Among the needs identified by our industrial customers are the mapping of OT systems (Operational Technology) and the detection of attacks. Over the last ten years or so, several players have been working on the development of tools to meet these needs: industrial cybersecurity probes, also known as detection probes or intrusion detection probes. For the rest of this article, we will simply refer to “OT probes”. For your information, there are also IT (Information Technology) probes, but they are not part of the subject of this article.
Our product vision: a solution with multiple functionalities
Description
An OT probe is a piece of equipment, virtual or physical, connected to the information system (IS) in order to map and monitor it. It consists of sensors distributed in the network to collect data and central equipment to correlate this data.
A probe is characterised by:
- Its operating mode,
- The positioning of its components,
- Its attack detection methods,
- Its bundle of features.
The illustration below provides more details on each of these items:
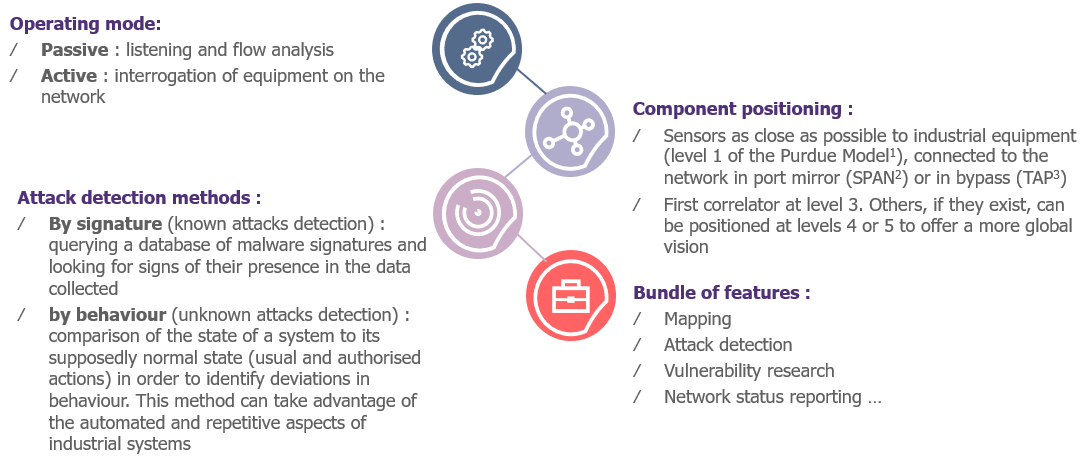
Figure 1: Main characteristics of an OT probe
Main functionalities
The functionalities of these OT probes are essential for their users. The illustration below presents a summary of the main functionalities identified:
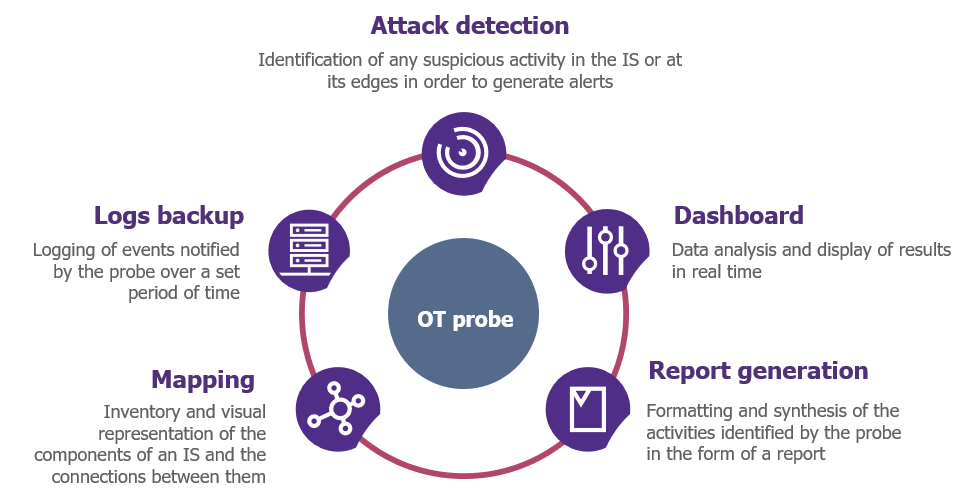
Figure 2: Main functionalities of an OT probe
More advanced functionalities also appear on some products, such as centralised management of several sites, provision of investigation guides, vulnerability research, etc. According to our observations, the solutions on the market tend towards the same objectives in structural and functional terms. The differences appear rather at the level of the global integration of the probe with the offers of the suppliers.
Our vision of the market: a market in the process of consolidation
Numerous and varied players
Our studies have enabled us to highlight a little over twenty players with diverse profiles on the OT probe market. Over the last five years, some players have appeared, others have disappeared, partnerships have been built and solutions have continued to evolve. All these elements indicate a market that is still in the process of consolidation.

Figure 3: Our market knowledge
Actors with different approaches
As might be expected in such a diverse market, different approaches to the sales model emerge. Some players put more emphasis on their product as such, while others emphasise its integration in their catalogues of services (threat intelligence, SOC, CSIRT…) or complementary products. These approaches naturally influence the contact between the players and their customers: the more the offer emphasises a service, the more the player will seek to have direct contact with his customer.
