
DECRYPTION
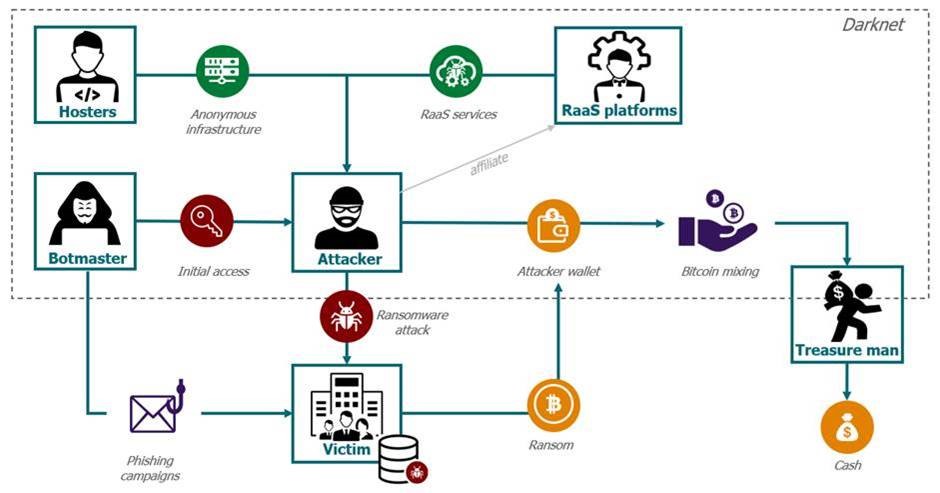
The underground economy of the ransomware
In recent years the products of the underground economy have evolved quickly. Cyber criminals now offer services for others to purchase, the most popular being: Ransomware-as-a-service (RaaS).
Let’s pretend you are a hacker aiming to launch a successful ransomware attack. Only, you are quite new to the business. What do you think you need? A very sophisticated level of coding and development skills? Not anymore. The whole underground economy of RaaS can provide you with every necessary element to conduct your attack, from the access credentials to the mixers helping you to launder your gains.
What do I need for my ransomware attack?
Need #1 – Enter my target’s network. In order to do so, you need to acquire access to the victim’s network: your first providers are the initial access brokers (IABs) or botmasters.
They are specialized in vulnerability exploit. They identify the flaws through massive phishing campaigns and/or scans and then access the system. Once inside, they set up remote persistent access to the target’s network. The botmasters then sell you the access: depending on its level of quality, prices can range from $1K to $100K (seen for a Mexican government body). The average price for network access in 2020 was $5,400. The botmaster’s services also include information on the financial health of the targeted victim, to help the attacker set the highest realistic price for the ransom
Need #2 – Anonymous infrastructure to host my hacking tools and store my data. The second actor of the chain is the bulletproof hoster, providing you with infrastructure-as-a-service, including anonymization services. The subscription can go from $5 per month to any price.
Need #3 – A ransomware to encrypt my victim’s files!
Now the main part: where can you find a ransomware? The most popular way is to subscribe to a RaaS platforms, offering 4 main services:
- Provide necessary information: potential victims, their financial status, security level…
- The ransomware: the malicious code and a tool kit to facilitate the attack
- Negotiation service (including support to collect the ransom)
- Money laundering service
Other services are offered, according to what you are ready to pay. Here is an example of different price subscriptions and services on a RaaS platform. It can go from $100 to $84,000 (Maze).
Where is the money going?
Need #4 – Clean my money! Once the attack is successful, the people in charge of the money laundering and money mules take the stage.
After a payment to the perpetrator’s wallet is made, money is then dispersed and mixed across numerous wallets, to provide anonymity. This bitcoin mixing through multiple other wallets makes the payment tracing quite difficult. In the Colonial Pipeline case, the wallet received the 75 BTC from them, mixed with 57 payments from 21 different wallets. However, this case has proven that the tracing is not insurmountable. No matter how many times the bitcoins are moved, ultimately it has to go through cryptocurrency trading platforms (such as BTC-E) and be cashed out at exchange points.
