In 2013, the FBI issued a Stored Communications Act warrant for emails stored in Ireland, on one of Microsoft’s datacenters as part of a drug trafficking investigation. Microsoft refused to provide this information, because the data in Ireland is beyond the jurisdiction of the warrant. In Microsoft Corp. v. United States, the court held that “the government cannot compel Internet Service Providers (ISPs) to turn over data stored overseas, even with a warrant”.
To address this issue, the US government decided in 2018 to amend the Stored Communications Act of 1986 by enacting the C.L.O.U.D. Act.
The C.L.O.U.D. Act stands for Clarifying Lawful Overseas Use of Data Act, a federal law to speed access to electronic information held by providers under the US jurisdiction that is critical to US foreign partners’ investigations of serious crimes.

Scope of accessible Data through the C.L.O.U.D act:
- Content of electronic communications in electronic storage
- Content of electronic communications on a remote computing service
- Records relating to an electronic communications service or a remote computing service
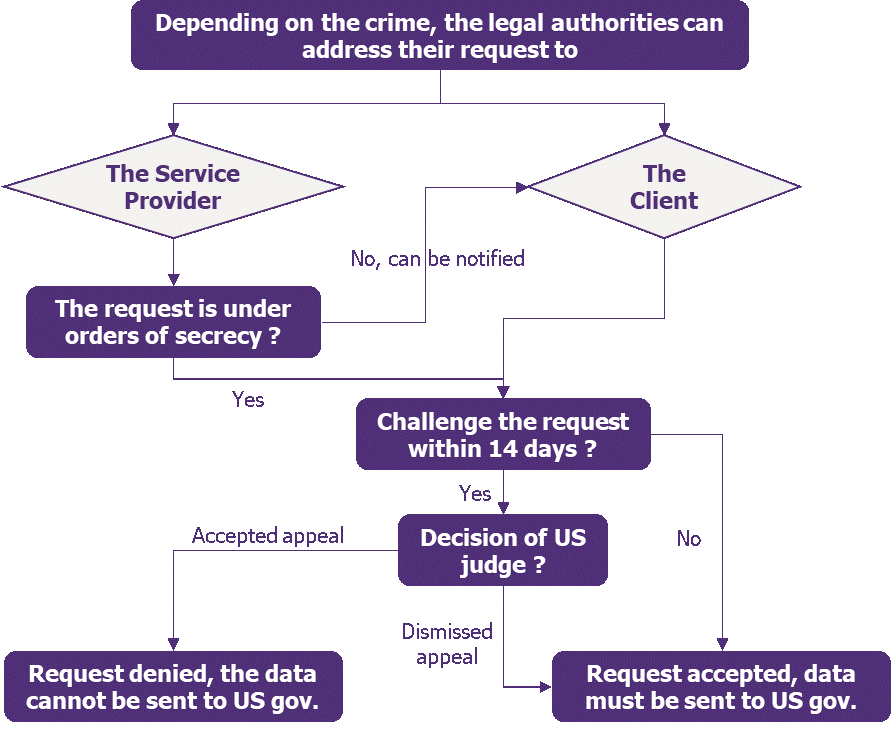
A controlled process for accessing the data.
First, the US authorities invoking this law to request content from all companies under US jurisdiction must obtain a warrant. They must prove a high likelihood of finding evidence, related to the ongoing criminal investigation, in the targeted data, whether the crime is perpetrated by the client or the company itself.
Once the warrant is issued, it must be reviewed and approved by an independent judge.
The request can be issued under orders of secrecy: the legal authorities can delay the CSP (Cloud Solution Provider) from notifying the account holder of the request. Orders of secrecy are examined more carefully by the Department of Justice.
If the warrant is approved and a request is issued, the Service Provider or the client, if notified, can challenge it within 14 days if:
- The data relates to a non-US person who does not reside in the United States, and/or;
- The request would lead to disregard the legislation of a foreign country and would expose it to sanctions.
Factors such as the importance of the information, the specificity of the request or the availability of alternative means to obtain the information will be analysed by the court.
C.L.O.U.D. Act = Cloud provider?
C.L.O.U.D. does not target only Cloud Service Providers! C.L.O.U.D. Act scope is wider than Cloud Providers and include some Software and Providers already deployed in some companies’ IS.

- Remote Computing Services (RCS): any service that provides computer storage and processing services to users through an electronic communication system.
- Electronic Communication Service (ECS): any service that provides its users with the ability to send or receive communications by wire or electronic means.

- US companies
- Foreign companies located outside of the U.S. but providing services in the US with sufficient contacts depending on the nature, quantity, and quality of the company’s contacts with the US (promotion to US customers, solicitation of business to US companies, usage by US clients, etc.
Besides the obvious scope of the RCS and ECS definition (Email providers, cell phone companies, social media platforms, cloud storage services, etc.), many softwares and providers used in most IS are in the C.L.O.U.D. Act scope:
- All Microsoft Office suite (Outlook, Skype).
- Security and network appliances and services (proxies, firewalls, anti-malware, etc.) provided by U.S. companies (e.g., Symantec, Pulse, Citrix, etc.).
- Business softwares that process business workflows to US companies or citizens (e.g.: payment orders).
In On-Premise IS, the C.L.O.U.D Act still apply.
The C.L.O.U.D. Act is wider than common expectations and on-premise implementation can give a false perception of protection. Here are two examples of how the data can be retrieved or transmitted:
1. Built-in technical outgoing flows
Many software communicate by design with the provider’s infrastructure (error and user reports, telemetry data). Most of the outgoing flows are encrypted through HTTPS but providers usually do not communicate on the content of the data sent nor precise the destination and, in most cases, these outgoing flows are required to use the service and cannot be disabled.
![]()
=> The US authorities can retrieve data desired for the Cloud Act such as individual login, client’s workflows, etc.
2. Foreign Third-party support
Support teams are performed remotely allowing access from provider teams all around the world (included US territory).
