Since the massive rise of DevOps, continuous integration and deployment (CI/CD) pipelines have become essential to automate application development cycles. Continuous Integration (CI) involves merging and testing code automatically, while Continuous Deployment (CD) automates the entire process of releasing that code into production, ensuring it runs properly in its target environment.
Attacks targeting these supply chains have opened a new perimeter of risk in information systems. Breaches can lead to intellectual property theft, tampering with source code, service disruption, and privilege escalation into more critical parts of the IT landscape.
What are the new attack vectors in CI/CD pipelines, and how can they be contained? This article reviews real-world compromise scenarios and provides recommendations to defend against them.
What risks for CI/CD pipelines?
The 2020 SolarWinds breach is very often cited as CI/CD compromise, as it revealed the true scale of that such an attack can cause. After supposedly stealing FTP credentials left in plaintext in an old GitHub repository, attackers poisoned SolarWinds’ supply chain by inserting a C2 beacon into Orion, its network management software, before the signing process.
This backdoor gave adversaries months of undetected access to the internal networks of U.S. government agencies and private companies.
Incidents like this, along with more recent ones such as Log4Shell, Codecov, and XZ Utils, highlight not only the need for stronger CI/CD security but also for a more adaptive incident response. OWASP published a dedicated overview for CI/CD Security in their Top 10, mapping out the most common areas of risk.
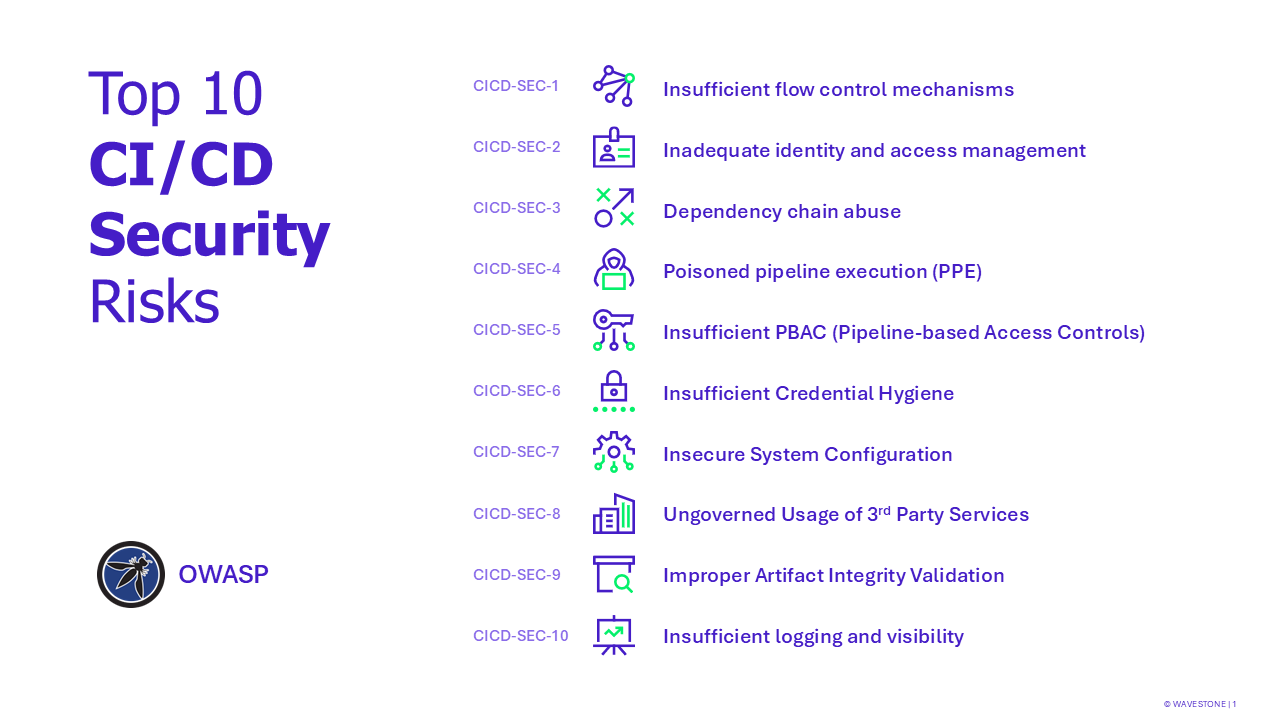
Figure 1 – Top 10 OWASP CICD-Sec
Field insights @ Wavestone
Audits and penetration tests help identify vulnerabilities proactively before attackers can exploit them. By simulating real-world attacks, these assessments provide concrete visibility into how systems can be compromised.
