The revolution is underway! The vehicles we drive will become ever-more connected and autonomous in the near future, something that will open the door to new uses. The user experience, in terms of mobility, will undoubtedly be better, but the services on offer will go hand -in-hand with new threats and new cybersecurity issues to be considered.
In this series, we’ll first present connected vehicles and their associated cybersecurity challenges; the main sources of threat and the risks will be addressed in a second installment. Lastly, a third article will present our views on the issue and the main lines of the response required to address it.
The connected car: a vehicle supporting a raft of interactions
Entertainment, an extension of your smartphone, shared mobility, management of the car’s life cycle… users are demanding new experiences, and the services and applications they generate are resulting in a range of interactions. We can imagine a smart car being able to find a free parking space, automatically schedule an appointment for maintenance, or turn a traffic light green as it approaches. Since April 1, 2018, all new vehicle models must also have an emergency call system, as well as geolocalization to enable the authorities to be contacted in the case of an accident. In this respect, they are already “connected”.
Manufacturers and other players are already capitalizing on the opportunity to maintain a close relationship with customers throughout the vehicle life cycle. By doing this, they become “providers of services and mobility solutions,” drawing on, among other things, collected data. In particular, because such connectivity represents a step toward autonomy, the vehicle needs to be able to communicate with other vehicles and the surrounding environment. These changes are underway, and their pace will progressively increase.
However, the challenge of cybersecurity is scarcely taken into account, or ignored: yet it has to be a key plank of any connected solution—from the design phase to the end of the life cycle. Such thinking is essential to safeguarding the vehicle’s integrity, protecting passenger lives, and complying with current and future regulation.
The first prerequisite is to properly understand the connected vehicle’s technologies and ecosystem.
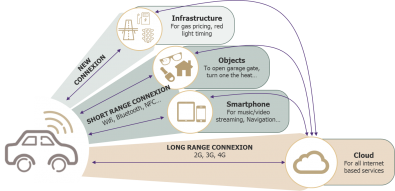
How connected vehicles interact with their environment
A specific feature of a connected vehicle is that it interacts with its ecosystem, via mobile data streams, over both the short and long-ranges.
- Short-range connections: Here, the vehicle interacts directly with an object (such as a smartphone, infrastructure, etc.), without any intermediary. It uses technologies with a limited range for local exchanges (WAVE, on-board Wi-Fi, Bluetooth, etc.).
- Long-range connections: Here, the vehicle uses remote access to interact with external components via a cloud platform. 4G, and soon 5G, connections are the technologies of choice for connecting vehicles to the internet.
This connected-vehicle concept also covers exchanges with the vehicle’s direct environment under the umbrella term “Vehicle-to-Everything” (or V2X). Lastly, the standard, ISO 20077, covers “Extended Vehicles” (or ExVe) as a whole: which comprise the physical vehicle as well as all the platforms and infrastructures that the car manufacturer is responsible for.
A range of ecosystems and players that need to work together
The car was once a very closed system; with the exception of diagnostic connections for garages and some connectivity to be able to broadcast multimedia content; any connectivity risks were largely contained. Today, the proliferation of forms of connectivity and access to the internet have opened up new opportunities for manufacturers and service providers, but also for attackers.
The first ecosystem to consider is the . Electronic and communication systems must be able to communicate with each other without the transmitted data or stored secrets being altered or stolen. Among these systems are the ECUs, the mini “on-board computers” that control the vehicle’s key functions, such as the braking system, air conditioning, lighting, etc.
Beyond on-board security, there are the user and owner (the latter not necessarily an individual) who have the right to give orders to the vehicle according to pre-defined rules. In the future, their authentication will be essential when it comes to questions of responsibility, as well as for verifying the legitimacy of the orders they issue.
Another vitally important aspect concerns connected services that use centralized platforms, or even cloud-based ones, which have been developed by the manufacturers or their partners. These platforms represent a significant threat because they can trigger orders for entire fleets of vehicles, and therefore the impact of any problem is multiplied. Manufacturers will need to put in place sufficiently secure solutions to allow such services; they’ll need to combine their own platforms with those of partners and the APIs on the vehicle, as well as ensuring the required level of confidence in the environment.
Lastly, in the medium-term, external objects and the surrounding environment (other vehicles, garages, parking lots, road infrastructure, etc.) will need to communicate and share information. The challenges of ensuring security in real time (in terms of availability, integrity, etc.) will be complex ones.
Cybersecurity issues: from the virtual to the real world
People’s safety, inside and outside vehicles, is a top priority for the automotive industry. We might imagine, then, that the cybersecurity issues raised by connected vehicles will be treated with the same degree of rigor—such that they can guarantee the car’s safety and integrity.
The first issue represents an organizational challenge for all stakeholders, especially manufacturers, because the emergence of this new model brings together two opposing worlds: services and engineering. The first is characterized by agility and speed, and large numbers of short-term projects. The second, with a much longer development cycle, must meet the safety and quality requirements associated with vehicle approval. This dichotomy has impacts on cybersecurity and, in particular, its integration into development projects, as well as the coverage of end-to-end risk. For example, as a result of its position, the backend becomes a nerve center that must be fully protected to avoid any risk of a systemic attack that could have repercussions for the entire fleet. Unfortunately, the true value of this need for security is not currently appreciated, mainly as a result of requirements for very short times to market.
Considering the other issues, it’s clear that the cybersecurity challenges for connected vehicles don’t differ greatly from those in the IS world: identity and access management, detection and response, the security of infrastructures, cryptography, third-party management, patch management, etc. A connected vehicle is a mobile IS, and numerous security standards (ISO2700x, NIST 800, etc.) have already been developed. These set out good practice in various guides and reference documents (SAE J3061, AUTOISAC, NHST, etc.) and the topic will shortly be covered to the ISO/SAE 21434 standard.
However, a number of factors inherent to vehicles and their embedded systems mean that the topic needs to be considered from new and specific angles.
The vehicle’s mobility and connectivity make security more complex: security must be guaranteed where there is a limited connection, or no connection, and in the context of a changing environment. Regulatory aspects must not be ignored either, given that the vehicle may have to move between countries.
The world of on-board systems also places constraints on hardware—in terms of cost, computing power, and size.
Questions about updating components and services arise too, given that a system must be able to function at all times but may also be shut down for long periods.
Lastly, vehicles are designed for a long life cycle, which implies thinking about security from the start, especially when it comes to managing identities and accesses. This long life cycle also means considering evolving standards over time, as well as developing a model for updates that guarantees vehicle security in a way that is sustainable and manageable for constructors.
The road ahead is long, and cybersecurity is approaching a crossroads that was not in view a decade ago. It’s vital that all players involved grasp the importance of what’s required and start to put in the effort now, before it’s too late.


