This first edition of Wavestone’s Industrial Control Systems (ICS) Cybersecurity Radar comes at a very special time. On one hand, the health and economic crisis context is considerably weakening the companies that manage critical infrastructures. On the other hand, the cyber threat is increasing, with ransomware affecting critical systems more and more often. It is no longer enough to ask the question of how to prevent cyber-attacks: one must also plan how to react in case of a crisis, how to quickly isolate a critical industrial system and how to quickly restore a compromised system.
In this article, we expose our vision of the market and the maturity of cybersecurity for industrial information systems (IS), as well as our convictions and analysis on the subject.
What is the state of the threat to industrial information systems?
In 2011, the cybersecurity of industrial information systems, suddenly came to the forefront with the Stuxnet attack and the discovery of a state level threat against Operational Technologies (OT). For a decade, Advanced Persistent Threats (APTs) were considered the biggest threat to industrial system security, through impressive and complex attacks, such as the series of “Black Energy” attacks against the Ukrainian power grid between 2007 and 2014, or the “Triton” attack against the safety systems of a chemical plant in Saudi Arabia in 2017.
However, the Snake/EKANS case in 2020 allows us to point out a trend that has been continuously increasing for the past few years: the appearance of ransomware in ICS. These ransomwares are the result of opportunistic attacks on vulnerable systems or are side effects of attacks targeting the corporate IS, as in the case of Colonial Pipeline in May 2021.
With the ransomware business model becoming sustainable on one hand, and the emergence of increasingly connected industrial IS on the other hand, it is realistic to expect a large increase in opportunistic attacks and ransomware side effects on industrial information systems.
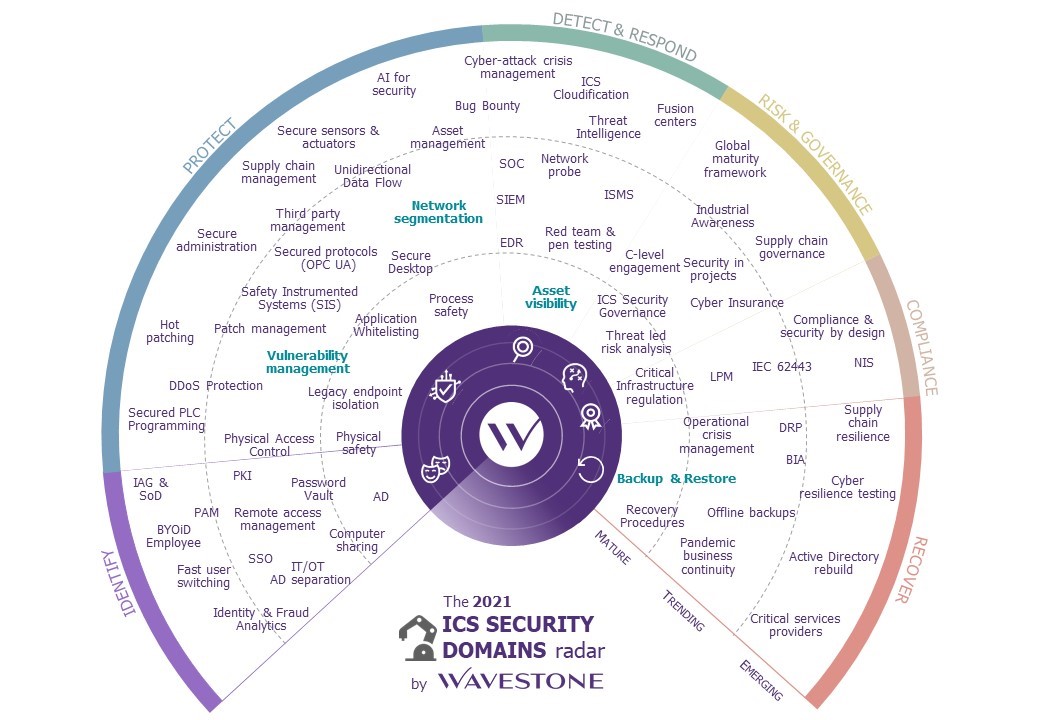
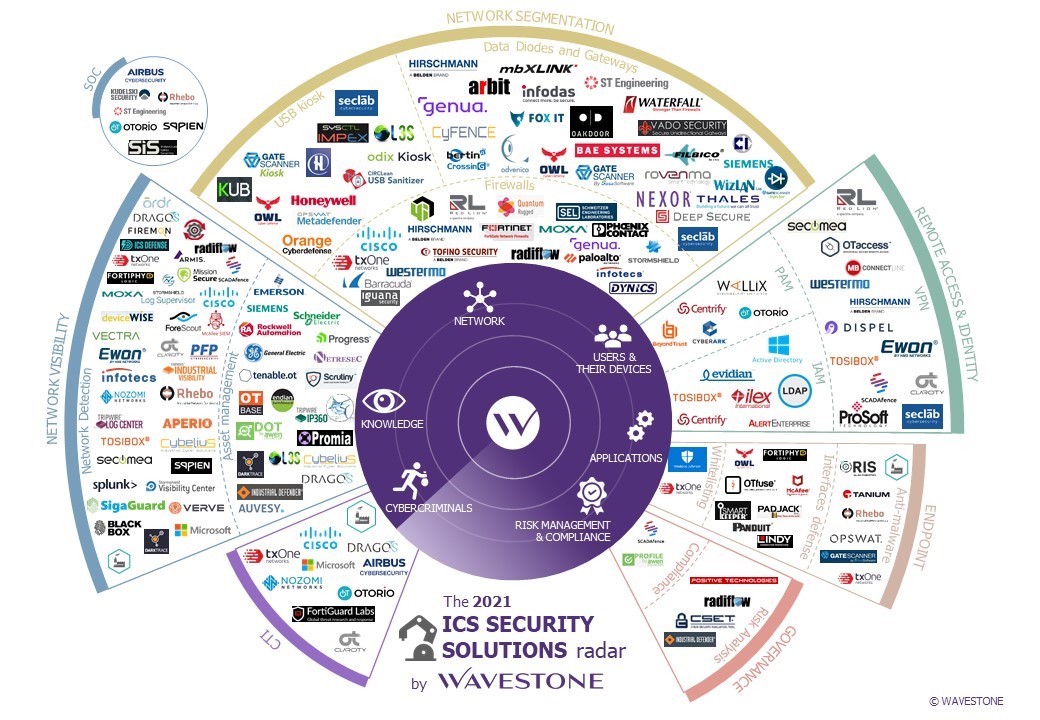
Faced with an increasing threat, companies must implement cybersecurity measures on industrial systems and define coherent strategic goals, but this requires a real investment. Therefore, we have worked on listing ICS cybersecurity domains and the solutions to secure them. This radar is not exhaustive, but it aims to clarify the topic by giving a high-level vision.
Methodology
