Networks are at the backbone of every modern systems; for the ecosystems of connected objects, this is no exception. In this article, we will provide you with a methodology to use from the get-go to help in choosing a secure and suitable network for your IoT project.
In this example, we will assume that you are a coffee machine manufacturer. Your current project is to build a connected coffee machine for your corporate customers. You have identified multiple use cases for this IoT machine. For instance, it automatically orders new coffee capsules when the stock falls below a certain threshold. A second option would be that the coffee machine, sends automatic alerts to your servers when maintenance management such as cleaning, repairs, etc. is needed. Finally, it offers your clients functionalities for monitoring consumption.
How can you choose the right network for your needs? What questions should you ask yourself? How do you make a good choice while considering the overall security of your system?
First Step – Define your business requirements and perform a risk analysis
First, you must identify the requirements for your IoT network which are twofold: business and security requirements. We characterize these requirements with levels 0 to 3, 0 being the lowest and 3 being the highest level.
For the business requirements, you must answer questions such as:
- How far should the object’s signal reach?
- How much bandwidth do you need?
- What is the autonomy of your object?
In our example, we assume that your connected coffee machines will be distributed to corporate customers operating over a large geographical area (i.e. over 100 km radius). Therefore, you will need a wide coverage to enable your customers’ widespread machines to communicate with your Information System.
Two business cases are outlined here: If your customer agrees to connect your machine to its existing local network, you will then only need a short-range wireless network between the machine and the internet router. If they refuse to do so, you will then need to set up a long-range network as you will deploy your service and machines over a wide area.
For the bandwidth, a small/short amount will be needed as it solely requires to be able to send small data packages a few times a day at most (capsule orders, alerts, general status, …).
In regard to energy consumption, a coffee machine is traditionally connected to a power supply to perform its tasks; henceforth, power does not constitute an issue in terms of IOT, i.e. the object autonomy is therefore not constraint. There is no energy consumption requirement per se as it is already covered by the coffee machine’s connection to the power grid.
We summarize the levels for business requirements as follows:
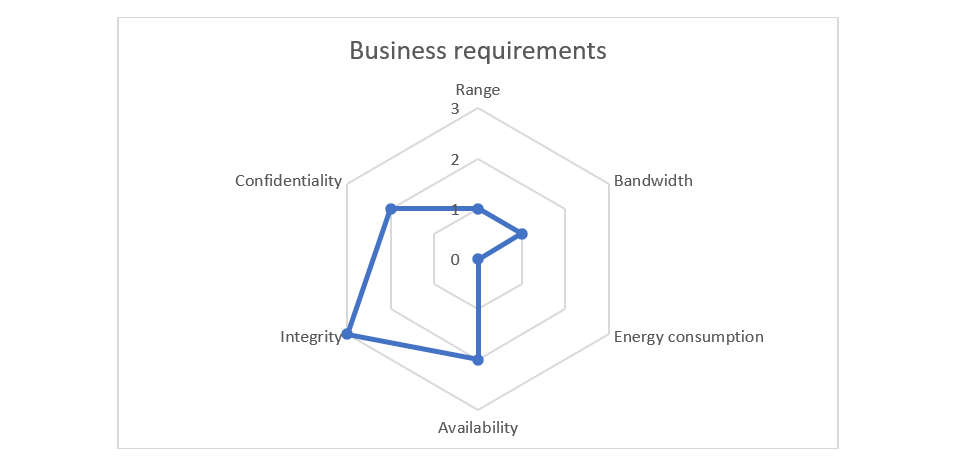
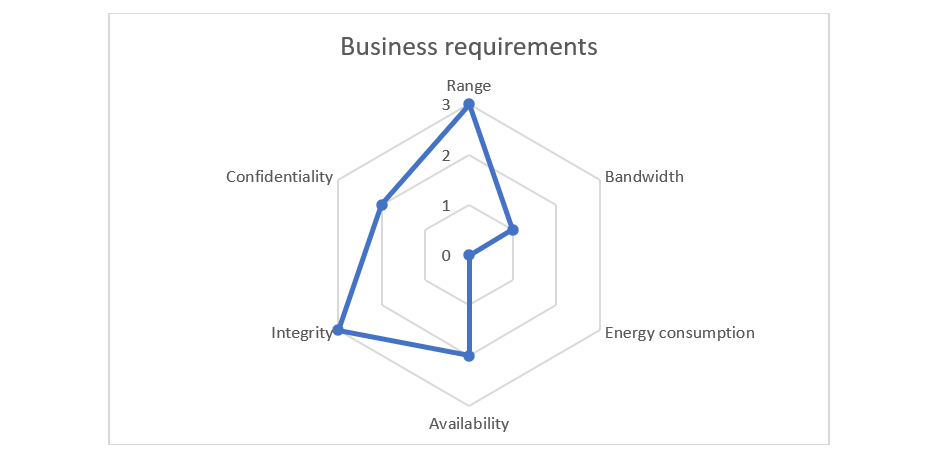
- Range (R) = 3 or 1
- Bandwidth (B) = 1
- Energy consumption (E) = 0
Having defined your business requirements, a risk analysis must be conducted to formulate the security requirements of your project for availability, integrity, confidentiality, and traceability purposes.
