How can the ISO 27001 framework be used to continuously improve the security level?
In a previous article, we told you all about the new European NIS directive and Belgium’s choice to use the ISO 27001 standard as a basis for increasing the security of Essential Service Operators (ESOs) with all that it entailed for the newly designated organizations.
A European directive does not mean a European regulation: it is therefore up to each member country to transpose the requirements of the NIS directive into its national law. Belgium has chosen to use an existing standard (ISO 27001), while some of its neighbours, including France, have chosen an approach based on the definition of a precise reference system of requirements combining both technical and governance measures (administrative IS, partitioning, approval process, etc.).
Today, let’s try to understand what it means for Belgian ESOs, and more broadly for all organizations attracted by international standards, to follow the requirements of ISO 27001.
The ISO 27001 standard, adulated by some and criticized by others
Some voices are rising up against the reference in the field, castigating in particular its bureaucratic aspect and its red tape which, however, can help to set up a useful reference system for the continuity of services and the training of people through the sharing of practices – especially when it is thought out pragmatically. Criticism is also rife about the added level of complexity, which is even more present for smaller structures. Here again, pragmatism is the rule, and measures must be adapted to the size of the organization and integrated into existing structures to avoid ex nihilo structures that are too cumbersome to manage.
Finally, some preconceptions have a hard time and often reduce ISO 27001 compliance to a list of checkboxes, with no real implications for the security of the organization. But the famous Declaration of Applicability (DoA), required by ISO 27001 for all those seeking certification, is not the same as listing all the controls of ISO 27002. It requires a real assessment regarding the issues and risks. This will provide concrete elements for the security of the organization.
ISO 27001, ISO 27002, are there many like that?
In the ISO family, a lot, really a lot. For cybersecurity, on the other hand, it is these two that are the most used, with ISO 27005 for risk management (if it is data protection that interests you, read also our article on the newcomer ISO 27701).
The ISO 27001 standard provides a framework for cybersecurity and aims to set up an ISMS (Information Security Management System). To help organizations in this direction, it is accompanied by the ISO 27002 standard which details the good security practices presented in Annex A of ISO 27001. The certification (the Belgian ESOs’ holy grail) is based on the ISO 27001 standard but the two standards work well together.
Certification is obtained on a perimeter defined from a business and IT point of view on which the main risks are identified. This risk assessment, combined with the consideration of the organization’s context, helps to select the relevant ISO 27002 good practices to formalize the Declaration of Applicability (DoA) and to exclude controls that are not applicable (be careful to justify these exclusions: they will be analyzed by the certification body). If less useful practices can be removed, other practices can also be added: the organization can thus complete the existing list of 114 security measures regarding its risks. The ISO 27002 standard does not address the exhaustiveness of possible security measures. This is where cybersecurity expertise comes into its own.
5 tips to find the right balance and achieve ISO 27001 compliance
Of course, seen as a whole, an ISO 27001 compliance program can quickly make you dizzy… Here are 5 reflexes to keep in mind to facilitate the launch of an ISMS and the maintenance of its performance over time:
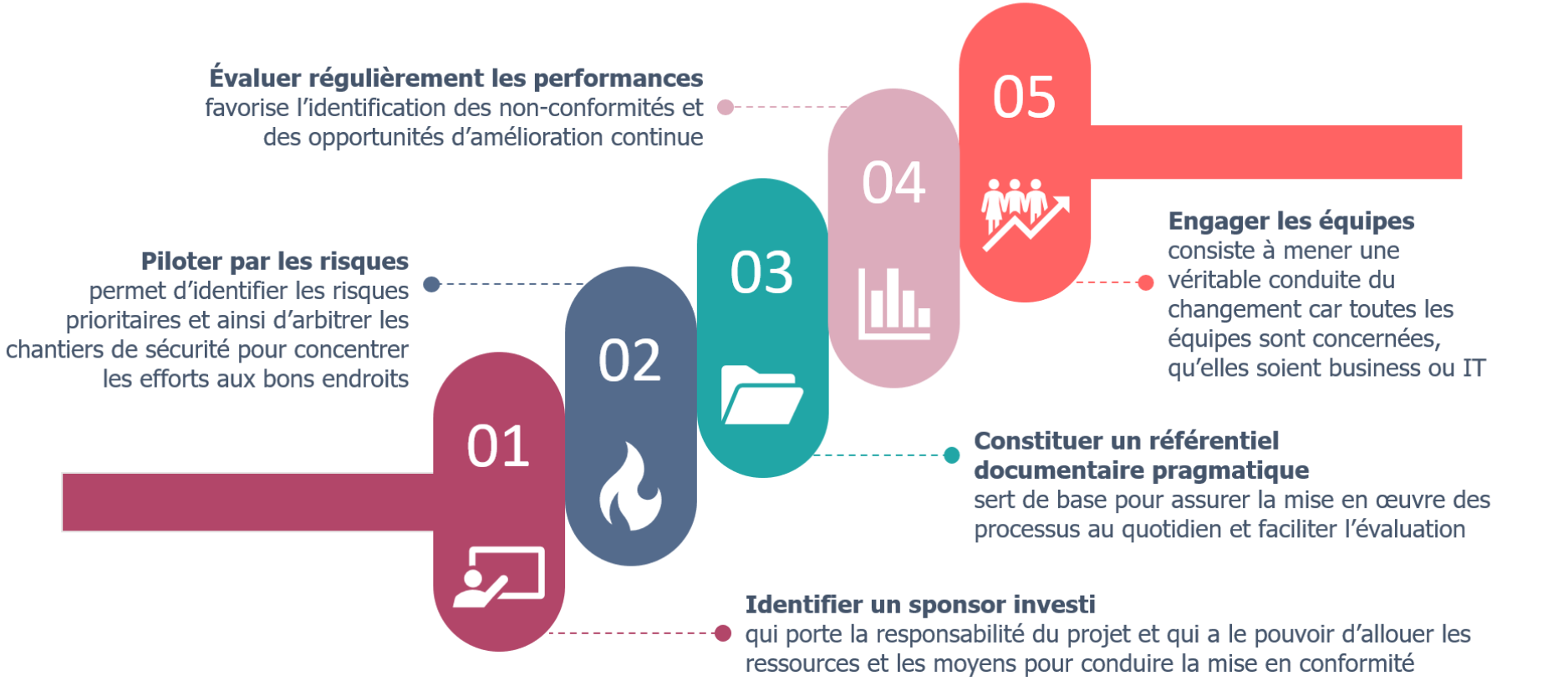
1. Identify a sponsor invested in the service of the security objective. As with cinema, there is no film without a director, and no director without the support of the producer. The perfect match must be fully aware of the added value of compliance with ISO 27001 to improve the security level, beyond pure compliance with the legal framework. He must use normative frameworks for the benefit of a better security level and must therefore see this project as a security project rather than a compliance project.
