Citalid is a French tech startup founded in 2017 that provides CISOs and Risk Managers with a software for quantifying and managing cyber risk. Citalid‘s highly innovative technology enables its clients to benefit from simulations, metrics and recommendations that are directly operational to optimize their ROSI (Return On Security Investments) thanks to its unique ability to cross-reference technical, contextual and financial data. Citalid is part of Wavestone’s startup acceleration programme, Shake’Up.

For the time being less well known and less widespread in Europe than its sisters EBIOS RM & Mehari (among others), the FAIR risk analysis method nevertheless fills the gaps left by other approaches. Already highlighted by Wavestone in a previous article, its main assets lie in the perspective of data usually ignored by traditional risk analysis on the one hand, and on the other hand in its ability to generate metrics dedicated to strategic decision support and adapted to the language of decision-makers, such as Value at Risk.
Nevertheless, as this same article points out, this approach is a priori undermined by time, human resources and the multiplicity of knowledge required to carry it out. Therefore, although the concept is attractive, is it realistic to deploy the FAIR method? How can its nomenclature be translated operationally? What about its automation? More generally, does it provide enough added value to justify its use?
Despite its undeniable effectiveness in quantifying risks, such an approach requires both an appropriate technical system and functional support, which is essential in the collection of data. Quantifying its potential financial losses in the event of a cyber incident is not enough: it is also necessary to have the capacity to put them into perspective in an ecosystem of polymorphous and evolving threats. This is Citalid‘s innovation: to be able to carry out a dynamic quantification of cyber risk for decision-makers, by automatically crossing the reality of the threat that weighs on a company, its business context and its defensive maturity. And, above all, not to stop at analysis alone: to generate an action plan that reflects the optimal balance between efficiency and profitability.
Empiricism as FAIR’s automation framework
Contextualizing the external environment
As in any analysis, the objectivity of the observation increases with the number of parameters considered. If it is frequent, even usual, that the internal context of an information system is studied, it is rarer for the analyst to be interested in all the external dynamics that can influence the analysis. These dynamics, which can take on a variety of realities as we shall see, can however strongly influence the frequency and intensity of cyber threats. However, it is difficult to draw up an exhaustive typology of these data, and taking them into account is almost systematically a mixture of two ingredients:
- Curiosity and the logical mind of the analyst (in fine, his capacity to project himself into / adapt to a context);
- The good visibility of the person(s) responsible for the system and the activities within their perimeters;
Among the exogenous criteria that can influence the risk analysis are: the competitive environment, the company’s position on its market, its geographical locations, geopolitical dynamics, internal policies, the normative framework, the socio-economic climate, the diversity of its activities, etc.
However, it would be easy to get lost in this labyrinth of criteria. It is therefore necessary to support the decision-maker in the creation of a cartography of its environment in the most comprehensive sense of the term. It is therefore through exchange and collective intelligence that a first level of filter is created, by drawing up a perimeter of analysis that is both structured and flexible.
While defining the perimeter of the analysis makes it possible to establish a coherent framework, a multitude of risks can nevertheless be inserted into it. It should also be noted that the defined perimeter can itself be a component of a broader scope of analysis. In this sense, the various perimeters determined can be articulated in the form of a hierarchical tree, often tracing the internal organisation of the company (see diagram below).
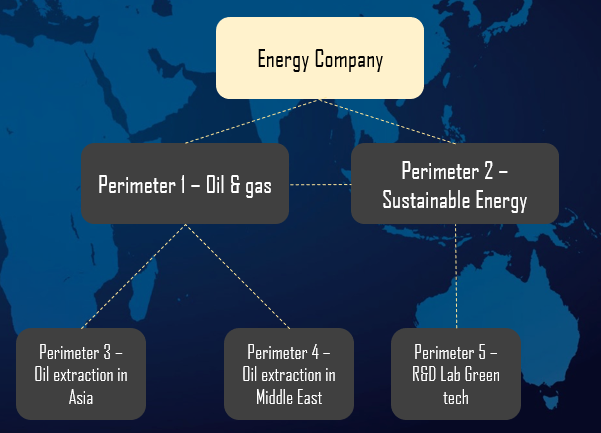
Thus, in the example opposite, the group level is represented by the “Energy Company” perimeter, which aggregates the risk of all its “children” perimeters (here its “business units“). However, each perimeter has its own context and risks. This tree structure plays a predominant role in the construction of a relevant library of related risk scenarios. One could easily be tempted to go back up to the group level to globalize its scenarios, but this often de facto deteriorates the granularity, and therefore the quality, of the analysis due to the particularities of each perimeter.
