In a previous article, we discovered how “Security Twins” could improve the security and trust of connected devices. In this new article we will now look at how the “Security Twins” can improve the security of physical accesses to a building through a PoC made by Wavestone in collaboration with the start-up Jitsuin using their tool: “Jitsuin Archivist”.
What does “Jitsuin Archivist” look like?
The start-up Jitsuin has developed a tool called “Jitsuin Archivist” based on Distributed Ledger Technology (DLT). The purpose of this tool is to know “Who did what to a Thing and When”.
As of today, 5 types of users can interact with the tool: Archivist Administrator, System Administrator, Maintenance Operator, Auditor, Custom (currently in beta version).

Figure 1 – The 5 user roles of “Jitsuin Archivist”
On this tool the user has access to the “Security Twins” of the connected devices. Indeed, after logging in, the user accesses a dashboard through which he has a global view of all the connected devices linked to the tool. He can see relevant statistics related to his IoT deployment, such as the number of critical incidents, the activity of connected objects, etc.
The user can also access the “Manage Assets” page where he will find a map with the location of all the connected objects linked to the tool and a list of them (where he can also see in more detail the events linked to a particular connected device).
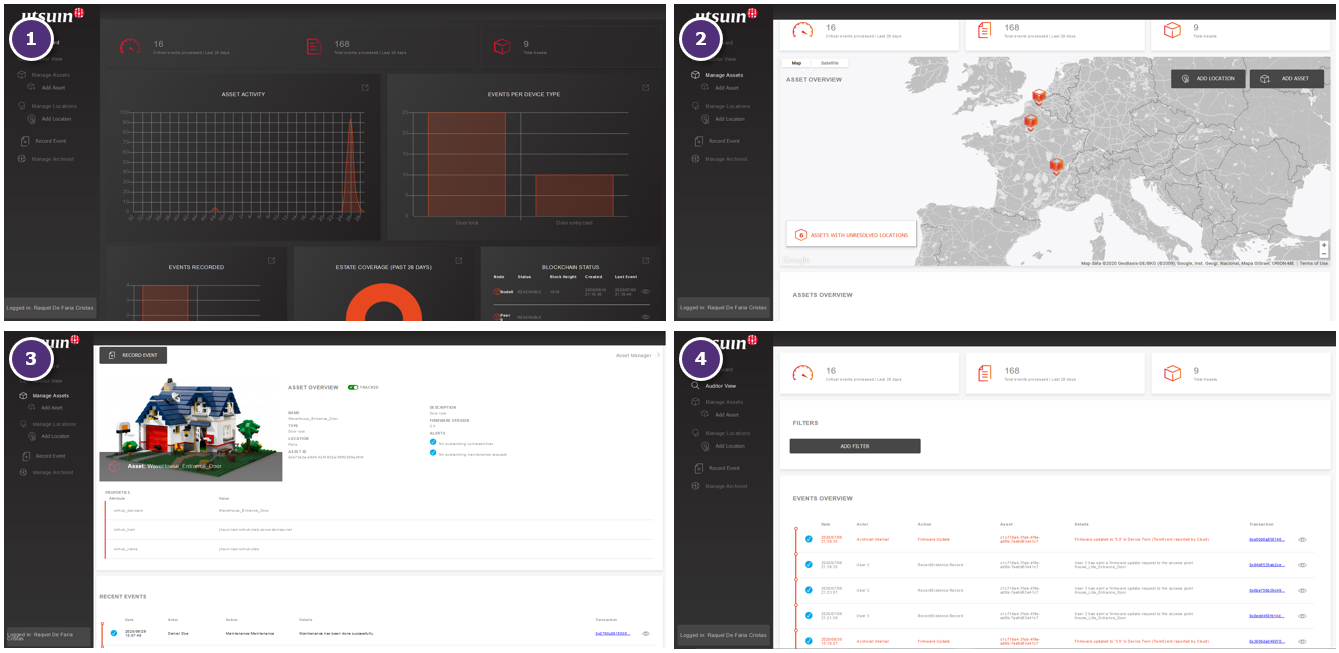
Figure 2 – The different views of the tool “Jitsuin Archivist”: 1. dashboard with a global view, 2. all the objects and their location, 3. detailed view of an object, 4. all the actions of the object useful during security audits
The PoC: A House with a digital lock
Wavestone used Jitsuin’s tool to first address the issue of identity and access management in buildings in at the dawn of digital transformation and the to illustrate the usefulness of “Security Twins”.
