Wavestone and Sigfox share a common passion for tech, innovation and security. Our discussions led us to explore the foundation of all cybersecurity initiatives (the risk analysis), why this is different for an IoT project and, most importantly, how you can get started.
What is a cyber risk analysis?
Did you ever wonder what would happen if a device your company developed and sells leak the data it collects? Or if that data were corrupted or suddenly made unavailable? What would be the most detrimental? What if your solution was vulnerable to a cyberattack? Could the consequences be a takeover of device(s) which leads to a safety hazard such as a building taking fire or even a human casualty? Or maybe it could “just” be a pivot attack onto your customer’s network that leads to a full incapacity for your and your customer’s businesses to operate.
If you are currently developing an IoT solution and are not having a nervous breakdown when considering such possibilities, you are probably wondering though how your CISO (Chief Information Security Officer) is not having one.
Well it is probably because your CISO has a method: they consider every risk from an unbiased perspective and in a comparable manner. Ensuring each risk is correctly evaluated (i.e. not overestimated or underestimated) and sharing the outcome of this evaluation with all project stakeholders is the first important step. Once all stakeholders agree upon every risk your company has the right basis to decide control measures.
This approach does not mean you should address every risk to the point that your solution is virtually unhackable. Frankly, this is not technically possible, and your budget would vanish far before achieving a so called zero cyber risk solution. Each control measure must be prioritized and proportional to the risk likelihood and severity.
What we described above is known as a risk analysis methodology. Cybersecurity professionals use this methodology as the baseline to their company’s cybersecurity initiatives. The professionals evaluate risk scenarios (often tied to service availability, data integrity, confidentiality and/or traceability of actions) and the impacts on their company’s brand image, legal liabilities, safety consequences and of course financial outcomes. The higher the risk is evaluated, the higher the priority is set to lower the likelihood of the risk occurring (e.g. add barriers to an attack, reduce the attack surface, etc.) or the severity of outcomes if the risk occurs (e.g. apply segmentation to reduce the spread of an attack).
If you want to learn more about the existing risk analysis methodologies you should start with ISO27005 which has a wide scope of adoption and understanding across various industries.
Be reassured that talking about risks will not increase the likelihood of the problem occurring (if you ever feared that), however not talking about them puts the project at great risk.
What makes an IoT Project risk analysis different?
Hopefully we have convinced you that doing a risk analysis of your project is an important task; we will touch upon how you can get started quickly in the next chapter. Before we get there, we will detail what makes the exercise specific for an IoT project: what are the characteristics of such projects and what makes the risk analysis more difficult or simpler?
Let us start with the common characteristics that should be considered for a risk analysis. First of all, an IoT initiative often relies on a very decentralized network of hardware (sensors, gateways, servers, etc.). These devices can be spread over a large geographical area, sometimes all over the world, and are meant to remain in the field for a long time with little to no onsite maintenance. It is common to see B2B IoT devices that aim for a lifetime of more than 10 years (e.g. a water metering project for utility companies). B2C devices can also aim for such lifetimes – think of connected vehicles for instance. It is also noteworthy that IoT devices usually have limited user interfaces such as a screen and keyboard. Despite this, the buttons, LED and mobile applications allow the necessary interactions or customizations to the IoT device for you to collect data from the field. Remember, the data collected from connected devices is where the value resides. Thus, whether that data is critical or not is essential in the risk evaluation. Finally, we need to remind ourselves that an IoT project is still an IT project. If the devices are not typical laptops, the application servers and storage remain central in most cases. This is where a large part of the risk remains, but fortunately, there are many best practices for this portion of the solution as well.
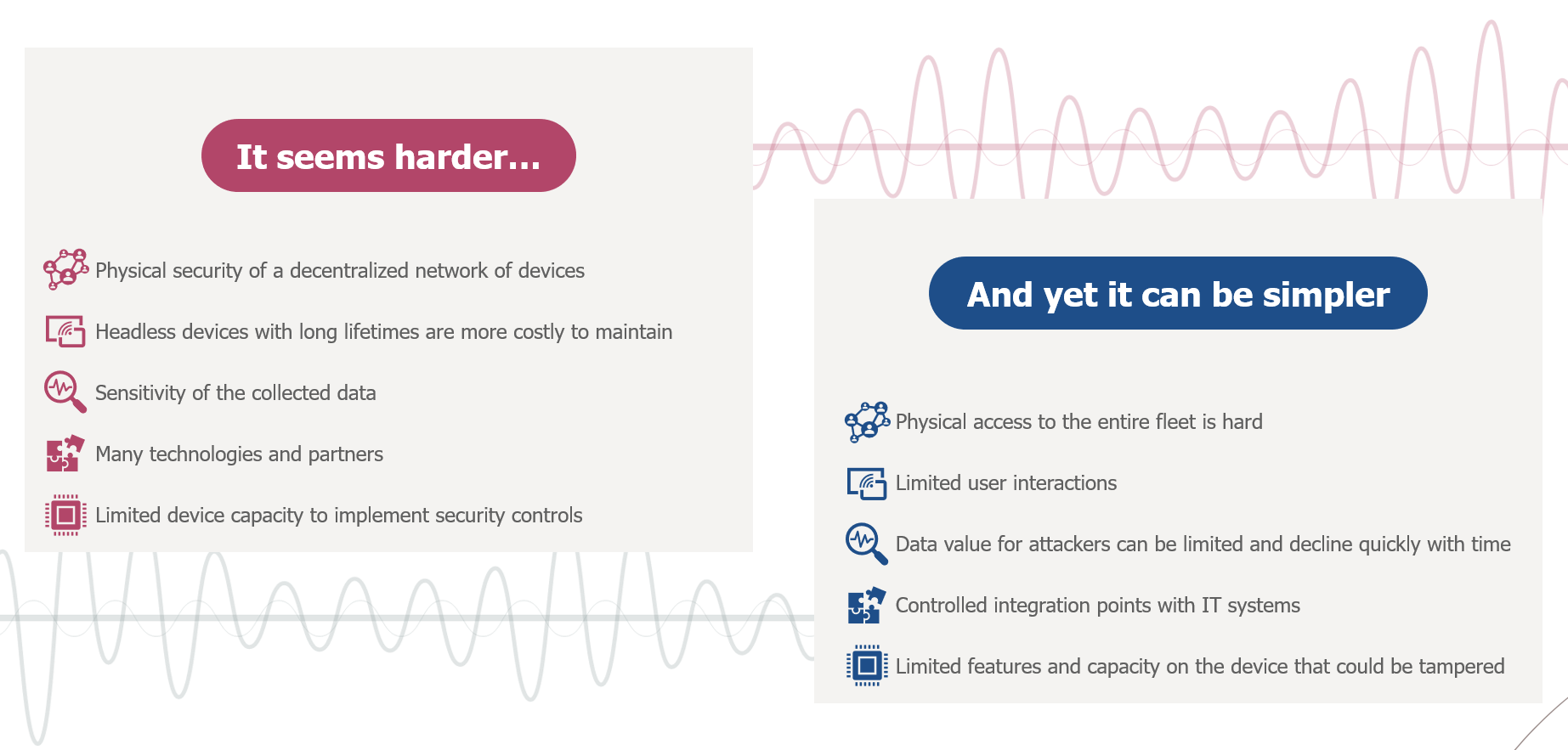
From a cybersecurity perspective such characteristics can make IoT projects riskier. For instance:
