Once again, the CERT-W 2022 report confirms that the main motivation of attackers continues to be financial gain and ransomware remains the most common means of extortion. Ransomware attacks are among the most severe cyberattacks in terms of their impact on the continuity of IT services and, by extension, the business operations itself.
Wavestone assists many victims in managing their crisis triggered by ransomware attacks. Often, poorly trained IT and management teams make incorrect decisions in response to these unexpected situations.
This list of the top ten pitfalls to avoid in ransomware crisis management is based on the feedback from over 5 years of supporting victims.
#1 Paying the ransom will speed up your back up process
Although the French National Agency for the Security of Information Systems (ANSSI) recommends never paying a ransom, this question will always arise for certain stakeholders, especially the decision-makers, who are not completely aware of these issues. Beyond the fact that paying the ransom encourages attackers to continue their activities, it should also be noted that paying the ransom does not always lead to the recovery of the decryption key.
In cases where a ransom payment allows the decryption key to be obtained, the decryption time is often very lengthy. It can take several hours or even dozens of hours per server or workstation, depending on the size of the encrypted files. When there are large numbers of computers, strict coordination is necessary for processing all the systems. In comparison, it will be faster to restore systems from backups.
In addition to the time required, the encrypting or decrypting process is rife with errors, according to past experience. Thus, even with the decryption key, certain files, particularly the largest ones, are sometimes modified and cannot be restored as they are.
In short, we are far from the widely held notion that a simple click can restore a functional information system after ransom payment. There is no point in considering a ransom payment to restart services if there are healthy and functional backups. In the case of data theft, the issue gets more complex.
#2 Reopening the information system too quickly
To limit operating losses due to inactivity, the crisis unit is often urged by the business to restart the information system as quickly as possible. During the reconstruction phase following a cyber-attack, it is necessary to control the following two main risks:
- Resumption of the attacker’s attack and re-encryption of the reconstructed systems
- Theft of new information by the attacker who restarts the data exfiltration
Isolating the information system from the outside world is the initial security measure that must be implemented to reduce these risks significantly (internet access in and out, links with partners, etc.). This measure eliminates the connection between the attacker and his malicious tools, and thus drastically reduces the likelihood of a repeated attack. Certain external flows can be opened individually for the most critical activities (from or to a controlled server, on a given port), but reopening a wide range from or to the outside increases the risks.
Restoring servers is the first step in the rebuilding process. However, since servers are not always backed up simultaneously, resynchronisation of applications and data are often necessary before the servers are put into service. As an example, a hasty restart of a payment application during a crisis has already resulted in a double payment of hundreds of thousands of euros, which had already been transmitted to the bank before the attack.
#3 Wait for an extreme level of security before reopening
As cyberattacks can have a significant impact, fear of repeated attacks can be traumatic for crisis teams, leading them to impose an extreme level of security before restarting. The challenge here is to find the right balance between security and rapid recovery.
There are two possible strategies for rebuilding servers:
- The green zone strategy- It prioritises security over the speed of recovery. It involves creating a new network zone in which only the rebuilt machines are hosted. The technical components (Active Directory, DHCP, DNS, etc.) are dedicated to this secure zone. However, changing the addressing plan can have unintended consequences and it will slow down the reboot.
- The grey zone approach- It favours the speed of recovery over security. It consists of rebuilding or restoring servers in their initial zone. Compromised machines can be found alongside the restored machines. This strategy will represent a risk when the attack is propagated from server to server.
