Today, many companies have initiated a migration to the public cloud, and this brings its share of benefits, but also new attack surfaces. In this article, we will look at how companies can best manage their security posture, by verifying the correct configuration of resources.
Due to a lack of internal resources or expertise, it is still common to see configuration errors, such as a publicly deployed Storage Account or S3 bucket, allowing attackers to access and exfiltrate the data, or Network Security Groups that have not been properly configured to restrict flows, allowing attackers to compromise the cloud account through the exploitation of uncontrolled flows.
These misconfigurations create new surfaces of exposure and provide attackers with new ways to compromise IS.
Ensuring secure and controlled use of cloud services is a major challenge, which requires specific skills and appropriate governance.
What is cloud security posture management?
Cloud security posture management is a set of strategies and tools to reduce the security risks associated with cloud usage. This is achieved by implementing controls on the configuration of resources as well as mechanisms to react in case of detection of a deviation from good practices.
There are 4 main pillars in the management of the cloud security posture:

![]() One of the first steps in managing the cloud security posture is to understand the entire environment; inventory and classification of resources, compliance indicators, risk visualization dashboards, etc. This overview makes it possible to identify the exposed surface of the environment and to prioritize the work to be done.
One of the first steps in managing the cloud security posture is to understand the entire environment; inventory and classification of resources, compliance indicators, risk visualization dashboards, etc. This overview makes it possible to identify the exposed surface of the environment and to prioritize the work to be done.
![]() Effective cloud security posture management relies on several tools that automatically detect resource configurations that do not comply with good security practices. Most of the tools allow companies to assess themselves against standards and norms (CIS, GDPR, HIPAA, …) and thus identify gaps between the current environment and the target to be reached. In addition to the generic security rules proposed by the tools, companies can also integrate rules specific to their context in order to refine the controls carried out and thus build their own security framework.
Effective cloud security posture management relies on several tools that automatically detect resource configurations that do not comply with good security practices. Most of the tools allow companies to assess themselves against standards and norms (CIS, GDPR, HIPAA, …) and thus identify gaps between the current environment and the target to be reached. In addition to the generic security rules proposed by the tools, companies can also integrate rules specific to their context in order to refine the controls carried out and thus build their own security framework.
![]() Cloud environments offer advanced industrialization and automation capabilities that enable the rapid deployment of new solutions to reduce time to market, the time it takes to bring an idea to fruition and deliver a finished product to consumers. In this context of rapid evolution, it is necessary to ensure continuous monitoring of the environment in order to be able to react as quickly as possible when a non-compliant resource is deployed: quarantine of the resource, automatic remediation, etc.
Cloud environments offer advanced industrialization and automation capabilities that enable the rapid deployment of new solutions to reduce time to market, the time it takes to bring an idea to fruition and deliver a finished product to consumers. In this context of rapid evolution, it is necessary to ensure continuous monitoring of the environment in order to be able to react as quickly as possible when a non-compliant resource is deployed: quarantine of the resource, automatic remediation, etc.
![]() One of the challenges of security is to succeed in integrating it as early as possible in the project cycle, in order to limit the impact of misconfiguration of a resource. To give an example, as part of the management of the security posture, it is possible to integrate compliance controls from the development phase with the integration of Terraform or CloudFormation template analysis in the CI/CD chains. Note that this step requires advanced maturity and mastery of the other three pillars mentioned above.
One of the challenges of security is to succeed in integrating it as early as possible in the project cycle, in order to limit the impact of misconfiguration of a resource. To give an example, as part of the management of the security posture, it is possible to integrate compliance controls from the development phase with the integration of Terraform or CloudFormation template analysis in the CI/CD chains. Note that this step requires advanced maturity and mastery of the other three pillars mentioned above.
Focus on CSPM tools: which type of tool for which use case?