Recently, the situation involves global anti-money laundering (AML) regulators armed with blockchain sleuthing tools to trace and screen transactions, making the cash-out process harder to go unnoticed. To face this upgrade, cybercriminals can use a system described as “The Treasure Man”. You can find and hire them on darknet marketplaces (such as Hydra). They will cash-out your gains and hide them – physically – for you to pick up. “They bury it underground or hide it behind a bush, and they will tell you the coordinates. There is a whole profession” (Elliptic)
Who are the people behind the RaaS platforms?
RaaS platforms are based on very organized and structured groups such as SMEs. REvil (one of the biggest RaaS) indicated having a team of 10 developers and systems admins, besides their project managers. To recruit the best experts, the platform’s leaders choose their employees after a challenging recruitment process. The candidates prove themselves through job interviews, hacking exercises and agree to an “ethical charter”. You can read here the undercover investigation of journalists who followed the process to be hired as hackers by a RaaS.
The subscribers or affiliates of a RaaS platform (in this story, that’s you) are “only” in charge of the intrusion, the data collect and the ransomware deployment on the victim network. The affiliates usually pocket between 60 and 80 % of the ransom, with the rest going into the operators’ coffers. The RaaS platform of Netwalker requires 20% of the ransom, but other groups can ask 70%. REvil recently announced being paid at least 100,000,000$ per year.
No honor among thieves?
If the RaaS market is a very well-organized business model, it still is the underground economy we are talking about. It’s not because you are a potential RaaS client, that you are in a safe place.
The two years of research on the darknet of Håkon Melanda have shown that most of the RaaS items sold on the darknet markets are frauds, where the buyers either get rubbish or ransomware that redirects the whole payment somewhere else than the buyer’s wallet. If the authentic RaaS vendors are indeed taking the lion’s share in terms of gains, the others are not doing bad either by targeting naive cybercriminals.
If the RaaS distribution process significantly facilitated the ransomware attack for more people, it does not mean it is accessible to every internet user. Not only employees of a RaaS platform need to have a strong resume to be hired, but the affiliates too have to prove their skills before being allowed to subscribe to a RaaS service. Well-established RaaS groups such as NetWalker are known to be rather picky and carefully check any new affiliate with interviews and a short trial period. The basic requirement for an affiliate candidate is – at least – to demonstrate experience in carrying out network intrusions and lateral movement.
Conclusion: The Circle of money
This very well-organized and profitable economic system yearns for one thing: to be even more profitable, like any business. To hire better experts, with better tools and launch more sophisticated attacks to collect more money. How can they develop themselves? Through the ransom paid by previous attacks. According to Ondrej Krehel studies, most of the largest ransomware gangs were launched with seed money from previous operations such as Darkside with Zloader. Moreover, as groups sought to diversify with new operations, members adopted a sort of venture capital structure, in which one team provides funds to help another build the infrastructure and tools needed to start its operations. The more ransom that is sent to the system, the more experts will be attracted by this profitable business, the more investors will fund it.
Besides, once a ransom is paid, the payer is identified as a “good client” by the market. Cybereasons studies indicated that 80% of organizations that paid the ransom after a ransomware attack were hit again. When a victim pays a ransom, it does not guarantee recovery of their system, but it is for sure the best way to fund a future attack, more sophisticated, against themselves.
