Today, cyber-attacks are part of our daily lives, and are becoming increasingly numerous and sophisticated.
Simultaneously, we are moving towards Information Systems built on an ever-increasing diversity of environments, thanks in particular to the Cloud, which is now an integral part within corporate Information Systems. This enables corporation to expand their capabilities, however it also the surface area and risks of attack.
Conventional intrusion detection and protection techniques already exist and are developing exponentially. These are effective against the most common attacks, however are not always adapted to the specificities of the Cloud.
This raises questions about the use of proactive strategies, such as Deceptive Security, to stay one step ahead of attackers. Particularly in the context of Cyber-Resilience: how can this kind of technology be used in both a traditional and a cloud environment?
When should Deceptive Security techniques be used? Are Deceptive Security solutions in the Cloud being developed today? Are there any specific strategies to consider in a Cloud environment as opposed to a traditional one?
We will answer these questions in a mini-series of 2 articles. In the first article, we will show you how to develop and evaluate your decoy strategy. In the second article, we’ll present a practical example of deceptive security in AWS.
Develop and evaluate your deceptive strategy
Ambitions of Deceptive Security
Deceptive Security in a nutshell
“Deceptive Security” (referred to as “Deceptive” in the rest of this article), or “digital decoying“, is a cyber-defense technique that deals with the intrusion of attackers into an IS (Information System). It works by setting up traps and/or decoys in an IS. These are designed to imitate legitimate technology, so as not to be identified as security systems/measures.
This method makes it possible to detect intrusions by generating alerts, to prevent damage to the actual infrastructure and to observe the practices used by the attacker.
Before delving into the details of this subject, we recommend reading the article “Deceptive Security : comment arroser l’arroseur ? “, which describes the main concepts of “Deceptive Security“.
The main objectives of Deceptive
The use of Deceptive on an IS can have several objectives:
- Detect an intrusion
- Distract the attacker
- Analyze the techniques used in the attack
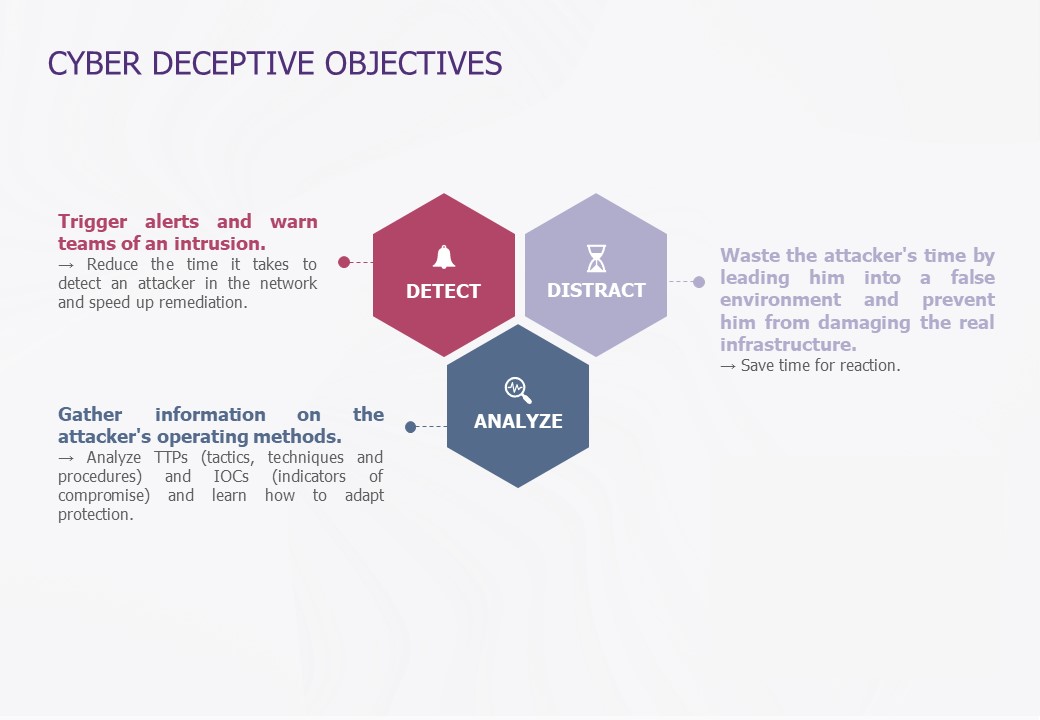
This technology can be used at different levels of maturity, depending on the needs identified.