Our recent client engagements have led to clear findings:
- In nearly all Cloud and CI/CD audits, vulnerabilities are always discovered in pipelines, often enabling full control of the pipeline, its artifacts, or even underlying infrastructure.
- In CERT and Red Team interventions, CI/CD pipelines frequently act as accelerators in attack paths.
Here are two examples observed in the field.
Example 1: Full AWS compromise through CI/CD abuse
In this first grey-box example, we compromised an entire AWS Cloud environment (600+ accounts) starting from standard DevOps accounts.
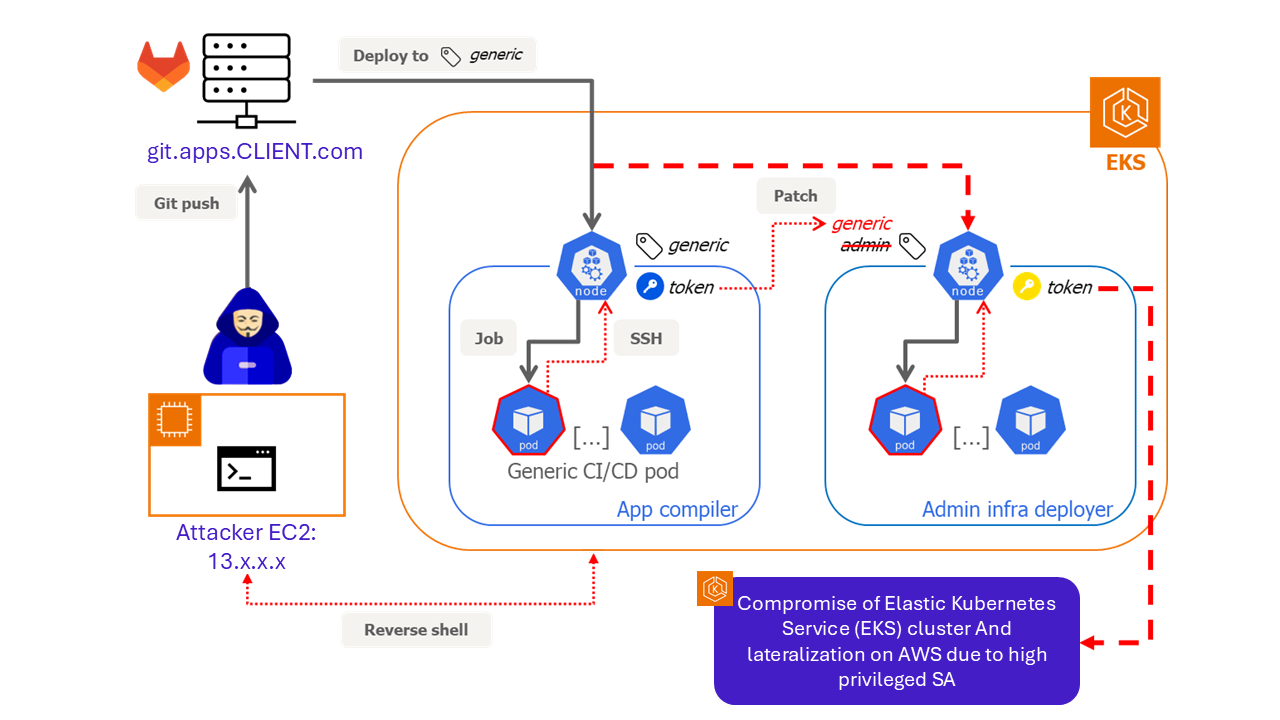
Figure 2: Full AWS compromise through CI/CD abuse
Attack path:
- An attacker pushed malicious code into a GitLab repository, triggering a GitLab CI pipeline that deployed the code into a generic Kubernetes pod.