For numerous softwares, providers bring foreign support team that can be US-based or under US jurisdiction.
=> The provider or the third party must be compelled to transmit the data in case of a request from the U.S.
What do the Cloud Service Providers say about it?
Cloud Service Providers assure their customers that they will not disclose their data unless they are obliged to do so by law… which is the case if they are compelled by the C.L.O.U.D. Act. In the event of a conflict of laws, such as with the GDPR, CSP further assure that they will take the necessary steps to oppose the US government’s request.
Some of them go even further, by assuring that the encryption keys used to secure client data or the ability to force the encryption will not be provided. For now, the C.L.O.U.D. Act does not mention encryption keys nor obliged to provide unencrypted data.
Twice a year, Cloud Service Providers such as Microsoft, Amazon and Google publish the number of law enforcement requests concerning customer data they receive. Those reports compile all the requests issued by law enforcement agencies all over the world. The law enforcement requests issued by the United States of America include C.L.O.U.D act related requests. The distribution of the laws used to issue the requests is not specified, meaning we cannot know which proportion of requests are C.L.O.U.D Act related.
Type of data retrieved
The last Microsoft and Amazon reports, for requests between July and December 2020 in the world can provide more information concerning the type of data requested to Microsoft and Amazon (Google does not provide information concerning the distinction between content and non-content data):
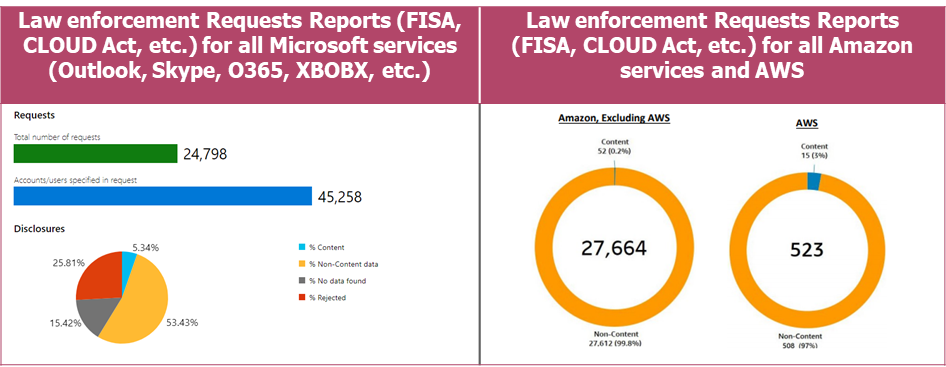
% Content : is what customers create, communicate and store on or through services such as the words in an email or the documents stored on OneDrive
