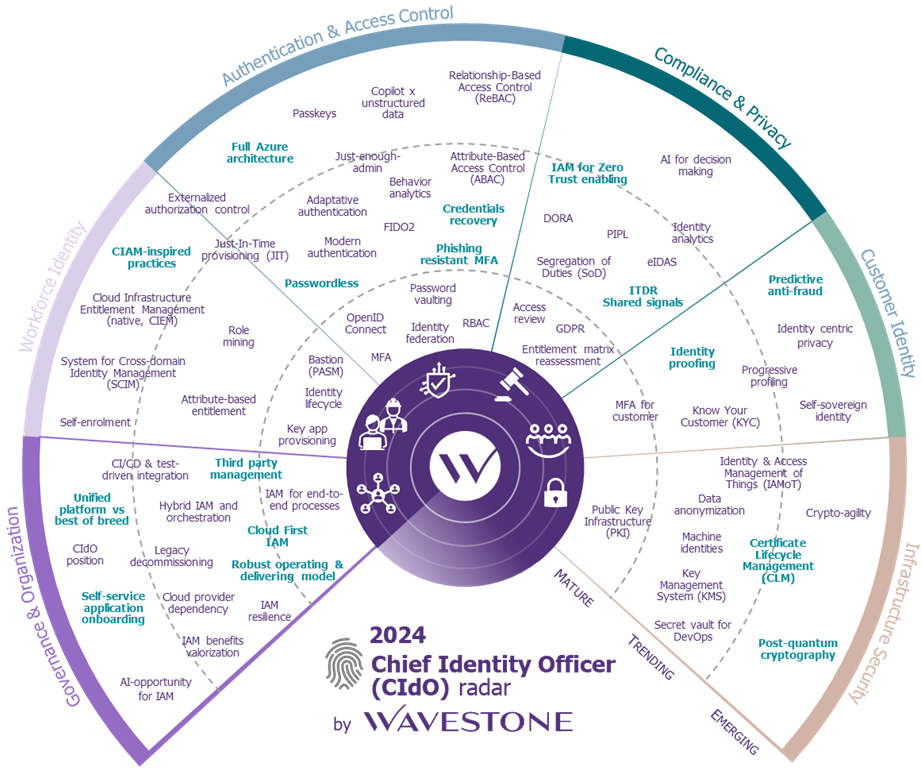
Chief Identity Officer (CIdO). That’s the new term introduced by Gartner to define the role of an identity manager within an organization. While this term is still relatively new, upcoming challenges regarding digital identity could well elevate the CIdO to the same level as its counterparts, the CISO and CIO (respectively Chief Information Security Officer and Chief Information Officer). In fact, Gartner estimates that by 2027, 45% of IAM (Identity and Access Management) leaders in organizations will be promoted to executive-level positions[1]. However, there are many challenges that can arise, such as : the integration of IAM within a Zero Trust strategy, exponential growth of machine identities, hybrid work models, etc. and an IAM expertise who will be required to address them.
Drawing from its experience in the field of digital identity, Wavestone is publishing its first edition of the CIdO Radar in 2024. This radar follows the same methodology as the CISO Radar published by the firm for the past 10 years and offers an in-depth look at the underlying trends driving the digital identity ecosystem.
In this article, we invite you to explore some impactful and structuring topics for the IAM landscape, with two currently trending subjects (passwordless and CLM) and moving towards the future topics they foreshadow in the emerging section of the radar (respectively predictive anti-fraud and post-quantum cryptography).
Passwordless, a major evolution not so simple to achieve
For decades, the password has been the central authentication factor for users (and often still is). Passwords have then been complemented into multi-factor authentication strategies to compensate for the inherent weaknesses of this authentication method (low complexity, reuse, phishing risks, etc.). New tools have thus been added to the user authentication process: OTP via SMS or email, push notifications, soft and hard tokens, etc. Despite the increased security level provided by the addition of these new authentication factors, the password remains both a weakness if discovered (it remains reusable on an account without MFA where it is enrolled) and a burden for the user’s experience, as they must remember it and securely store it.
All these reasons have led vendors to imagine secure authentication methods not relying on the use of a password. Eliminating the password allows companies to improve the user experience for their employees, enhance authentication security by reducing the attack surface, and benefit from a positive image in the market. The user finds themselves in an environment where they no longer need to remember a multitude of complex passwords and where they are no longer at risk of having their account stolen through phishing attacks. The use of FIDO2 (Fast Identity Online 2) technology is based on asymmetric cryptography which is currently the most widespread alternative to passwords. This technology is driven by the FIDO Alliance (Google, Microsoft, Amazon, Apple, etc.) and, relies on the use of physical security keys locally storing the private key associated with each service. Ultimately, this allows a user to log into all their accounts without a password, their login, or email address (simply by using the physical key they possess and a second factor such as biometrics).
