
What is a bug bounty and what is it used for?
Mere buzzwords a few years ago, bug bounty programmes and vulnerability disclosure initiatives have since permeated the cyber-related vocabularies of a wide range of organisations, whether it be digital giants, top investment banks, or government bodies. The basic principle is the following: companies provide a financial incentive or reward for well-intentioned hackers to find and report vulnerabilities discovered in their assets. The catch is that the company behind the initiative sets a fixed window of opportunity for hackers to discover and fix these vulnerabilities. Wavestone has studied the adoption of these initiatives within the banking sector and the good practices to be drawn from such initiatives.
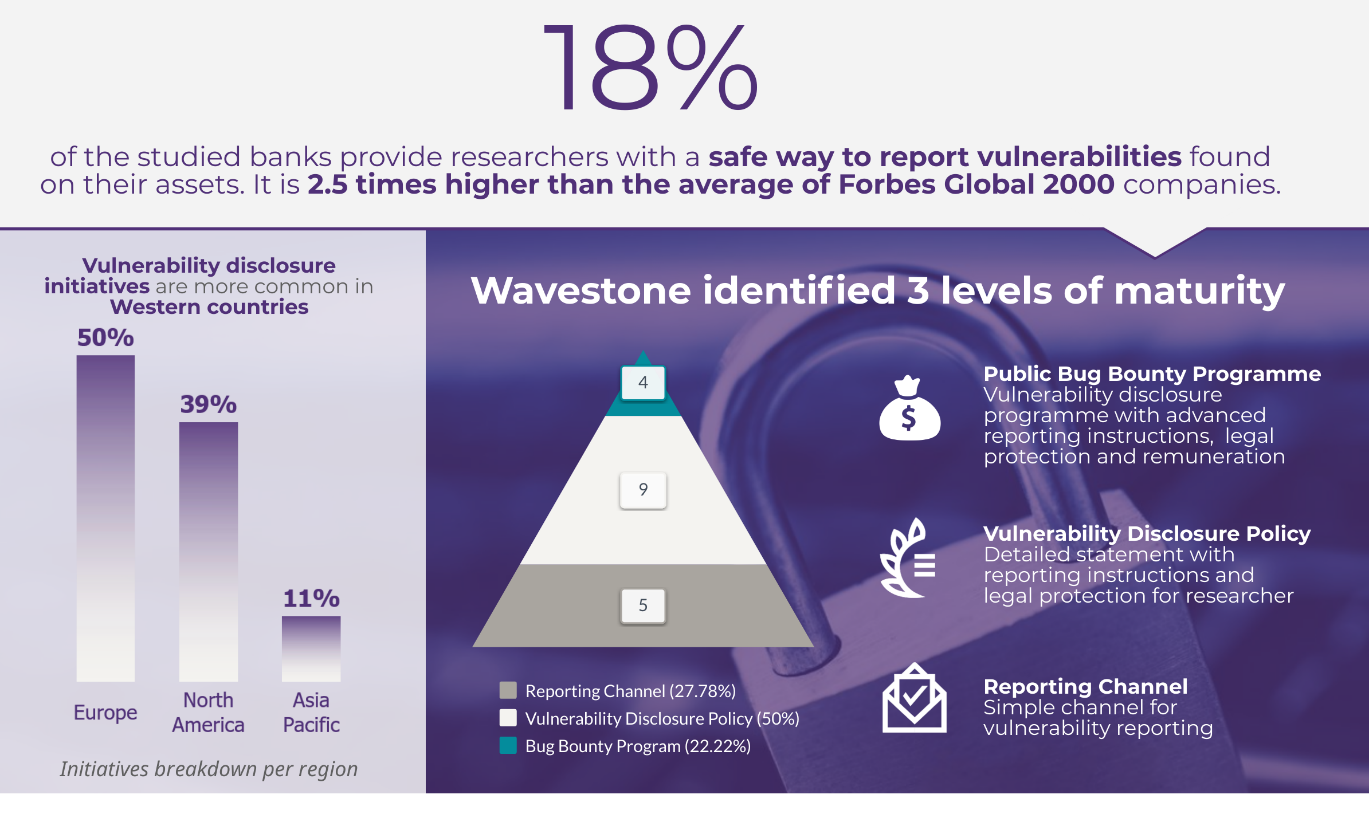
3 levels of maturity: Reporting Channel, Vulnerability Disclosure Policy and Bug Bounty Programmes
When it comes to vulnerability disclosure, the initiatives are various and the terminology is broad, whether it is Coordinated Vulnerability Disclosure, Responsible Vulnerability Disclosure or Vulnerability Disclosure Policy. All of these initiatives aim at providing researchers with a safe way to report vulnerabilities, yet the level of detail regarding the reporting process, rules for searching for vulnerabilities and the expectations of the organisation in question varies greatly from one programme to another. In the light of these observations, we identified 3 levels of maturity as follows: Reporting Channel, Vulnerability Disclosure Policy (VDP) and Bug Bounty Programmes (BBP).