The technology can be used to meet many of the needs mentioned above, but the key is to determine our requirements for this technology in advance. If we restrict the needs for detection, it should be noted that the configuration, deployment and maintenance of Deceptive will be far less complex than if we push the possibilities of this technology to the maximum (e.g. setting up complex scenarios to lure the attacker and strategic analysis of his actions).
The benefits of Deceptive
Why Deceptive ?
As discussed in the introduction, today’s cybersecurity challenges are fueled by the need to detect and react to growing attacks.
Deceptive does not replace existing standard cybersecurity solutions. Being a more complex tool, it acts as a complement to cover all types of attack, including the most sophisticated.
This technology is not designed to prevent an attack, but to alert security teams, minimize the effects of the attack and observe the intruder’s modus operandi (“Detect, Distract & Analyze”).
Honeypot VS Honeytoken
Presentation of concepts
Depending on the needs and how they are to be used, different types of decoys exist. Whatever the case, they take on the appearance of attributes that make up our Information System.
The best-known decoys are “honeypots”. These are servers or workstations that imitate real machines on the network. There’s also what’s known as a “honeynet”: a network of servers.
Another type of decoy is of growing in popularity. This is a decoy that hides directly on a system. These are generally represented by documents or other files whose role is to trigger an alert when someone comes to interact with them. Finally, we have “honeytokens”, which are data, information, often secrets or keys used to access a dummy resource on the IS (a honeypot, for example).
A fundamental difference
Traditionally, honeypots enable the observation and understanding of an attacker’s actions, as well as detecting an intrusion. The difficulty in this case is to configure a decoy that is attractive and credible enough for the attacker to fall into the trap, without delivering information that could compromise a component of our real infrastructure.
However, honeytokens can be more complex and enable the creation of a finer and more credible decoy. Without honeytokens, the probability of trapping an attacker is lower, and analysis results are not always reliable. The honeytoken’s dependence on its environment makes it more attractive in comparison to a honeypot, which represents no more than a trap with no possibility of subsequent escalation. For honeypots to be effective, we recommend deploying one or more complete honeynets, however it is important to consider the cost of such an infrastructure.
Cloud technology development
Today, the challenge for the most mature Deceptive solution vendors is to develop specific services in the Cloud.
Indeed, companies are increasingly using the Cloud to extend their storage, deploy virtual machines, containers and so on. This provision of services is very popular and effective, but at the same time, the interest of cyber-attackers is growing. Templates, or default configurations, make life easier for businesses, but can increase cybersecurity risks. Even though many Cloud providers are making great strides in this area, default configurations don’t always comply with IT security guidelines.
The Cloud is therefore a new playground for cyber-attackers. That’s why we’re focusing today on adapting our knowledge of Deceptive to protect Cloud environments and services too.
Overview of the main publishers on the market
It’s important to note that Deceptive is not reserved for overly complex applications. There are all kinds of offers on the market. Some companies offer services that enable you to obtain a complete off-the-shelf tool, while others focus on customization, lure quality and therefore the possibility of using their tool to create your own lures (configuration and maintenance not managed by the solution itself).