- The code opened a reverse shell, giving the attacker remote access to the Kubernetes environment.
- From there, the attacker exploited excessive privileges granted to the node’s service account (ability to patch tokens in the cluster) and replaced the admin node’s token.
- On redeployment, the malicious pod lands on the former admin node, still holding admin rights.
- The attacker escalated privileges and pivoted into AWS, compromising the entire Elastic Kubernetes Service (EKS) cluster and its resources.
Example 2: Chained attacks across pipeline components
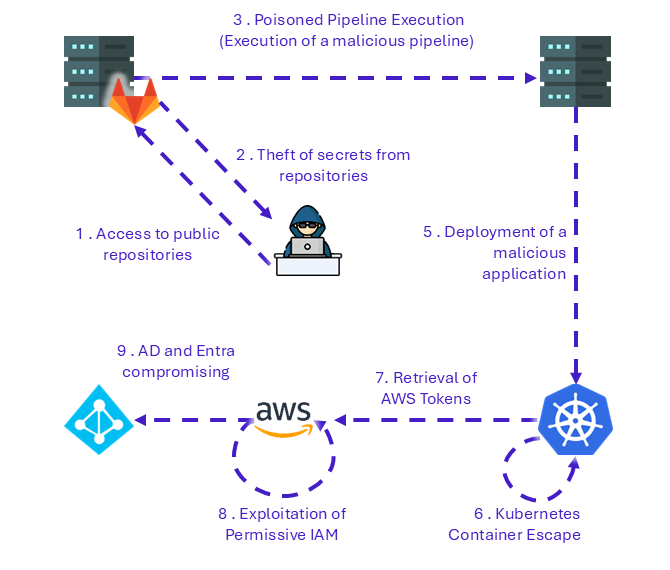
Figure 3 -Summary of real chained attacks across pipeline components
In another case (presented at DefCon & BSides 2022), we demonstrated how multiple components of a CI/CD pipeline can be chained together in compromise scenarios. [Video].
Recommendations to secure a CI/CD
CI/CD pipelines have now become systemic components of information systems and can be leveraged to compromise an organization’s most critical resources.
Our recommendations for securing the CI/CD chain can be grouped into three main themes: identity and access management (IAM), better pipeline design, and continuous monitoring. These align with the ANSSI DevSecOps guidance.
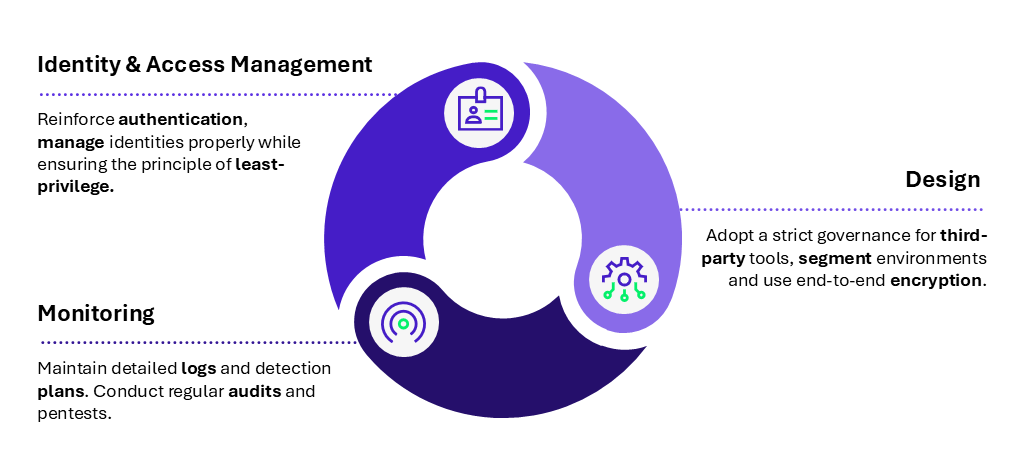
Figure 4 – Three main recommendations to secure a CI/CD
Identity and Access Management (IAM)
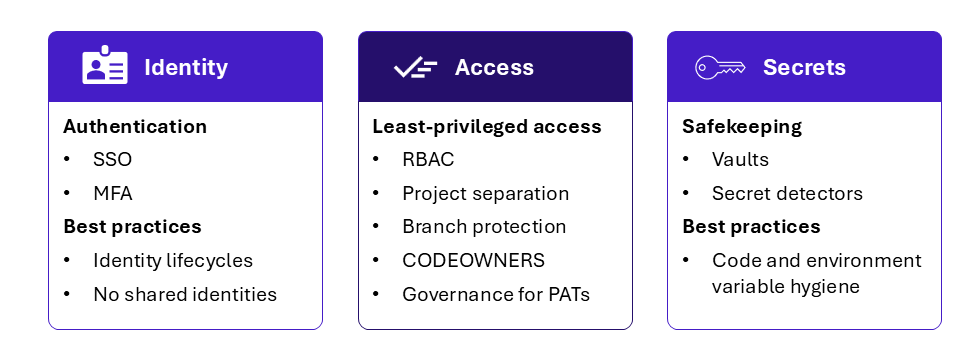
Figure 5 – IAM recommendations
Identity management
Beyond the traditional rules for managing identity lifecycles, it is strongly recommended to systematically use Single Sign-On (SSO) combined with Multi-Factor Authentication (MFA). This significantly reduces the risk of intrusion into the CI/CD chain, by ensuring that any user accessing code repositories, signing commits, or performing other privileged actions is properly authenticated.
Access control