To do this Wavestone used the lego house “SmartHouse” :

Figure 3 – The “SmartHouse”
Equipped with an RFID card reader, a Raspberry Pi microcontroller and a servomotor, the entrance door of the “SmartHouse” only opens to users who have an authorized access card. All actions related to opening, closing, granting of entry rights, etc. are recorded on “Jitsuin Archivist” (see figure 4).
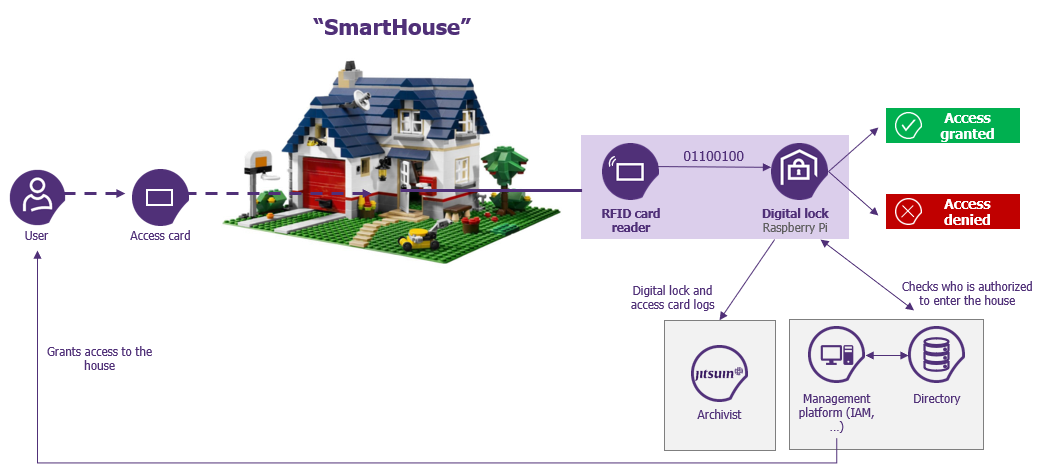
Figure 4 – The functional diagram of the “SmartHouse”
In order to facilitate the interaction with the digital lock of the “SmartHouse”, a platform allowing the simulation of different operations made by different peopled involved in the life cycle of connected devices has been created using the Django web framework and Bootstrap. This platform allows, among other things, to:
- Send security patches to the connected lock (using Azure IoTHub)
- Assign access rights to the “SmartHouse”
- View the history of access rights requests made and those awaiting validation, etc.
