The encryption of data in transit and at rest now makes it possible to ensure a good level of security. For data being processed, a solution is now emerging confidential computing.
I had the opportunity to organize a round table on confidential computing for the Assises de la Sécurité de 2022, moderated by Thierry AUGER, CISO & Corporate CIO of Lagardère, and including Mathieu Jeandron of AWS, Thiébaut Meyer of Google Cloud, Arnaud Jumelet of Microsoft France and Julien Levrard of OVHCloud. This article intends to summarize the exchanged elements by discussing use cases, the technology, and the initial steps to be taken.
Purposes of Confidential Computing
The principle of confidential computing is to create an enclave that ensures that only the processes running within the enclave has access to clear text data. Before going into more detail about how the technology works, we’ll look at how it can be used to improve cybersecurity.
Multi-party Confidential Data Analytics
Several parties want to share data in such a way that none of the external parties will be able to access thier data. This requirement will be met by putting in place a confidential computing enclave. Only the cellar will be able to see the information of what each party shares.
Example: Several banks wish to collaborate on the development of a fraud detection algorithm. However, none of the banks wants their customer information to be used for this analysis in the fear of data getting exposed to other parties.
Federated AI Learning
Several parties want to pool their data to train an artificial intelligence algorithm. The data must not be disclosed to or known by another actor. The confidential computing enclave will guarantee that only the artificial intelligence algorithm has access to the data.
For example, several hospitals want to train an AI model to upgrade their medical diagnosis on a larger scale. Medical secrecy also requires, under no circumstances another actor will have access to their patient’s data.
Protection of Calculations in Edge Computing
Edge computing cannot guarantee the same level of physical security for processing as the data center. However, it is desired that the embedded code and processed data remain inaccessible and unmodifiable. The confidential computing enclave will be able to provide the aforementioned guarantee.
Example: An IoT solution provider wants to ensure that the code embedded in its objects cannot be accessed, guaranteeing its intellectual property.
Finally, the most frequently cited use case is the protection from its infrastructure provider.
Here, it’s important to make sure that the administrators of the infrastructure on which I’m going to carry out my processing cannot access my data. Satya Nadella, CEO of Microsoft, stated at the Microsoft Build in May 2022 that he considers confidential computing to be a game-changer.
For example, a cloud service provider should not have access to the data processed on its infrastructure. Today, confidential computing provides a hardware-based guarantee in addition to the existing logical isolation mechanisms and implemented security measures. This can restrict the administrators’ actions. In the event of a vulnerability on the latter, the enclave also provides enhanced security against malicious access by a different virtual machine running on the same hypervisor.
The promises seem interesting, but how does confidential computing work?
Confidential computing aims to perform the processing in an enclave accessible only to the processor; this property is materially guaranteed by the processor and its firmware (*). A secure channel is established between the enclave and the processor, preventing any intermediate components (Hypervisor, OS, etc.) from accessing the data.
(*) The technical implementation of the enclave differs based on the processor founders (Intel, AMD, ARM, IBM, etc.). Let’s not elaborate on it in this article.
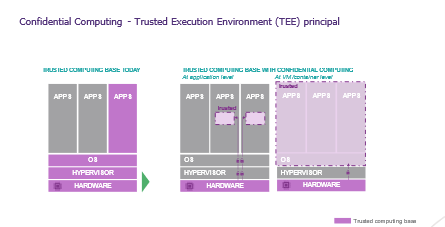
There are two primary forms of an enclave:
- Enclave at the machine or container level: all processing performed within the virtual machine or container is protected.
