Laboratory Equipment: An Overlooked Cybersecurity Risk
Industries such as pharmaceuticals, chemicals or agri-food heavily rely on laboratory equipment, especially for quality control, R&D or chemical analysis. These instruments are vital for numerous business processes, many of which are critical for operational and regulatory compliance (i.e. in pharmaceutical industries, quality control of raw materials and finished products for batch release, or the production of regulatory reports). As a result, ensuring the availability and reliability of laboratory equipment is a top priority for these companies. However, these devices—originally designed to operate in isolation—are now increasingly connected to improve operational efficiency through automated data collection and harmonized analytical methods across sites.
These operational requirements have driven the widespread adoption of Laboratory Information Management Systems (LIMS). In pharmaceutical settings, LIMS manages analytical batch records, monitors quality parameters, and provides full traceability for regulatory audits. In environmental testing, they streamline data collection, validation, and reporting, reducing manual errors. In food safety labs, LIMS automate compliance reporting and trigger alerts when contamination thresholds are exceeded.
Centralizing the management of laboratory equipment data with LIMS requires instruments to be networked, even when this was not initially anticipated by manufacturers. This increased connectivity thus brings new cybersecurity challenges, as many laboratory systems are based on outdated technologies and thus potentially increase the attack surface.
Obsolete Systems: A Growing Security Risk
Many laboratory devices still run on proprietary or outdated operating systems (such as Windows XP) that no longer receive security updates. These legacy systems are highly vulnerable to known exploits and are difficult to patch.
Manufacturers rarely release patches for obsolete equipment, despite the long lifespan of these devices. Once deployed, patching is further complicated by governance issues—specifically, determining who is responsible for applying updates.
Most laboratory instruments also have limited built-in security features. They often use unsecure or outdated communication protocols (such as HTTP, FTP, or SMBv1/v2) and are frequently deployed with poor configuration practices, further weakening their security. Although newer models support secure standards like OPC UA or SFTP, these features are not always enabled or properly configured.
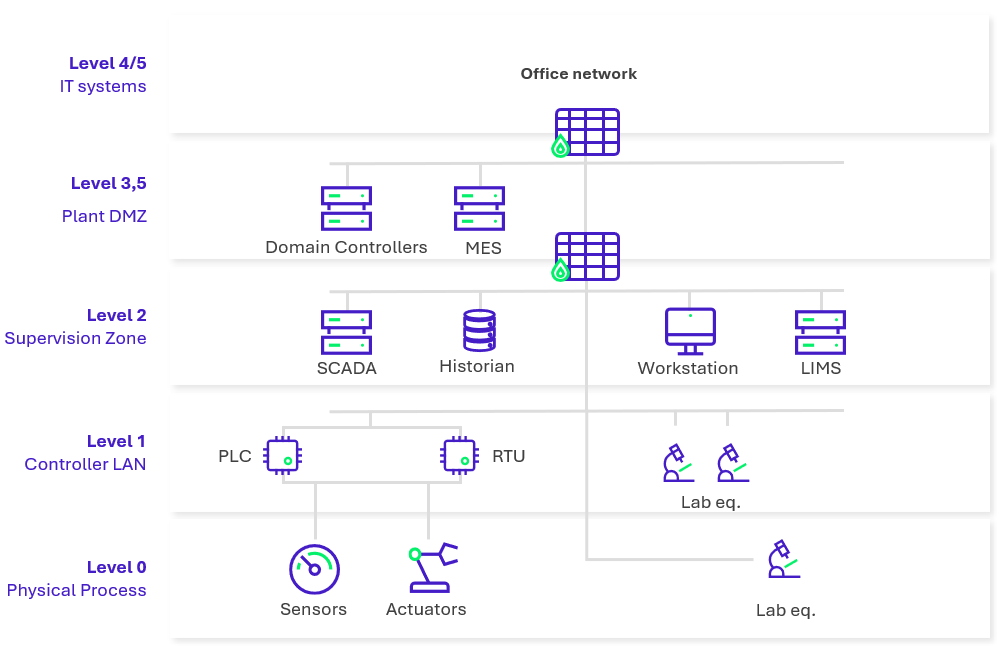
Figure 1: Typical industrial network architecture in pharmaceutical manufacturing.
Identity and access management is another major challenge in laboratory environments. Many devices still rely on default or shared local accounts and cannot enforce proper authentication mechanisms. These systems are rarely compatible with centralized directories through protocols such as LDAP, making it difficult to enforce consistent security policies across multiple sites. While from an operational perspective authentication may not seem necessary, when combined with obsolete operating systems, insecure communication protocols, and limited access control, these weaknesses turn laboratory devices into easy entry points for cyberattacks.
As laboratories increasingly interconnect their instruments with LIMS, cloud analytics, and centralized data historians, this lack of cybersecurity hygiene not only directly exposes devices but also puts the broader corporate network at risk.
Securing Laboratory Systems with Isolation and Gateways
When laboratory equipment cannot be secured due to its inherent limitations, exposure must be minimized as much as possible. This involves placing such devices behind secured intermediary systems—such as dedicated gateways or workstations—and defining specific network zones to limit the surface of a potential compromise. By segmenting the network and filtering data flows, potential compromises can be better contained and the impact on other critical systems limited.