% Non-Content : include basic information such as email address, name, country and IP at time of registration, IP connection history or billing information
% No data found: when the data required by the mandate cannot be found
% Rejected when unable to disclose the requested information (not meeting legal requirements)
=> 40% of requests to Microsoft are unsuccessful: no data is found, or the request is rejected.
=> Most requests to Microsoft and AWS resulting in the disclosure of data are for non-content data (mostly login data).
Closer look
Let us deep dive into Microsoft and Google reports as Amazon does not provide as much detail. The Google services concerned by the requests are Youtube, Gmail, Google Voice and Blogger. The Microsoft services concerned by the requests are Outlook, Skype, O365, Xbox, AZURE, etc.
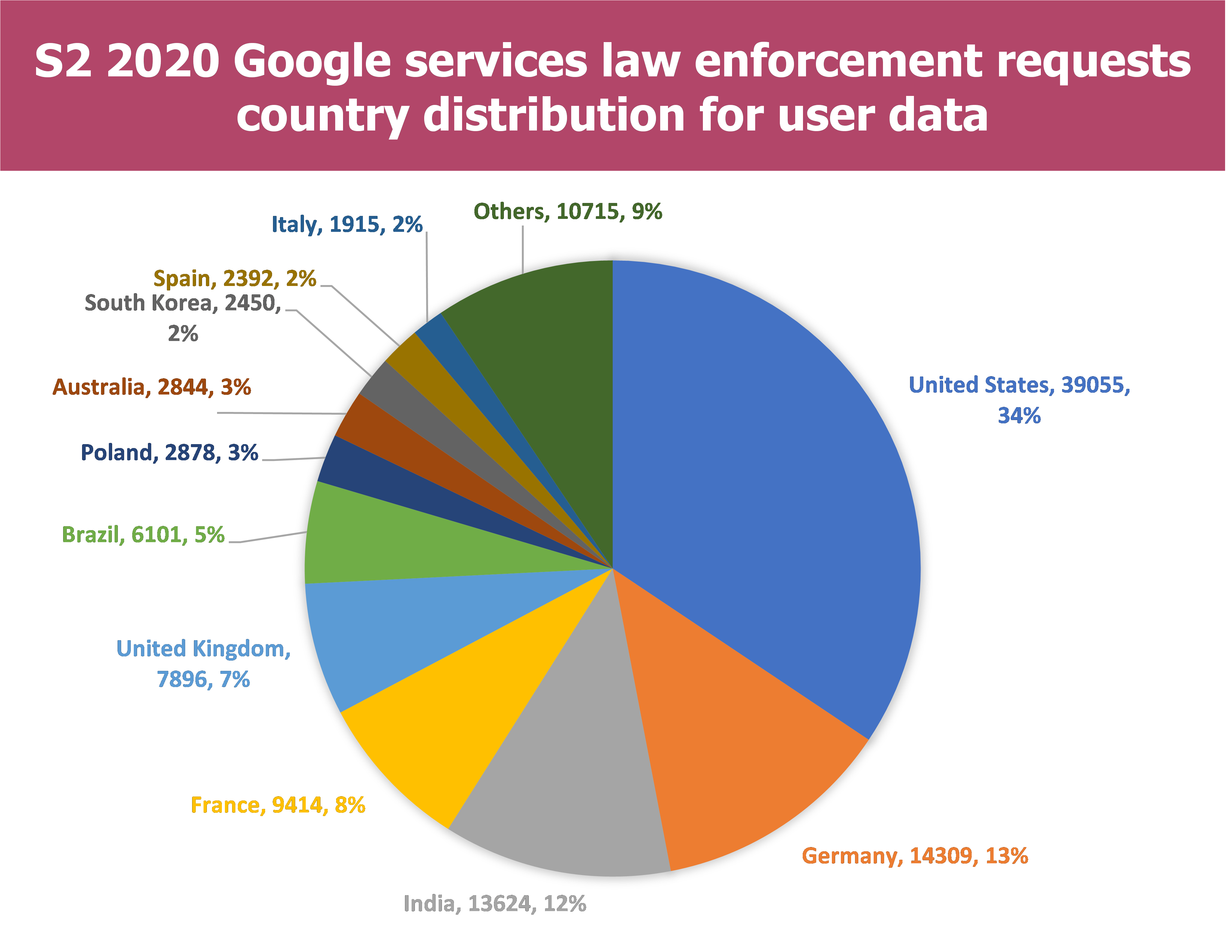
In a geographical point of view, we can identify countries that are the most concerned by those requests for the second semester of 2020 :
Microsoft
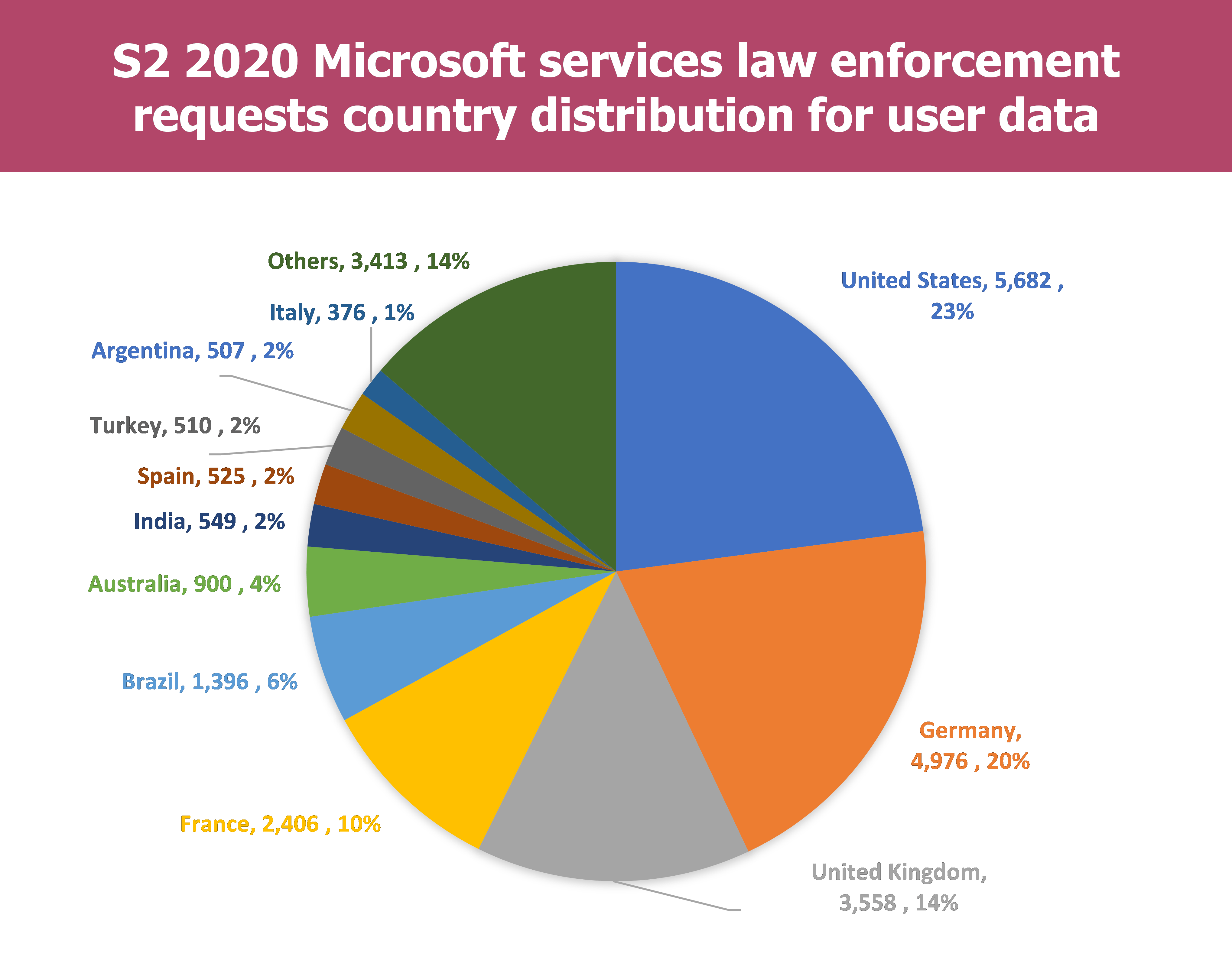
- Only few countries are concerned by most of the requests:
- For Microsoft : 6 countries have been concerned by 900 requests or more in S2 2020 which represent more than 77% of the overall requests
- For Google 11 countries have been concerned by more than 900 requests in S2 2020 which represent more than 90% of the overall requests
- France authorities are at the 4th place of each Provider regarding requests issuance :
- For Microsoft 10% of the requests are issued by the French authorities
- For Google 8% of the requests are issued by the French authorities
Additionally, we can analyse the number of requests which end up in data being disclosed to the authorities and which proportion of the total requests it represents. In the rest of the article, data disclosure means that the authorities have received data following their requests.
