During protests in Philadelphia towards the end of May 2020, two police vehicles were set on fire. Photos of the event posted on Instagram and cross-referencing of aliases, visible on Etsy, Poshmark and LinkedIn, will lead[1] an FBI investigator to suspect a person who will later be convicted.
- In this case, FBI used Open-Source INTelligence (OSINT) techniques.
Overview and use cases
Behind the myriad of acronyms related to OSINT (SOCMINT, GEOINT and so on) lies a single methodology: identify and consolidate a variety of information related to a target, using publicly available tools and services. Similar to technical audit activities, the underlying approach will be iterative, with its share of false positives and dead ends.
Regardless of the information sought, the techniques used can range from complete passivity (search without being authenticated, without leaving any trace) to a much stronger interactivity (sending emails, subscriptions, or interaction on social networks …).
Although this specific field of cyber is rapidly evolving, the constants will be:
- Remain humble and critical about the quality of the sources and information retrieved.
- Be aware of the traces generated and left as a result of our research.
- Consider legal aspects, including research and retention of personal data.
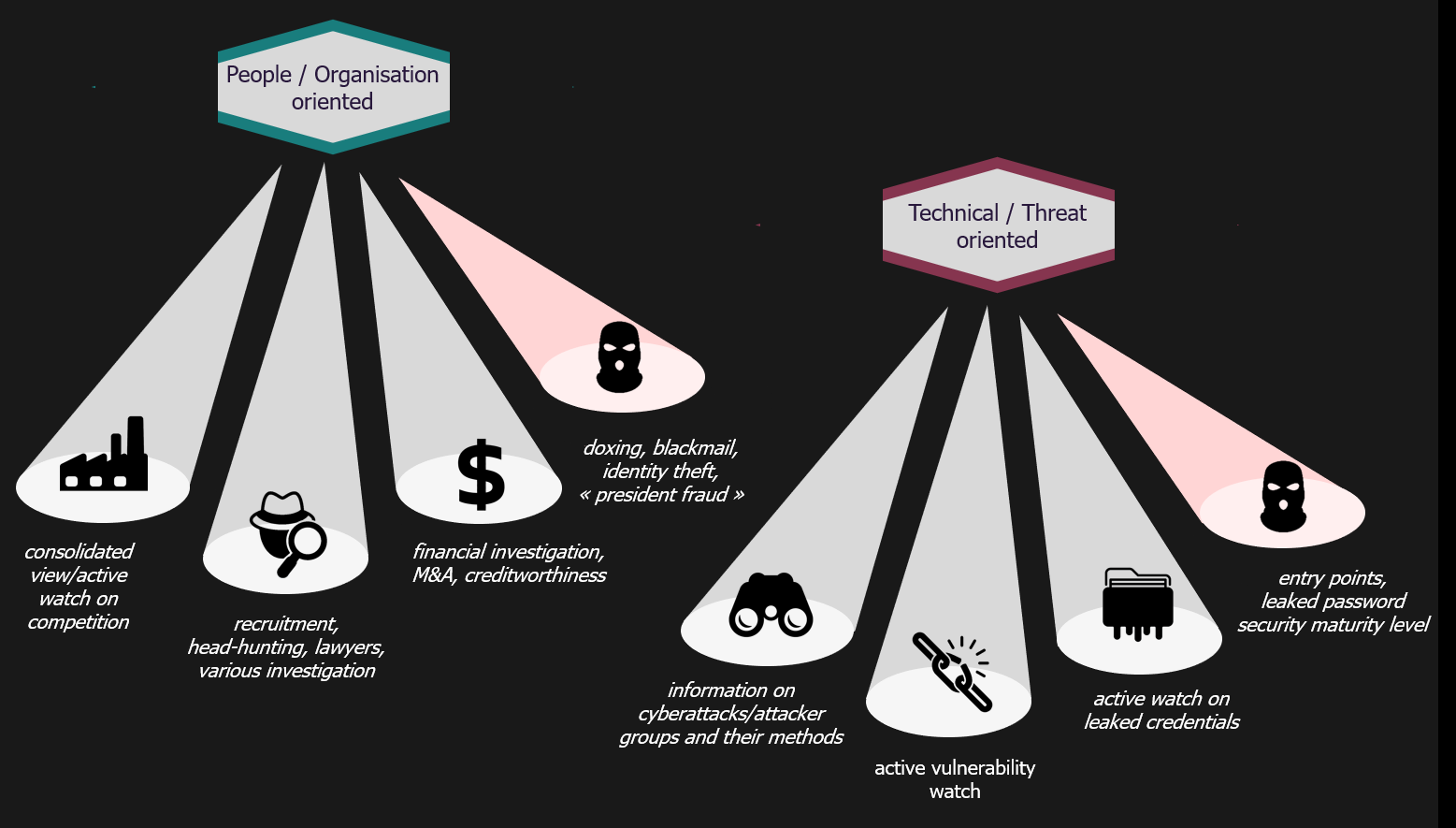
At present, the possibilities offered by OSINT methods and tools make it possible to consolidate information in various fields:
- On the organizational and human side, it will be mainly financial investigations, obtaining a consolidated view of the competition, headhunters, or lawyers.
- On the technical side, the objective may be to conduct a proactive watch on actors and threats, or to obtain an overview of an organization’s exposure on the Internet, looking for technical entry points or leaked data.
In both cases, attackers deploy similar methodologies to achieve their goals, whether it’s doxing, blackmail, fraud, or simply the reconnaissance phase of a larger cyber attack.
What market for OSINT?
The OSINT market is growing rapidly (+20 to +25% per year on average according to studies[2]).