CSPM (Cloud Security Posture Management) tools are a range of software that can assist companies in managing their cloud security posture. There are many of them on the market, which we will distinguish into 3 main categories:
- Tools from market publishers (e.g., Prisma Cloud, Cloud Conformity, Cloud Health, CloudGuard, Zscaler, Aquasec…)
- Native tools from cloud providers (e.g., Microsoft Defender for Cloud & Azure policy, AWS config…)
- Open-source tools (e.g., Cloud Custodian, ScoutSuite…).
Although these tools have a common objective, there are many differences, and it is important to study the impacts in order to determine the most appropriate solution for the local context. Some examples of points of attention when selecting a CSPM tool:
Governance and administration of the tool:
What resources are available to facilitate the management of the tool (e.g., available roles and RBAC model, implemented processes, management interface, possible interconnections, etc.)?
Tool coverage:
Is the tool single or multi-cloud? What services are supported? What security rules are implemented in the tool?
Tool features:
What are the dashboard capabilities? Is it possible to set up alerts? Some CSPM tools specialize in one or more of the security posture management pillars mentioned above or are more mature for one cloud provider than for others. It is important to study the features offered by each tool to ensure that it covers all the desired use cases.
Ease of deployment:
How is the tool deployed? How long does it take? Is the tool available in SaaS mode or does it require the implementation of a specific architecture?
Ease of use:
How is the user interface? This criterion is particularly important because some tools, although very flexible, require specific skills (e.g., scripting) and may require detailed knowledge of the subject.
Available support:
Are security standards updated automatically? How long do new cloud services take to implement after they are released? The cloud is a very evolving environment, new services are regularly made available, implying new security risks. The ability of a CSPM vendor to adapt to its customers’ evolutions by proposing new rules and supported services is therefore a major asset.
Pricing:
What is the pricing model? Do we have to pay per resource? How many people are needed to administer the tool? Depending on the tool chosen, prices can vary widely. Particular attention must be paid to the choice of a solution that is well sized in relation to the expectations expressed.
Based on these criteria, it is possible to observe major trends shared by tools in the same category.
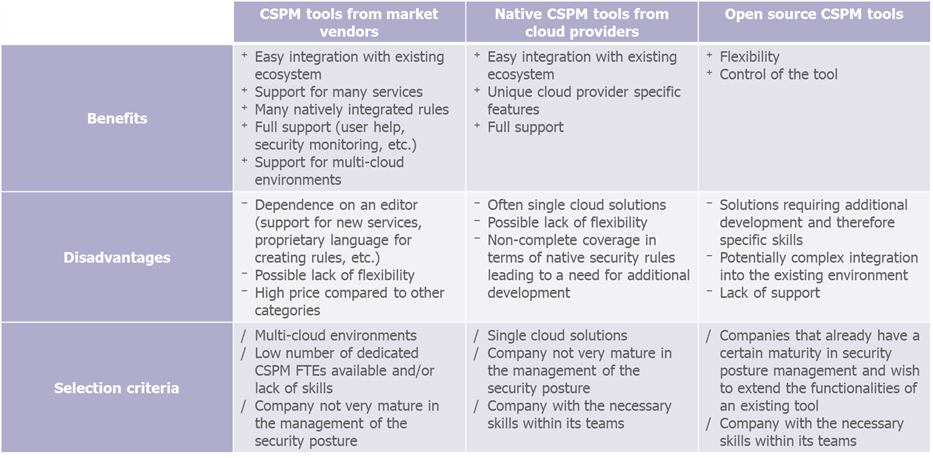
To summarize: CSPM tools from market vendors offer a lot of functionality that is easily deployable but not very customizable.
Native CSPM tools from cloud providers are easily integrated into the existing ecosystem and have cloud provider-specific functionality, which does not always cover all needs.
As for open-source tools, they have the advantage of being very flexible and giving the user a great deal of leeway, but these tools are complex to maintain over time and require specific skills to be deployed and used.
Choosing the most appropriate type of tool therefore requires identifying the challenges specific to one’s context and studying how each type of solution responds according to its characteristics.
