In 2010, the early hype-cycle of IoT (Ericsson and Cisco) predicted 50 billion devices by 2020. In reality, that figure was highly overestimated. Today, Gartner states that approximately 5.8 billion IoT terminals will be in use in 20201. Even if the market is not as developed as it was first predicted, it is still growing: those 5.8 billion of IoT devices represent an increase of 21% over 2019.
Despite their usefulness, introducing connected devices unfortunately brings new risks for companies. Indeed, according to the Palo Alto Networks report2 published in March 2020, 57% of the connected devices analyzed were vulnerable to medium or high severity attacks. This is not surprising. Securing connected devices is proving to be an arduous task that explains why Beecham Research3 finds 62% of Industrial IoT transformations fail to scale because of a lack of trust.
Therefore, with this article we will try to ask ourselves about the security and trust issues of connected devices and how companies can deal with them.
What are the security and trust issues of connected devices?
In order to mitigate the security risks on connected devices, NIST recommends in its report4 published in 2019 to focus on 6 main areas:
- Inventory: Maintain an accurate inventory of all connected devices and their most relevant characteristics throughout their lifecycle (see the article detailing the lifecycle of connected devices).
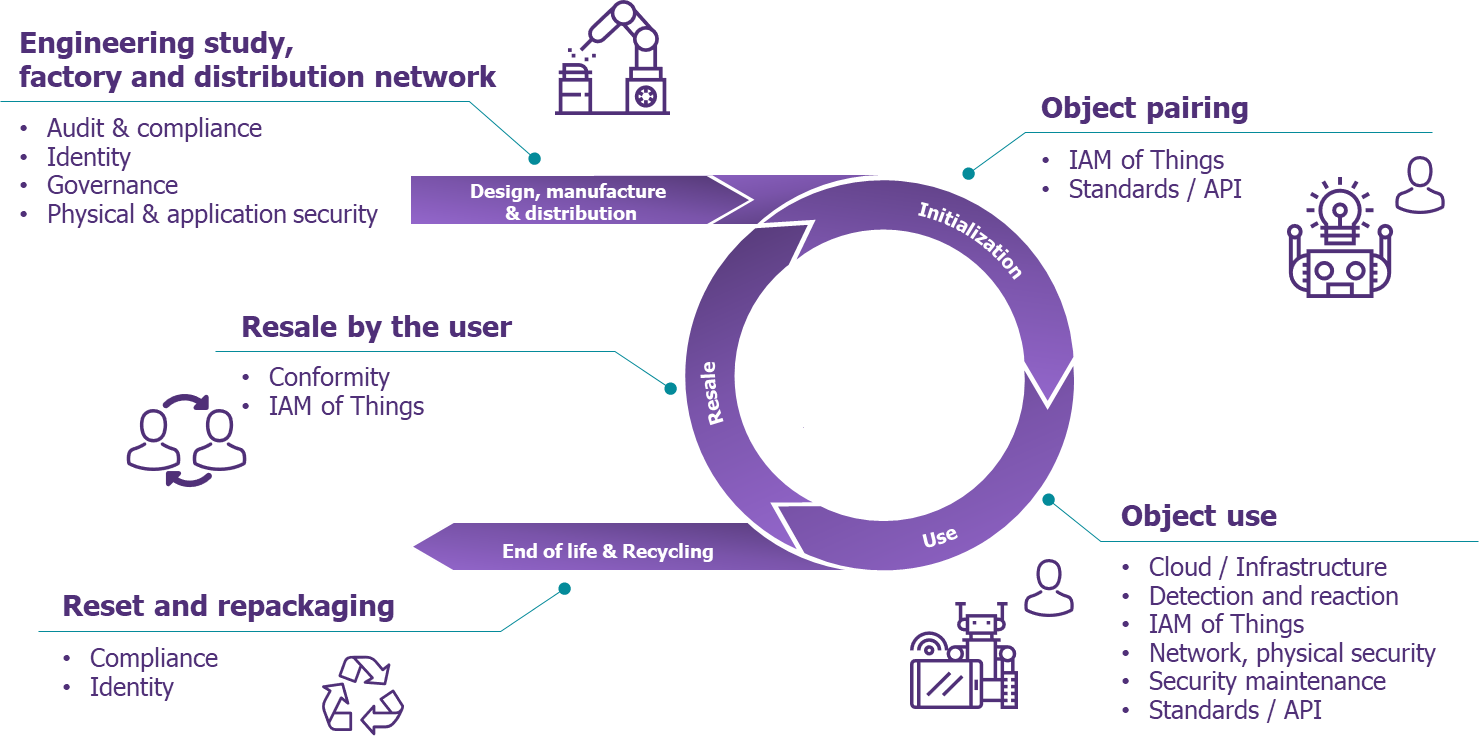
Figure 1 – Connected device lifecycle
- Vulnerabilities: Identify and eliminate known vulnerabilities in the software and firmware of connected devices to reduce the likelihood and ease of exploitation and compromise.