Build a relevant library of scenarios
This framing work therefore conditions the choice and parameterisation of risk scenarios. This parameterisation and the resulting calculation is made complex by the number of criteria to be taken into account and the uncertainty inherent in cyber risk. Without going back over the FAIR methodology already discussed on this blog, it can therefore be long and tedious to build a large number of scenarios of risk while considering the specificities of each perimeter. A solution to this problem therefore lies in the construction of a library of scenarios that can be adapted to each business context and encompass several types of threats. Based on operators’ experience and accumulated data, Citalid now has several libraries of scenarios and losses, listed in ‘Business’ directories. These are easily exportable on the platform, while retaining a degree of flexibility that allows the scenarios indicated to adapt very precisely to the business context. Following on from the use-case used above, the image below illustrates a ‘fictitious’ library of scenarios related to the Energy sector. As this is a ‘Demo’ version, this panel is however not exhaustive.
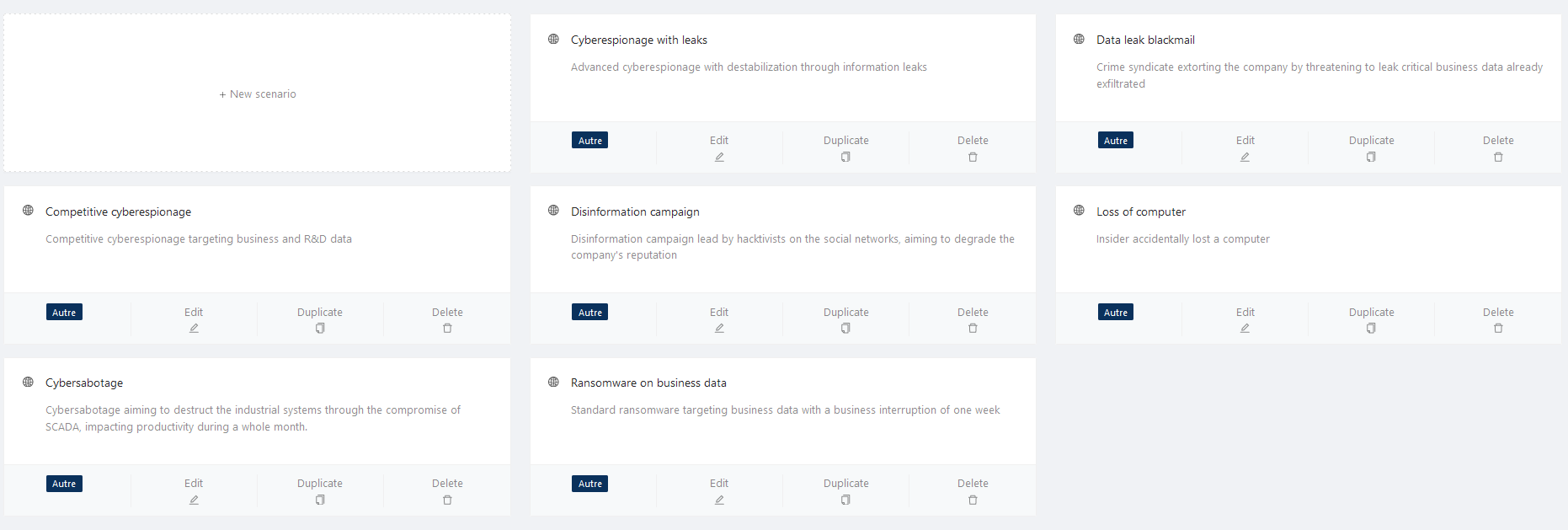
Citalid‘s library of scenarios is thus part of a double dynamic that at first sight seems contradictory: capable of meeting the requirements of efficiency and automation of the analysis, it remains flexible enough to be implemented with precision and relevance in any context. Each typology of threat, combined with the characteristics of the perimeter analyzed, determines the frequency of occurrence and the financial losses, whether primary or secondary, inherent in the chosen scenario. In the case of an economic espionage scenario, for example, it is safe to say that there will systematically be a loss related to the remediation of the incident, a loss related to the exfiltration of data and a loss resulting from damage to the entity’s reputation if the attack were to become public.