A loss of availability would occur in the event of a dysfunction on the connected coffee machine that would render it unusable for a customer. A loss of access to the network or unavailability of backend servers should never result in the machine being unavailable: it must remain working off-network. However, if a dysfunction of the machine occurs, we assume that you would want it to be reported back as quickly as possible through the network in order for maintenance actions to be triggered.
How long can this last? The answer would be several hours rather than several days, as we wouldn’t want to deprive employees from their coffee breaks! Therefore, 4 to 24 hours is an acceptable window of unavailability which can be translated into an availability requirement level of 2.
A loss of integrity would result in data corruption. For example, a potential excess order of coffee capsules may occur by altering the messages sent by the coffee machine or by replacing the same order multiple times. In both cases, this would result in a financial loss for your client. Data on the network needs to be communicated rigorously and exactly. Hence, we can conclude this is a requirement level of 3.
A loss of confidentiality would result in data being divulged; orders quantities are rather sensitive data that shouldn’t be shared with external parties. It needs to be ensured that data is communicated securely on the network and is not accessible by externals parties. Hence, we conclude that confidentiality has a requirement level of 2.
For traceability, and for simplification reasons, we choose to leave this aspect aside assuming that it is already accounted for by the study of the first 3 criteria.
In a nutshell, risk analysis concludes to the following security requirements:
- Availability (A) = 2
- Integrity (I) = 3
- Confidentiality (C) = 2
For more details about risk analysis methodology for smart objects, you can refer to this article.
At the end of this analysis, you obtain for both of your business cases a radar chart of your requirements.
Business case 1: your customer connects your coffee machine to its local network
Business case 2: your customer does not connect your coffee machine to its local network
Though not discussed in this article, financial aspects are also important and depend on various factors such as the network operator pricing model. Same goes for geographic constraints as some networks may not be available on some regions.
Eventually, the ease of configuration of the network may be included in your business requirements, especially if your connected object targets a B2C audience.
Second step – Choose your IoT Network
Building on business and security requirements, we developed a methodology to choose the right network that will be optimal to meet your business and security needs: range, bandwidth, energy consumption, availability, integrity, confidentiality.
The three business requirements are mandatory, the network you choose must fulfil them, otherwise, it will be eliminated.
For security requirements, the assessment requires pre-emptive analysis. Between two networks that cover the same business requirements, you should choose the one that offers the best level of security with the minimum cost.
If a network doesn’t cover one of the security requirements, you will have to implement some additional security feature as a part of your project backlog, consequently raising your costs.
You should also be vigilant that the additional implementation doesn’t impact the system’s performance. For instance, if you implement data encryption at the application layer, increasing processing times would negatively impact your maximum data rate or could be constrained by the hardware capabilities of the device, with a potential financial impact in case of a hardware upgrade. Consequently, one of your business requirements may no longer be met.
In case high availability is required (A=3), you ought to choose a robust network by design that will meet your real-time needs.
In fact, spread spectrum (like Bluetooth or ZigBee) or frequency hopping modulated protocols (like Sigfox or Bluetooth) are more resistant to radio jamming or radio interferences.
These types of networks are particularly recommended when availability is an important requirement, such as on an industrial production line.
Moreover, mesh protocols are known to be more reliable and scalable than point to point protocols. However, for them to achieve efficiency, they need to be used in a context where multiple connected devices are linked together. Mesh protocols like WirelessHART can also guarantee real-time communications. Their usage is especially adapted to an industrial context.
A simple methodology to choose the right network is to confront your business requirements to the network’s business and security offerings.
In the following radar charts, we present different types of IoT networks providing different levels of business and security offerings, and we compare each one of them to our business requirements.