User and service account permissions must be strictly limited to what is necessary for their role within the CI/CD chain, always applying the principle of least privilege. This should be enforced through Role-Based Access Control (RBAC). For example, a developer working on a specific project generally should not have write access to the overall pipeline configuration.
It is also advisable to segment projects using separate code repositories, and to ensure that the orchestrator account of one project does not hold excessive rights over the deployments of projects it is not associated with.
Secrets management
In CI/CD, “secrets” refer to sensitive data such as passwords, API keys, certificates, or access tokens. Since these secrets often enable privileged actions within pipelines, they must be retrieved in an automated and controlled manner.
Vendors such as HashiCorp provide dedicated secret management solutions that make it possible to store sensitive data centrally, while ensuring encryption in transit and at rest.
CI/CD pipeline design
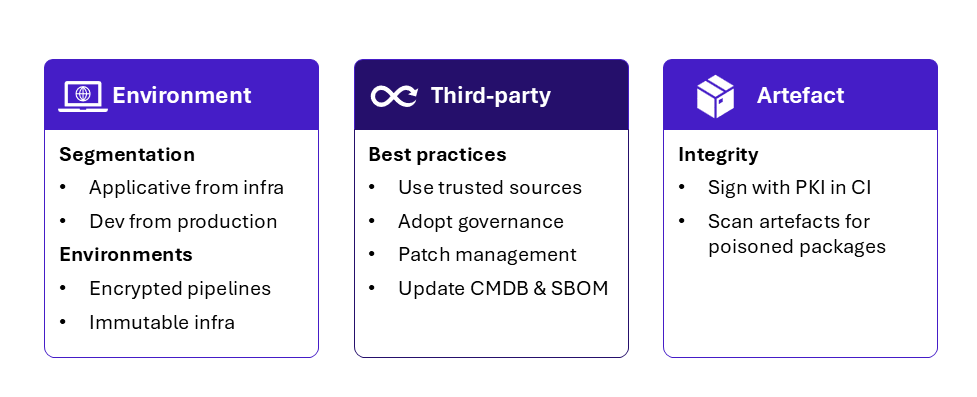
Figure 6 – Design recommendations
Environment segmentation
Segregation between users, applications, and infrastructure is essential to minimize the impact of a compromise. In line with ANSSI’s guidance, actions performed by the production CI/CD chain should be treated as administrative actions, and the number of users authorized to access it should be kept to an absolute minimum. Furthermore, communication between environments must be protected with end-to-end encryption.
Integration of third-party tools
As the SolarWinds attack demonstrated, many supply-chain compromises originate from a third-party component integrated into a CI/CD pipeline. These tools are indispensable for supply-chain operation: they may be as small as a development add-on, or as central as a version control system or orchestrator.
