More and more clients request our help regarding their third-party cyber risk management strategy. Indeed, third parties constitute a privileged attack vector. A recent study from Soha Systems showed that 60% of security incidents involve directly or indirectly a supplier. The most glaring examples are the accounting software M.E.Doc identified as the patient zero of NotPetya and Cloud Hopper attacks which aim at compromising cloud service providers to attack a targeted company.
Paradoxically, only 35% of organizations consider their third-party cybersecurity management process as effective (according to a study conducted by the Ponemon Institute).
How to define an effective third-party cyber risk management strategy? What are the key success factors?
Adapt your third-party cybersecurity strategy to the risks
From business partners to subcontractors and IT service providers, a lot of your suppliers manage or have access to your assets. Therefore, they represent a risk for your organization and thus it is important to ensure they are committed to respect a cybersecurity level that meets your requirements.
Depending on which business perimeter they operate and which type of service they provide, the level of risk would be more or less critical. Therefore, our recommendation is to classify your suppliers to adapt your cybersecurity strategy according to the risks they imply.
Since your suppliers can be thousands, this classification will also allow you to prioritize and keep an acceptable workload for your teams.
In order to do that, our first piece of advice is to inventory your suppliers. We notice that few organizations have an exhaustive cartography and that its realization is a tedious project that requires the involvement of many stakeholders (purchasing, legal, department, business…). Therefore, we advise you to start by defining a process to capture your new third parties and by identifying your suppliers involved in the critical business activities identified in your BIA (Business Impact Assessment). Afterwards, you will be able to extend progressively to other third parties.
From this cartography, you will be able to assess your supplier’s criticality and classify them on a scale with several levels. We advise you to consider the following criteria:
- The business criticality of the project or the asset the supplier is working on;
- The degree of interconnection to your information system;
- The access to sensitive or confidential data;
- The service exposure on the Internet.
Nevertheless, we can observe in our client’s environment that applying those criteria can be challenging due to the lack of information about some third parties. Then, we suggest organizing workshops with cybersecurity teams, IT teams and business teams to validate your cybersecurity classification by expert knowledge.

Example of a classification scale with 3 levels
Consider cybersecurity throughout the whole lifecycle
The feedbacks from the field show that most organizations assess their third party’s cybersecurity level before contracting and include cybersecurity clauses into their contracts. Nevertheless, cybersecurity is not always taken into account thereafter.
We recommend integrating cybersecurity throughout the whole third-party lifecycle by empowering them and adopting a control position.
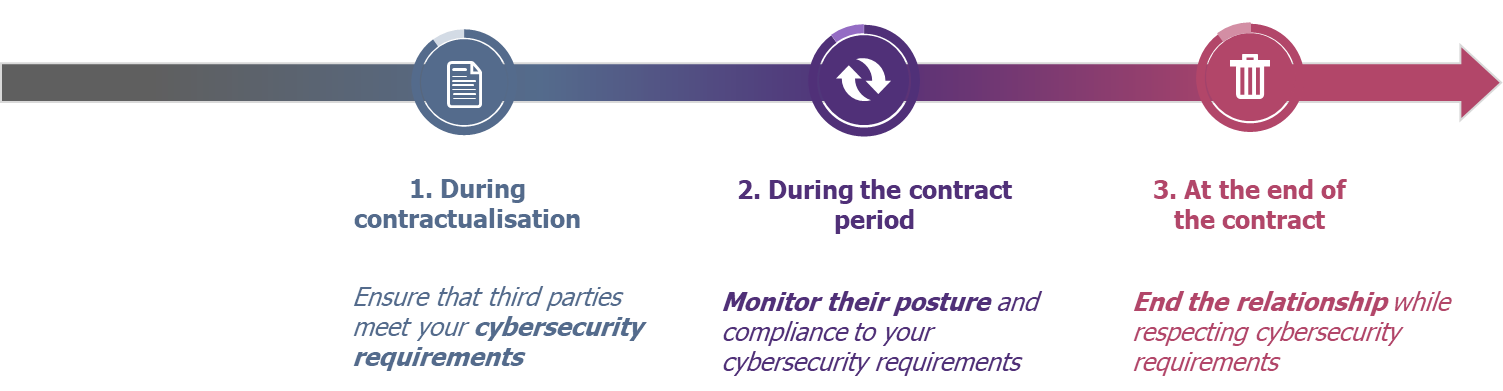
Third party management lifecycle
During contractualisation
Before the contract signature, the objective is to ensure that the supplier chosen by your business meets your cybersecurity requirements. To do so, we advise you to integrate cybersecurity at each step of the supplier selection process:
- Include your cybersecurity requirements in your Request For Proposals;
- Assess the maturity level of the suppliers responding to your Request For Proposals;
- Provide a cybersecurity recommendation to your business according to the project sensitivity and the risk implied by the third party,
- Include in the contract cybersecurity requirements adapted to the criticality and the type of service delivered.