CERT-W: FROM THE FRONT LINE
The CTI Word

FOCUS TECH
File Obfuscation
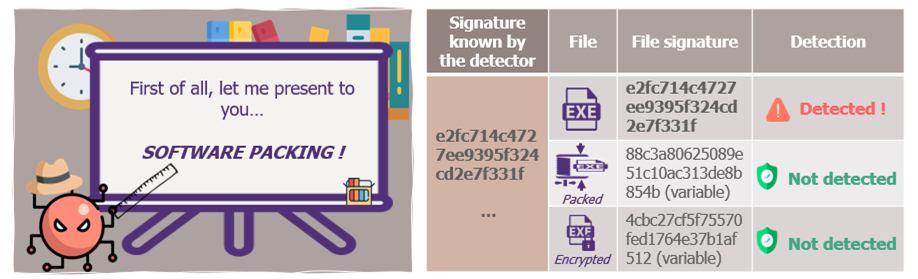
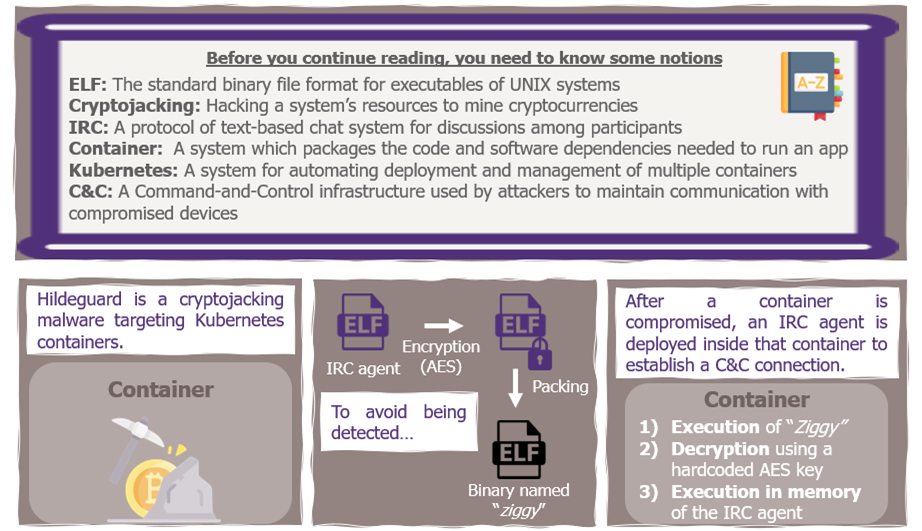
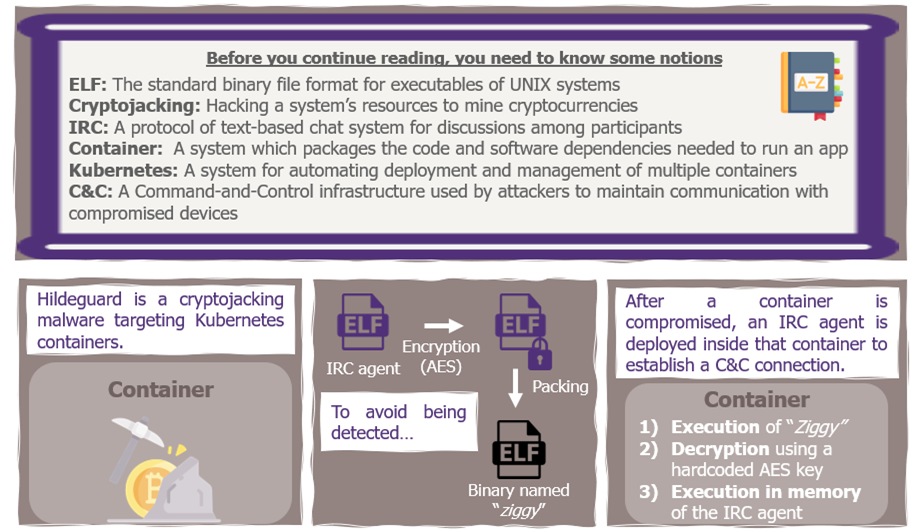
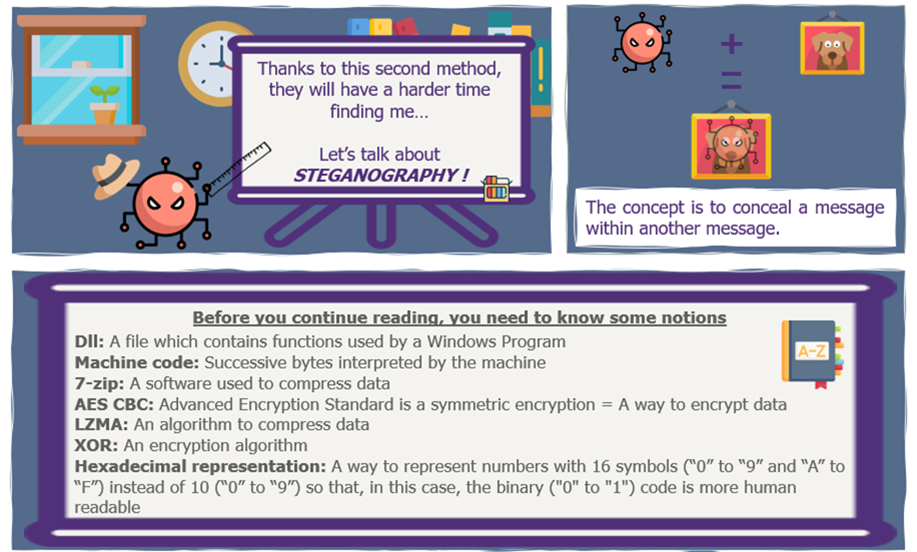
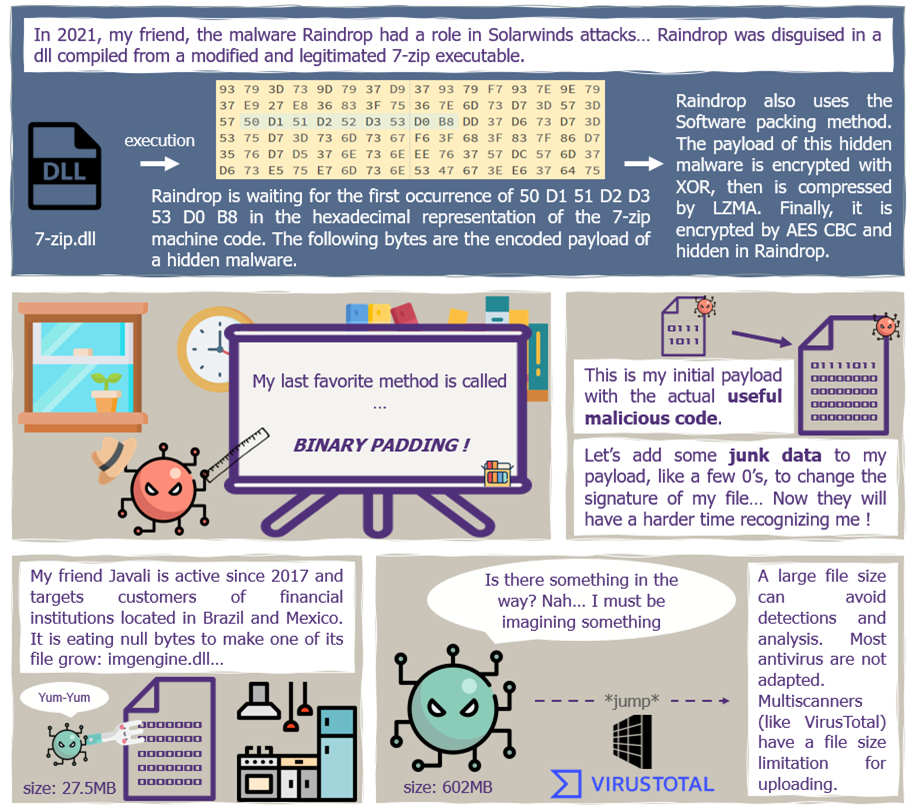

To learn more about the given malwares:
Reading Of The Month
Instead of a report, we recommend for the reading of the summer the interview of BlackMatter, who has his heart set on explaining how there are taking the best from REvil and DarkSide, their business model and their guidelines of victims’ target.



