Internet of Things (IoT) platforms enable the connection, management and monitoring of fleets of devices. The 3 cloud leaders, GCP, AWS and Azure each have their own offering, in a particularly fragmented sector, which sees many players competing.
Azure, in recent years, has been gaining a foothold in this sector, as Gartner has pointed out, ranking them among the visionary leaders of Industrial IoT (IIoT) platforms [1] due to its capabilities, and its almost complete coverage of all use cases and industries.
The IoT, by nature often widely exposed, even on the Internet, can be the target of attacks. It is therefore essential to put in place security mechanisms, and to apply best practices to improve the security level of the platform and the objects that connect to it, which we will explore in this article.
Before moving on to specific recommendations for protecting your IoT devices and data, let’s look at how the various Azure IoT services can be used together to create secure IoT solutions.
Presentation of the Azure IoT offer
Microsoft Azure IoT is an end-to-end platform for connectivity, analysis and visualization of data from IoT devices. It also offers interconnection with other standard Azure services such as Azure Machine Learning and Azure SQL Database.
Azure IoT offers two solution ecosystems to its customers:
- Azure IoT Central is a fully managed aPaaS, Platform as a Service application that simplifies the creation of IoT solutions. This service is responsible for connecting, managing and operating fleets of devices, and provides a management user interface. Azure IoT Central is an aggregate of different Azure IoT services such as Azure IoT Hub or Azure IoT Hub Device Provisioning Service (DPS).
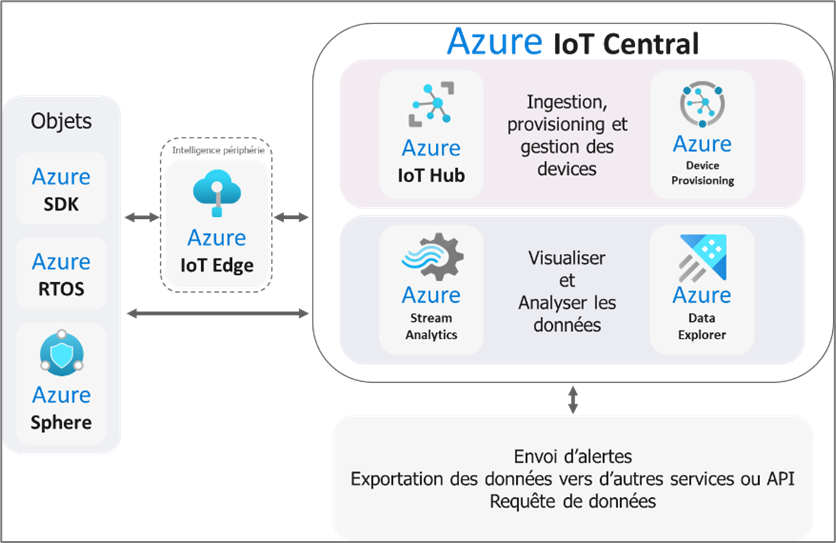
Azure IoT Central offers application models according to several business domains: Retail, Health, Energy, Industry, etc., and aims at a “turnkey” implementation.
- A customised ecosystem thanks to the various Azure PaaS (Platform as a Service) services. In this ecosystem, two services; Azure IoT Hub and Azure Digital Twins are the foundations of an IoT solution. We have also combined them with Azure Device Provisioning and Azure Device Update for optimal coverage of cyber security needs.
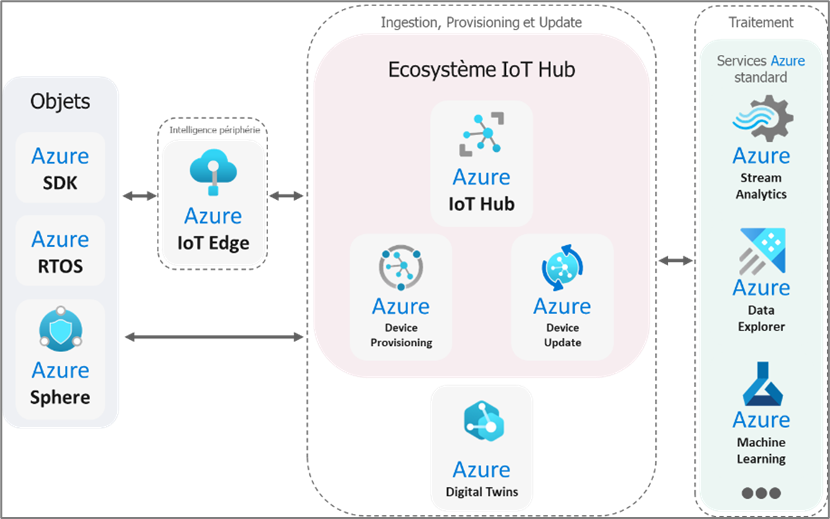
These two ecosystems enable Azure to address all types of IoT and IIoT needs:
- Azure IoT Central offers a complete service if you want to quickly develop a low-complexity application thanks to its application template catalogue.
