We recently learned from AdvIntel researcher Yelisey Boguslavskiy that the Russian group Conti shut down its operation, thereby making the brand obsolete.[1] This announcement comes only a few months after it was the center of attention of the specialized press following the “Conti Leaks“.
Last February, a Ukrainian researcher released more than 60,000 messages from inside conversations between different members of the group. Through these discussions, several revelations are made about their operations, allowing us to understand the RaaS ecosystem (Ransomware-as-a-Service).
Through this article, let’s take a look at how a Ransomware platform operates, then let’s question the organizational structure and the benefits generated by former CONTI group.
Ransomware platform ecosystem
The proliferation of articles on the Ransomware threat over the last few years gives the impression that the sector is flourishing. There are several players involved, and data theft amounts to hundreds of millions of dollars per year. For instance, CERT-Wavestone shared that about 60% of its incident responses in 2021 were for ransomware attacks.[2]
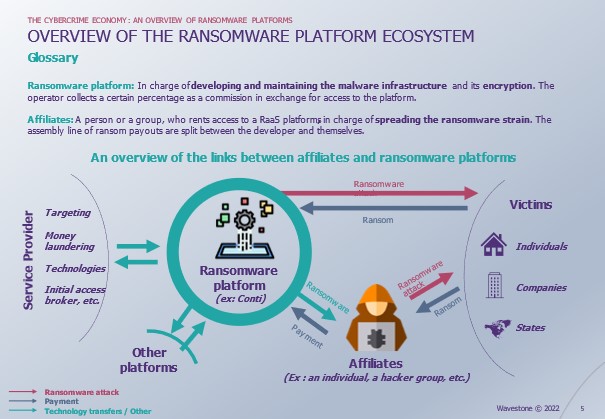
As described in the figure, ransomware platforms do not work alone. It receives help from different service providers or other platforms and offers its services (in the form of ransomware) to different groups of attackers. Finally, the platform can also directly extract data from its victims: individuals, companies, states…
These platforms have fueled the growth of a RaaS economy. Approximately $5.2 billion of BTC transactions have been identified by the US Treasury with the payment of the most commonly reported ransomware platforms.[3] This makes it a highly profitable business.
At the same time, it is also an activity where there is a significant number of established groups of players that seem to frequently appear and disappear and which generally last several months. Behind these multiple platforms usually hide the same individuals. If the CONTI franchise, supposed successor of the Ryuk[4],has only survived 2 years, its former members still seem to be active.
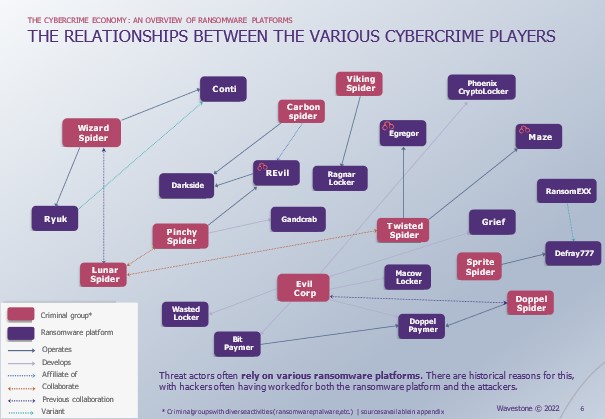
In this fragmented and complex environment, it is difficult to retrieve consistent information on the functioning of the platforms. The internal discord that followed the war in Ukraine and the publication of the Conti Leaks allowed us to investigate the functioning of this secretive group before its dissolution.
Conti enterprise ?