This is what the platform looks like:
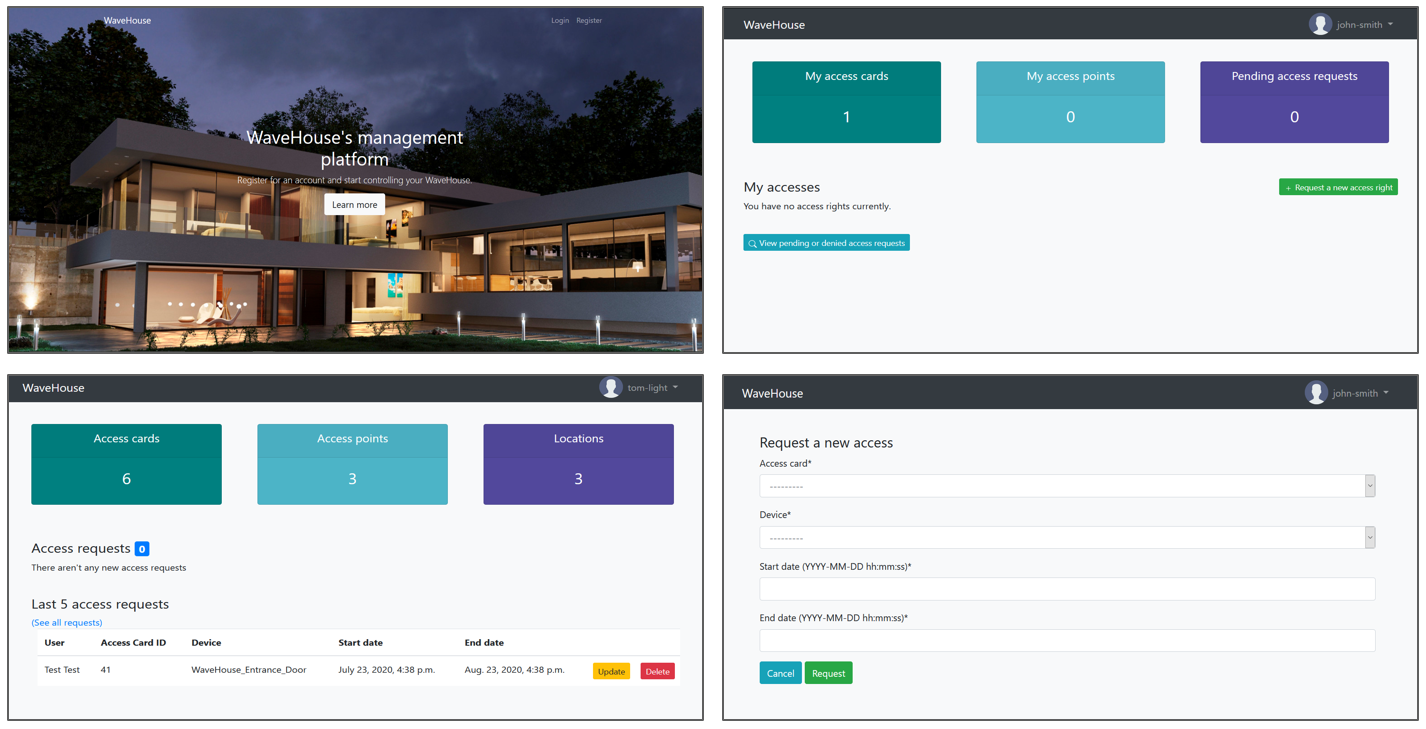
Figure 5 – SmartHouse’s management platform
The use of “Jitsuin Archivist” in this PoC is very interesting when regards to security audits of connected devices. Indeed, as “Jitsuin Archivist” is based on Distributed Ledger Technology (DLT), this system can be considered as “secure by design” since an auditor has a technical guarantee on the non-compromise of data (provided that the sending of this data is secure).
Here is the “Auditor View” on “Jitsuin Archivist” where it is possible to see all the information regarding the connected devices linked to the platform and to know who has done what to the connected device:
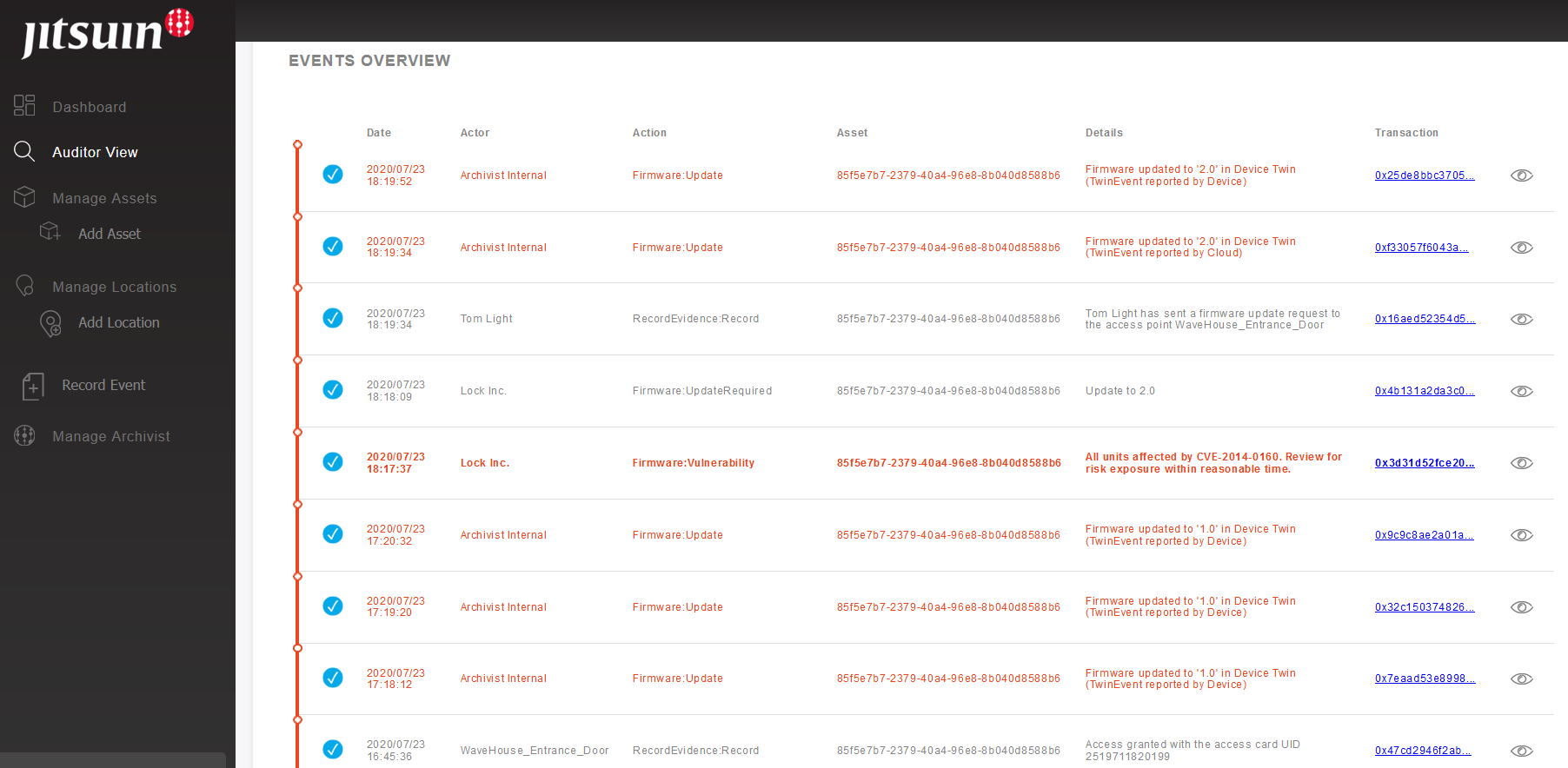
Figure 6 – The “Auditor View” of “Jitsuin Archivist”
The PoC scenario: WaveHouse rents “SmartHouses” in France …