- If you want a custom solution, or with features not supported by Azure IoT Central: opt for an ecosystem based on Azure IoT Hub.
Now that we have a good understanding of the Azure IoT ecosystems, it is important to focus on securing these ecosystems. How can we effectively protect IoT devices and data when using Azure IoT services? This is what we will explore in the following sections.
Preamble: the Azure CLI tool
In order to manage Azure resources, Microsoft provides several tools, most of which can be used in CLI (Command Line Interface). The tool offering the most functionality for management is Azure CLI.
This tool, available for Windows and UNIX operating systems, allows a user who is a member of an Azure environment to manage and obtain information about Azure resources. It should be noted that the range of possibilities of this tool varies according to the rights that the user has over the resources in question.
To install it, Microsoft provides a dedicated page explaining the steps for any type of environment.
In order to use it, all you must do is connect to an Azure user account via the chosen command interface (PowerShell or Bash), then enter the desired commands. Once the use of this tool is finished, a disconnection of the account is recommended.
A typical use of this tool is shown below:
|
az login [-u Nom d’utilisateur] [–use-device] [Commandes Azure CLI] [Exemple : ] az logout |
The documentation of this tool, presenting and explaining all the possible commands, is available at this address.
This tool will be used later in the example of technical manipulations.
1st security vector: authentication of objects
Device authentication is crucial for an Azure infrastructure as it ensures that only authorised devices can access cloud resources. Azure IoT services support two main means of authentication for IoT devices:
- A SAS Token (Shared Access Signature) is a string of characters used to authenticate devices and services. An SAP token has the following structure:
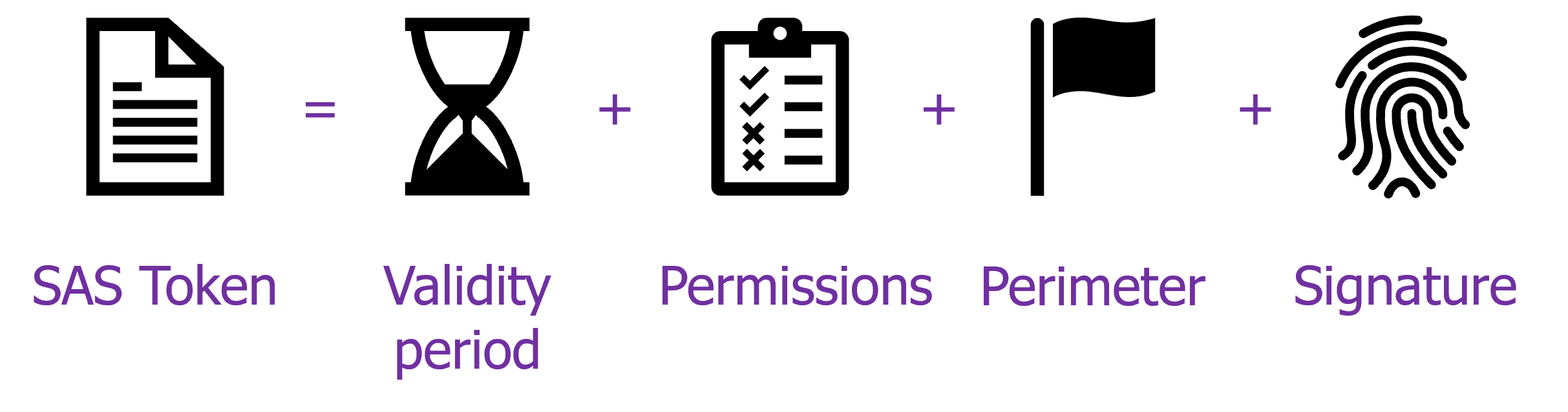
This type of authentication has a defined validity period and permissions, which are assigned based on an access policy, on a given perimeter. The signature, on the other hand, is a crucial element because it is responsible for guaranteeing the security of communications between the object and Azure services, but also for proving the identity of the device. This signature is generated from a secret that must be specific to each device.