Here’s an overview of the main publishers and their solutions:
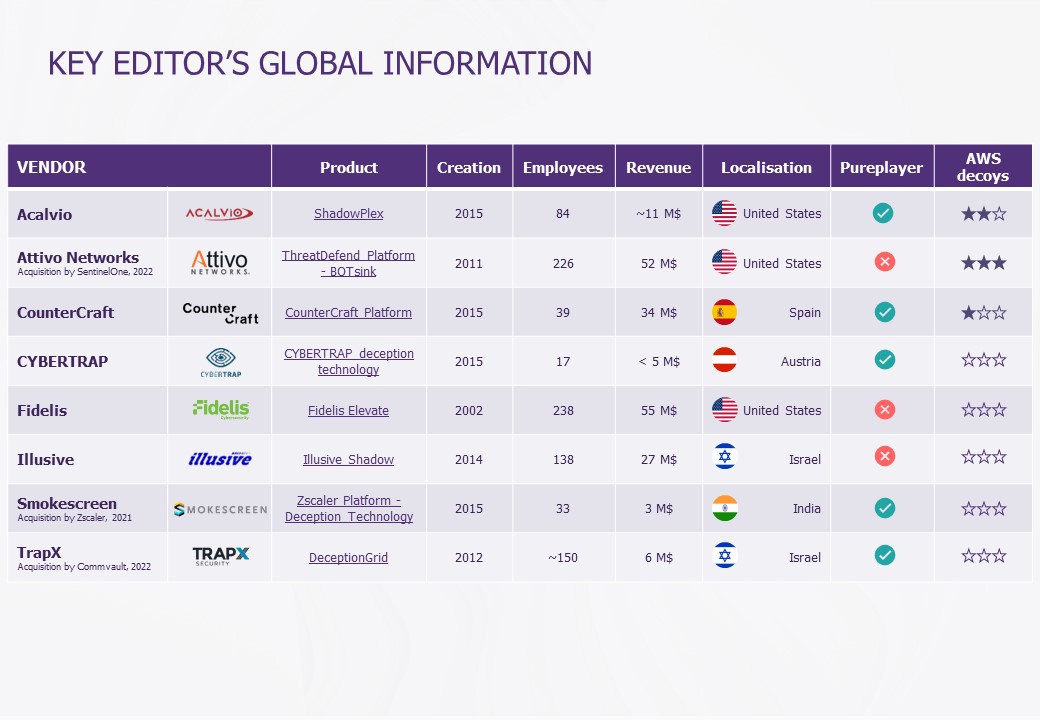
For some, the current trend is to join forces with other tools or integrate their solution with an EDR (Endpoint Detection and Response) to increase the effectiveness of the technology and meet market needs.
As mentioned above, the challenge that some have chosen to tackle is to adapt to a Cloud environment. For example, solutions such as “Attivo Networks”, acquired by SentinelOne, are developing Cloud AWS offers that propose the creation of decoys linked to the service (e.g.: EC2, S3, AWS access keys, etc.).
How to build and place decoys?
Deceptive strategies
Once you’ve familiarized yourself with this technology and all the possibilities it offers, it is worth asking yourself the question, what strategy or strategies you should adopt with regard to the number of traps and/or decoys to be implemented, and where they should be placed in the IS.
To adapt to different use cases, 3 strategies stand out, responding to distinct needs:
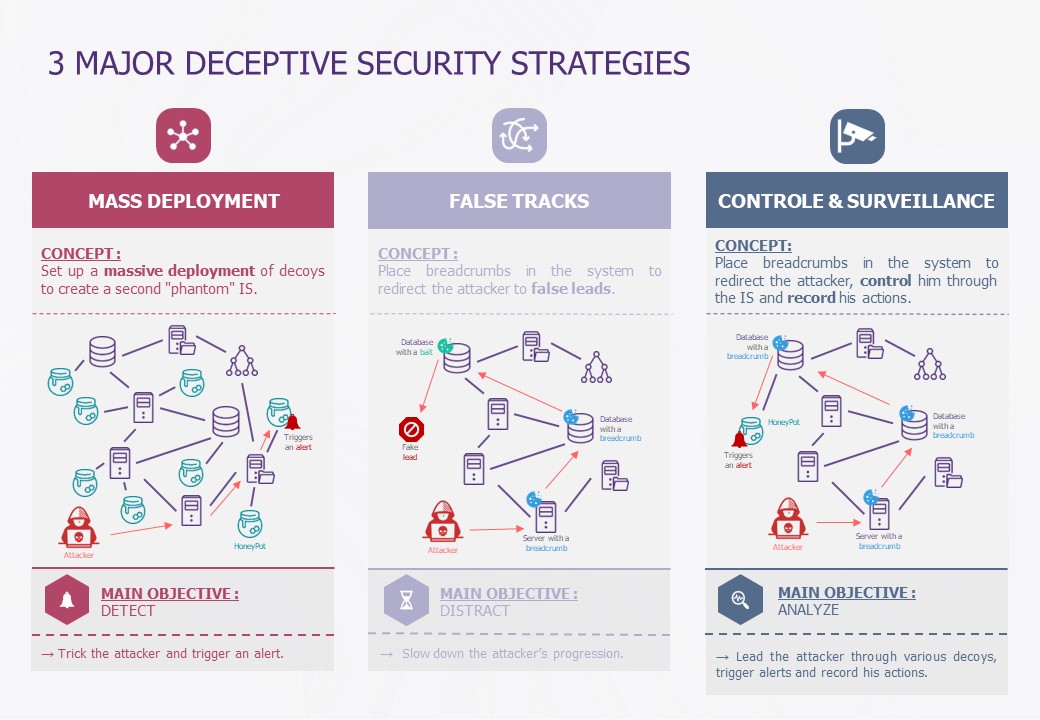
Indeed, the Deceptive strategy to be adopted is often tailor-made according to the IS infrastructure and, above all, according to the priorities and objectives defined beforehand.