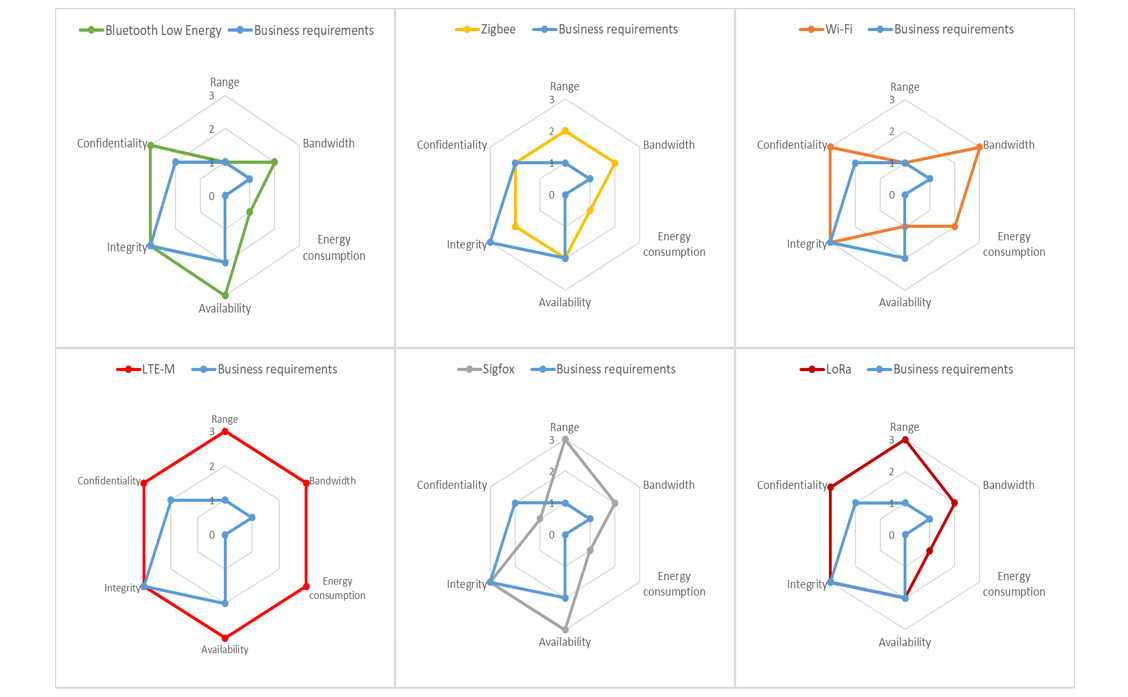
Business case 1: your customer connects your coffee machine to its local network
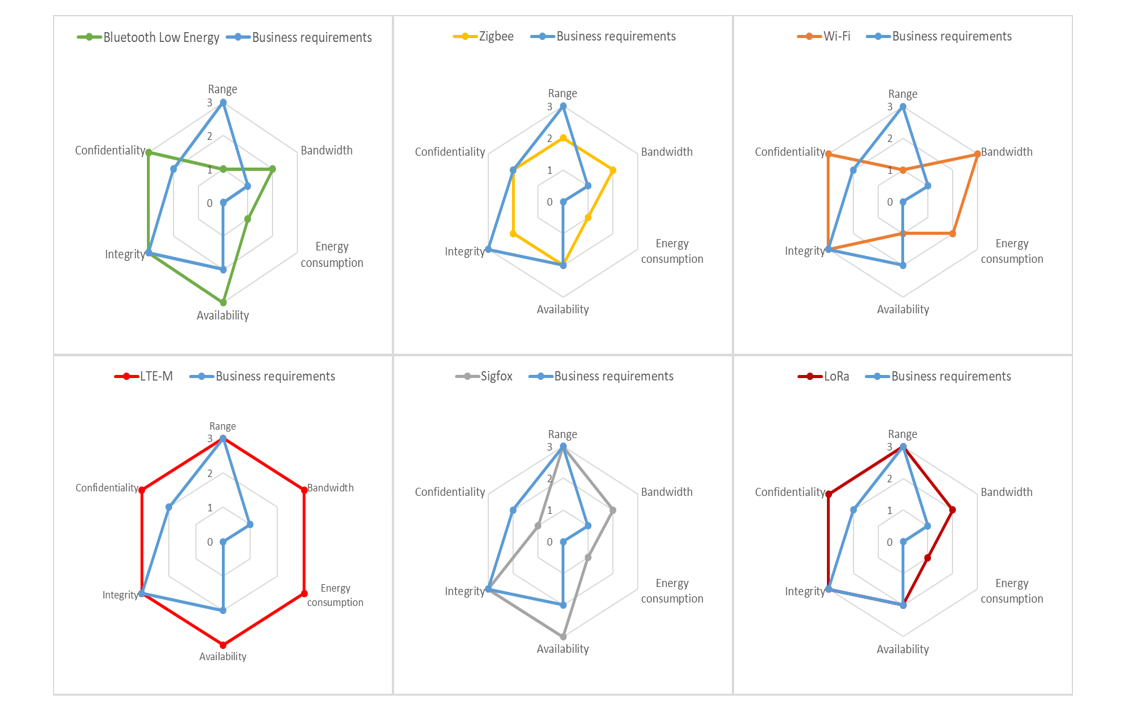
Business case 2: your customer does not connect your coffee machine to its local network
Let’s apply the previous methodology to your connected coffee machine. First, we use our previous radar charts to see which networks comply with our business requirements.