- An X.509 certificate [2] is a digital certificate allowing strong authentication of the object. It contains information about the entity issuing the certificate, the validity period of the certificate and the identity of the subject (e.g. the object). One of the strengths of certificates is the ability to create chains of certificates, and thus create trust relationships:
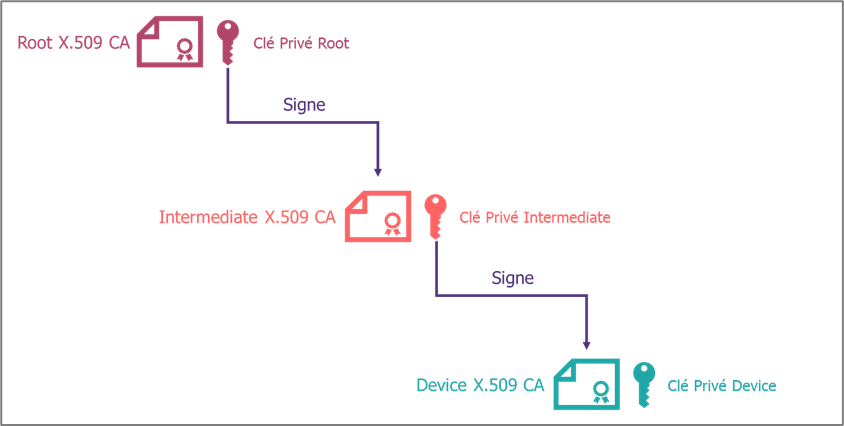
X.509 certificates offer a higher level of security, assuming a state-of-the-art cryptographic algorithm, as they allow trust relationships to be represented. However, the management and use of certificates can involve additional complexity for an IoT project.
In order to force the use of X.509 certificates to authenticate connected objects, it is possible to prohibit SAS tokens for an IoT Hub. Indeed, Azure IoT Hubs have three properties related to the use or not of SAS tokens: disableLocalAuth, disableDeviceSAS and disableModuleSAS. Therefore, the best practice associated with disabling SAS tokens is to set these three parameters to True. This can be done using the Azure CLI tool:
|
az resource update –resource-group <Resource_Group> -n <IoT_Hub> –resource-type Microsoft.Devices/IotHubs –set properties.disableDeviceSAS=true properties.disableModuleSAS=true properties.disableLocalAuth=true |
Checking the values of these same parameters can also be done using the Azure CLI:
|
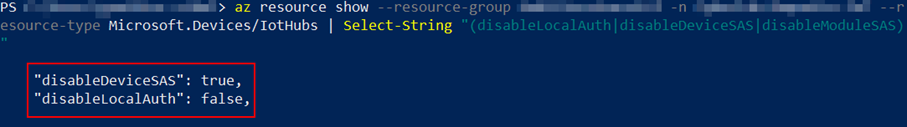
az resource show —resource-group <Resource_Group> -n <IoT_Hub> –resource-type Microsoft.Devices/IotHubs | Select-String “(disableLocalAuth|disableDeviceSAS|disableModuleSAS)” |
In the example response below, the disableDeviceSAS property has been set correctly, but the other two have not.
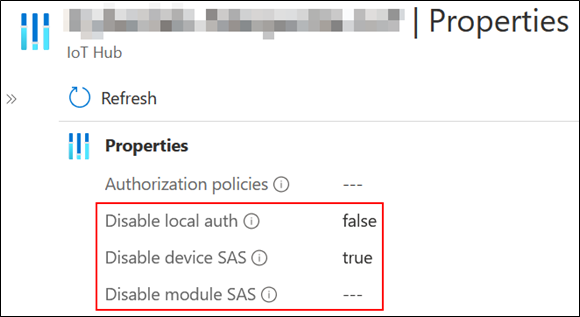
The Azure portal also allows you to perform this verification:
The choice of authentication method for Azure IoT will depend on the security requirements of your solution. If you need strong security and have the infrastructure to manage certificates, then X.509 certificate authentication is a good option. However, if you are looking for a solution that is simple to manage and use, the SAS token may be more suitable for your needs.
2nd security vector: RBAC and alerts
The assignment of roles on your Azure IoT infrastructure must be thoughtful and defined according to the needs of the users. A precise definition of roles and permissions makes it possible to limit access to resources and to the various functionalities available on the platform. The various Azure IoT services provide a multitude of pre-configured roles that can be adapted to your needs and your organisation. Secondly, applying the principle of least privilege, and limiting the number of accounts with important privileges, allows you to improve the security level of your Azure IoT infrastructure.