In addition, for the quantitative parameters (frequency of the threat, IS resistance to the attack, frequency and magnitude of losses, targeted assets, etc.) of the scenario to remain relevant, they must be profiled on the characteristics of the target perimeter. Therefore, Citalid’s expertise lies in part in defining and keeping up to date – cyber threats and available abacus evolving rapidly – a library of templates from which the analyst must be able to draw to easily and automatically initiate his risk assessment.
Accumulating data on cyber threats and their impacts therefore makes it possible to calibrate scenario “templates” and thus gradually automate the FAIR analysis. By combining threat intelligence, technical models and abacuses from open source analysis and customer feedback to assist analysts, Citalid‘s award-winning innovation platform leverages collective intelligence to ensure scientific rigor and unparalleled accuracy in quantifying financial losses.
Putting risks in perspective with the defense ecosystem
The CISO as pilot of his IS
In terms of cybersecurity management, the CISO is, unsurprisingly, the focal point of the system. To do this, he must be able to quickly visualize the entire panorama of cyber risks weighing on his IS – a “cockpit” view, in order to then inflect orientations on a larger scale. He therefore needs a GPS to guide him in his decisions: how to take his IS from point A (current risk situation) to point B (desired risk exposure), taking care to optimize his trajectory (cyber investments) while avoiding obstacles (threats) that appear dynamically along the way.
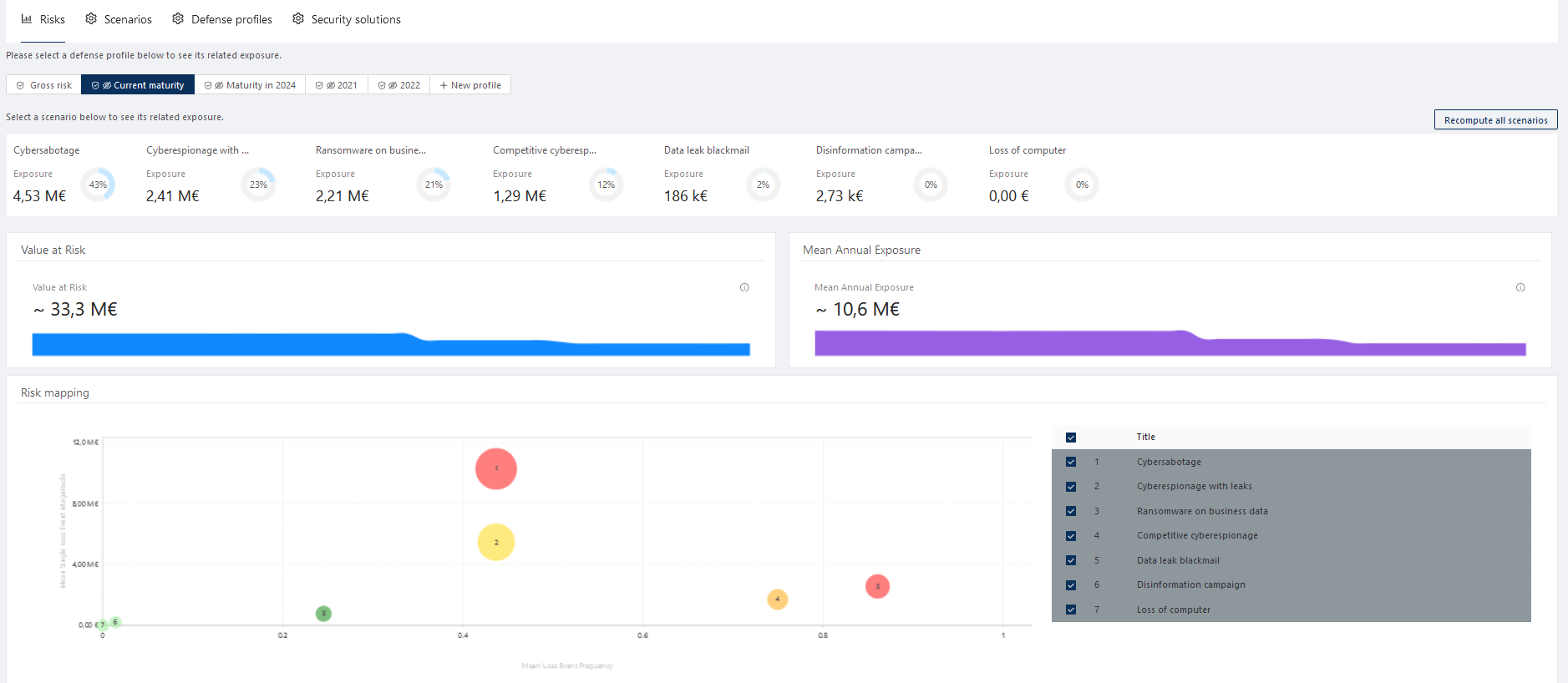
Example of a risk dashboard, illustrating the ISSM’s cockpit vision.
