directories;
- Cloud App Security: search and classification of data on Cloud spaces;
- Windows Defender ATP: search and classification of data on Windows 10;
- eDiscovery: Cloud data search (by hijacking the original functionality).
The SDK Microsoft Information Protection can be used by third-party applications to apply classification or protection to data, or simply consume protected data.
As you can see, there are a number of tools with different names to protect organizations’ data. The important thing to remember is that users will only be directly confronted with classification and protection.
Governance
The year 2020 may be selected as the year of compliance for Office 365. Microsoft has reorganized existing products and introduced new ones to address various HR and regulatory risks. All these products are grouped together in the new Compliance Center, which replaces the equivalent part in the Security & Compliance Center.
The first group of these products is related to information retention. Retention policies (retention, legal registration, deletion, etc.) are defined via retention labels applied to a piece of data or a shared space. Labeling can be done manually, by default on containers (e.g. user mailboxes or SharePoint sites), or automatically, in the same way as privacy labels.
The products related to traceability and audit of the holder are then found. By design, the Unified audit logs can trace the actions of users or administrators. These logs, although very complete, are not exhaustive and are regularly completed. In order to increase the 90-day retention period of the unified logs, last year Microsoft introduced Advanced auditing, which offers a retention period of up to one year and more complete logs (such as all accesses to a mailbox).
In addition to logging, four products offer investigation possibilities:
- Core eDiscovery allows to extract content according to a query (e.g.: messages sent by a user containing this or that information);
- Advanced eDiscovery is an advanced feature to filter the most relevant content and provide visualization possibilities on the results;
- Microsoft Data Investigations,still in pre-version, is a clone of Advanced eDiscovery allowing to trace the context that may have led to a data leak;
- Data Subject Requestwas introduced when the GDPR came into force, in order to identify and export data related to a natural person. Again, this is a clone of Core eDiscovery, which can be searched in this context.
Note that the eDiscovery functionalities of Exchange Online (Hold, search, etc.) will gradually be phased out in favor of those of the Compliance Center.
Finally, Microsoft recently presented a whole range of products to combat internal risks (insider trading, data leakage by users on departure, discrimination, illegitimate access to data, etc.). In concrete terms, these products are designed to implement and automate existing principles in organizations’ existing HR, legal and business policies:
- Insider Risk Management is a feature to raise alerts in case of suspicious actions performed by an internal user (e.g. massive downloads performed by a user on departure, breach of security policy). The product is centered around the following axes: alert, investigation, automatic or manual remediation;
- Information Barriers allows to regulate exchanges (OneDrive, SharePoint and Teams) between internal persons, in order to technically force bans on content exchanges between entities due to regulatory requirements;
- Communications Compliance extends Office DLP’s functionality by enabling alerts when inadequate communication is detected (Teams, Mail or Yammer), such as regulatory non-compliance, non-compliance with an internal policy (e.g. harassment) or exchanges around a specific project;
- Privileged Access Management (PAM) is Azure PIM’s counterpart for operational administrative tasks. In order to perform a task, a person will have to request a privilege elevation for a defined perimeter and time;
- Customer Lockbox : is the name of the internal Microsoft process that allows a support person to access data within an organization. Customer Lockbox adds a validation step by the customer in question. In practice, this product ensures that a Microsoft employee does not inadvertently modify data, but does not protect against government requests. On the latter subject, Microsoft regularly publishes statistics.
Most of these products are still in pre-version. There is still very little feedback from the field on these solutions, which are expected to become more mature.
Control of services
In addition to the products described in the previous chapter, Microsoft provides organizations with two additional tools to comply with local regulations.
First, Customer Key allows an organization to add an overlay of encryption at the application level (Exchange Online, OneDrive, SharePoint Online and Teams), that manages the lifecycle of the keys used. This overlay is in addition to the encryption applied by construction to data at rest on Microsoft servers. However, be careful not to lose the keys, which would lead to a total loss of data.
Secondly, Multi-geo‘s functionalities ensure that data is kept at rest in a given geographical area. The challenge with this functionality is to be able to differentiate between personal and shared spaces according to the target location.
Mastering the Cloud
With Cloud App Security, Microsoft has its Cloud Access Security Broker (CASB): fighting against Shadow IT (using the APIs of supervised solutions or SaaS applications not managed via proxy log analysis), Data Protection, Detection of abnormal behavior and Analysis of SaaS application compliance.
Again, three levels of functionality are available:
- Cloud App Discovery: Accessible with Azure AD P1, this level allows you to take advantage of Shadow IT;
- Office 365 Cloud App Security: Accessible with an Office E5 license, this is an intermediate level allowing you to benefit from degraded functionalities limited to Office 365;
- Microsoft Cloud App Security: Highest level of CASB functionality.
It is important to remember here that Azure AD P1 will be required if one wishes to implement conditional access policies for connected applications (including Office 365).
With the Governance features presented above, Cloud App Security is the least exploited brick today, mainly due to the excessively high level of licensing.
Find the rest of this writing in the article “A short guide to find your way through the jungle of Microsoft 365 security and compliance licenses – Part 2”.


