DECRYPTION
THE RISE OF INITIAL ACCESS BROKERS
As seen in the underground economy edition, the cybercriminal economy relies on the professionalization and specialization of its system. Among the main actors of this ecosystem, such as the Bullet Proof Hoster or the RaaS, the Initial Access Brokers (IAB) have become more and more crucial these last years.
What is the IAB’s role in the underground economy?
They are providers of victims’ access. They scan the web for vulnerabilities, send phishing e-mails or try to use brute force to get hold of the passwords of company employees, or even create persistent access in the victim’s network. Those ready-made ‘access’ are sold on the dark market: depending on its level of quality, prices can range from $1K to $100K. The average selling price of initial access to a network is $7,100. Price is based on the organization’s revenue, type of access sold, and number of devices accessible. For example, Access to an Australian company with 500 million USD in revenue that enables an attacker with “admin” level of privileges has been offered for 12 BTC, and access to a Mexican government body for 100,000 USD.
The market of corporate initial access grew by almost 16% in H2 2020–H1 2021, from $6,189,388 to $7,165,387. The number of offers to sell access to companies almost tripled over the review period: from 362 to 1,099. The geography of initial access brokers’ operations has also expanded: if the US-based companies are the most popular victims (30% in 2021), the European companies access sold was multiplied by three between 2019 and 2021. French companies were the most popular lot for sellers of access to compromised networks – they accounted for 20% of all victim companies in 2021 in Europe, followed by the UK (18%).
Finding and selecting access opportunities represent an essential but very time-consuming piece of the current “ransomware business model”. By monetizing this activity, the IABs are offering a huge advantage of time and energy for the buyers, who can select from a menu of options, picking victims based on their revenue, country, and sector, as well as the type of remote access being offered.
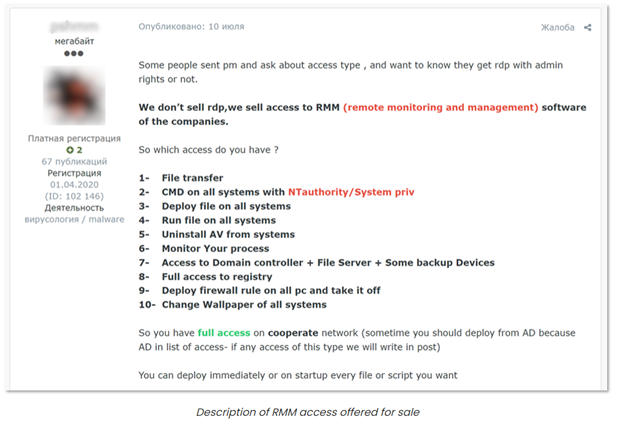
What kind of access are we talking about?
One of the main trends of the IAB market is the diversification of access Grows. If RDP and VPN are still the most common offer, new attack vectors such as access to VMWare’s ESXi servers have become quite popular.
According to several types of research, the kind of access mostly sold are
- Active Directory credentials: domain administrator access is one of the most valuable access since it allows the attacker to distribute malware all over the network immediately.
- Initial Network Access (RDP, VPN, SSH): : is one the most common access sold since it is a very popular protocol among remote workers to access their corporate resources. One of the methods used by the IAB is to launch massive scans for RDP servers all around the internet and try to brute force it.
- Web shell access: some IABs set up web shells on compromised web servers and sell access to it.
- Admin account on CMS (WordPress, PHP): they provide access to web hosting content (including payment solutions and credit card details)
- Admin account on virtualization machines and root access on Linux servers: the sale of root access to VMware ESXi increased significantly and some attacker’s group contains code that specifically targets those systems.
- Remote Monitoring and Management access: offer elevated permissions into several machines of the network, making it interesting data for IABs to sell.
According to the IAB, the services can include more stolen data, such as information on the financial health of the targeted victim, to help the attacker set the highest realistic price for the ransom.
What does that mean for me?
The rise of the IABs activity is, among other things, a direct consequence of the mass shift to remote work and an increase of exposed remote services, (RDP, SSH…) and of the adoption of cloud applications increase. As seen; the main kinds of access sold relies on several vulnerabilities that can be corrected with standard cybersecurity measures: utilize strong passwords, enable 2FA when possible, admins and user awareness, frequent account review…
Besides, the IABs have become a keystone of the current cybercriminal system. Which means they are an interesting indicator to look at to monitor the criminal activity and the risk to become a target. Especially in the case of a mature actor, setting up monitoring programs across surface-, deep-, and dark-web forums and marketplaces, to detect IABs offering can provide relevant information to prioritize defense actions and prepare against potential attacks.
CERT-W: FROM THE FRONT LINE
The First Responder Word

READING OF THE MONTH
We recommend the Cisco Almanac for 2022:
“2022 Cybersecurity Almanac: 100 Facts, Figures, Predictions and Statistics”

UPDATE ON THE UK NATIONAL CYBER STRATEGY
The UK’s National Cyber Strategy transmits a more ‘proactive’ stance to cyber power with a commitment to a ‘whole of society’ approach. The new strategy is supported by £2.6 billion investment seeing a 26.9% percent increase in comparison to previous strategy.
It is structured in five pillars: UK Cyber Ecosystem, Cyber Resilience, Technology advantage, Global leadership and finally Countering threats with 53 action plans. The plans aim to improve intel sharing platforms to truly ‘defend as one’ with a new Govt Cyber Coordination Centre (GCCC). Supporting industrial partners and strengthening business regulations through govt levers and enhance the nation’s cyber structure and skills.
Access the summary from the UK office here!
SEE YOU NEXT MONTH!!



