On a daily basis, stakeholders within construction handle a variety of data that may be of interest to malicious parties. They are subjected to the same types of malware attacks as players in other industries (e.g. theft, espionage, phishing, etc.). The main data at risk are linked to business activities: exchanging legal documents, drawing up quotations, responding to calls for tender, studies and plans for projects involving sensitive areas such as fire safety, high and low voltage, access control, video surveillance, etc. The risk of cyber-attacks on this data have increased with the emergence of new working methods and tools (Building Information Modeling, collaborative and common data platforms, on-site robotics, connected objects, etc.).
According to the latest Digital Trust Insights study carried out by PwC in September 2019, 53% of the Engineering and Construction (AEC) companies surveyed (sample of 270 global companies) said that they had suffered from cyber incidents which had caused an interruption to their operations between 2017 and 2019.
Even French construction companies are not spared from targeted attacks to compromise data linked to sensitive projects. As an instance, Bouygues Construction has been targeted twice since 2019, and the latest attack in January 2020 caused a paralysis that affected more than 3,000 head office employees. The Rabot Dulliteul group was also attacked in July 2020, causing a slowdown in business. The attackers requested a ransom of 973 bitcoins (~€8 million) and threatened the group to disclose hacked information.
All these examples teach us that it is time to question engineering processes, from design to operation and maintenance, by identifying the cyber risks threatening these processes. Prevention methods need to be put in place to reduce their probability.
In this article, we will focus on one of the collaborative methods used within the construction industry, which could be a gateway to cyber attacks if the collaborative processes are not properly controlled and secured. This is known as the BIM method.
What do really hide behind the BIM term?
The BIM (Building Information Modeling) method is a digital collaboration process based on the creation and exploitation of a digital building asset. According to NF – EN ISO 19650, it is defined as the use of a shared digital representation of a built asset (buildings, bridges, roads, factories, etc.) to facilitate the design, construction and operation processes and form a reliable basis for decision-making. As a result, this digital asset represents the most valuable and sensitive asset in a construction project.

How does the BIM collaboration work and what assets does it rely on?
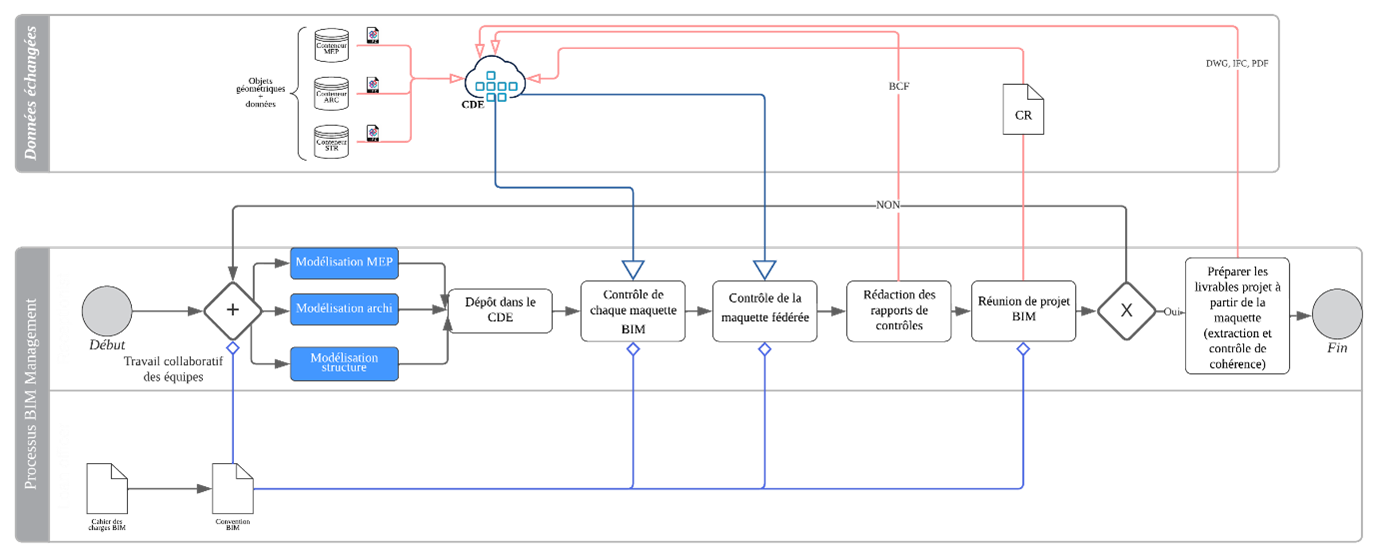
BIM collaboration process level 2 in compliance with NF ISO 19650
The BIM collaboration is essentially based on the exchange of data via models. The starting point is the modelling of business models (MEP, Architecture, Structure) based on the requirements of the BIM convention. These models are then uploaded to the CDE by the BIM coordinator for each discipline. The BIM Manager checks the mock-ups (semantic and geometric checks) and the synthesis unit compiles all the mock-ups into a single synthesis mock-up from which geometric conflicts are detected.