Our vision of the field: a need for maturity
Our feedback
At least initially, we recommend focusing on critical sites and processes for reasons of time, cost and skill savings. Moreover, in order to offer relevant behavioural detection, the probes require a significant learning time depending on the site on which they are deployed (identification of false positives, false negatives, accumulation of data for learning…). In addition to this time, significant human resources are required during this learning phase, but also later during the daily use of the product (mainly alert management). It will also be important to link the probe management teams and the incident response teams in order to deal with incidents detected by the probe and then confirmed.
Prior to deployment, the positioning of the probes should be studied. Indeed, it will be the key to both a complete mapping and an optimal detection surface. These initial considerations must address important points such as hardware compatibility (switches, for example) with the probes and the architecture of the site (on which the number of probes may depend). In addition to providing a real-time inventory, mapping can help implement or review network segmentation, an essential step in a security project. The qualification phase should also make it possible to check that the chosen probe will understand all the industrial protocols used and to discuss the processing of encrypted flows, if any.
Finally, of course, this type of project cannot be carried out without the integration, from the outset, of the OT teams.
A number of our clients stop at the test phase, but others have started to deploy probes on their critical sites or even on their entire industrial information system. The reasons given for not deploying probes are mainly related to costs, charges and required skills. The sovereignty of a detection probe can also be an important issue in certain environments.
Identified limits
In addition to the above points, technical limitations may also arise. Issues of bandwidth and network overload, induced by the collection of logs, can be anticipated. Moreover, an OT probe is by nature limited to network exchanges, its results (detected threats, security level evaluation…) are therefore to be put into perspective in relation to the resources at its disposal.
Finally, the probes ensure detection. On the other hand, the reaction must be carried out by other means, human or technological. More generally, with their many interesting functionalities, the probes are complementary to good security practices such as: the installation of antivirus and firewall, the implementation of a well of logs and adequate collection configurations, the construction of network documentation, the establishment of dedicated SOC and CSIRT teams… All these practices remain in force and will allow the full exploitation of the probes’ capacities.
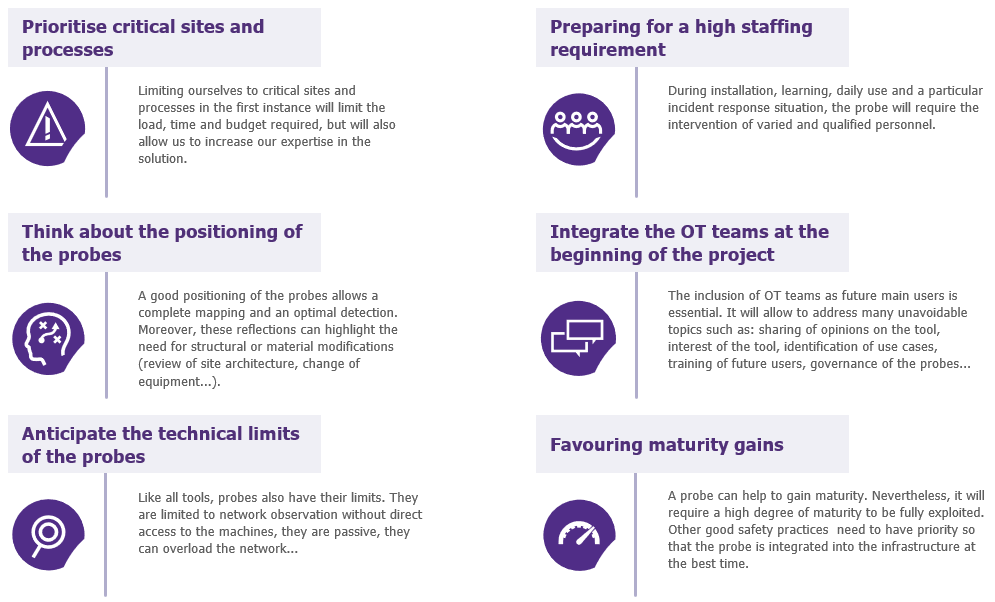
Figure 4: Our main feedback on the deployment of an OT probe
Conclusion
The probes offer a range of functionalities that meet real needs. Our meetings indicate that the market players continue to take into consideration the needs that have been brought to their attention in order to improve their product. Despite a consolidating market, the players seem to be technically converging towards extremely similar end products. Differences will be played out on ergonomic details, on the approaches adopted by each and on costs.
Our initial feedback shows the importance of the load and the skills required to use a probe. While they may be useful in an immature context, in order to help with system knowledge and the implementation of good network hygiene, they only really reveal their potential once they are fully integrated into the arsenal of detection and incident response teams, which corresponds to a highly mature context. Thus, it would seem to be a higher priority to follow the good practices outlined above in order to gain in maturity and then to consider deploying a probe in a second phase.
1: See https://en.wikipedia.org/wiki/Purdue_Enterprise_Reference_Architecture
2: See https://en.wikipedia.org/wiki/Port_mirroring