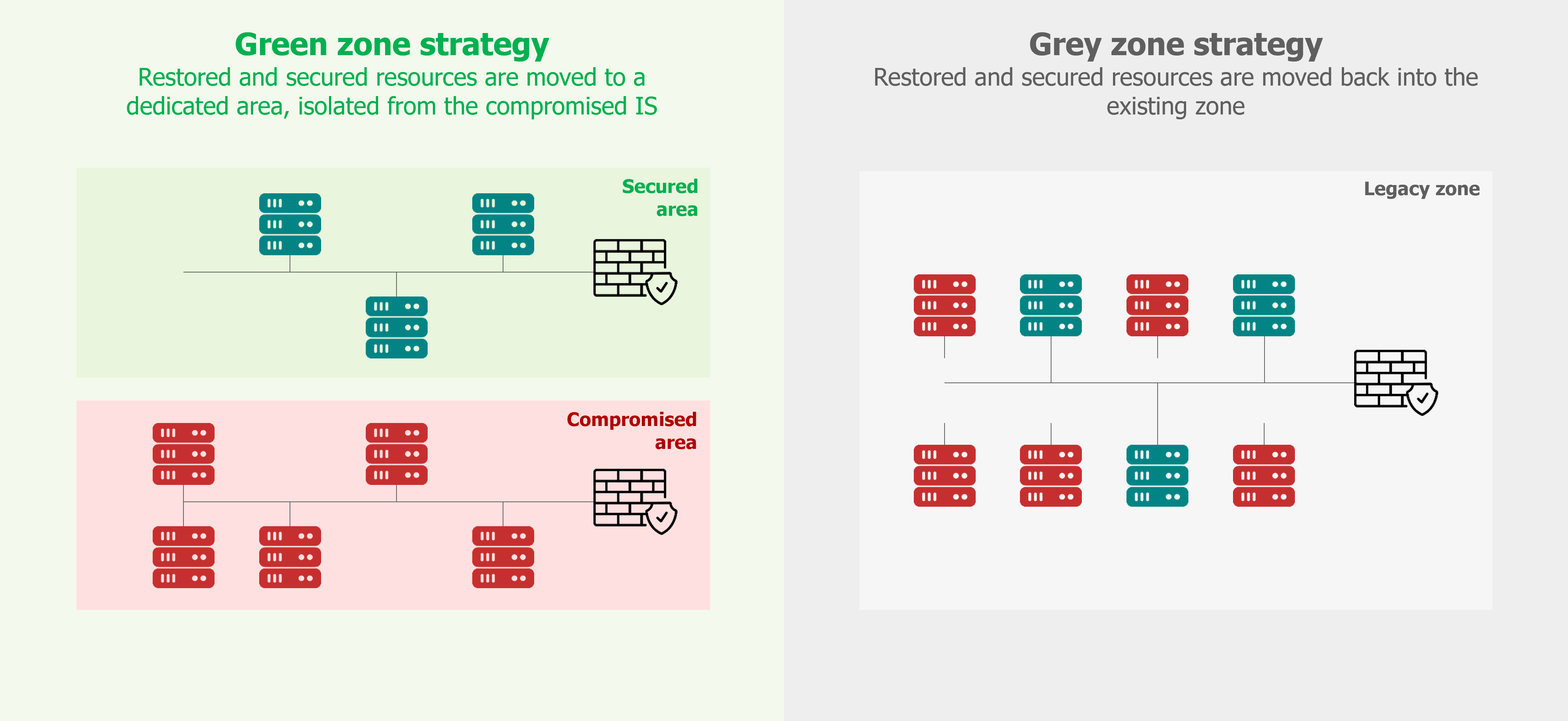
The choice of strategy must be made in the light of the investigations and techniques used by the attacker. As mentioned earlier, isolation from the outside world remains as a key measure in reducing the risk.
#4 Denying a restart in degraded mode
In most companies, IT has become indispensable for all their operations. In the exceptional situation of a total IT shutdown, it is often initially inconceivable to continue working without IT. This is the common argument put forward by the IT and business managers during cyber crisis.
By working in degraded mode, it is possible to limit the impact in many instances. This includes implementing previously defined resilience and business continuity plans. To consider implementing these plans when all the activities are ceased during a crisis, special emphasis must be given to when these activities were stopped during the crisis, as well. Managers often underestimate the mobilisation and creativity of the teams to work differently (disengaging non-essential processes, transferring to a partner, carrying out operations manually, etc.).
It is essential to find a good balance between restarting the first application in degraded mode within two days, rather than waiting two weeks to have the complete application chain.
#5 Wanting to restart all at once
Quite often, the information systems of large organisations contain hundreds or thousands of applications. During cyber crisis situations, it is impossible to spend an enormous time on all these applications. Thus, it is essential to prioritise them by defining a restart order.
Each department often tends to consider that its own activity is the most important in the company. Arbitration by general management is often necessary to establish a restart plan that can be utilised by everyone. Some departments, countries, or regions will see their applications getting started later than others too.