Here are some examples of questions an enterprise might ask when selecting a CSPM tool: Is the enterprise’s security posture management maturity appropriate for its current use of the cloud? If not, is the delay in tooling or in the definition of security best practices in a Group framework? Does the company have the internal skills to ensure that the management of the security posture evolves at the same speed as the business needs of cloud usage?
Indeed, the choice of a CSPM tool must be part of a more global process of managing the security posture, in other words, by relying on the company’s local governance and expertise capacities.
CSPM industrialization: the key steps
Implementing an effective security posture management is a long process with several steps. Any company wishing to gain in maturity on the subject must define an industrialization strategy allowing to progressively reach the target. The following chart is an example of an industrialization strategy:
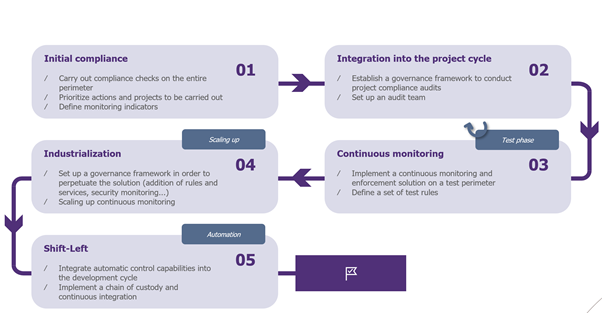
This consists firstly of the initial compliance of the cloud environments to secure them. This phase can be carried out using cloud native CSPM tools or using a tool from the market. The advantage of these tools is that they provide a framework and generic security rules on which a company with little experience in this area can rely. In order to capitalize on the tool’s feedback, a governance and action plan must be put in place to:
- Prioritize the identified projects
- Define indicators for monitoring compliance (e.g., percentage of resource compliance by service and/or by criticality)
- Support projects in bringing their environment into compliance by providing them with the necessary elements to remediate non-conformities
Once the desired minimum level of security has been reached (or in parallel with the initial compliance), one of the next challenges is to ensure that new cloud projects do not create new vulnerabilities. It is therefore necessary to set up a structure to support development teams in their cloud projects. This structure should allow the following:
- Maintain a group cloud security repository that is adapted to the company’s context and evolves with the demands of new business use cases
- The implementation of security validation processes (automated or not) in order to validate the various project stages (cloud eligibility, transition from development environment to production, etc.)
- Security monitoring of cloud services used within the company
The first two steps allow to secure the existing and future evolutions.
The next two steps aim to add a layer of additional validations and controls to perpetuate the use of best practices throughout the organization. In order to implement a generalized continuous monitoring, it is preferable to initially focus on a test perimeter; this test phase allows to:
- Test a new approach in terms of monitoring infrastructure. Technically, this means setting up the CSPM tool(s) needed to ensure both spot audits on a specific perimeter and continuous monitoring of the entire test perimeter. From an organizational point of view, this translates into the implementation of validation processes and specialized teams.
- Define organization-wide control points and mechanisms to ensure their durability: management of the life cycle of security rules, definition of remediation actions per rule, etc.
- Prepare the scaling of continuous monitoring.
Based on the feedback from the previous test phase, the scope of continuous monitoring can then be extended to industrialize the management of cloud security posture within the organization.
The last step corresponds to the last pillar of cloud security posture management, anticipation, and therefore the implementation of advanced features to improve existing practices. Security is integrated upstream of the production launch, i.e., on the left side of this cycle, which is called the “shift-left”.
Synthesis
Managing the cloud security posture within an organization is a major challenge with strong impacts requiring a progressive and incremental implementation.
By relying on the four pillars of security posture management – Visualize, Control, Monitor, Shift-Left; companies are able to ensure the compliance of their cloud environment while following the needs and changes of the business. This objective requires dedicated governance and tools adapted to the local context, all of which evolve with the company’s cloud security maturity.
There are many CSPM solutions available and each one has its own benefits and disadvantages. Particular attention should be paid to the study of the solution that is best suited to the needs expressed and to the future developments envisaged.