The first level of maturity, Reporting Channel, generally consists of a simple web page providing very basic instructions and a dedicated channel to report vulnerabilities. This first step toward vulnerability disclosure acts as a safety net in case someone discovers a vulnerability, but it doesn’t actively attract hackers, particularly due to the lack of monetary incentive. Reporting Channel is the second most common type of initiative, accounting for 28% of the identified initiatives.
The second level of maturity, Vulnerability Disclosure Policies, also takes the format of a dedicated web page but this time with much more detail. It contains advanced information on reporting processes, the assets in scope, and the preferences, rules and exceptions for vulnerability researching. Furthermore, in most cases (90%), information regarding the expectations that hackers may have after submitting a report in terms of both service-level agreements (SLAs) and public recognition for their work are outlined. In many of these initiatives (77%), companies commit to providing hackers with safe harbour and not pursuing legal action against hackers if they follow the rules and act in good faith. This kind of initiative can be managed internally or by a third-party platform (HackerOne, BugCrowd, Synack…) that will communicate with hackers and oversee bug triage.
Finally, Bug Bounty Programmes represent the highest level of maturity, as it features the same level of information as Vulnerability Disclosure Policy but this time, hackers are financially rewarded for reporting vulnerabilities. This aims to attract talented hackers and make bug bounties a fully-fledged tool in banks’ cyber-ecosystems. Third-party platforms can either manage these programmes or set up private programmes to which only vetted hackers will have access (following a background and skills check). In many cases, private programmes are used as a steppingstone to bug bounty, allowing companies to gain experience with the concept before moving on to a public programme. They also make it possible to implement advanced security features (full research monitoring through VPNs, Non-Disclosure Agreements, advanced vetting, on-location research…) which make it easier to comply with the security and confidentiality standards that are common in the banking sector.
The banking industry is not outdistanced by other industries
These initiatives were implemented by 18% of the studied banks, which is 2.5 times higher than the average reported in the Forbes Global 2000. Therefore, it can be said that the banking sector has well-integrated vulnerability disclosure processes as part of its cyber ecosystem, with the banking and insurance sector ranking in 3rd position in terms of number of programmes for Internet and online services and computer software. However, it is not the most attractive from a financial point of view, ranking in 12th place in terms of the average remuneration for a critical vulnerability, with blockchains and crypto currencies offering an average remuneration that is almost 3 times higher (source: HackerOne’s Hacker Powered Security Report 2019).
Western banks are more confident about engaging in vulnerability disclosure processes
Although the adoption of vulnerability disclosure processes in the banking sector seems to be global, this research found that initiatives are mainly adopted by European and American banks with some specificities. These observations can be explained by several factors.
In the US, vulnerability disclosure has long been part of the culture of tech industry giants such as Google and Facebook which, among other companies, launched their own programmes before 2012. The US are also home to players that now rank among the world’s leading bug bounty platforms, including BugCrowd (2011), HackerOne (2012) and Synack (2013). It is therefore not a surprise to see that these platforms are managing most of the American banks’ vulnerability disclosure programmes.