All these conflicts are passed on to the project team via reports in BCF format and are discussed and reviewed at the BIM project meeting. If all goes well, the summary model will be used to prepare the project deliverables, which are then published in the CDE in DWG, IFC and/or PDF format.

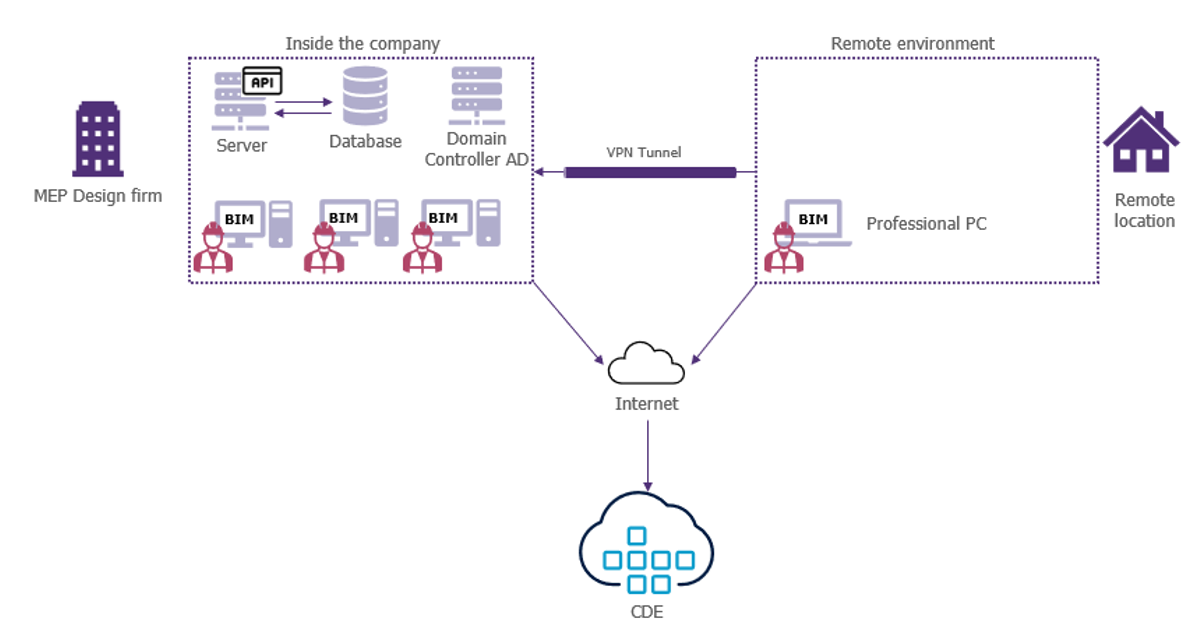
Example of an information system based on a collaborative MEP model
To understand the technical foundation on which BIM collaboration is based, we first need to focus on the information system hosting the models. To do this, we have taken the example of an MEP designer who is going to create a model within a design office.
In general, an MEP designer can work on the model either within the company by connecting to the local network or at home using his professional PC and a VPN enabling him to create a tunnel to his company’s local network.
In both cases, the data modified in the model is stored in a database hosted by the company. Access to the model is often uncontrolled within a design office and no authentication system is put in place to access resources as long as you are connected to the company’s local network.
The collaborative platform is then accessed via the Internet to publish the models and documents and share them with all relevant stakeholders.
What are the critical business processes associated with a BIM collaboration?
Digital mock-up management
The mock-up is an ideal target for attackers who want to access the data and exploit it for malicious purposes (blackmail, ransomware, physical attack on the building, etc.). They may aim to destroy all data, making it unavailable and inaccessible. To achieve this, it is essential to secure the model, and this cannot be done without ensuring the security of the data attached.
The security requirements of such an asset in terms of availability, integrity, confidentiality and traceability are very high.
On the one hand, a model that is unavailable due to the loss of a non-redundant server, for example, has a major financial impact. Penalties can start to be applied as soon as project milestones are no longer met. This unavailability can also affect the company’s image and tarnish the trust placed in it by partners.
