At a time when the internalized IS is no more than a distant memory giving way to a multiplication of external services hosting data, the SOC’s mission remains the same: to detect cybersecurity incidents in order to react as quickly as possible. But how do you detect in an information system where boundaries are no longer defined? Mission Impossible? Maybe not.
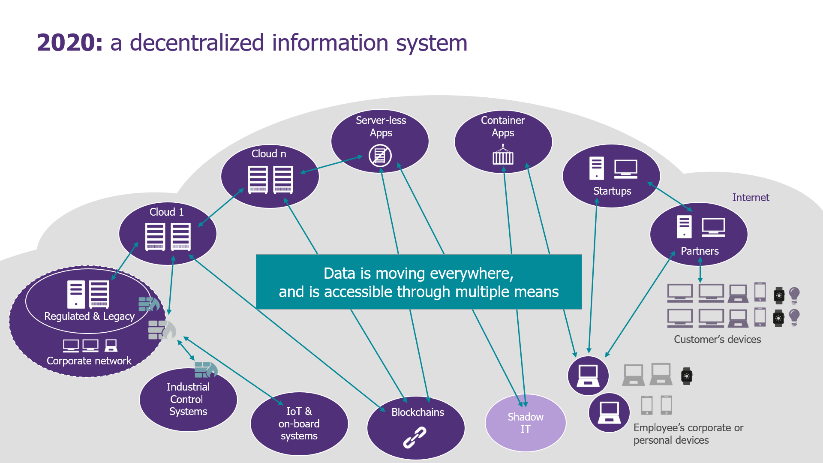
Fifteen years ago, when we first started working on SOC implementations for our clients, defining a roadmap was simple: set up a tool, then collect and analyze the logs of security equipment and critical/exposed assets.
However, new challenges linked to the IS decentralization, the evolution of an ever-evolving threat and the crisis we are going through (teleworking, reduction in cybersecurity budgets…) must make us realize that the SOC must reinvent itself.
Involve (really) everyone!
By rewriting the story from the beginning, the SOC is managed by the cybersecurity population, which has therefore set up monitoring mechanisms on cybersecurity equipment with cybersecurity use-cases. The result is mixed, it works quite well, and the figures from our CERT benchmark are there to prove it: 167 days on average to detect an incident!
The first detection strategies were obviously defined, challenged and validated by the cybersecurity industry. Their objective was to increasingly extend the surveillance perimeter by collecting more and more logs (firewalls, WAF, …) and setting up new surveillance equipment (SIEM, probes, …).
This first observation was inevitably found in the majority of our SOC audit conclusions: objectives are poorly defined and not aligned with the expectations of SOC clients (CISOs, CIOs, business functions), leading to a loss of trust and credibility.
Striking examples can explain this feeling: lack of SLAs, poorly defined perimeter, too raw reporting that is too raw, non-contextualized and containing erroneous information.
If you do not want to redefine your SOC strategy once again in a one-sided way, organizing a seminar is the right exercise to establish a new starting point. All the stakeholders must be present (cybersecurity teams, CIOs, SOC clients, …) and the goal is to address the main issues:
- Redefining objectives: concentrating surveillance on much smaller perimeters that are both technically and humanly feasible
- Clarifying governance: redefining the positioning and role of the SOC in the organization
- Redesigning reporting: sharing customer misunderstandings in order to provide the right level of information.
We have seen that this step, which is essential to the renewal of the SOC, enables an entire ecosystem to be federated around a common target.
Give priority to quality over quantity!
Paradoxically, although the attack area of the IS has significantly increased, the priority is indeed to restrict the surveillance scope to focus on what is really valued.
Firstly, once the functional perimeter of surveillance has been redefined and validated by all, the SOC mission is to technically translate these new objectives into detection scenarios in the tools. There is no need to reinvent the wheel, because new frameworks such as MITRE ATT&CK now allow the different types of attacks to be clearly identified and materialized (techniques used, examples/references and suggestions for detection). The objective is obviously not to be able to cover all the techniques that can be used (330 in total) but to prioritize the efforts on what will allow the objectives to be achieved.
In addition, an HR observation was also raised in most of our audits: teams lack motivation, experience and autonomy to bring added value to operations.
This leads to a high turnover because some tasks are considered uninteresting. The objective is to concentrate human effort on what really brings added value. We have assisted many customers in the implementation of SOAR (Security Orchestration, Automation and Response) tools to automate repetitive tasks of the teams in charge of analysis and reaction. These tools are extremely effective in automating the processing of common, very annoying attacks (ransomware, phishing…) which account for a large proportion of alerts.