It should also be noted that there are many dependencies between applications, and these are not always known by IT teams. But this must be considered in the reboot plan.
#6 Executing major changes in a hurry
It is sometimes tempting to want to take advantage of the situation of a system shutdown to carry out major changes in the information system.
Security teams see this as an opportunity to carry out projects that the IT department has turned down in the past because of their perceived complexity and impact: network partitioning, upgrading operating system versions, Active Directory tiering, multi-factor authentication, etc.
If these projects are necessary to reinforce a level of security, it is advisable to avoid making too many changes during the crisis period. Thus, the teams can concentrate on actions that are necessary to restart within a controlled level of security.
For example, partitioning the network requires a review of the addressing plan, the addition of network equipment, and the modification of configurations. These actions often cause additional problems to be dealt with (IP hardcoded in the application, blocking of flows necessary for the proper functioning of the application, etc.).
#7 Waiting until investigations are complete
Investigations are essential to understand the attacker’s techniques and identify the vulnerabilities they exploited to carry out the attack. These vulnerabilities can be corrected during the reconstruction to avoid a new attack. However, investigations are complex and time-consuming (sometimes several weeks).
A standard mistake is to wait until the end of the investigation to launch the reconstruction. In reality, it is essential to start the reconstruction operations before the end of investigations. According to the conclusions from the investigative teams, the plan for secure reconstruction will be regularly revised.
In many instances, it will not be possible to identify patient zero or reconstruct the attack’s chronology. Indeed, the traces (log) maintained by the information system are not always precise (verbosity) or it does not permit going back far enough (retention time). They have sometimes been deleted by the attacker itself, while erasing his traces.
Finally, decision-makers frequently ask whether the data has been exfiltrated from an information system. It should be emphasised that unless the organisation has advanced security systems, it is rarely possible to respond precisely to this issue (DLP, for example).
#8 Not anticipating human resource management
Cyber crises are situations where employees are intensely mobilized. Some members of the teams can be so determined to settle this matter, that they do not wish to quit at all! Concurrently, it is quite common to see cases of burnout, hospitalization, or sick leave during a poorly managed crisis.
In the case of a large-scale ransomware attack, intensive team mobilisation will take at least three weeks. It is essential to organise team rotations from the start of the crisis ensuring that key resources are maintained over time.