By way of example: if you need to enrich your detection technologies within your IS, it may be worthwhile to study the strategy of “mass deployment” of decoys. The aim is to create a phantom IS, thereby increasing the likelihood of the cybercriminal falling into a trap that will trigger an alert to the security teams.
PARCS matrix
The challenge when talking about Deceptive, and more specifically about lures, is to answer the questions: What is a good lure? How do you create a good lure? Where to place it? How many to place? etc.
The article “ HoneyWISE : stratégie d’exploitation d’honeytokens en environnement Active Directory ”, written by Augustin TOURNYOL-DU-CLOS and Nathan FAEDDA, proposes a decoy strategy against certain attacks in a specific context: AD (Active Directory). We’ll also look at honeytokens in comparison with honeypots in the rest of this article.
The objective of this study was to simply test the implementation of decoys within the AD and to measure their effectiveness using the “PARCS” matrix.
PARCS was born on the basis of 5 criteria, originally conceived in the context of an AD environment but applicable to all environments:
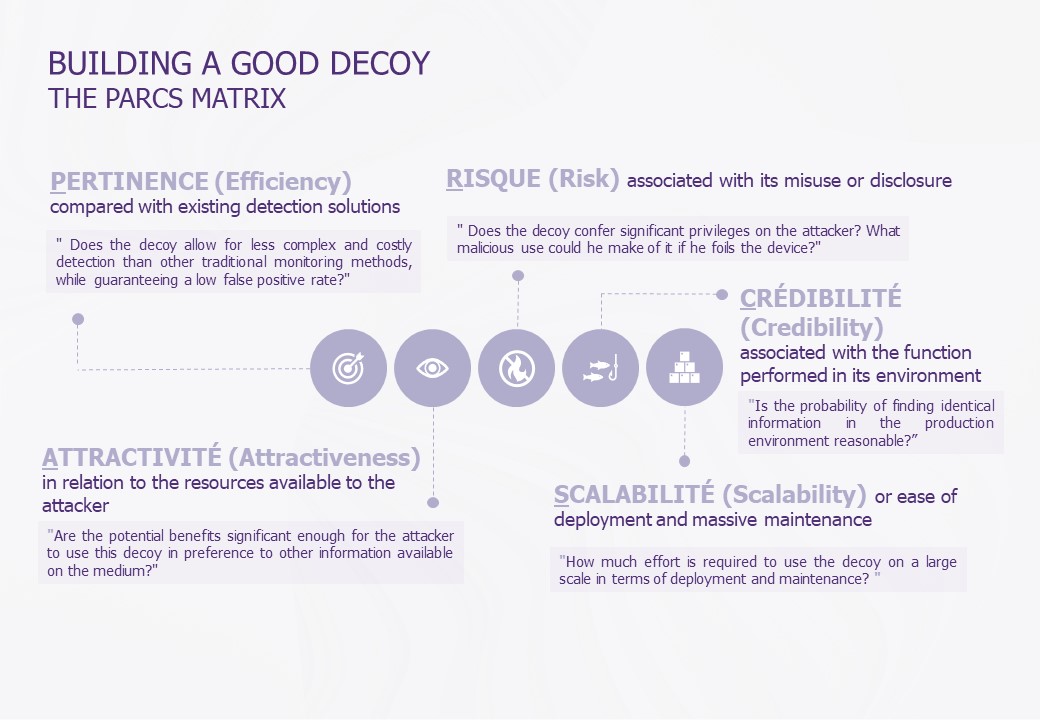
When designing a decoy, it’s a good idea to prepare a PARCS to check your thinking and ensure that it matches your expectations. It is also important to take into consideration minimum requirements illustrated by these 5 criteria: Relevance, Risk, Credibility, Attractiveness and Scalability.