For five months, this radar was built with five experts in cybersecurity of Industrial IS, in addition to the hundred consultants of Wavestone’s industrial cybersecurity offer.
This radar has two parts (we will call them dials): one is presenting cybersecurity products specialized in industrial IS and the other is presenting the different domains of industrial IS cybersecurity, sorted by maturity level.
Industrial cybersecurity products are identified as such according to the following criteria:
- They meet a need in the process of securing industrial information systems
- They are adapted to an industrial environment in terms of hardware and software:
· The hardware is rugged to withstand harsh conditions and/or has a long service life
· Network security products consider industrial protocols
· Terminal security products are compatible with obsolete systems.
The cybersecurity domains are also selected and evaluated based on the observations of our consultants in the field, with various customers in varied industrial domains, but in the French context.
The rest of this article highlights some of the important ICS domains, from the most mature to the most emerging. This analysis echoes and updates our 2019 publication presenting feedbacks on ICS protection and security. Indeed, if the main topics remains the same (e.g. IT/OT separation), the players and their maturity evolve quickly, bringing new issues and transforming the old ones.
Which basis should be used to secure an industrial network?
People, procedures, and resilience
The strengths and weaknesses of industrial IS and management IS are different. To implement effective cybersecurity measures in an industrial IS, one must first understand the levers already present in Industrial IS that can be useful for cyber security.
First, the operators in industrial production networks are very familiar with the processes and the usual functioning of the production system. In addition, procedures in the event of an incident are much more developed than in corporate IS. Together, these elements give a capacity to detect malfunction and to respond efficiently. A clever way to improve this resilience capacity is to add cyber incident detection procedures based on the teams’ current knowledge.
Network knowledge
Knowing your network makes it easier to secure the IS and maintain it in secure conditions by allowing risk analysis, network segmentation, vulnerability and patch management, regulatory compliance, etc.