- Access: Prevent unauthorized and inappropriate physical and logical access, use and administration of connected devices by people, processes and other computing devices.
- Detect security incidents of connected devices: Monitor and analyze connected device activity for signs of incidents involving the security of the device.
- Detect data security incidents: Monitor and analyze the activity of the connected device for signs of data security incidents.
- Protect data: Prevent access and alteration of data that could expose sensitive information or allow manipulation or disruption of the operation of connected devices.
However, current IoT platforms only partially meet these security requirements (see the article detailing the usefulness of IoT platforms).
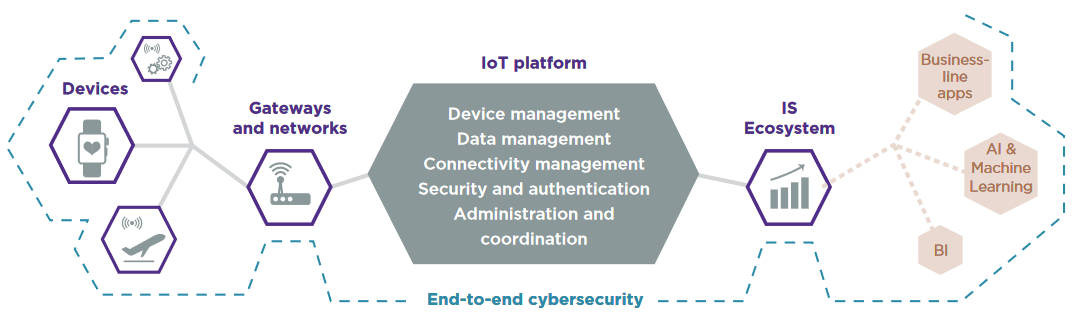 Figure 2 – The usefulness of IoT platforms
Figure 2 – The usefulness of IoT platforms
Indeed, traditional IoT architectures rely on a centralized cloud platform, operated by a third-party company and where most often the rules for data collection and storage are opaque. This is not the best solution to ensure the security of connected devices since:
- The use of a centralized cloud platform introduces the risk of “single point of failure” on the IoT architecture (although today this risk is mitigated with the implementation of a redundant architecture and backups).
- It is entirely possible for an attacker to change the data stored in the cloud database. The decision making of the different stakeholders is therefore impacted.
- Collaboration between the different stakeholders of the IoT deployment (manufacturers, maintenance operators, …) becomes more difficult because access to the platform can be restricted to them.
The use of a decentralized management system for connected devices where all stakeholders would have the possibility to reliably consult or contribute information regarding connected devices (firmware version, maintenance operations, etc.) becomes essential to guarantee the security of those devices and the integrity of data they produce.
How do “Security Twins” help meet the security challenges of connected devices?
In order to support IoT platforms and improve the security of IoT deployments, the notion of “Security Twin” should be introduced in IoT deployments.
The principle of a “Security Twin” is simple. It is a virtual representation of the connected device that contains all its security information, such as firmware version, vulnerabilities, etc. upon which all stakeholders involved in its upkeep can reach consensus (see figure 3).