Because these tools are often granted high privileges—access to sensitive resources or the ability to perform critical actions within the pipeline—a vulnerability that is left unpatched can be catastrophic. In many cases, the ability to remediate will depend on the vendor, limiting the organization’s own control. A strict governance framework and a Third-Party Cyber Risk Management (TCPCRM) process for third-party tools is therefore necessary.
Artifact management
To avoid the risk of distributing malicious artifacts, it is recommended to sign artifacts as early as possible in the pipeline, and to verify those signatures at deployment time to guarantee their integrity. Similarly, regular Software Composition Analysis (SCA) should be performed to prevent the introduction of malicious libraries.
Monitoring and supervision
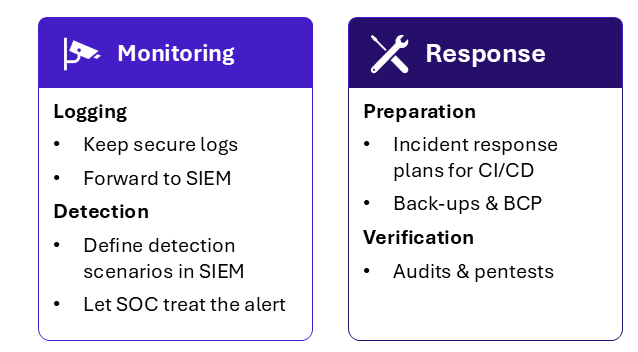
Figure 7 – Monitoring recommendations
Logging and detection
Maintaining a high level of visibility and control over all pipeline components is critical for easier maintenance and faster response to attacks.
A tailored logging strategy should be implemented: logs must contain only the data needed to ensure traceability and accountability in the event of an incident, should be stored securely, and must not contain secrets in plaintext. Logs should be shared effectively with the organization’s Security Information and Event Management (SIEM) system.
Regular audits and penetration tests are also required to reassess the security posture and identify potential new compromise paths within the CI/CD pipeline.
Incident response
Finally, CI/CD pipelines must be included in incident response plans just like any other perimeter of the information system. This means ensuring that source code and configurations are backed up, and that business continuity plans exist in case of a tool failure.
In conclusion
CI/CD pipelines have become a genuine cornerstone of modern information systems. They are now systemic components, indispensable for developing and deploying applications. Yet their critical role within IT also makes it necessary to implement appropriate security measures so that they do not themselves become attack vectors.
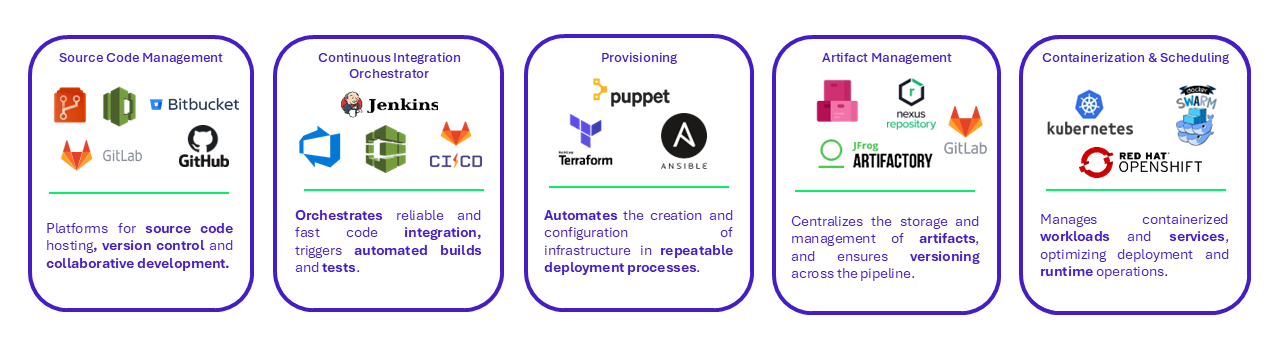
Figure 8 – Some systemic CI/CD components
Beyond the recommendations detailed in this article, further preventive measures can be implemented in the form of hardening guides tailored to specific tools within the pipeline. In addition, adopting a robust training strategy for users, together with structured change management, is essential to ensure the success of these transformations.
Thanks to Jeanne GRENIER for her valuable contribution to the writing of this article.