The objective of this matrix is to determine a balance between importance and priority based on these criteria’s (Is the lure’s attractiveness important in my use case? Do I need a scalable solution? How scalable? etc.).
Example of PARCS use: Kerberoasting scenario “Stealing or falsifying Kerberos tickets”
Perhaps the best way to illustrate the PARCS matrix presentation is with an example from the “ HoneyWISE ” article.
The AD attack called Kerberoasting is, “[…] in synthesis, the offline brute force (no logon failure) of a Kerberos ticket receiving the secret of a service account, without having to send a single packet to this service or even being the local administrator of the compromised workstation”.
“Kerberoasting […] hijacks the native operation of Kerberos in order to carry out an attack. This hijacking takes place on steps 3 and 4 of the Kerberos authentication process, as shown in the following diagram”:
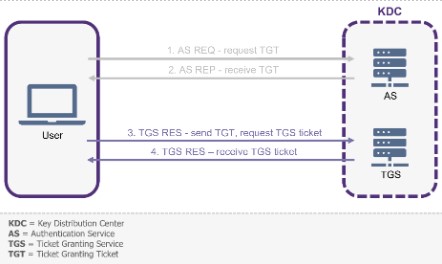
For this attack case, Augustin TOURNYOL-DU-CLOS and Nathan FAEDDA propose in their article to deploy a honeytoken against Kerberoasting (see part 2.3 “Description of detection scenarios” – scenario 2).
Here is the result, through PARCS, of the study of this type of honeytoken in the context of a Kerberoasting scenario (16/20):
- Pertinence (efficiency): 4/4
- « The alerts generated by this honeytoken are reliable. In fact, as soon as a TGS ticket is requested to access an unused and non-existent service, it becomes clear that a malicious action is underway. »
- Attractivité (attractiveness): 3/4
- « The attractiveness of this token lies in the fact that carrying out the attack does not require any privileges, and can potentially gain privileges while being silent (generation of traffic deemed legitimate). Provided that the account chosen to lure the attacker appears privileged and managed by a user (so that the password is likely to be simple), this honeytoken is highly attractive. »
- Risque (risk): 4/4
- « In our example, a 64-character password has been defined, which cannot be broken in a reasonable time. »
- Crédibilité (credibility): 3/4
- « Subject to the choice of account name and attributes according to the production context in which it is deployed, since the attack is based on normal Kerberos operation, it should come as no surprise that it can be carried out. Credibility is therefore high. »
- Scalabilité (scalability): 2/4
- « The decoy account can be deployed automatically on several domains using scripts. However, for an effective lure, contextualization remains essential and will be the major obstacle to effective mass deployment. The cost of providing this contextualization and keeping it up to date must therefore be taken into account. »
To conclude, Deceptive Security solutions must be considered on a case-by-case basis. It is imperative to determine in advance the objectives to be prioritized, the strategy to be adopted, the scope to be covered, and so on.
In certain situations, especially for companies with mature IT security systems, it may be appropriate to implement Deceptive Security solutions. This is to be applied in addition to standard minimum security tools such as firewalls, antivirus, intrusion detection and/or prevention systems, etc. The aim is to cover all types of cyberattack (“0-day” type, with no known pattern).
This technology can be difficult to implement for smaller companies, as they may not have the essential security tools in place by default, nor the resources to configure (e.g., design decoys, create strategies and scenarios) and maintain such a solution (e.g., dedicated maintenance teams).
Today, the market is expanding, mainly around detection thanks to Deceptive, but not exclusively. For the time being, however, vendors’ interest in building deceptive solutions is focused on traditional environments. Solutions for Cloud AWS, Azure, etc., are still underdeveloped.
Thanks to Augustin TOURNYOL DU CLOS for his contribution to this article.