Business case 1: your customer connects your coffee machine to its local network
For your first business case, Bluetooth and Wi-Fi are two viable short-range options if your customer connects the machine to its local network. On the one hand, Bluetooth meets all the security requirements, but it is less straightforward to implement compared to Wi-Fi. On the other hand, Wi-Fi meets all of them except for availability but that is something we can work out with SLA agreements.
Business case 2: your customer does not connect your coffee machine to its local network
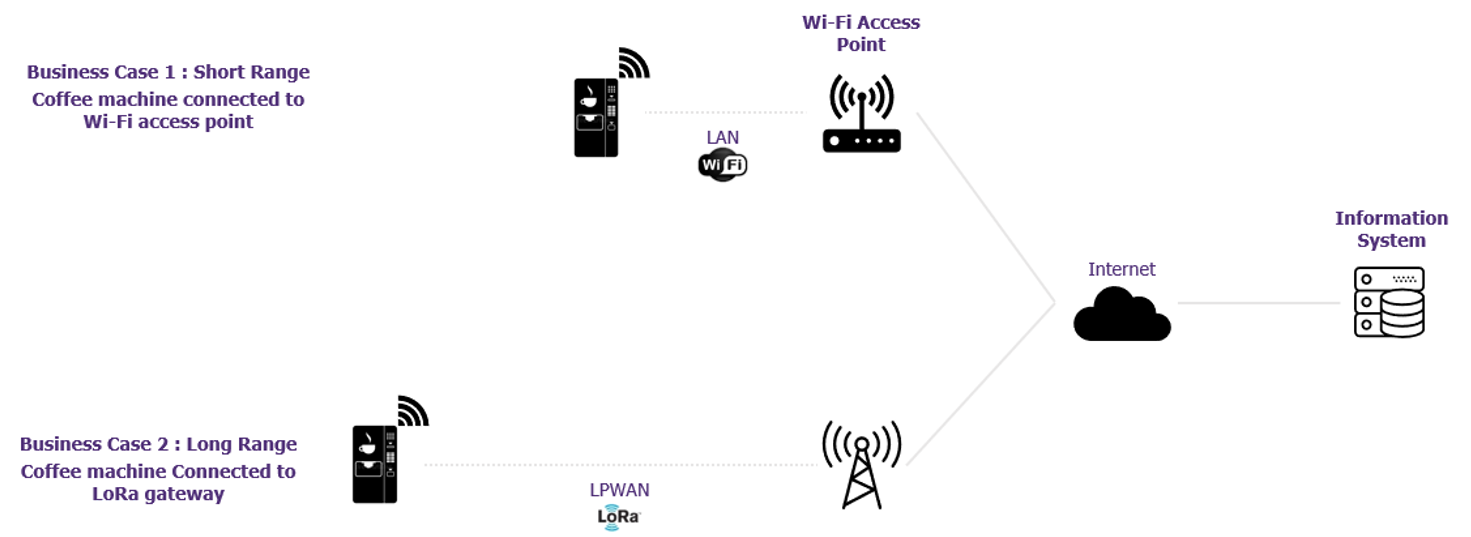
For your second business case, Zigbee, BLE and Wi-Fi are clearly out of the equation because they do not meet the range requirements. However, LoRa, LTE-M and Sigfox are still in the mix.
We use the radar charts again, this time to assess these three candidate’s compliance with the security requirements.
Sigfox does not meet one of your security requirements (confidentiality) whereas LoRa complies with all security requirements. LTE-M is the best offering as it meets all your requirements, but it is also the most expensive. We conclude that LoRa is a relatively good candidate.
In conclusion, we have one good candidate: LoRa which will require the deployment of a new network and an alternative using a pre-existing Wi-Fi network. It should be noted that you may refuse to connect to the Wi-Fi network on company premises for security reasons.
We will undertake a new scenario in a next article: a customer company buys the machine and discusses what payment options to use.