Azure CLI allows you to list the users with rights to the desired Azure IoT resource and their associated roles. The following command allows you to perform this action
|
az role assignment list –scope “/subscriptions/<ID_de_souscription>/resourceGroups/<Resource_Group>/providers/Microsoft.Devices/IotHubs/<IoT_Hub>” –include-inherited |
It is possible to use string selectors (Select-String for PowerShell, grep for Bash) to retrieve only the desired information.
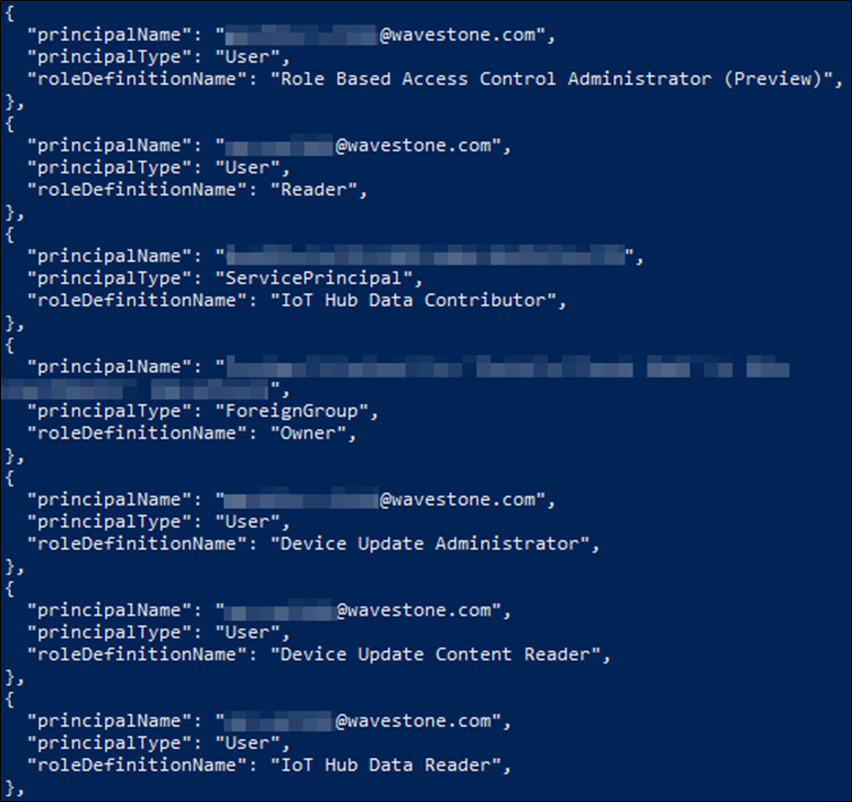
In the example below, names, types and roles were the only items retrieved using Select-String:
The Azure built-in roles feature is available on this page.
Configuring alerts based on the metrics of your Azure IoT services is another tool to consider. Alerts can be configured to detect suspicious behaviour or anomalies, allowing for rapid investigation of your infrastructure. Azure provides its customers with a large collection of signals to define alert conditions. It is also possible to define custom alert signals via the query language used by Azure Log Analytics.