Once the various scenarios have been established and the quantification carried out, the difficulty lies in the possibility of translating these “raw” risks into a strategic roadmap. The first step is to put these risks into perspective by comparing them with the current defensive infrastructure of the IS. Knowledge of its environment is a prerequisite for the CISO’s analysis. All the more so as, in terms of defensive infrastructure, two major options exist and sometimes complement each other: opting for a logic of defensive maturity based on compliance with one or more reference systems (ISO 27k, NIST, CIS, etc.) or carrying out – and then comparing with peers – an inventory and evaluation of all the security solutions deployed on the perimeter.
“A permanent confrontation between theory and experience is a necessary condition for the expression of creativity” [1]. 1] The aphorism could not be more revealing of the method described here: that of the confrontation between theory (raw risks) and experience (evaluation of defensive maturity based on a multitude of feedback and incidents) as a necessary condition for the creation of a roadmap. The confrontation makes it possible to obtain the “net” risk with which the company is really confronted, lower than the gross risk since it considers the defenses of the IS.
Fueled by “actionable” metrics, the decision-maker will now be able to have visibility on his real risk in his own language, and consequently be able to arbitrate and determine its destination – his B point – according to his appetite for risk and the company’s policy. Which scenarios should be dealt with by investing to reduce the associated risk? Which ones should be maintained, given their low economic impact? Which ones to share with a cyber insurer? However, as we will see, the modelling of net risk described in the previous paragraph requires a consequent knowledge of the threat ecosystem in which it is embedded.
Cyber Threat Intelligence, a catalyst for optimal risk management
One of the main shortcomings of risk management in cybersecurity is the difficulty in deploying an approach that reflects the reality of the risk “on the ground”. The CISO or Risk Manager must therefore also have a radar to dynamically detect obstacles in his path (threats) and, as far as possible, anticipate and prevent impediments.
Thus, just as a rock slide on a road is the result of a conjunction of multiple factors (weather conditions, geological characteristics, human activity, etc.), an attacker’s action depends on many elements. These elements should, as far as possible, be observed and included in the risk analysis. Consequently, Cyber Threat Intelligence (CTI), a discipline dedicated to the study and contextualization of attackers’ operating modes, enriches and energizes traditional risk analyses. The mastery and inclusion of this discipline in cyber risk management is one of Citalid’s major differentiators and permeates its entire corporate culture.
How can CTI data be operationally and sustainably combined with the risk calculations announced in the previous paragraph? We can get an intuition of this by noting the following three facts:
- The company’s market segment helps to determine the operating methods most likely to be of interest to the company;
- The attack techniques used by these operating methods and their centers of interest within the targeted information systems make it possible to identify the most critical assets and to know how to improve their protection;
- By comparing again the CTI data defined in the two previous points with its defensive infrastructure, the entity can identify which scope (in the sense of a security repository) or which defense solution is not cost-effective enough (reduction of the risk in relation to the cost).