Here is the general architecture of the PoC:
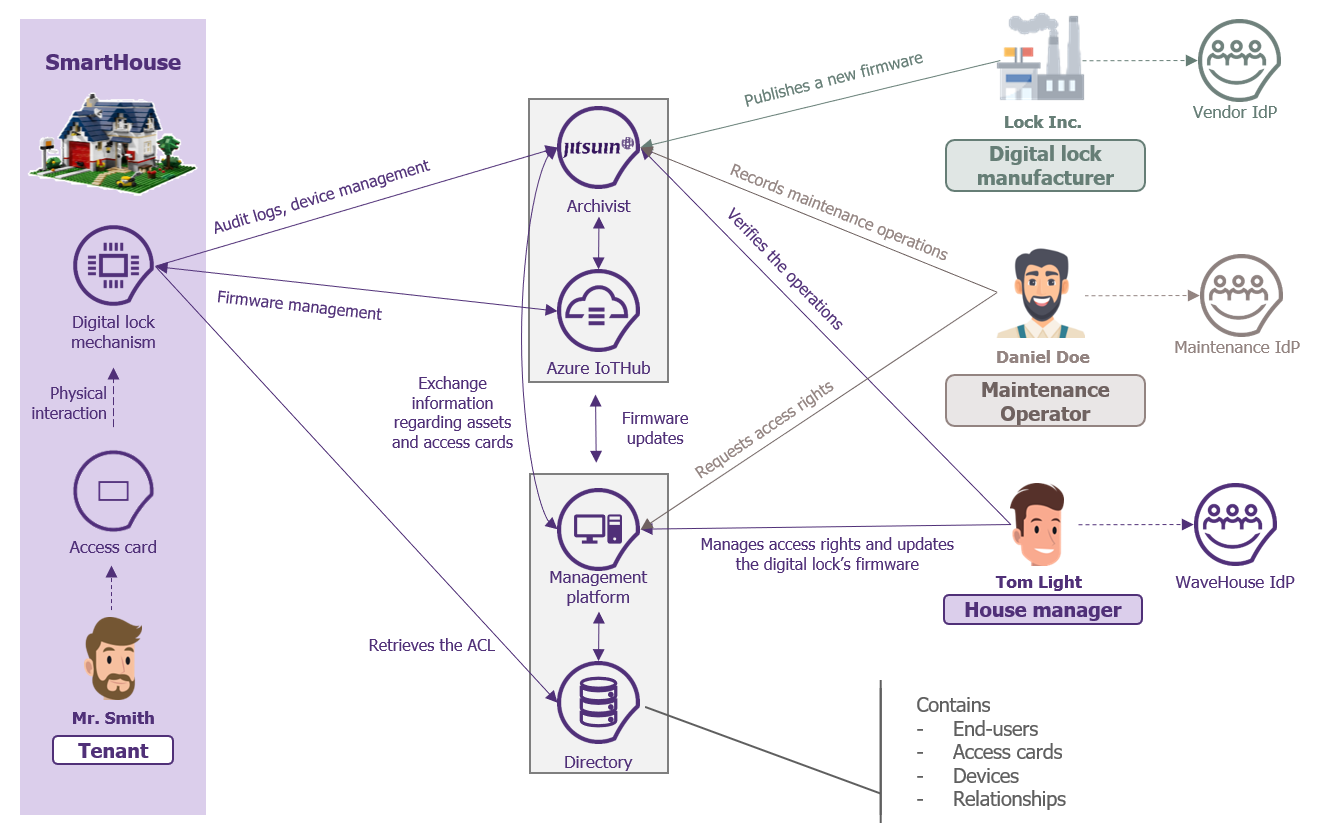
Figure 7 – The general architecture of the PoC
As one can see, the digital lock (represented by the RFID card reader, the Raspberry Pi microcontroller and the servomotor) interacts with Azure IoTHub as well to facilitate the management of its firmware updates.
The main use cases studied by Wavestone and Jitsuin
The main use cases studied by Wavestone and Jitsuin are explained in the video below:
Conclusion
Wavestone and Jitsuin were able to demonstrate – with the different use cases illustrated above in the video – how to improve the security of connected devices:
- First of all, all of the people involved in the life cycle of the digital lock of the “SmartHouse” had access to its “Security Twin”. Indeed, each of them had access to a decentralized and unchangeable register provided by “Jitsuin Archivist” with all the information regarding the security of the digital lock.
- Then, as mentioned above, this architecture is “secure by design” because as “Jitsuin Archivist” is based on Distributed Ledger Technology (DLT), one has a technical guarantee on the non-compromising of data.
- The “Security Twin” of the digital lock ensured physical security since it had the rights management information, allowing all the people involved to know who had access to the “SmartHouse”.
- Finally, since the “Security Twin” also had firmware information, the different people involved could easily know which connected devices had vulnerabilities and quickly plan the distribution of security patches.
The “Security Twins” would therefore ultimately improve the security of the connected devices, since it would be easy to know which objects are secure and which are not.


