Identity & Access Management (IAM) is an “old” topic for companies. Virtually all major groups have already carried out several IAM projects, often with the growing aim of pooling, centralizing and standardizing. And while those involved in these projects are convinced of the contributions and benefits of IAM, they also have fond memories of the difficulties and challenges they had to overcome in order to succeed.
So, despite some success stories and the cardinal role of identity in business transformation, IAM remains a disparaged theme in organizations, synonymous with a “necessary evil” rather than a “key issue” for the company.
How can we restore IAM’s reputation? How can we explain it better, and give it its rightful place in the enterprise?
The paradox of identity
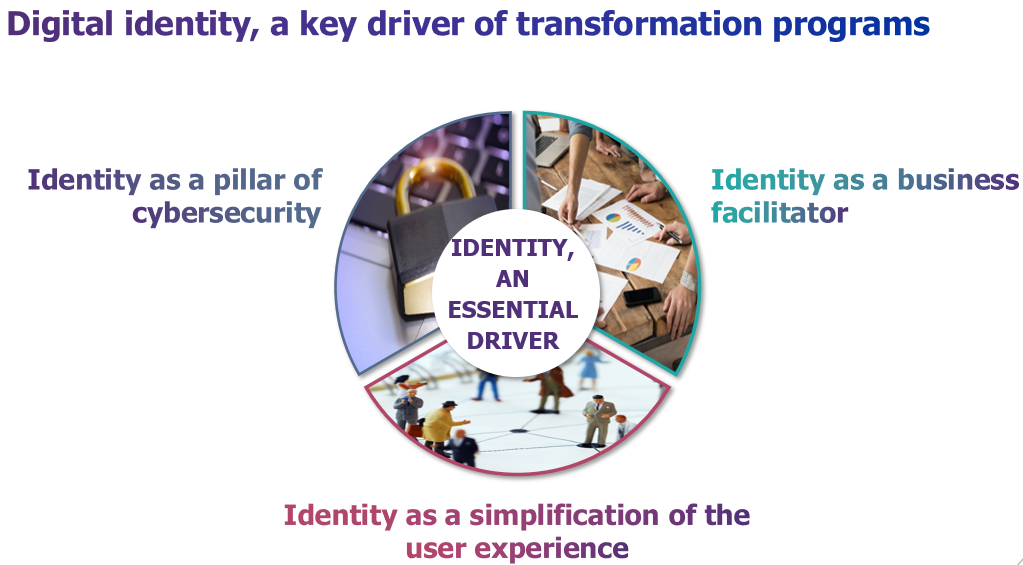
An essential driver of transformation programs…
This situation is paradoxical as identity plays a fundamental role in current transformation programs, presenting three major assets.
- It is first of all a pillar of cybersecurity by allowing:
- Have a homogeneous knowledge of all users, centralizing essential information such as name, manager, title and many other characteristics specific to each;
- Guarantee the uniqueness of individuals through the publication of a single repository;
- Control and adapt user access throughout their lifecycle;
- Be part of a Zero Trust approach by ensuring that only the right people, with the right level of rights and the right level of authentication access to the appropriate resources.
- It is also an essential business facilitator, particularly for:
- Accelerate cloud service adoption and deployment of new applications through automatic account creation and simplified entitlement (often through an IGA – Identity Governance & Administration tool);
- Facilitate the controlled opening of the IS to and towards third parties: partners, suppliers or in case of creation of Joint Ventures;
- Improve, thanks to CIAM (Customer Identity and Access Management), the customer relationship and regulatory compliance by simplifying the progressive creation of accounts and compliance with privacy regulations such as the GDPR in France.
- Finally, efficient identity management is a prerequisite for a state-of-the-art user experience, combining comfort and security requirements:
- Seamless and seamless access to all its applications and data, regardless of its access context;
- Access rights granted automatically and available on the day of arrival;
- A single portal to make and follow up your ad-hoc requests.
- Pertinent dashboards and targeted review campaigns to meet regulatory requirements without over-soliciting managers and process owners.
… but a theme unfairly considered
Despite the significant advantages it represents, the theme of identity is rarely at the centre of companies’ concerns. It is rather perceived as a necessary evil, or even occupies a place of «ugly duckling». Thus, it is common to note the pitfalls when Identity is insufficiently well managed, and even more common to consider as normal and acquired the benefits it produces.