On February 27th, 2022 we discover the underside of CONTI organization. The disclosures are made within a few days and soon reveal :
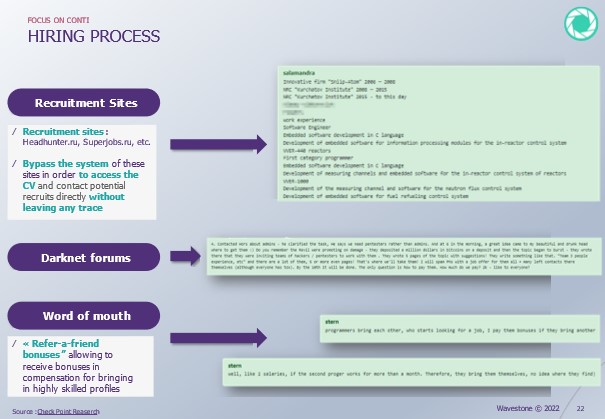
- Well-established recruitment processes, that can even go as far as advertising on legitimate recruitment sites
- A vertical organization with its own HR, financial and operational departments
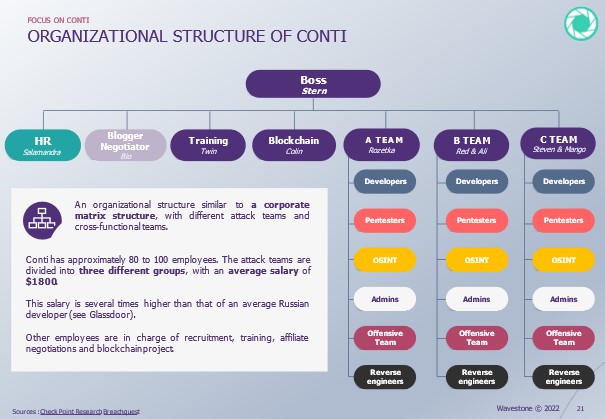
- A salary policy established according to the different functions in the organization, including bonuses per position after a successful ransom (See. Full study)
This thoughtful and efficient organization seems to be one of the secrets to the profitability of the group.
A highly profitable business model
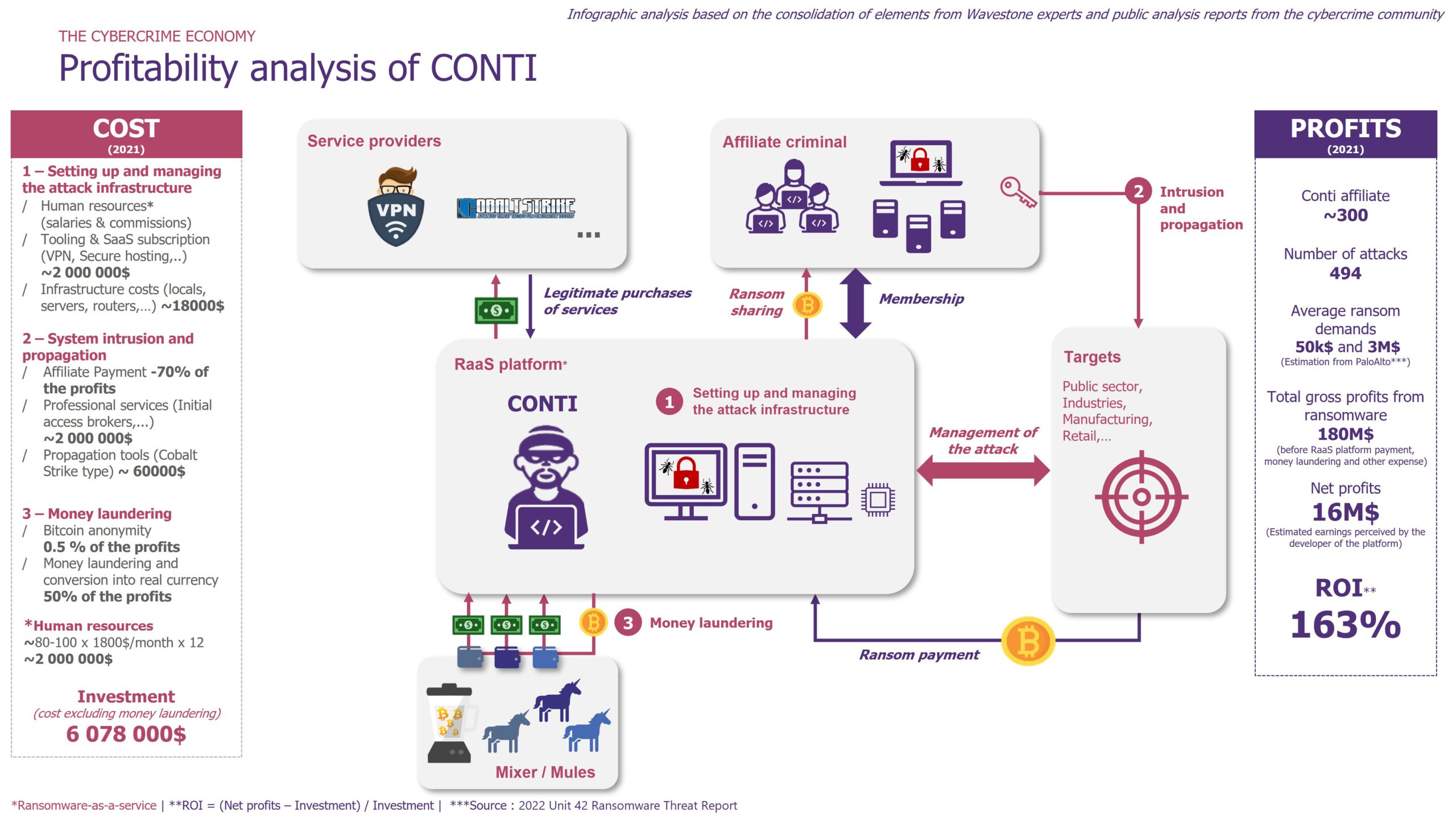
We have endeavored to recreate the cash flow statement of CONTI from scratch.
Each line of profit and cost is researched to be estimated as accurately as possible over a year.
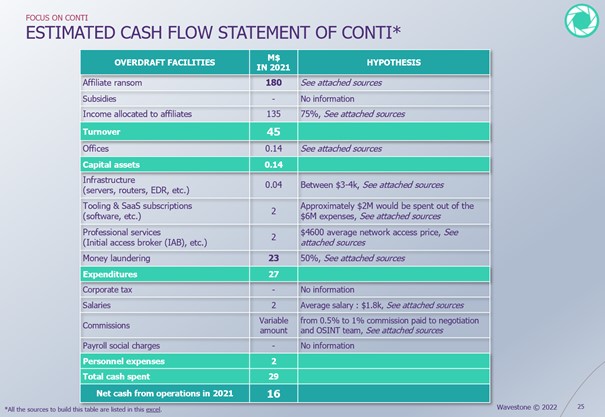
According to The 2022 Crypto Crime Report[5], in 2021, CONTI and its affiliates held at least $180M in bitcoins for ransom from addresses traceable on the blockchain. It is estimated that 70% is paid back to its affiliates, and the remaining $45M is the group’s revenue.
CONTI then has to deal with traditional expenses, which are common in traditional companies. The main ones are: money laundering, which represents up to 50% of the earnings, purchases of third party services and maintenance costs, and finally.