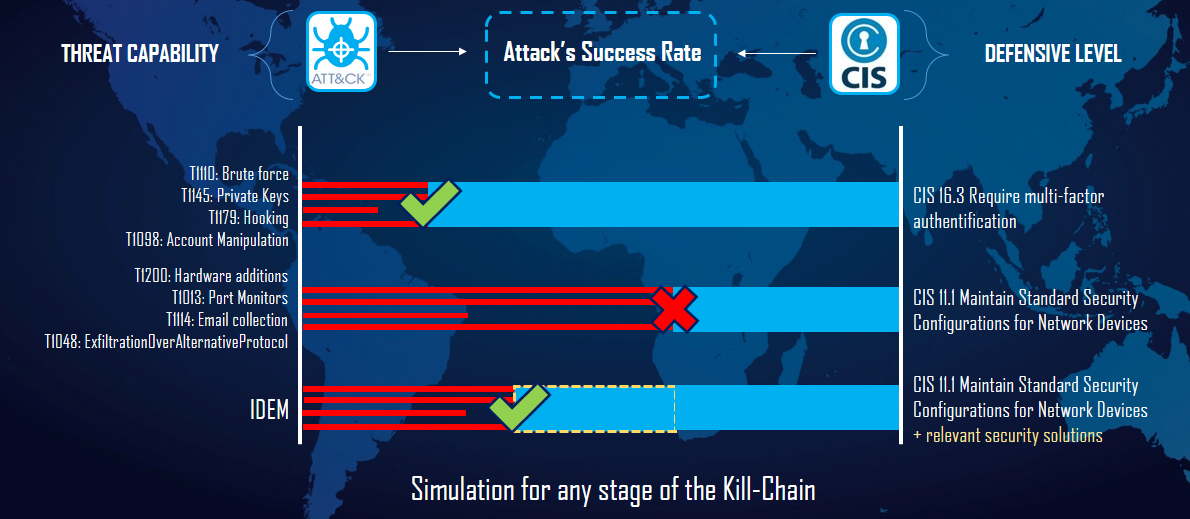
The diagram above represents a concrete example of the application of CTI to risk analysis, acting as a real catalyst for drawing up guidelines. A modus operandi is technically expressed through its “Kill Chain”, i.e. the sequence of attack techniques it uses to achieve its objective. Citalid has mapped the links between these TTPs (Tactics-Techniques-Procedures) and specific points of different security reference systems (here the CIS20), the latter being the defensive measures best adapted to the TTPs defined in the diagram. On the first line, for example, the CIS 16.3 measure (among others) is sufficiently deployed at the target entity to limit the impact of the TTPs indicated at this stage of the Kill Chain. On the second line, on the other hand, the opposite occurs: the CIS 11.1 measure is not mature enough to provide effective protection against the sophistication of the attacker. It is therefore on this line that the defender potentially needs to concentrate.
The last line crystallizes the interests of the enrichment of the analysis by the CTI. The yellow square determines the maturity progression due to the implementation of security solutions relevant to the CIS 11.1 measure (e.g. a network device management system), which are automatically determined and recommended to the user in the case of the Citalid calculation engine. In other words, this differential indirectly expresses a path towards optimal maturity and resilience for this specific scenario, the starting point for the definition of a tailor-made cyber investment strategy.
Turning analysis into strategy
Formulate a cyber strategy aligned with group objectives
A successful and relevant risk analysis is characterized by the ease with which the observer can immediately visualize how to translate data into action. It must therefore be intelligible and coherent for the recipient, whatever his or her technical level and position in the organization chart. In other words, risk analysis alone is insufficient: it can only be truly useful if it gives rise to a long-term strategy.
This vision, strongly oriented towards the most strategic levels, marks the very DNA of Citalid. Behind the calculation of the risks (raw and real) and the most effective recommendations (referential as solutions) thanks to CTI, the objective is to be able to propose an indicator of the return on investment (ROI) of the security solutions. By visualizing his initial position (A), his desired position (B) and the different possible paths (defense investments), the final decision-maker must be able to compare the ROI of the different options and draw up a cyber investment strategy in line with his budget and real objectives.
Moreover, the objective behind this singular approach is twofold. Firstly, it is a question of accompanying our clients in the definition of their cyber security strategies and in the application of a co-constructed action plan, aimed at compensating for the flaws made visible by the analysis. However, in order to keep this strategy realistic, it is essential to ensure that it can be part of a global dynamic and therefore quickly assimilated by a higher hierarchical body (COMEX). To meet this need, Citalid has refined its service so that it is in line with the realities of the CISO:
- By adapting the platform in terms of ergonomics, level of technicality and language, so that the dashboards are transparent and easy to interpret;
- By assisting our clients in defining budgets and in their legitimization and justification (advocacy) in view of the reality of the threat.
By aligning cybersecurity strategies with broader investment strategies, in line with the objectives set by the group, Citalid intends to guarantee and reinforce the predominant role of the CISO in steering cyber resilience.