Microsoft
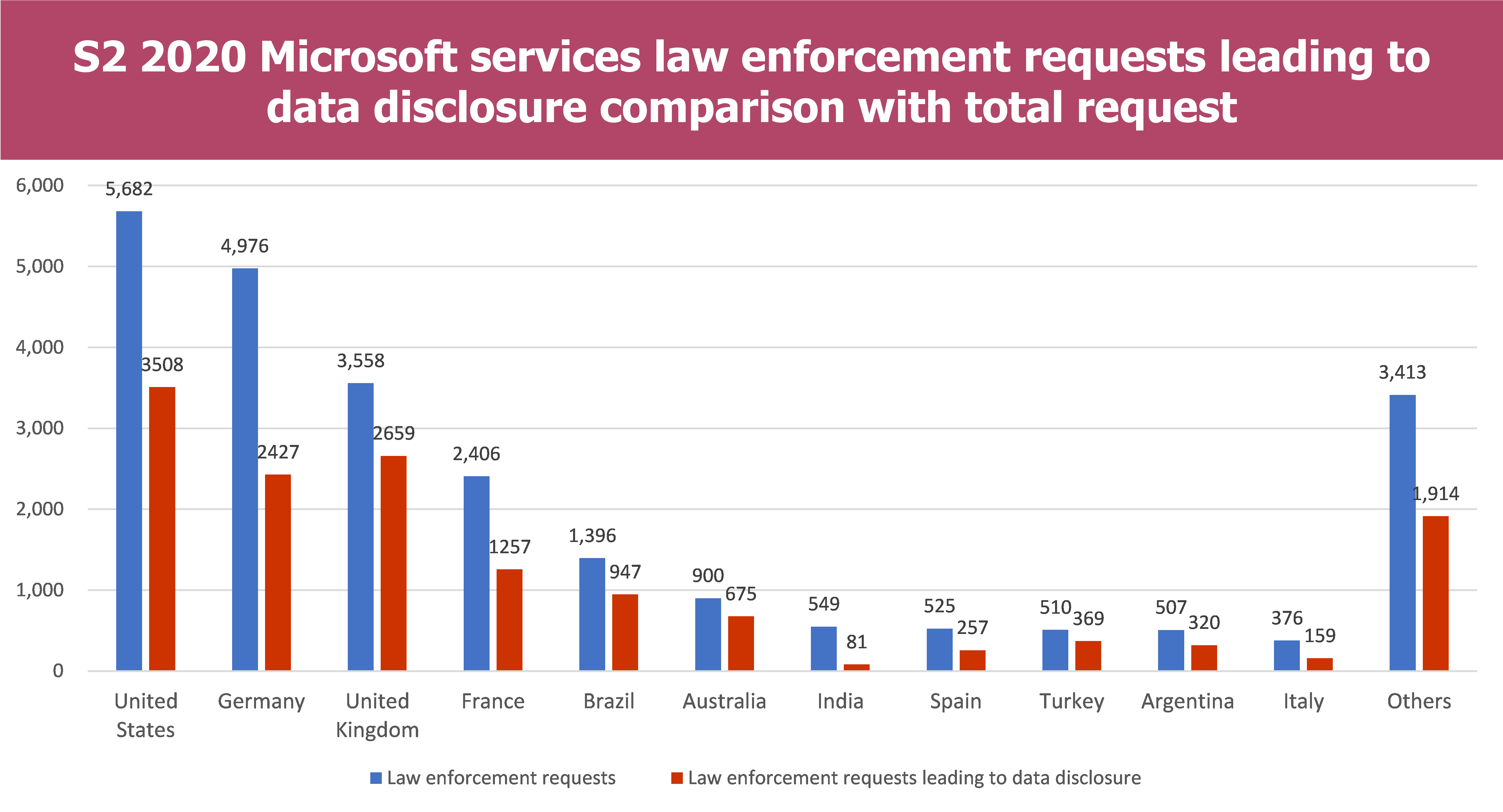
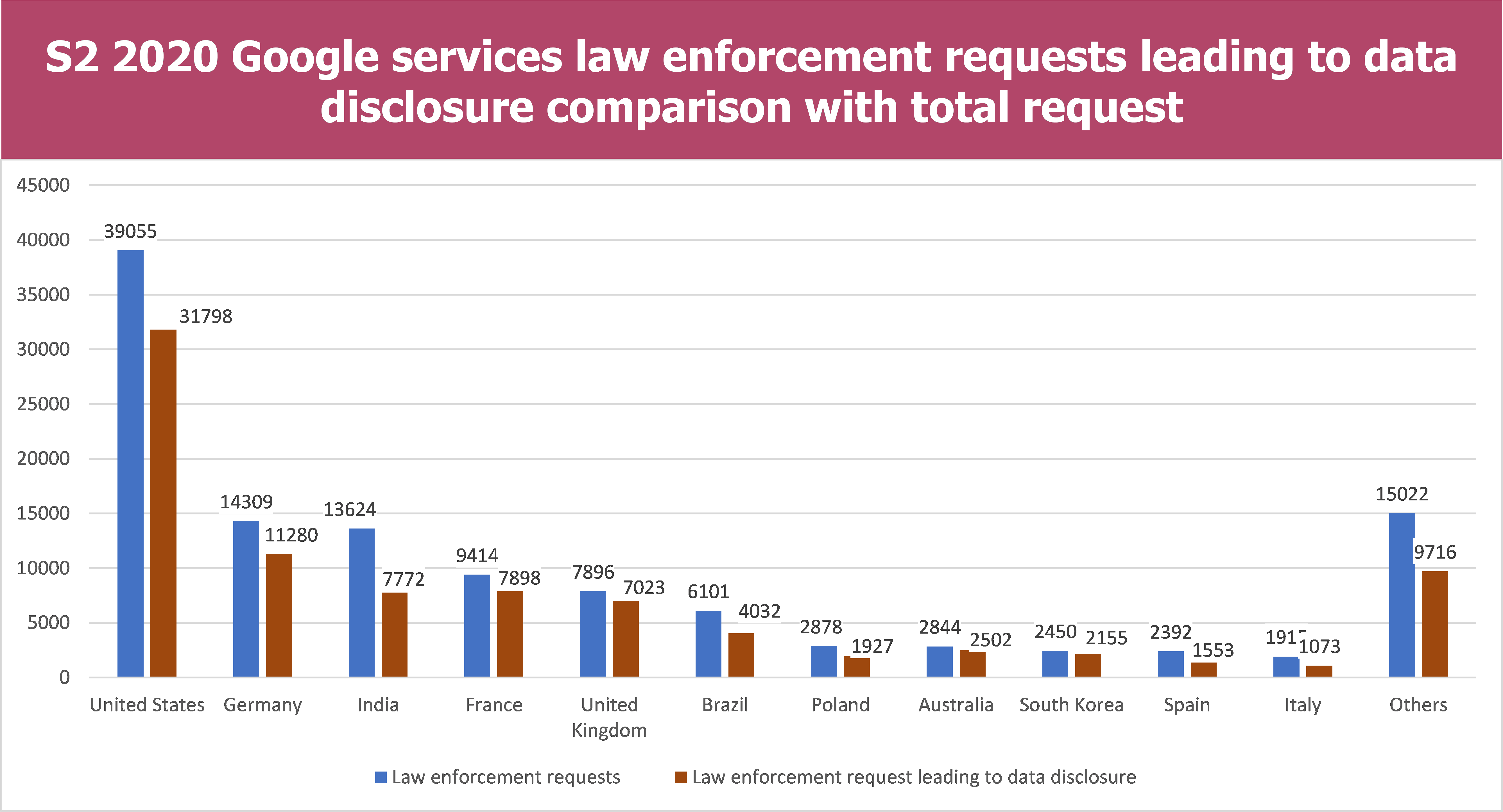
- The percentage of Law enforcement requests which lead to data disclosure is quite similar for Microsoft and Google and contained between 50%-75% (Microsoft) and between 55%-88% (Google)
- However, there are some disparities regarding the Country. For example French authorities have gained access to data in 52% of their requests for Microsoft whereas they have gained access to data in 83% of their requests for Google
Seeing the raw data, one can at first sight conclude that data disclosure to authorities is more likely for Google service than Microsoft ones. It can be explained by the fact that Google services are aimed more towards individuals than businesses and Google services are more widely used (Outlook 400 million users versus Gmail 1,5 billion users). Additionally, the law enforcement requests are issued in criminal cases which are more likely to concern individuals meaning those requests are more likely to be send to Google.