CONTI would therefore generate a net profit of $16M (if we assume that the group does not pay Russian taxes). The ROI of the group is estimated at about +163%, according to the same information.
Conclusion
The Conti Leaks enabled to better understand the organization and ecosystem of Ransomware-as-a-Service platforms through the study of a group. This work thus provides a solid foundation for the popularization of the RaaS threat.
About our method
All of the information presented in this study comes from Wavestone’s field observations as well as multiple sources – both public and private such as: the National Cyber Security Center, Check Point Research, Palo Alto Networks, Breachquest and Chainalysis.
Sources :
[1] « Conti ransomware shuts down operation, rebrands into smaller units », Bleeping Computer, May 2022
Conti ransomware shuts down operation, rebrands into smaller units (bleepingcomputer.com)
[2] « Cyberattacks in 2021: ransomwares, still threat n°1 », Risk Insight, October 2021
https://www.riskinsight-wavestone.com/2021/10/cyberattaques-en-france-le-ransomware-menace-numero-1/
[3] « US links $5.2 billion worth of Bitcoin transactions to ransomware », Bleeping Computer, October 2021
[4] « Le rançongiciel Ryuk », ANSSI, September 2021
CERTFR-2020-CTI-011.pdf (ssi.gouv.fr)
[5] « THE 2022 CRYPTO CRIME REPORT », Chainalysis, Février 2022