Three key solutions can enhance security in this context:
- Workstations equipped with cybersecurity tools to ensure compatibility between lab equipment and secured networks. This approach works best when modern workstations act as intermediaries, translating data securely and enabling monitoring. In reality, this approach has been the historical way to interconnect laboratory devices to manage them and manipulate their data.
- Laboratory equipment isolation from broader network environments to limit exposure. This approach extends standard network segmentation practices to laboratory systems, controlling their exposure without fully isolating them, and maintaining necessary data flows for operations. It is cost-effective and easy to deploy, making it ideal for older systems that cannot be patched.
- Edge devices for protocol translation and network isolation. These devices are highly effective for environments needing real-time data exchange between incompatible systems.
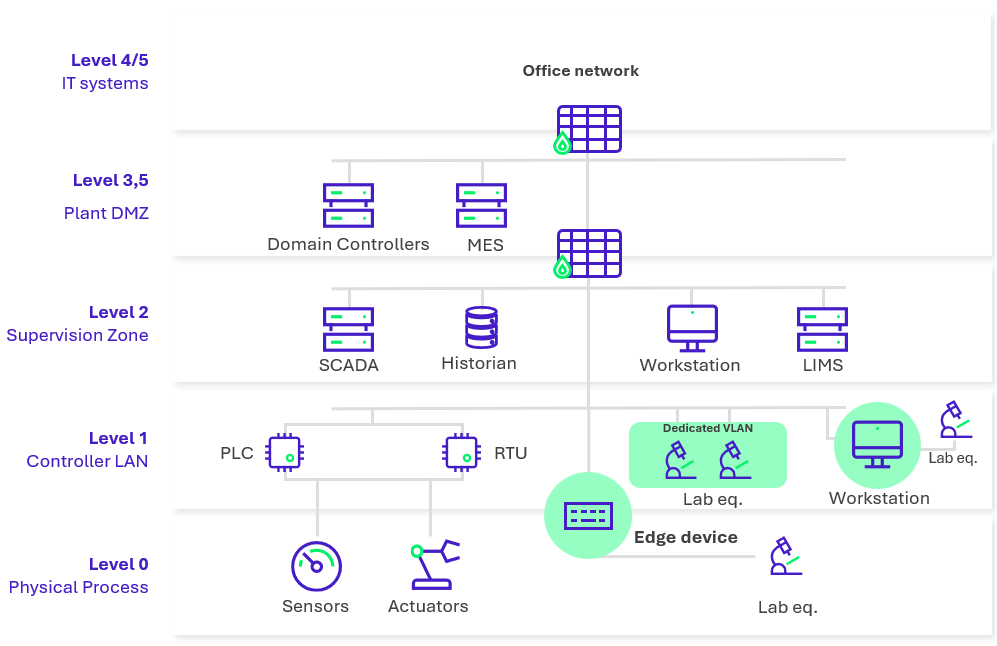
Figure 2: Pharmaceutical network architecture implemented with laboratory equipment protection measures.
While these solutions help secure industrial environments, they also introduce new challenges such as patch management and equipment ownership — critical factors in maintaining long-term security. Ultimately, these are responses to an initially unsecured situation, and therefore not perfect: for instance, using workstations as gateways is a good practice, but it requires patching, lifecycle management, and can come with added costs and increased footprint in server rooms (increased infrastructure requirements).
The choice of solution to mitigating cybersecurity risks must align with organization’s technical constraints and operational context. A few common practices help illustrate the diversity of strategies:
- Laboratory equipment isolation in a dedicated VLAN remains an effective first step. However, even segmented systems must rely on secure communication protocols to ensure data integrity and prevent unauthorized access.
- Edge devices offer another layer of protection. But they come with their own set of challenges, particularly around organizational ownership, management and maintenance responsibilities.
- Workstation equipped with cybersecurity tools often act as gateways by default, converting data into formats that can be read and processed downstream — whether by LIMS, cloud platforms, or internal databases. This setup is common and secured as long as the workstation is properly managed and hardened to avoid becoming single points of failure or introducing additional attack surfaces. Implementing this intermediary layer is ideal but this requires developing or integrating reliable translation mechanisms, sometimes not handled by the vendor.
Conclusion: Strengthening Cybersecurity in Laboratory Environments
In given industries, ensuring the integrity of data, quality of final product and the safety of consumers remains one of the priorities. However, as laboratories become increasingly digitalized and interconnected, new use cases are emerging that challenge traditional architectures and operational models. This evolution demands a more comprehensive, end-to-end approach to cybersecurity—one that integrates technical safeguards, process maturity, and clear governance throughout the laboratory ecosystem.
Implementing a cybersecurity-by-design approach throughout the entire project lifecycle is essential—not only to anticipate risks early but also to support business teams in integrating security seamlessly into their operations.
The Cyber Resilience Act (CRA) will reinforce the cybersecurity of digital assets within the European Union for manufacturers as well as importers and distributors of such assets.
To go further: Cyber Resilience Act: A revolution redefining product security and transforming the ecosystem – RiskInsight