Step back – How the law enforcement requests have evolved since 2013 for Google and Microsoft?
If we compile reports since 2013, we can identify trends regarding data disclosure following C.LO.U.D Act implementation.
Microsoft
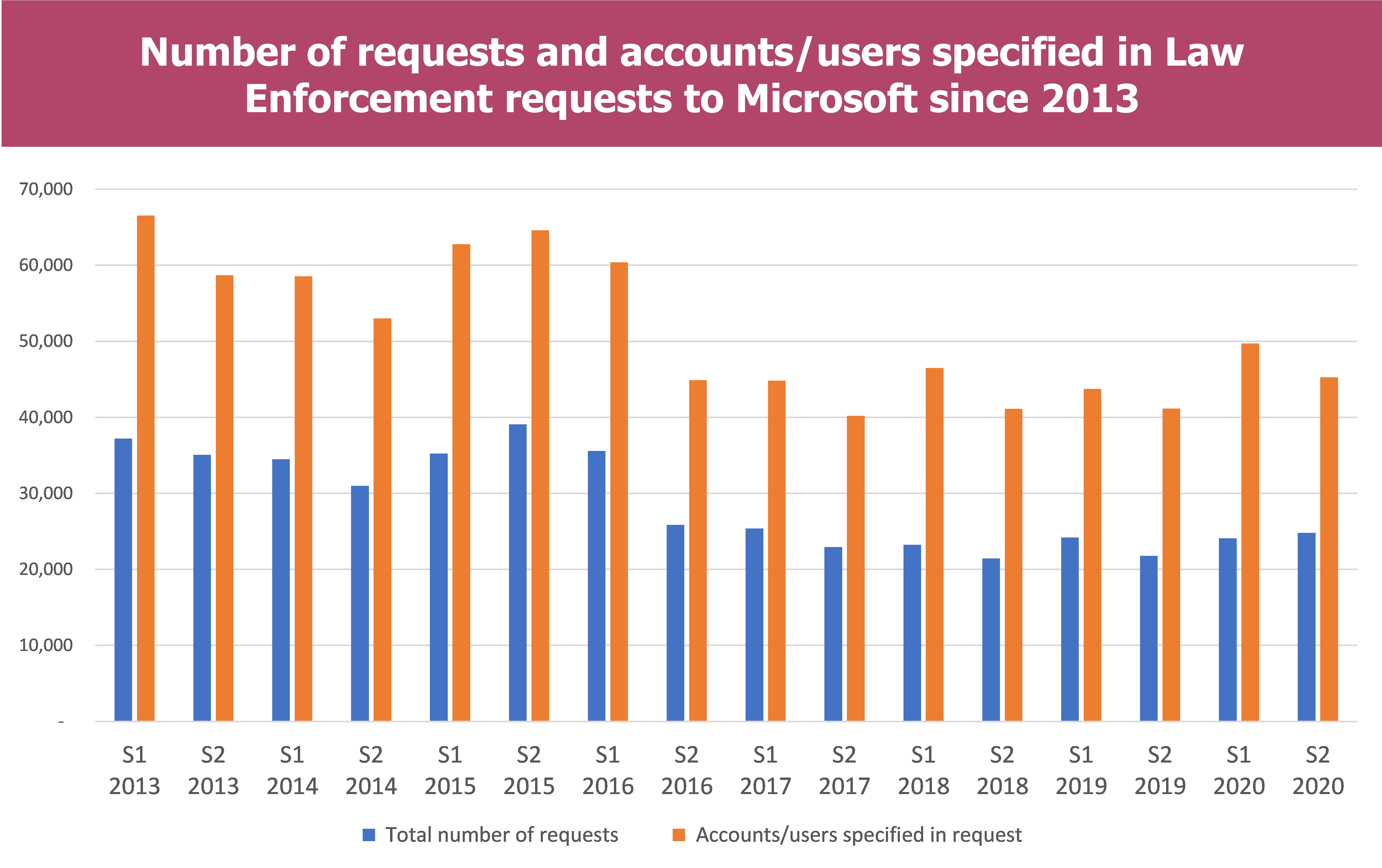
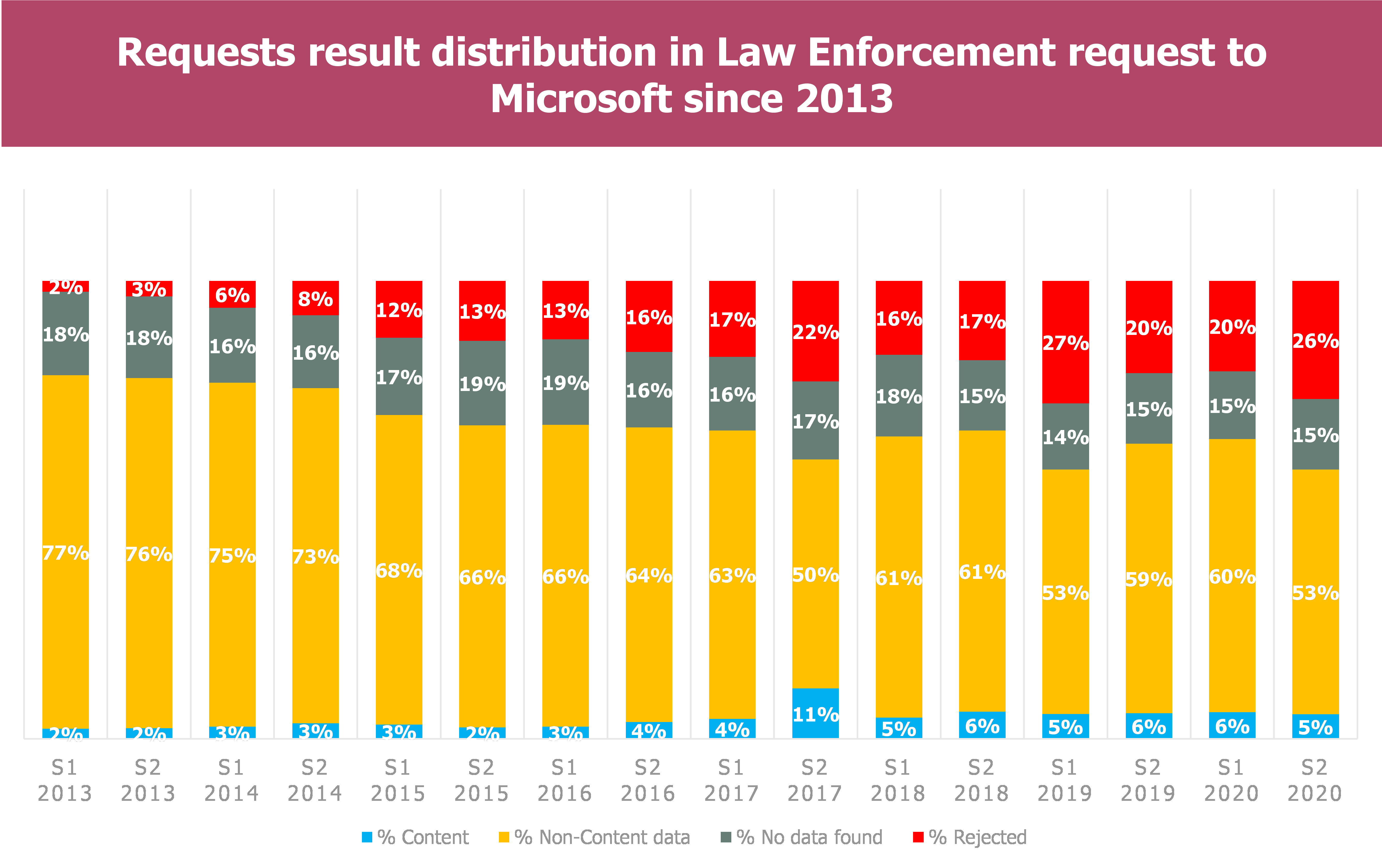
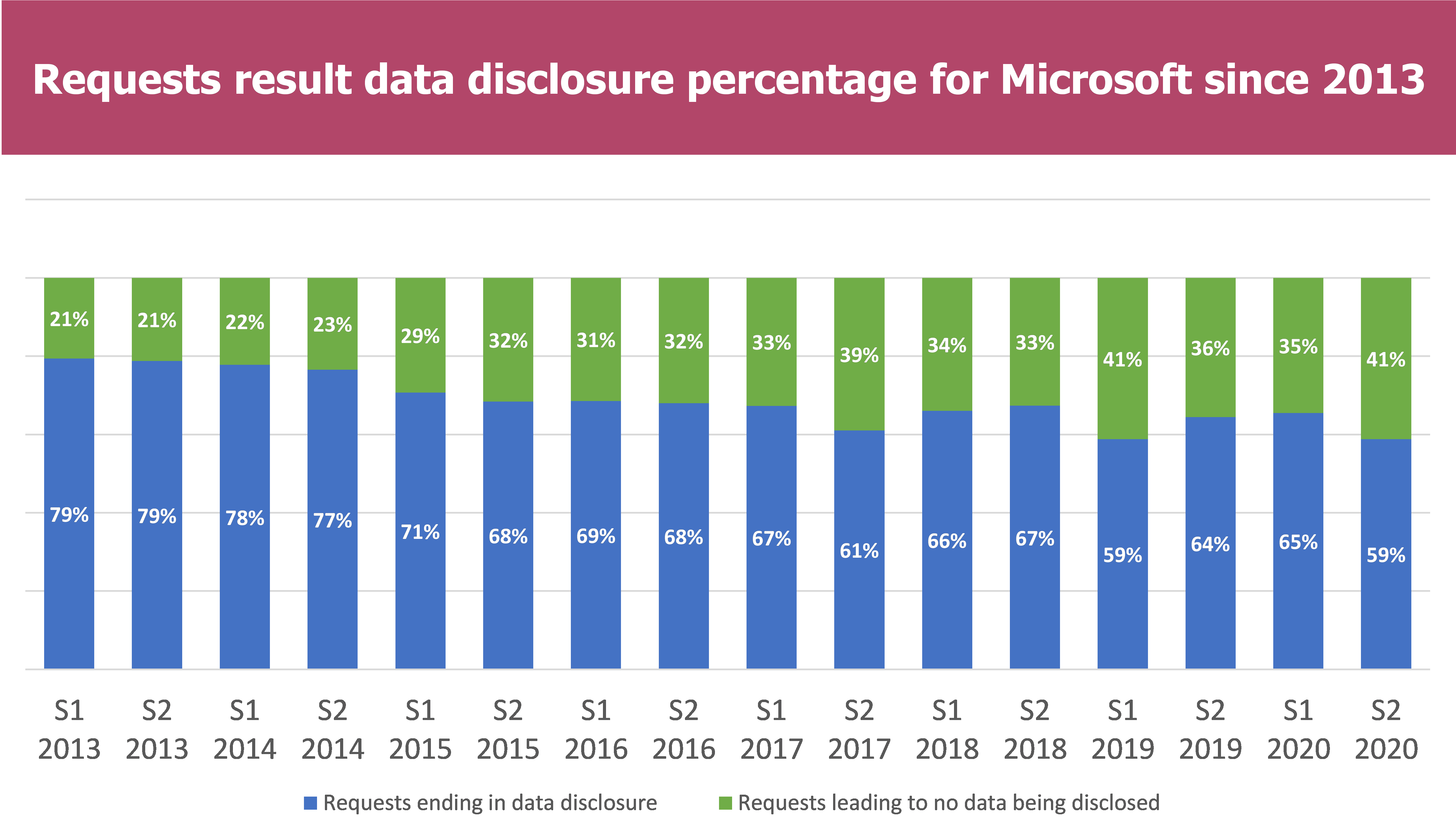
It is worth noting that in the Microsoft report, the requests which are rejected and requests approved but in which no data is discovered are classified in the category “Data request leading to no data being disclosed”
- The total number of requests seems to stabilise around 20K-25K each semester since S2 2016, the same for the account/users concerned, around 40K-50K.
- Distribution tends to evolve, notabily regarding rejected requests :