Beyond the simple constant, it is necessary to understand the reasons that led to this situation of lack of investment, sponsorship, even recognition.
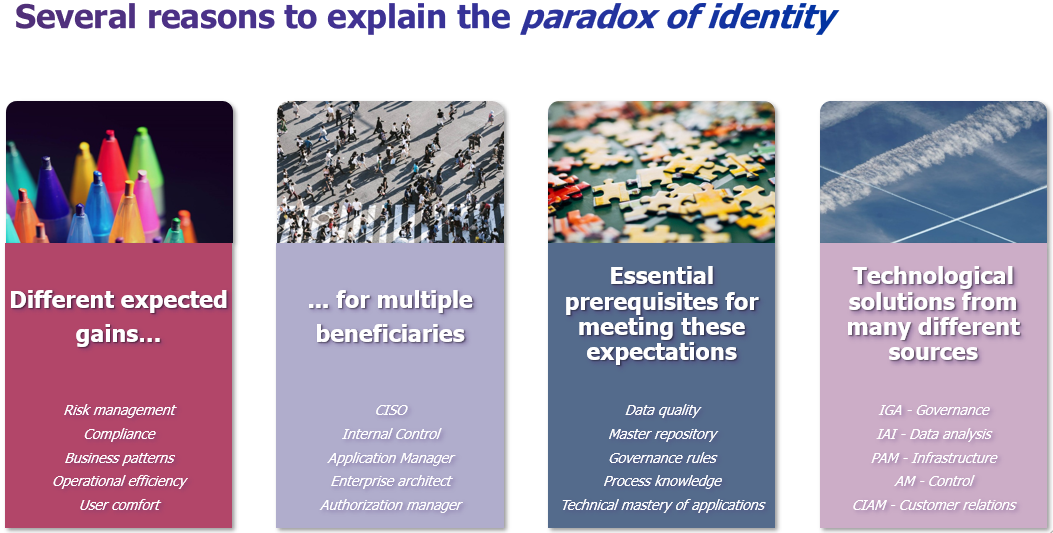
First explanation of the paradox: the dispersion of expected gains towards different beneficiaries. Indeed, the IAM is, by nature, very transversal in the company. To succeed, it must embrace a wide range of topics and therefore mobilize many stakeholders. If each of them will see gains; none will stand out enough to bear primary responsibility. For example:
- The identity makes it possible to simplify the customer relationship, subject of major interest for a marketing/ digital manager, but not the compliance manager.
- The latter will see identity as a significant advantage in meeting the CAC’s access review requirements.
- The IT department will expect consistent and automatic management of the allocation of accounts and rights, synonymous with financial gains, particularly in terms of licenses, support, etc.
- As for the CISO, its priority will be to remove access in the event of departure and the application of the principle of “less rights granted or the early detection of “suspicious” behaviour.
Second explanation: like any transformation, which is transversal, the launch and success of an identity project is conditioned by essential prerequisites.
The difficulty and effort required to achieve these prerequisites depend on the context of each company; but the prerequisites themselves are relatively constant and can be articulated around 4 axes:
- Data quality: both for data consumed by IAM (organizations, structures, identity data from HR…) and for data that IAM must make available (application account identifiers, attributes in applications…).
- In-depth knowledge of end-to-end processes: this is essential to anticipate the impact of future changes on users, but above all to be able to change and harmonize ways of doing things, and not to continue with what already exists “because that’s the way it’s always been done”.
- Mastery of the applications to be connected: it is necessary to mobilize both technical knowledge (technologies used, APIs available…) and functional knowledge (user populations, data model, authorization model…).
- Last but not least, the ability to impose a “normative” IAM framework, to find a compromise and to arbitrate both on the target (operational model, functional framework, attributes and management rules, arrival/mobility/departure processes, standardized connection framework for applications…) and on the trajectory and success indicators (priorities, subdivision…). To put it in a nutshell: “It’s not IAM’s job to heal what has been poorly thought out or what has become inadequate over time“.