Capitalizing on the approach through the deployment of a risk index
The major advantage in choosing to take a global approach to security lies in its potential for aggregating risk at any level (group, business unit, application, project, etc.) and for standardization (comparison between perimeters and peers). Like rating agencies, this “scoring” of the entity, which takes into account not only its level of maturity on its exposed assets but also its risk management strategy, internal organization, the reality of the threat, its own business context, etc., can be transformed into a global risk index, symbol of the entity’s resilience and monitored by its management. This is truer since a scientific approach based on many heterogeneous parameters presents a desirable objectivity, for the entity as well as for its partners and collaborators.
This time, it is no longer just a question of positioning oneself in one’s environment, but of positioning oneself in relation to possible peers (comparison) and partners (guarantees). A risk index reflecting high resilience and sound risk management will ensure that its suppliers or end customers have optimal security and respect for their data, while reassuring investors that their funds are being used correctly.
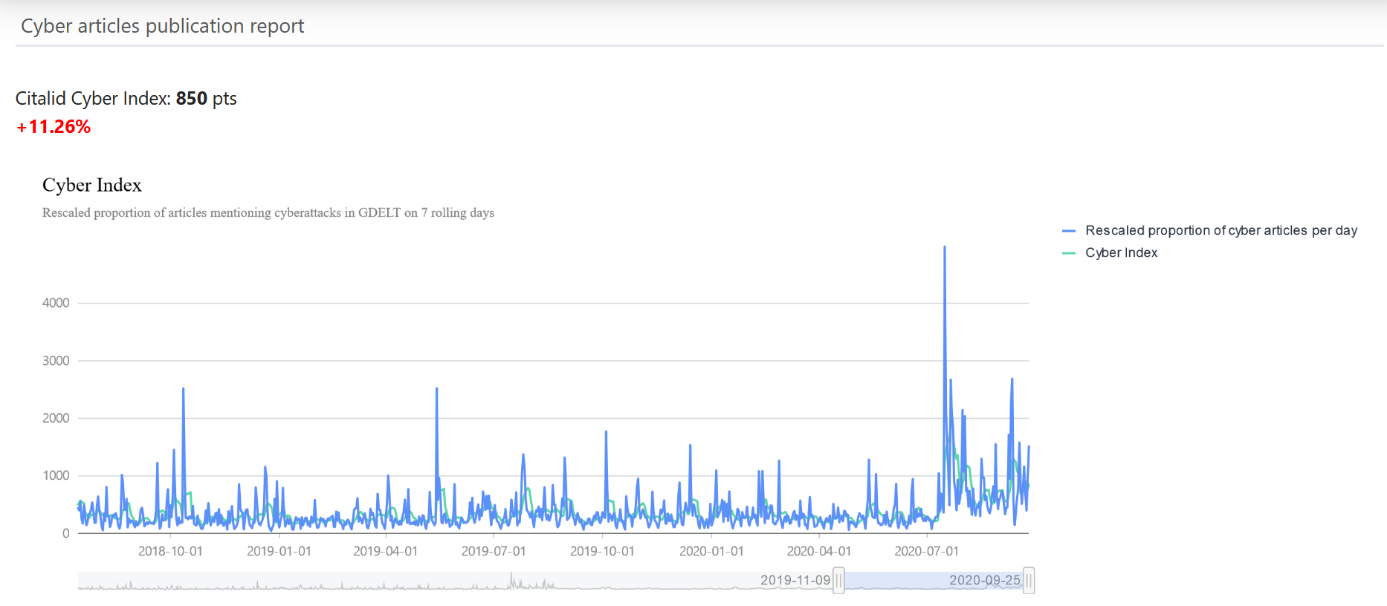
Examples of risk indices produced by Citalid: in this case, a ‘Cyber Weather’ that identifies variations in a client’s media exposure.
Other players could also benefit from such an index: the insurance industry, and cyber-insurers. The quantification of cyber risk remains an obstacle for them, as traditional actuarial approaches are limited by the lack of historical cyber security data. Citalid’s model, presented here, combines threat expertise, advanced probabilistic models and innovative attack-defense simulations to overcome this lack of data. Our scoring and metrics, based on risks rather than on a simple level of defense, allow us to refine the insurance model to be as close as possible to the real needs of our clients.
Thus, quantifying cyber risk and the return on investment of security solutions is one of the biggest challenges facing today’s CISOs, Risk Managers and insurers. Through its innovative approach, Citalid responds to this need to reposition cyber security at the heart of corporate strategies and to optimize its action plans and investments.
[1] Attributed to Pierre Joliot-Curie