In Europe, the situation is different and there are fewer key players. After several major cyber incidents, the Netherlands was the first country in Europe to launch a national initiative by publishing the Guidelines for Coordinated Vulnerability Disclosure (2013) – a collaborative effort between the Dutch Government’s National Cyber Security Centrum (NCSC) and various private sector companies. Today, nearly 70% of the major Dutch banks have a self-managed bug bounty programme and the country has played a key role in the construction of EU guidelines on the subject matter. It is also regularly referred to as an example to be followed by several European authorities. Other initiatives and platforms have also emerged elsewhere in Europe, such as YesWeHack, Intigriti, HackenProof, Yogosha, etc. However, it is difficult to precisely assess the emergence of bug bounty programmes across Europe, as more than half of them are private and lack publicly available information for the purpose of confidentiality.
In Asia, banks are less proactive on vulnerability disclosure on account of reservations about private programmes and other cultural factors. However, the last few years have seen growing initiatives from both Asian technology giants and government institutions, notably in Singapore and Japan. This is not surprising, as many government institutions have launched this type of initiative in the past (for example, Hack The Pentagon in the USA or the recent StopCovid application’s bug bounty that is managed by YesWeHack in France).
Getting into vulnerability disclosure will require truly effective preparation
With many success stories and a growing number of companies from all sectors launching vulnerability disclosure programmes, it is tempting to follow the trend. However, to ensure the success of this type of initiative, it is crucial to address a few points. First, a vulnerability or bug bounty disclosure programme should be part of a global cyber security approach and be complementary to more traditional measures such as regular code reviews, security by design and security/pentest audits. Reporting bugs and flaws is only the first step of the process. The company must then have the in-house skills to analyse the provided reports and remediate the vulnerabilities as soon as possible. Second, to avoid wasting both the hackers’ and the company’s time, the scope of the programme must be carefully designed in order to maximize its effectiveness and prevent intrusion on unwanted assets. The same rules apply when it comes to the rules for searching and reporting. Finally, it is crucial to address hackers’ motivations to ensure the success of a bug bounty programme. Expectations for submitting a report must be clearly specified and address the process, response time and reward. Constant communication with the hacker community as well as an evolution of the programme or the rewards are some key elements that can ensure the sustainability of the programme and the motivation of hackers, thus contributing to the programme’s success.

The image of hackers is still often associated with criminal actions…
When it comes to bug bounty, one of the main concerns is security, with organisations questioning whether exposing their platforms to hackers might lead to exploitation of any discovered vulnerabilities through the sale of user data or the vulnerabilities themselves directly on the black market.
These fears are partly justified, as user data can now easily be sold on the black market: credit cards, passports, medical records or authentication information can be sold for less than EUR 15 and targeted phishing using this information can generate even more profit. A critical flaw can also be exploited and result in a much larger cyber-attack, as demonstrated by the havoc wreaked by cryptolockers in recent years. However, these incidents are rarely linked to bug bounty programmes, as malicious hackers do not wait for organisations to launch bug bounty programmes in order to attack them. Rather, these attacks can occur at any time.
Secondly, different skills and levels of preparation are required to find vulnerabilities and exploit them.
Finally, money is the primary motivation for hackers participating in these programmes in less than 15% of cases, according to HackerOne. For the majority of hackers, hacking is a passion and they are mostly looking for challenges and opportunities to improve their skills and make the web more secure – in this case, financial rewards are just a small bonus and getting on the wrong side of the law is not worth it.
Vulnerability Disclosure Policy: a first step to improve cyber security
Vulnerability disclosure and bug bounty initiatives are now a mainstream topic in the cyber security field, and the banking sector is no exception. Although bug bounty programmes are not miracle solutions and some effort is required in order to ensure that they are really effective, implementing a Vulnerability Disclosure Policy appears to add a great additional layer of security for a low investment. We can therefore only recommend implementing such a policy as soon as an organisation’s cyber maturity allows for it.