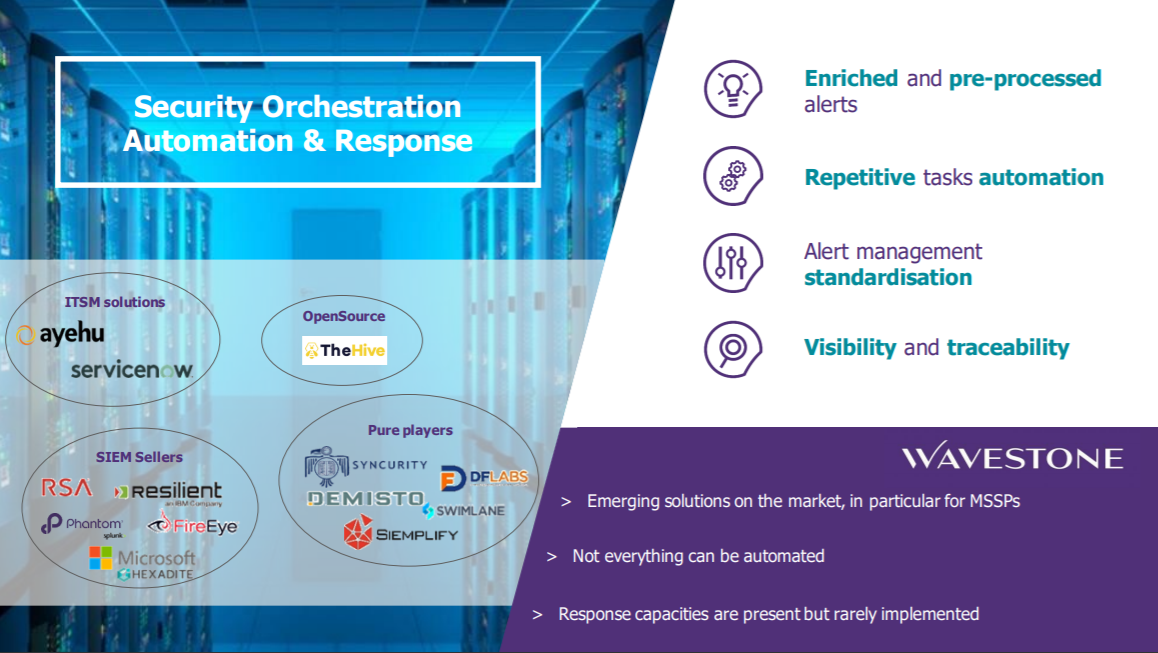
Once these measures are in place, the teams can then be mobilized on activities with higher added value such as the implementation of automation tasks or Threat Hunting activities.
And now, improve and challenge each other continuously!
Once all the foundations are in place to breathe new life into your SOC, how do you stay up to date?
The answer to this question would have been complex 5 years ago, but many recognized standards now allow us to assess the maturity of the SOC in a continuous improvement process. SOC CMM is the perfect example, as this framework enables self-assessment based on a set of precise questions addressing all the issues in terms of tools and organization. This methodology has enabled us to support customers on many before/after comparisons.
Red Team or Purple Team operations are also excellent ways to challenge the systems put in place in relation to the defined objectives. These exercises highlight concrete examples of vulnerabilities as well as precise recommendations to remedy them. In addition, the MITRE ATT&CK Framework can be used to consolidate the tests carried out by type of attack, as well as their results.
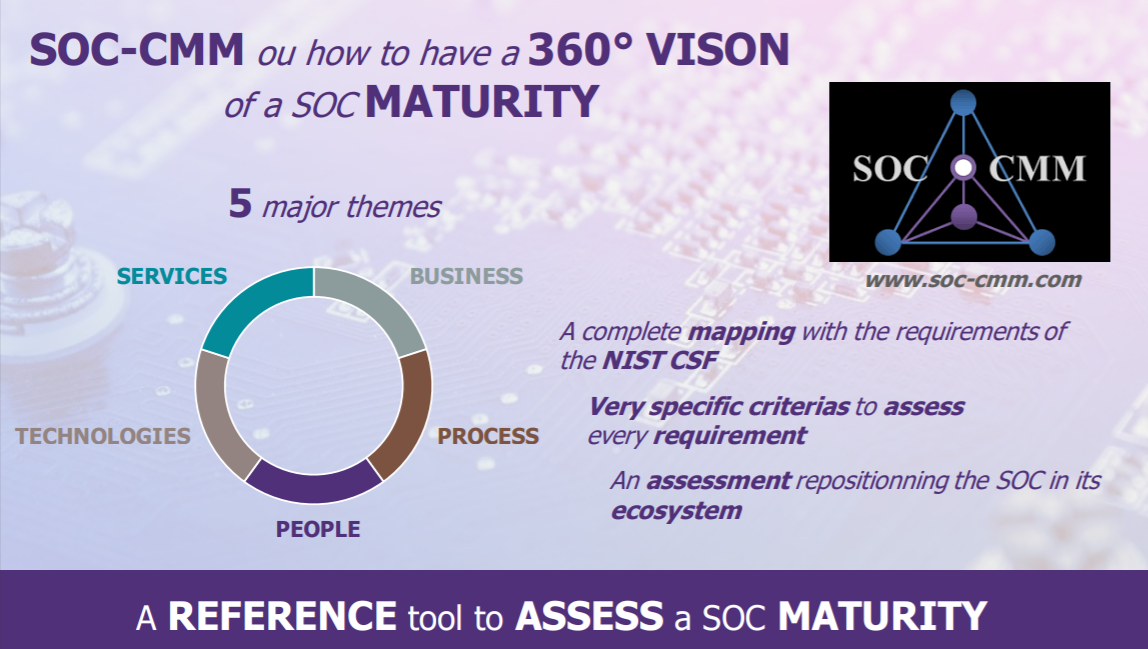
These various initiatives do not provide an exhaustive overview of the problems that SOC are currently facing, but they do highlight our main findings: an isolated SOC, poorly configured tools and demobilized teams.
The exercise of redefining a SOC strategy is a great opportunity to re-mobilize an entire ecosystem under the same banner. This initiative helps to give new meaning to both operational teams and all the stakeholders in the SOC activity. So… let’s do it!