- Application-level enclave: the enclave will protect only a portion of the application (for example, the code performing sensitive processing: raw data is never accessible, only the results are)
During the round table, Arnaud Jumelet presented an analogy with a building:
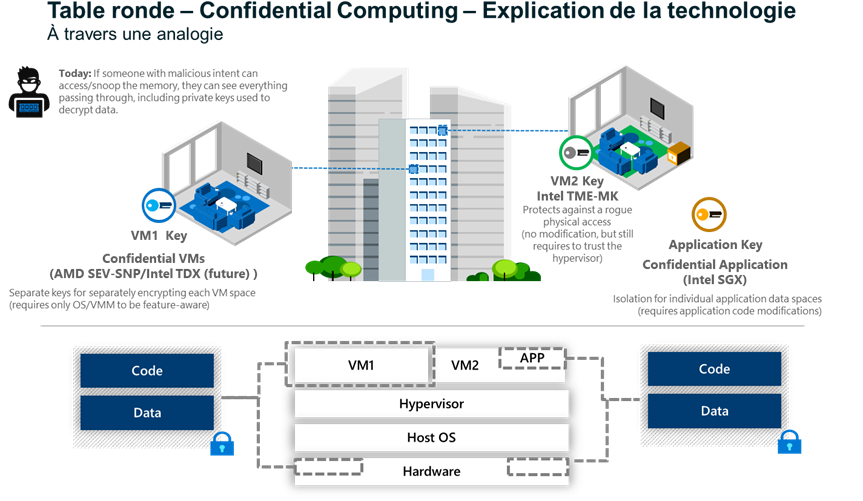
An enclave at the level of a VM or container can be compared to the protection that an apartment would provide in relation to the rest of the entire building: only those with the keys can enter.
In the case of an enclave at the application or code level, it can be compared to a safe within the apartment that protects the processing.
In the first case, the building manager (i.e., the IS infrastructure management) has no view of what is going on in the flat, whereas in the latter case, not even those with access to the apartment (i.e., the VM administrator) can see what is happening in the safe.
It all sounds magical; does it cover all my risks?
Confidential computing is a new toolbox for reducing risks. Mathieu Jeandron warns that it should not be used in opposition to existing measures; it is a matter of adding a hardware-based guarantee to the logical isolation offered by virtualization.
Like any tool, it can have its own security flaws, such as side-channel attacks (like the SQUIP vulnerability) or attacks affecting other functions of the processors (such as attack on the server). However, these attacks require a high level of expertise. During the round table, Thiébaut Meyer stated that disabling hyperthreading can reduce the risks associated with these vulnerabilities. It is also crucial that the enclave, upon startup, verifies that it is running in a trusted space like process challenge, processor firmware version verification, etc.
Mathieu Jeandron mentioned that completely understanding confidential computing will not address all his risks, with respect to the following:
- In the context of a VM-level enclave, the VM administrator will always have access
- Vulnerability in the code running in an enclave could still be exploited by an attacker to access the data
- Compromise of the supply chain producing the processors is always a possibility…
Implementing an enclave can blind certain external cybersecurity detection mechanisms; beware that what is on one side could be lost on the other!
To make a well-thought-out plan for using the technology, it is important to understand both the technology and the associated risks.
Data protection is a matter of key management
Encryption is never far away when it comes to data protection. Moreover, encryption requires key generation and storage tools. Julien Levrard reminded us that the protection provided by the enclave is only one part of the problem, whereas it must be seen holistically!
Specifically, both the data to be processed and the code running in the enclave originate from outside the enclave. The data must therefore be encrypted, and only the enclave must have access to decrypt the data. Therefore, the keys must be sequestered in an HSM or KMS, which must verify that the correct enclave is requesting access prior to releasing the keys. The customer will have the option of utilizing the services of the supplier or implementing BYOK or HYOK.
I see an opportunity, but isn’t it too complicated to go there?
The Confidential Computing Consortium, which aims to promote the technology, provides accelerators to facilitate this adoption. For example, Arnaud Jumelet mentioning about the open-source project OpenEnclave or Enarx. There are also services that offer player-building solutions, such as Securitee, Cosmian or Decentriq. Furthermore, many software players have also incorporated the integration of confidential computing functionalities to their roadmaps; in the future, this may be the default operation!
The majority of confidential computing initiatives in France are currently in the Proof of Concept (POC) stage. However, some use cases are already in production; the SIGNAL messaging system uses confidential computing to protect messages, for instance. Thiébaut Meyer even indicated that the first ransomware used this technology to evade detection!
Julien Levrard explained that the technical requirements for testing are straightforward: simply order a server of the latest generation and activate the function in the firmware or subscribe to cloud resources that are compatible. In an enclave, one can then easily deploy an OS or container with the appropriate drivers. For the business use cases described at the beginning of this article, however, the application code must be redesigned.
Confidential Computing- A Maturing Technology
Confidential computing has matured to the point where an expert assembler is no longer required to use it. This is probably the right time for companies with use cases to test this technology to better understand it before deciding on its use in the production. Moreover, it makes sense to incorporate this into a security roadmap.