It is possible to carry out this exhaustive inventory by hand on a regular basis, especially by using industrial maintenance tools. To go further, it is possible to automate the task with free mapping tools (Dragos CyberLens, GrassMarlin). Finally, probes (Nozomi, Claroty, Dragos, etc.) can go much further by automating the detection of anomalies on the network or even by helping with incident response.
Backup and recovery
The best resilience weapon against ransomware is the systematic and, if possible, offline backup of critical data for the production system. This practice is more and more implemented in OT systems.
However, additional conditions are necessary for backups to be truly useful. First, all the data needed for the system to function must be identified. This data can be either technical data (machine configuration for example) or business data. A risk analysis allows you to identify it efficiently. Finally, you must ensure that you are able to restore a functional system from the backups made, especially for certified systems.
What are the opportunities in 2021?
Our study has enabled us to highlight effective measures to greatly increase the security level of an industrial IS.
Segmenting your network
Network segmentation has been around for several years. However, it is still an important step in securing your industrial network. Having a segmented network allows to efficiently prevent the propagation of an attack and therefore its impact.
In addition to the use of appropriate firewalls, a network segmentation project requires competent architecture and integration teams with sufficient time and resources. Network segmentation is a balance between security and business needs. The use of new “Software Defined” network technologies allows to perform segmentation in a more agile way.
Separate the management network from the industrial network
The connection of industrial IS to corporate IS is necessary today, but it is also a vector of risk.
The solutions to be implemented depend on the criticality of the industrial network and the necessary flows between the two networks. However, a single interface between the two networks must always be favored to maintain control over this particularly critical interface.
A complete range of products exists, from firewalls to data diodes. A good practice is to assemble several of these solutions within a DMZ, to control the services that can communicate between the two networks.
Nevertheless, IT/OT separation goes far beyond the network issue discussed above. In terms of identity, the separation of the Active Directory (AD) between the management network and the industrial network must also be addressed. From a security perspective, it is best, if the resources are available, to separate these two ADs to avoid the spread of attacks. However, the ADs can also be linked by closely controlling authorized flows and/or providing remediation if one of the two ADs is compromised.
Identify network users
A particularity of identity management in ICS is the strong presence of shared workstations. In this situation, an adapted solution must allow several users to work on the same machine in an authenticated way, thus allowing to identify the actions of each one.
In this case, the model where each user has his own Windows session is not adapted. A possible solution is to set up a generic Windows session on which the user authenticates himself in a simple and fast way thanks to a badge and a Fast Switching software.
What are the next major cybersecurity projects for industrial IS?
SOC
Several Managed Security Services Providers (MSSP) are starting to propose ICS specialized Security Operation Centers (SOC). However, these SOCs should not be considered as miracle solutions: it is above all by knowing your business and all its particularities that the SOC can be effective.
A key aspect when setting up an industrial SOC is to clearly define a scope that is correlated with the cyber maturity of the IS. In an industrial cyber SOC, only cyber incidents should be dealt with, without considering purely operational events, which are already handled by the supervision system.
Third party security
Supply chain management, both in IT and OT, is becoming one of the most important cyber topics. REvil’s attack on Kayesa and its customers in July 2021 gives an idea of the possibilities of a supply chain attack: the attacks reach a new scale and can affect hundreds or even thousands of organizations at once. Obviously, industrial IS also involves third parties and are therefore not immune. For example, the compromise of a PLC vendor could impact numerous customers.
Third party attacks can take different forms, including the following examples:
- Access to the IS by using a software update with a trojan inside
- Theft of data stored by a third party
- Access to the IS via a remote access, for example used by the third party to perform maintenance
Protecting oneself from supply chain attacks is particularly complex. However, tools exist. First, it is essential to know your supply chain and the risk related to each third party. Third parties at risk can then be subject to measures to reduce the chances of compromise such as a Security Assurance Plan (SAP) or regular audits.
Remote access to the IS can be controlled by using Bastions or privileged access management (PAM) solutions, which monitor all actions made by the third party and finely manage their rights. However, this solution can become a constraint for the user, therefore it is advised to focus on the user’s needs to propose the most relevant solutio.
Cloud
Still mainly confined to secondary functions such as inventory and supply management, the cloud is gradually making its way into industrial IS with the development of Industry 4.0. By doing so, it allows, for example, global IoT terminals management in production sites or optimizing server sizing.
But this change also raises security issues. Some of these issues have already been addressed with the democratization of the cloud in management information systems, but others have yet to be resolved. How to manage the security of IoT devices? How can cloud systems be integrated into critical environments, which are highly regulated? Who stores the data and what regulations apply?