Implementing a sustainable ISMS requires human, organizational, physical and financial resources and means. Steering the compliance project will only work if it is supported by a manager who has the authority to allocate the resources and means necessary to manage the risks and ensure an acceptable level of security regarding the business challenges. Compliance with the NIS directive, at European or Belgian level through compliance with the ISO 27001 standard, is above all a means of increasing the security level and not an end in itself.
2. Manage by risk. This is the basis of security; the key concept to always keep in mind. This management makes it possible to identify the risks within the perimeter and to ensure that the business challenges are considered. Risk management does not stop at the identification and initial treatment of risks. It requires the mobilization of teams and activities to deal with existing risks and monitor the evolution of risks (existing and new risks that emerge) and their treatment, through periodic updates and during major events within the scope.
By implementing this global approach to risks, the organization ensures a cross-functional vision of risks that allows it to focus its security measures where the stakes are highest. This validation and arbitration must be carried out in consultation with the owners of the risks (business or IT) who are responsible for the risk within their perimeters and must position themselves on the possible treatments (acceptance, reduction, transfer or avoidance). Refined and tightened risk management thus enables real, informed decisions to be taken, by players who are sometimes far removed from security.
3. Establish a pragmatic documentary repository. This step helps to define and document practices and thus promote business continuity, control and continuous improvement. This documentation must reflect reality while ensuring consistency with the requirements of the ISO 27001 standard to help define the practices to be implemented and manage them on a daily basis (implementation and updates as changes occur, etc.).
The key words when setting up this reference system are pragmatism and usefulness: it must be integrated into the existing system by completing existing procedures and creating new ones that were missing; it must not unnecessarily complicate the situation but be based on a relevant interpretation of the standard; it must be useful to the teams carrying out the activities to enable operations to be maintained. Therefore, avoid copying and pasting requirements from the standards. They create a useless referential for the field teams and will arouse the curiosity of your auditors who will then doubt the effectiveness of the measures…
4. Regularly evaluate performance. Any self-respecting management system requires a control loop to assess its performance and, in the case of ISMS, its non-compliance with the ISO 27001 standard and with the reference system in place in the organization (summarized in the DoA). The identification of these non-conformities must make it possible to trace them back to their source and initiate reflection on the best way to manage them. The reflection to be carried out must focus on how the non-conformity will be resolved to ensure an increase in the level of security while ensuring that the measures correspond to the requirements of the standard and are adapted to the context, the risks and the stakes of the organization.
The different levels of control (self-monitoring by the teams, internal/external audits, management reviews) must all keep the objective of improving the security level in mind by pragmatically using the requirements of the standard and the company’s reference framework, and if necessary, make the latter evolve in the light of the practical reality of the organization. It is a question of finding the right balance between the context of the organization and the management of the identified risks. If your challenges are mainly related to the availability of an activity, focus your efforts (measures and controls) on this issue as a priority. To be relevant, this assessment cycle must distribute efforts on the most relevant perimeters for the organization (according to its risks and impacts) and feed the next steps of the ISMS life cycle.
5. Engage the teams. An ISMS implementation project is not only the prerogative of the CISO or a team of documentalists. It is first and foremost a large-scale project that requires a wide range of expertise, from cyber security to business, IT, legal, procurement, human resources, etc. It is a real change management process that needs to be organized with the full and complete involvement of the various teams and the organization’s management to ensure an ISMS that serves the sustainable improvement of the security level for the entire perimeter.
ISO 27001 certification, yes but pragmatic!
The real strength of ISO 27001 certification is above all to trigger a security dynamic within the organization. Documentation can certainly make practices more cumbersome but does not detract from the philosophy of continuous improvement of the level of security. By providing a minimal basis for cybersecurity, without defining strict requirements, the standard leaves the organization the choice of placing the security cursor at a level that is suitable and to obtain positive results – as long as you surround yourself with good people who are aware of the topic.
Treated with a critical and pragmatic eye, the standard thus provides a framework for installing cybersecurity governance within each organization by mobilizing key concepts while leaving the necessary room to propose complementary measures that, together, serve to improve the level of security.
The free implementation of the NIS Directive at the European level offers a new testing ground where different cultures and different visions of cybersecurity are mixed. Only the future will be able to tell us what works at European level, but the Belgian approach once again demonstrates the culture of compromise between strict framework and freedom of movement. For Belgian ESOs and certification bodies alike, the unknown is above