On the other hand, the data and information contained in the objects of the model also contain a value. They must not be altered under any circumstances and must remain consistent with the data entered by the business specialists. In addition to the financial and image impact, this could lead to legal proceedings for failure to comply with contractual documents, and could also jeopardise the safety of people and property if the alterations are not detected.
Furthermore, the protection of data at rest and in transit is an essential element in case of data leaks. This data can affect sensitive areas such as networks, access control and fire alarms. Failure to comply with this requirement can have a major impact on the company’s financial situation and image, and can damage the safety of people and property, leading to prosecution.
In general, in the process of modelling a digital mock-up, several players can intervene in the modelling and make their own modifications. These actions must be traced and attributed to their author so that the person responsible can be identified in case of a problem. A lack of due diligence in traceability could easily have an impact on the project’s lead time, in which case the only solution is to revert to an older version instead of correcting the error made by the concerned person.
Creating and sharing of deliverables
Tampering with deliverables is a critical issue, because altering a calculation note or a working drawing can lead to the structural damage of a building, therefore endangering people’s lives. If we apply this logic to that of a nuclear power plant or a military building, the long term effects of this could be catastrophic.
Whether the deliverables are unavailable or leaked, these compromised scenarios have a major impact on data security and can have disastrous consequences for the design office in financial, operational and/or image terms, not to mention the impact on people.
What are the main risk scenarios associated with BIM collaboration?
Scenario 1: Loss of availability of a BIM model
One of the most common risks in BIM collaboration is the unavailability of a model following the failure of a server. In today’s construction industry, some companies are not yet fully aware of the challenges of cybersecurity and do not value the importance of server redundancy. They often use a single server or, in rare occasions, two servers located in the same geographical area, which will not cover all the risks that the building housing these servers could incur (fire, flood, power cut, etc.).
Scenario 2: Unauthorized access to the company’s IS and compromise of sensitive data linked to the model.
A company that only uses a simple authentication system based on login IDs and passwords remains vulnerable to external attacks. A malicious attacker can easily identify a vulnerability in the company’s information system and manage to compromise the credentials of an authorised user and gain access to the models hosted on the company’s servers.
The attacker will then be able to access all the sensitive data entered on the mock-up, in particular data related to high/low voltage, fire safety, video surveillance, air conditioning and ventilation. This data is likely to give him a detailed understanding of how the building works, and will enable him to steal the building plan or sell the data to external parties.
Scenario 3: Unauthorized access to the CDE and exploitation of access rights to deliverables
Similarly to scenario 2, a Common Data Environment without a strong authentication system cannot escape a potential attack, particularly if someone manages to recover a user’s login details using techniques such as phishing or social engineering.
Once the attacker has gained access to the CDE, they can exploit the access rights associated with that user to gain access to sensitive deliverables: plans, diagrams, specifications and any strategic and competitive data. These can then be destroyed or exploited to plan further attacks, or simply sold to third parties to give them a competitive advantage in the marketplace.
Scenario 4: use of external scripts or plugins and alteration or theft of sensitive data
Developing plugins in-house using the functions, methods and properties of the BIM design software API can sometimes seem complex and time-consuming. Some developers reuse scripts provided from sources online. Using these uncontrolled scripts can easily push a malicious element into the IS, subsequently causing access to be compromised. The attacker can then gain access to the model data and steal it for later use or alter it so that it will be unusable.
What are the recommendations to deal with these risks?
Taking into consideration the various security risks compromising the business values associated with a BIM process, it is vital to think about ways of securing the system so as to avoid any potential cyber threats that could jeopardize its IS foundation.
Strengthening the resilience of model servers
A digital mock-up can either be hosted locally on a company server or hosted in the cloud on a CDE. This does not prevent it from being unavailable due to the unavailability of the company’s IS or that of the CDE supplier’s IS.
Among the best practices for avoiding loss of access to a model :
- Redundancy of internal servers on the one hand to balance the load in case of excessive use and therefore ensure optimum performance and fluid access to the model, and on the other hand to ensure business continuity in the case of losing one of these servers. It is strongly recommended that servers are redundant in two different geographical zones to take account of all risks (fire, flood, blackout, etc.).
- Setting up regular back-ups and replicating data in several locations, so that data can be recovered in case of loss. It’s a good idea for these procedures to be tested regularly to check data integrity and to ensure that teams are able to carry out the restoration process smoothly.
Implementing multifactor authentication
As previously demonstrated, simple authentication to access the model from the company’s internal server or from a Common Data Environment is not enough to be protected from cyber attacks. It is now essential to introduce a strong factorial authentication mechanism (e.g. two-factor authentication) enabling the person to be identified accurately :
- TOTP (Time Based OTP): It is a one-time password based on time. The idea is to encourage users to enter two factors: their user name and password, and a unique six-digit code generated every 30 seconds.