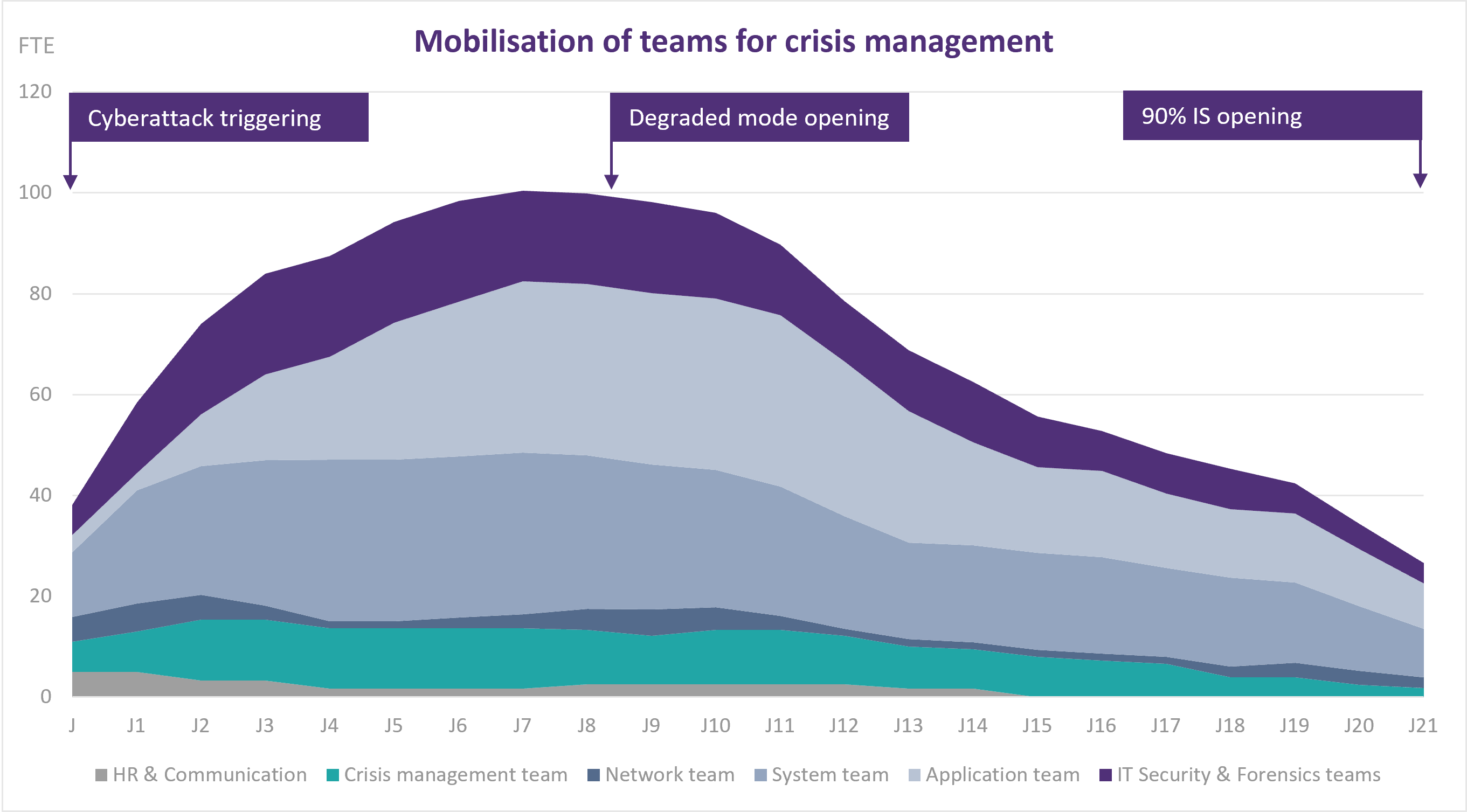
It is often appropriate to call on external service providers for expertise (digital investigations, Active Directory reconstruction, backup systems, etc.) to multiply efforts (reinstallation of workstations, upgrading of operating system versions, coordination of tasks, etc.).
#9 Hiding the situation from employees, partners, customers
More than five years ago, companies that suffered a cyberattack but failed to take adequate precautions had their reputations severely harmed. Due to the rise in cyber-attacks, an increasing number of organisations are falling victim to cyber-attacks, and firms will be evaluated not just on their ability to manage a crisis, but also on their status as victims.
One of the first reflexes of management teams is often not communicating with stakeholders (employees, partners, and customers) in the hope that the attack will go unnoticed. It is clear that a major attack will always end up being communicated. In these situations, social networks and the media will communicate before the victim, who will then have to adopt a defensive posture in response. It is recommended to adopt a posture of transparency with the stakeholders, who will be reassured to know that the situation is under control.
Finally, there must be appropriate communication between partners. Without specific information, many of the attackers tend to cut all the links with the victim, and thus the reopening could be longer and more complex. Moreover, s will be inclined to reopen if the victim has proactively warned them.
#10 Failing to structure crisis management
Since ransomware attacks have a significant impact on information systems, they inevitably cause chaos within an organization. Thus, no longer we can rely on the current communication and decision-making procedures.
Some people think that a crisis situation allows approximate management: improvised meetings, follow-up of perfectible actions, lack of formalisation, etc. On the contrary, decisions must be precise, rapid, formalised, and communicated to all stakeholders involved. This discipline is the key to successful crisis management, where everyone finds their place and is utilised wisely.
In certain large-scale crises, such as those involving international groups, keeping a PMO crisis unit for several dozen individuals is advantageous. It will be their responsibility for consolidating precise inventory, organising crisis committees, communicating, and following up on the decisions taken by the crisis unit. This unit of crisis management professionals is an indispensable asset for effective crisis management.
A ransomware attack is a sudden event that has a very significant impact on the business’s operations. There are various pitfalls to avoid in crisis management to quickly regain a functional situation. To optimise operations and gain valuable feedback, it is strongly advised to surround yourself with cyber crisis management professionals.