During the contract period
To ensure your third parties respect their cybersecurity commitments throughout the contract period, we advise to:
- Integrate your third parties into your risk analysis when they operate on the scope of a project. For instance, the methodology allows you to identify all the stakeholders involved in a project and to define an action plan to secure and monitor your ecosystem. The implementation of the security measures must be followed-up with the third-party;
- Organize cybersecurity reviews at a frequency adapted to the risks and thus the level of classification. For instance, the most critical third parties can be reviewed at least annually while the less critical ones can be reviewed at contract renewal;
- Define a process dedicated to cybersecurity incidents involving a third party and create emergency instructions;
- Perform audits only when necessary (for instance following a major cybersecurity incident or after identifying a critical risk…)
At the end of the contract
A contract renewal is an opportunity to perform a new assessment of the third-party cybersecurity posture and if necessary, update the contractual requirements.
If the contract ends, you must apply your reversibility clauses and ensure that cybersecurity is part of the decommissioning of the service provided.
Industrialize third parties’ assessments thanks to market solutions
We observe that many organizations assess and monitor the cybersecurity level of their third parties with proprietary and non-automated questionnaires that require many external resources. In addition, big-sized suppliers may refuse to complete these questionnaires while smaller ones may not always answer correctly.
Furthermore, we also notice that few organizations have yet adopted a mass assessment approach.
In order to rationalize the approach, we therefore suggest giving-up these historical assessment tools to adopt solutions adapted to the supplier classification level and thus be able to scale up.
For the most critical third parties
We advise you to adopt a co-constructive approach with your most critical suppliers, while adopting a position of control. This translates into the following actions throughout the lifecycle:
- Assess your most critical suppliers based on their cybersecurity certifications and compliance reports on the scope of the service provided;
- Define a contractual Security Assurance Plan to precise the security governance of the service;
- Organize security reviews (at least once a year) to control the security level of your suppliers based on the indicators defined in the Security Assurance Plan (maintaining certifications, security incidents, audits, security roadmap…). These committees are also an opportunity to build a relationship of trust with your suppliers, for example by discussing security news and events as well as the conferences that you could do together.
For third parties with a medium to low criticality
In order to take a massive approach in assessing and reviewing the cybersecurity level of your non-critical third parties, market solutions can be used. Indeed, editors and startups (such as CyberVadis, CyberGRX, Risk Ledger…) are positioned on the industrialization of third party’s cybersecurity assessments. This will be the topic of one of our next articles.
Their solutions are based on maturity questionnaires whose results are shared with all their customers. More concretely, these platforms work as follows:

Third party maturity assessment platforms
Although these solutions are currently not customizable according to your organization’s specific requirements, they will allow you to:
- Get cybersecurity assessments tailored to non-critical third parties;
- Reduce the workload of your cybersecurity teams;
- Share third-party assessments with other customers and therefore be able to quickly access assessments already performed;
- Adopt a win-win approach with your suppliers who will share a single questionnaire with all their customers and will be proposed action plans to remedy any discrepancies;
- Popularize third-party cybersecurity management to your business or purchasing teams thanks to didactic scores on different topics.
Ensure the effectiveness of your third-party cybersecurity management process
From business to IT project managers and including purchasing and legal teams, third-party cybersecurity management involves many players in your organization. It can only be successful if your process is well-known and applied by all. Therefore, it is key to train and raise the awareness of all stakeholders.
To ensure that your process is properly implemented, it is important to define and implement controls covering all stages of the supplier management life cycle. As a first step, we recommend that you define realistic targets by focusing on your most critical third parties. Over time, these targets may evolve to consider your suppliers with lower levels of criticality. Your controls may include the classification of your third parties, their assessment and their review at an appropriate frequency during the contract period.
Integrate third-party cybersecurity management in a “Know Your Supplier” approach
Just as the KYC (Know Your Customer) approach in B2C sectors, we suggest that you include third-party cybersecurity management in a KYS (Know Your Supplier) spirit where the objective is to take all supplier risks into account in a consolidated way.
Cybersecurity assessments and notably maturity assessment platforms can be integrated within supplier management tools (source to contract), as well as financial, CSR, environmental impact, anti-corruption and anti-money laundering assessments. This will ease the integration of cybersecurity into your sourcing and supplier review processes.
See you next episode for an article about market solutions that automate the cybersecurity assessments of your suppliers.