- FIDO2key : It allows users to authenticate themselves in complete security using biometric data or a security key instead of a password.
- Smart Cards: This is a method of securing access to a resource. Users must have a physical or virtual card to access an internal company server or to connect to their CDE account.
It is important to emphasize that these mechanisms are given as an illustration and that the implementation of multifactor authentication is highly dependent on several parameters. On the one hand, it depends on the capacity of the server and infrastructure hosting the CDE and on its interoperability with other systems (ability to integrate with other third parties via API). On the other, we need to ensure that the authentication to be put in place is compatible with the users’ devices: types of device (desktop, tablet, phone, etc.), level of ownership (BYOD, COPE, COBO, etc.), operating systems (Windows, Linux, MacOs, Android, etc.).
Managing access and identity lifecycle
Managing identities and access to a CDE, which represents a goldmine for attackers, should not be taken lightly. Mastering the identity and access lifecycle is a prerequisite.
Identity management
If a new person joins the BIM team :
- Account creation : When a new person joins the organization, a user account must be created in the company’s IS or in the CDE following standardized procedures.
- Roles assignment : Depending on the individual’s role and responsibilities, appropriate roles and privileges must be assigned to access just the necessary resources.
In case of a change of position or mobility within the BIM team :
- Reassessment of privileges : This person’s access rights must be updated accordingly, revoking old privileges and granting new ones. It is therefore important to regularly reassess access privileges to ensure that they still correspond to the person’s actual needs.
If a member leaves the BIM team :
- Account deactivation : This person’s user account must be deactivated immediately to prevent any further unauthorized access.
- Cancellation of rights : All the individual’s access rights must be revoked, including access to systems, applications and data.
Access management
When assigning rights, access rights should be granted according to the principle of least privilege, i.e. users should only have access to the resources they need to carry out their professional tasks.
In addition, it is desirable that access rights should be requested by users, usually via an access request system, so that all requests can be traced and approved.
Regarding the approval of these rights, an approval process must be clearly defined, involving the appropriate managers, to ensure that requests are examined by the right people before being granted.
What is also important is to regularly review and reassess these access rights to ensure that they are still appropriate. If access rights are unused or unnecessary, they should be revoked to reduce the attack surface of the system.
Avoiding installation of plugins or using of unauthorized scripts
Now more than ever before, modelers, coordinators and BIM managers use Visual Programming scripts (Dynamo for Autodesk Revit, Grasshopper for Rhinoceros, etc.) or specific developments via C# or Python on the software’s IDE (Integrated Development Environment) using the API. These manipulations are not controlled and can be a cause of IS access compromise if something has been downloaded from the Internet.
In this case, it is advised to take safety measures such as :
- User privilege check: Access to installing plugins should only be given to users who need them for their work. To do this, simply limit administrative rights on workstations to prevent standard users from installing plugins.
- Centralized installation management : if the company has a centralized network, it is possible to manage plugin installations from an administrative server. This allows you to control which plugins are authorized to be installed on users’ workstations.
- Corporate network security : It’s a good idea to set up firewalls and network security devices to block access to unauthorized or suspicious websites, where users could download potentially malicious plugins.
- Controlling API calls: it is possible to use GPO group policies (on Windows environments with Active Directory) to disable these calls on the workstations of unauthorized users.
- Scripts check: It is recommended that a process for checking and approving scripts is put in place before they are used. It is also advisable to examine scripts in a test environment before using them in a production environment.
Conclusion
It’s clear that the use of Building Information Modeling (BIM) has revolutionized the way we design and manage built assets. However, this transformation has also opened new doors to cyber threats. In this article, we have explored the many cybersecurity issues in the context of digital design with BIM, highlighting the key risk scenarios and best practices for responding to them. It is important to note that the entire approach presented in the article is a cyber standard method adopted by many mature companies (banks, insurance companies, retail actors, etc.). It can be applied to any business sector, whether or not it is accustomed to cyber security.
It remains essential to see cyber security as a challenge that can be met with a proactive approach and concentrated efforts. As we continue to reap the benefits of BIM for the construction and management of modern infrastructure, the protection of our data and systems must remain at the heart of our concerns.
Cybersecurity remains not only an issue for BIM, but a challenge that affects many aspects of our modern lives. Rapidly evolving technologies and increasingly sophisticated cyber attacks demand constant vigilance. As a company, we must continue to invest in the research and development of new cybersecurity solutions and promote awareness of this critical issue.