These include players related to marketing solutions, business intelligence and homeland security; as well as players related to cyber threat intelligence or the provision of more OSINT-specific solutions.
- Marketing intelligence platforms, such as Brandwatch, Cikisi or Digimind, which are able to analyze what is being said about a brand on social networks.
- Players specialized in consulting and investigations in the field of economic intelligence, such as Avisa partners/CEIS, ADIT or Axis&Co.
- Homeland security oriented solutions, with players:
- French, such as Thales with OSINTLab used by the Gendarmerie Nationale or Airbus ;
- foreign, such as the American Palantir, used temporarily by French governmental administrations, while waiting for a sovereign alternative encouraged by the public authorities[3].
- Cyber threat intelligence actors:
- working more classically on attacker groups, trends, vulnerabilities, such as Sekoia and Tehtris;
- having the ability to automate searches, such as information leaks based on keywords (e.g., CybelAngel) or the digital footprint of a set of people (e.g. AnozrWay).
- Providers of specific commercial solutions, used in particular for:
- automated monitoring of Web data sources, or even the Darknet, such as Fivecast Onyx or Aleph Networks;
- transcription/indexation of speech from videos posted online, such as Chapvision and natural language processing, such as expert.ai;
- investigation assistance, such as Maltego or Osidian.
Tools
The panel of essential OSINT tools is constantly changing and can be largely adapted according to the objectives set. We mainly count the following typologies:
- Public tools, such as major search engines (Google, Yandex, Bing …) and their reverse lookup services, storage and archive sites (Pastebeen, WaybackMachine …), tracking services (airplanes, boats …) as well as some social networks.
- Specialized SaaS services, often with trial offers or free versions, but which often limit the quantity and quality of the information presented. The use cases can be oriented towards people search (Lusha, Kaspr, Anywho, Hunter.io …), face search (TinEye, PimEyes), technical information search (Shodan, IntelX.io, Onyphe, BinaryEdge), or even leak search (HaveIbeenpwnd, DeHashed …).
Various toolkits, including complete frameworks (Maltego, Lampyre), as well as a large number of open-source tools and scripts (GHunt, Maigret, Phoneinfoga …). Most of these tools will be based on automation via Selenium and will be confronted with the API limitations and possible countermeasures of the targeted services.
Within the framework of an investigation, the key will be to position our needs on the triptych Quality of information / Price of information / Simplicity of access (speed, specific developments…), and to adapt the choice of tools accordingly, given the time and financial means deployed.
The legal framework surrounding OSINT activities is often vague and may depend on the country or geographical area, the durability of certain tools and platforms is never guaranteed. This is why it is useful to have a redundant toolbox and to update it regularly. As an example, the technical information search site Spyse, mainly hosted in Ukraine, has seen its services interrupted since March 2022.
How to protect yourself from malicious use of OSINT?
Three pieces of advice can be given to actors wishing to limit the exposure of their digital footprint:
1/ (Have) your digital footprint searched on the Internet and clean up what can be cleaned up (close unnecessary accounts, do not expose unwanted information – especially using privacy settings).
2/ Diversify and hide your logins and passwords (e.g. avoid leaving information that can be linked to your identity in the accounts you choose or that are offered to you by default).
3/ Before posting public content, think about whether its content could be exploited against you; talk about this subject with your friends and family, reminding them that the Internet does not forget.
What regulatory framework applies to OSINT?
There is no specific regulatory framework applicable to OSINT in France, which is also generally the case abroad. The existing legal framework is however applicable, in particular:
- The Godefrain law, which will repress the fact of accessing, fraudulently remaining in an information system, extracting, holding, or fraudulently reproducing its information. The fraudulent character can in some cases consist in bypassing a simple security mechanism or in downloading files exposed by mistake. It is assessed, on a case-by-case basis, by judges whose level of familiarity with digital technology may vary.
- The General Data Protection Regulation (GDPR). For example, the CNIL condemned in October 2022 the company ClearView AI, champion of the indexing of face photos on the Internet. Clearview announced a target of 100 billion indexed photos, which was 10 times more than in 2020.
In addition to the regulatory framework applicable to the countries concerned, whose jurisprudence may diverge, it is desirable that the players conducting OSINT activities adhere to a framework of good practices. In this respect, we can mention the Berkeley Protocol, even if it is more specifically oriented towards investigations.
What can OSINT concretely bring to cybersecurity?
The proliferation of OSINT techniques and tools accessible to the greatest number of people can facilitate its use and its industrialization for offensive purposes, with regard to information systems, people and organizations.
Putting oneself in the shoes of an attacker, by using OSINT as he does, is a way to better protect oneself. This is how OSINT finds its place in certain risk analyses, awareness-raising initiatives for people at risk, or RedTeam missions. But always within a legal and ethical framework to which the attacker will not adhere.
_________________________________
[1] Detail of the report https://heavy.com/wp-content/uploads/2020/06/merged_87745_-1-1592492707.pdf
[2] Including Open-Source Intelligence (OSINT) Market by GMInsights https://www.gminsights.com/industry-analysis/open-source-intelligence-osint-market and Open-Source Intelligence (OSINT) Market by Market Research Future https://www.marketresearchfuture.com/reports/open-source-intelligence-market-4545
[3] “Chapsvision annonce l’acquisition d’Ockham Solutions après avoir finalisé celle de Deveryware” https://www.aefinfo.fr/depeche/680407 and “Une alternative française au logiciel d’analyse de données de Palantir est possible, d’après Thales” https://www.usine-digitale.fr/article/une-alternative-francaise-au-logiciel-d-analyse-de-donnees-de-palantir-est-possible-d-apres-thales.N1020429