- A small part concerns Content data, generally aound 5% of the requests
- More than half are requests for non-content data
- An approxymately equal share of 15% each semester are requests for which data have not been found
- Rejected requests have been growing since 2013 to reach almost a quarter of the request results
- In total more than 40% of the requests lead to no data being disclosed to the authorities
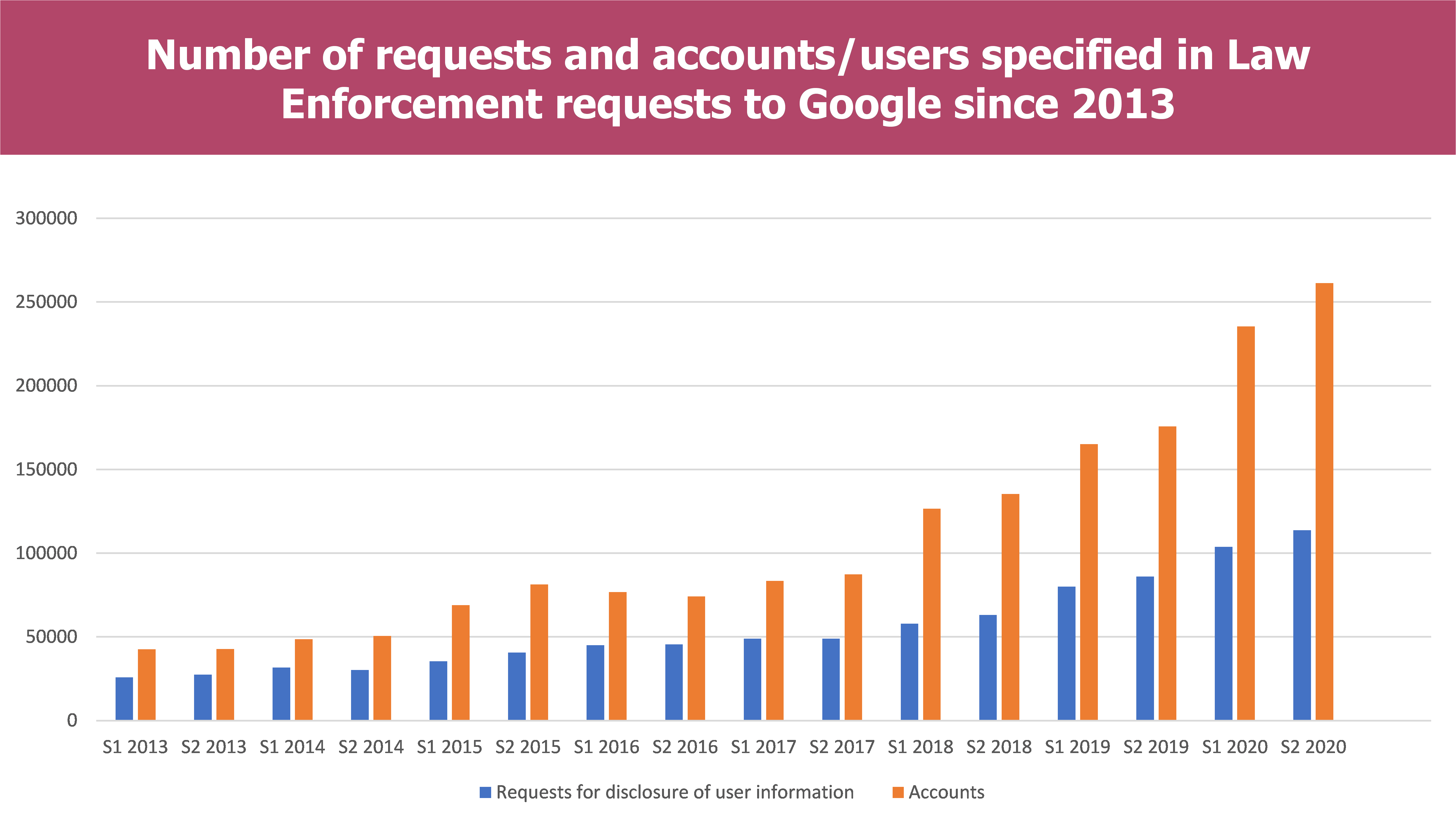
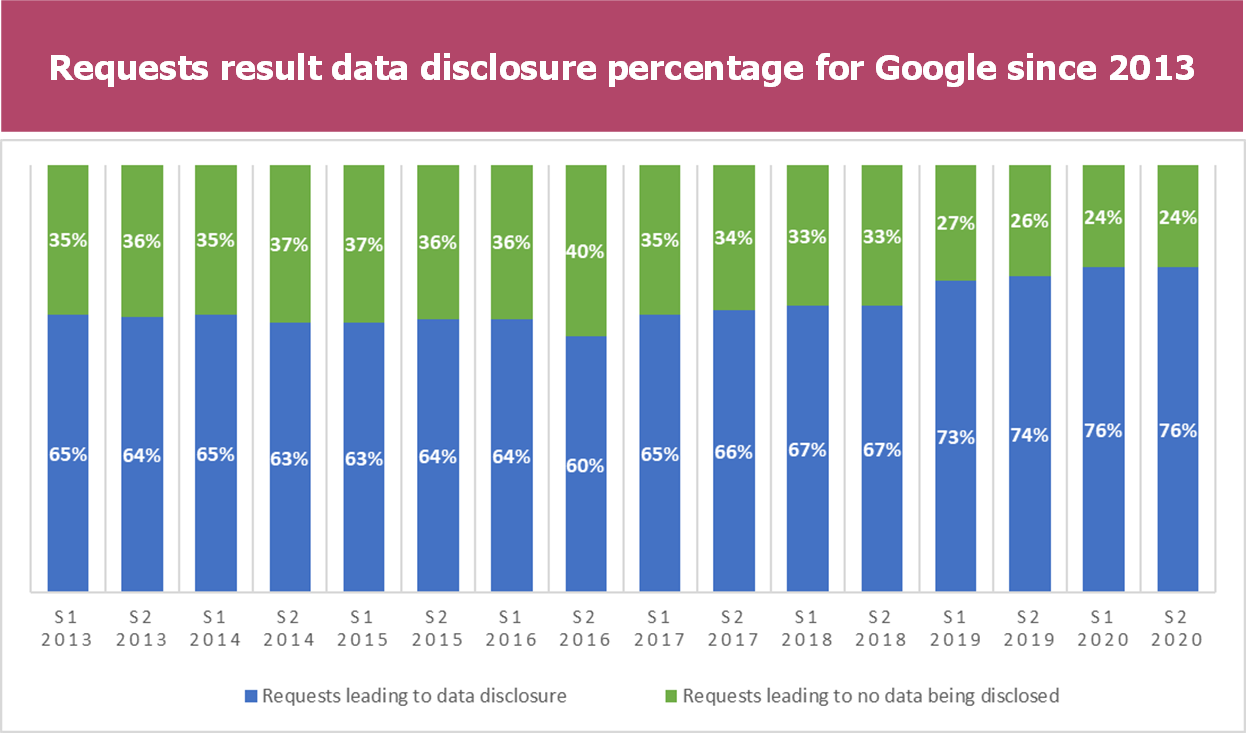
- The total number of requests has been exponentially growing since 2018 to reach more than a 100k requests for the first semester. This can be explained by the increased number of countries which are included in the google reports (68 in 2013 versus 85 in 2020), the omipresence of Google services in any indivuals’ connected life as well as the release of the C.L.O.U.D Act in 2018.