- The physical security of a decentralized network is very hard to enforce. Where are the devices located? Are the devices accessible to the public? Can someone easily steal, damage or tamper the devices? For example, a tracker installed on a pallet travels outside trusted premises and can be damaged or removed – intentionally or not. Of course, this risk is amplified by a wider geographical footprint.
- Given the limited user interactions and the longer device lifetime, it can become very costly and time-consuming to maintain the devices, especially if you must physically dispatch technicians. Hands-on intervention can be simply unrealistic, but even firmware upgrades have a failure rate. Because of all this, the controls must be relevant for the long run.
- In any IoT project, the sensitivity of the data is a factor that must be considered. Is it critical for your company? For consumer projects the sensitivity of the data can be perceived as very high because the devices will collect data from the “real” world.
- IoT solutions consist of many different technologies and vendors. This is a challenge for us: what are the security practices followed by each of these vendors and do these practices sufficiently cover my risks?
- Finally, the security controls that can be applied are dependent on the capacities of the devices and softwares. For example, many sensors run on 8-bits MCU and thus cannot run complicated encryption algorithms.
Fortunately, all these characteristics also play a role in reducing the cyber risks for IoT projects.
- With very decentralized deployments, the level of effort required by an attacker to access a large number of devices is burdensome. Compromising a single device is one thing but compromising the entire fleet of devices is an entirely different task. This is especially true if physical tampering or proximity is required.
- The application of the IoT devices are rarely handled directly by a user and there are limited user interactions after installation. Thus, attackers have limited opportunities to trick the user into misusing the application.
- Depending on the context, the value of the data can be very limited for attackers (e.g. room temperature monitoring used to control AC systems). What is more, the value can also decrease sharply with time. Production data can be critical for real-time control of processes, but it becomes a lot less valuable a few minutes after.
- The architecture of IoT solutions is usually segregated from the IT systems including servers or data centers. This segregation enables companies to easily define and protect integration points.
- Finally, the limited capacities of the device play a role in preventing any harmful attempt. Attackers simply cannot access, implant malware or effectively control sensors with 8-bit MCUs.
So now, how can I get started?
Well, take a deep breath and involve your CISO.
The CISO must identify and evaluate applicable regulations, decide what level of risks is acceptable, provide policies to follow and tools to implement security measures. Perhaps you should appoint Product Security Officer to specifically address IoT security in your company or even a given IoT product’s security if the stakes require it.
Getting to an acceptable level of security will require expertise on the various areas of the IoT solution. If you are that expert, then you should probably be ready to get involved. This will drive the whole team to consider the:
- End-to-end security on the technology stack: from hardware to cloud including embedded software, network connectivity, mobile apps, etc.
- End-to-end security from a device lifecycle perspective. When you design your device, think about all phases: from manufacturing to distribution; from initial use to normal usage; resell, refurbish, recycle or trash.
- Partners involvement: make sure not to forget them and assess their maturity. You might need to take measures to support them or upskill them (hint: ask your CISO or PSO for it).
- Audit of your device and the whole technology stack. Do this regularly because your software may not have changed but the threats and known vulnerabilities may have.
- Long-term security updates and maintenance: define for how long you will update and deploy your devices.
- Incident response organization: define how you can be notified of vulnerabilities or breaches and how you can plan to respond (from a technical and a communication point of view).
IoT cybersecurity is not impossible. It actually provides methodologies and tools to help achieve a secure landscape.
Project stakeholders and customers are seeking and pressuring for secure products. Regulation to enforce security are imminent and frameworks to help align every actor regarding its duties will continue to be applied. It is time to get ahead now if you are looking to make cybersecurity an asset for your product on your market!