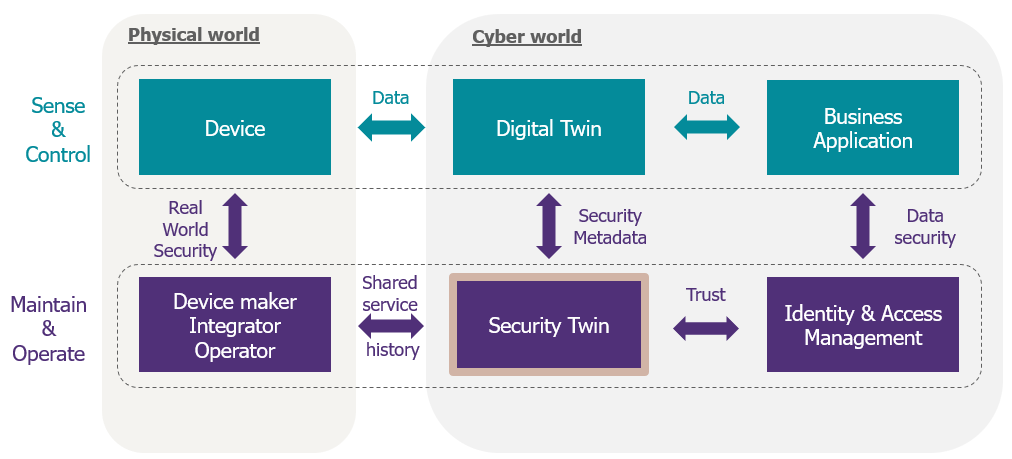
Figure 3 – The “Security Twin” mechanism (from: Jitsuin)
A “Security Twin” gains effectiveness when more stakeholders of the deployment can interact with it and reach consensus that the information provided/recorded is correct.
Therefore, solutions based on Distributed Ledger Technology (DLT) represent a logical first step in the creation of Security Twins, as they would allow the security information of the connected device to be gathered in a decentralized and immutable registry that would be accessible by all authorized stakeholders in the IoT deployment. The best well known distributed registry solution is the Blockchain (see the article on Blockchain’s uses and limitations).
Taking up the points raised earlier in the NIST report, one could say that the use of a “Security Twin” would therefore improve:
- Device and access management: all stakeholders of the IoT deployment would have access to a decentralized and immutable register of all the connected devices with the corresponding security and trust information.
- Vulnerability management and the detection of device security incidents: the different stakeholders could share device security information and take the necessary actions (e.g. the manufacturer of a connected device could notify the other stakeholders of the availability of a new firmware update thanks to the “Security Twin”).
- Data protection and the detection of data related security incidents: The very foundation of a “Security Twin” is based on the use of a decentralized and immutable register to record data related to the security of connected devices. This makes it more difficult for attackers to change the data, which reduces the risk of a security incident.
The use of “Security Twins” therefore offers the possibility of strengthening the security, integrity, trust and resilience of connected devices.
The start-up Jitsuin has developed “Jitsuin Archivist” a tool based on Distributed Ledger Technology (DLT) to overcome the lack of collaborative tools to secure connected devices. The purpose of this tool is not to replace IoT platforms but to allow the creation of “Security Twins”.
Together, Wavestone and Jitsuin sought to demonstrate the benefits of using a decentralized architecture with “Security Twins”. The two companies have therefore collaborated on the construction of a PoC (Proof of Concept) to tackle identity and access management of buildings using connected devices, which will be introduced in a future article.
1 Gartner, 29th August 2019 : https://www.gartner.com/en/newsroom/press-releases/2019-08-29-gartner-says-5-8-billion-enterprise-and-automotive-io
2 Palo Alto Networks, 10th March 2020, “Unit 42 IoT threat report”: https://unit42.paloaltonetworks.com/iot-threat-report-2020/
3 Why IoT projects fail https://www.whyiotprojectsfail.com/?cs=br2
4 NIST – “Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks” : https://csrc.nist.gov/publications/detail/nistir/8228/final