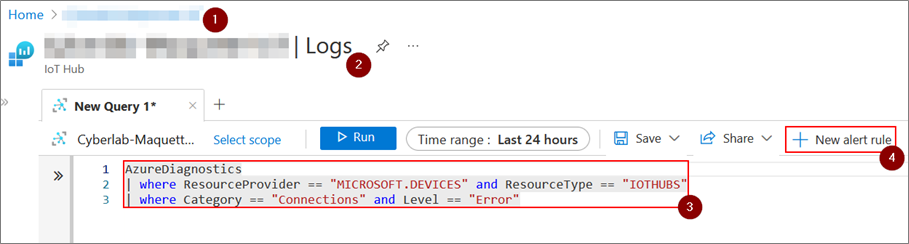
The Azure Portal is the easiest way to set up alerts based on the data collected by the IoT Hub. For example, to define a log alert rule, you need to:
- Go to the management page of the desired IoT Hub;
- Go to the Logs sub-category of the Monitoring category;
- Choose a rule using the Azure Log Analytics language;
- Add an alert rule related to this query;
- Choose the operator, unit, threshold value, check recurrence and time period for the rule
These actions are summarised in the screenshots below:
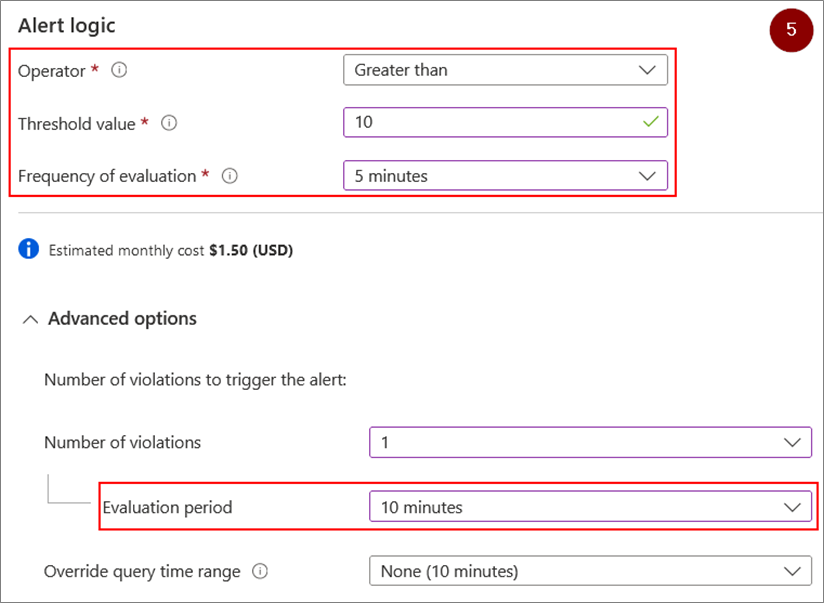
It will then be sufficient to choose an action group linked to a type of action (sending an email, SMS, etc.).
The example given will lead to an action if the number of failed connections of connected objects to the IoT Hub concerned exceeds 10 failures in 10 minutes or less.
A detailed guide in the form of a tutorial is available on the Azure documentation. Note that this service is available at an additional cost.
3rd vector of security: the service itself
Finally, setting up proper configuration of Azure IoT services is a key element in improving the platform’s cyber maturity level. This includes options such as routing rules or setting the minimum version of TLS used by devices to connect to Azure IoT Hub.
Routing rules are used to redirect messages from IoT devices to an endpoint (storage, services, database, etc.) and are configurable by routing requests. It is recommended to filter incoming messages, via routing requests, to increase the security of your IoT solution.
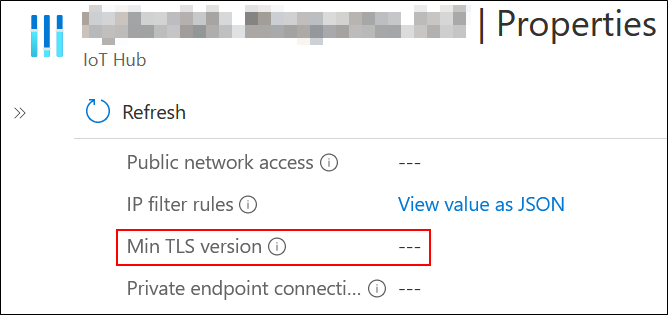
Checking the minimum TLS version accepted can be done using the Azure CLI: indeed, an IoT Hub has the minTlsVersion attribute to check this property. This check is performed using the following command:
|
az resource show —resource-group <Resource_Group> -n <IoT_Hub> –resource-type Microsoft.Devices/IotHubs | Select-String “minTlsVersion” |
Si cette commande ne retourne rien, ou retourne une valeur inférieure à 1.2, alors la configuration n’est pas satisfaisante.
Le portail d’Azure permet également d’effectuer cette vérification
If this command returns nothing, or returns a value less than 1.2, then the configuration is not satisfactory.
The Azure portal also allows you to perform this check:
En synthèse
Security is a major issue for IoT projects: Microsoft, with its Azure IoT product, provides an IoT platform that meets the majority of IoT needs in a secure manner, provided that it is configured correctly. In this article, we have discussed recommendations for improving the security of your Azure IoT infrastructure.
It is important to keep in mind that other attack vectors exist, such as hardware and software vulnerabilities and the networks used by IoT devices. Securing an IoT infrastructure is a complex challenge that requires an end-to-end approach.
With the help of Marius ANDRE
[1] “Magic Quadrant for Global Industrial IoT Platforms”
https://www.gartner.com/doc/reprints?id=1-2BQFX3BJ&ct=221116&st=sb
[2] “Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile”