- The evolution of requests tends towards the increase in data disclosure starting in 2018 and the release of the C.L.O.U.D Act. However, since the beginning of the reports publication in 2013, the percentage of the data disclosure has always been between three and four fifth.
Conclusion
After analysis of the bigger picture, all CSPs are not in the same situation:
- Amazon does not provide any detailed information regarding data disclosed location or percentage of data disclosed on overall requests
- Google receives more law enforcement requests than Microsoft and discloses more often information than Microsoft that can be explained by the fact that Google services are aimed more towards individuals than businesses
Nevertheless, the decision to disclose the information is in the hands of the legal institutions and not the CSPs’ (even if it can contest the request). Therefore, the CSPs’ cannot be held responsible for the amount of data they disclose to the authorities through legal means.
Additionally, even if law enforcement requests are over thousands every semester and tens of thousands of users, this remain a tiny part of the total amount data treated by main Cloud Providers. The data access procedure remains exceptional. The requests mainly concern logins and metadata, there is no proven case of industrialized espionage with mass data recovery.
Finally, keep in mind that these statistics cannot be challenged or aggregated with other sources. It is necessary to underline that this is only at the goodwill of the Cloud Service Providers to disclose the data and the reports, so it should be taken with a grain of salt.
At least, the notion of trusted Cloud remains key for every Companies, Cloud Providers as well as authorities tend to get more involved into the subject as evidenced by the Thales and Google new partnership to build a sovereign Cloud Offer or the planned evolution of ANSSI’s SecNumCloud qualification.