Third and last explanation: a complete identity management is based on several complementary technological bricks. With varied origins and somewhat ambiguous names, it is not always easy for a non-expert in the field to understand precisely the contribution of each of these bricks:
- IGA – Identity Governance & Administration: Identity Governance
- IAI – Identity Analytics & Intelligence: Data analysis and control
- PAM – Privileged Access Management: Privileged Account Management
- AM – Access Management: Authentication and Access Control
- CIAM – Customer Identity & Access Management: Client identity management
What’s more, these names have evolved over time, sometimes legitimately to reflect major developments, sometimes more as a result of publishers wishing to differentiate their value proposition. The emergence of new functionalities (real-time detection, consent management, etc.) and the innovations proposed by software publishers are also changing the lexical field of IAM.
How to give identity its rightful place in the company?
To overcome this paradox, the usual avenues (high-level sponsors, more resources, evangelization, etc.) are necessary but often insufficient. More structural transformations are needed.
Unify the strengths of identity under one banner
IAM topics have emerged in scattered order in companies, and have matured at very different rates. The result is that, all too often, teams remain isolated.
It is therefore imperative to bring together all identity-related teams and budgets under a single umbrella. And if, as the saying goes, there’s strength in numbers, the aim is not just to be visible, legitimate and have a say in the organization.
Synergies abound:
- Make identity a perennial and recurring topic, at the very least at the level of the CIO CoDIR, and in all company evolutions.
- Define a global value proposition, proposing a unified offering that is more legible for business lines and application managers, who will be able to rely on a single point of contact.
- Be part of a long-term strategy to take advantage of software publishers’ roadmaps, create a continuous improvement approach and prepare for future corporate changes: reorganizations, mergers & acquisitions, new ERP…
- Improve the consistency of IAM services and manage with end-to-end service indicators.
- Guarantee a high level of expertise by enhancing team know-how, building loyalty and offering richer development perceptives.
This far-reaching transformation can appear delicate and a source of risk for companies with less mature IAM systems. This is why it is possible to initiate it gradually, starting from one of the following axes:
- Bringing together under a single organization the teams working on the various IAM themes: IGA, IAI, AM, PAM and even CIAM.
- Unify the teams in charge of projects and those in charge of “RUN” in order to offer a “product” approach to each identity service, and to be part of a continuous improvement logic.
- Extend IAM teams’ responsibility for data control, so that they can commit to indicators and, ultimately, to the quality of service provided and perceived.
On this last point, however, IAM teams cannot assume responsibility for the quality of the company’s data and repositories. They must, however, guarantee the quality of the service rendered, by ensuring both the proper operation of IAM services (the “container”) and the quality of the data manipulated (the “content”). IAM teams must therefore be equipped and organized to supervise, control and alert the quality of data received, as well as the use made of it.
An advantageous unification but which obligates
This ambition for unification, which puts IAM in the spotlight, de facto obliges the Identity manager to be exemplary in his role and responsibilities:
- With regard to customers: have a clear service offering, take into account feedback and realities in the field, define and respect a roadmap of evolutions, provide “meaningful” service quality indicators, i.e. those that make sense in the day-to-day life of the business, promote gains and benefits…
- Regarding other stakeholders in the company (HR, Purchasing, Cybersecurity, Regulatory Compliance, Audit and Control…): communicate, materialize and help to appropriate the Identity value proposition on a day-to-day basis and during structural transformations (reorganizations, acquisitions…), find ways to compromise, show the “win-win” character of process and operational model evolutions, share everyone’s roles and responsibilities, illustrate the impacts in the event of breaches…
- For its teams: have a robust operating model, balance responsibilities between internal employees and external service providers, build a genuine HR ambition for the medium and long term (validation of expertise, talent management, building career paths, enhancing the value of the IAM channel…).

Conclusion
The unification of IAM services is a fundamental trend, and within 3 years a large majority of large companies will have converged towards this model, at least partially.
This movement is not always the result of a desire to reposition identity within the organization on a long-term basis. It is sometimes imposed by teams to compensate for a lack of resources or expertise, or in the hope of keeping costs down; in such cases, it reinforces the feeling of lack of consideration.
And yet, there are many opportunities to demonstrate the need for an in-depth rethink of IAM ambition, and to give it its rightful place: technical obsolescence of IAM tools, corporate strategy to switch to Cloud solutions, difficulties in accompanying structuring transformations in the organization, new regulatory requirements, or the results of a simple satisfaction survey among users or application managers…
Do you dare to seize them?