However, implementing passwordless authentication comes with significant organizational questions for a structure. How to manage account recovery if this account does not rely on a password? If an employee loses their security key, how can access to their account be restored without being able to use the associated private key? This major issue of “credentials recovery” is inseparable from any passwordless policy and assumes that an organization has anticipated each step of it, such as: purchasing and distributing authentication media, managing their loss/theft/destruction, obsolete media rotation processes, account backup solutions, double enrolment for critical accounts and management of employee departures, etc.
Passwordless authentication is a trending topic and is being deployed in many organizations. For many, the next step involves establishing fraud detection capabilities before they occur (also called “predictive anti-fraud”).
Predictive anti-fraud, how to prevent fraud before it occurs?
Predictive Anti-Fraud corresponds to proactive monitoring of systems aimed at identifying and stopping fraud before it occurs, rather than relying solely on post analysis of malicious activities that have already happened. These surveillance capabilities are particularly relevant for securing online business activities involving money transfers (such as pooling funds, loyalty accounts, online payments, etc.) in sectors like retail or luxury for instance (as they are often less mature on this subject than banks). We are currently witnessing an increase in phishing attacks aimed at stealing customer account data to misuse their contents (loyalty card fraud, for example, is a real concern for players in the retail sector).
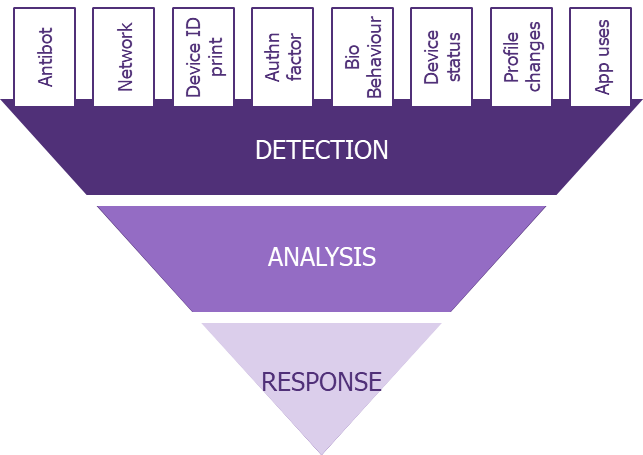
Access management solutions are increasingly capable of detecting fraud patterns and halting illicit activities before completion. All these capabilities rely on machine learning (involving a training phase for the tools) and involve three key stages:
- Detection: Systems can detect behaviours deviating from typical user/customer journeys and as well as sequences of suspicious actions. Detection relies on the customer context (browser used, network, cookies, etc.), the dynamic context (IP address, device used, user behaviour, typing speed, strength of authentication performed, etc.), and the business context (type of requested transaction, amounts, modifications of sensitive information, etc.).
- Analysis: Automatic analysis is conducted with the assignment of a confidence score to the current user profile.
- Response: Response rules are defined to best address alert triggers, with automatic responses for obvious or critical situations (e.g., additional authentication factor, session termination), or manual responses for cases requiring human decision-making.
The main challenge of predictive anti-fraud is the correct calibration of machine learning tools and their adaptation to the specific business context. Placing too much emphasis on security could cause a disproportionate amount of negative impact on the service: a high number of false positives affecting user experience and an increase in service complexity and slowdowns (captcha, step-up authentication, significant network consumption, longer processing times). The definition of relevant security and detection rules must be accompanied by a model based on machine learning, as specific as possible to the use case. Given the increasing complexity of attacks, the key to an effective predictive anti-fraud strategy lies in the solutions’ ability to detect and correlate weak signals. For example, some vendors are now capable of detecting fraud attempts during false customer service calls by correlating the users’ actions with whether they are on a phone call.
Certificate Lifecycle Management (CLM), a new market for an old issue
Many companies are currently facing an explosion in the number of electronic certificates within their IT systems. These certificates (and associated cryptographic keys) serve various purposes such as machine-to-machine authentication, user authentication, data signing and encryption, websites security, application micro-services, etc. This increase in the number of electronic certificates significantly increases the workload for the teams in charge of their management. The lifecycle of an electronic certificate includes several stages such as:
- Requesting the certificate from a PKI (Public Key Infrastructure)
- Receiving the certificate and associated keys
- Deploying the certificate within its scope (either as a replacement for an expiring certificate or on a new scope)
- Decommissioning and revoking the old certificate (if applicable)
- Continuously monitoring the certificate and its future expiration date
- Reproducing this process for each certificate before its expiration.
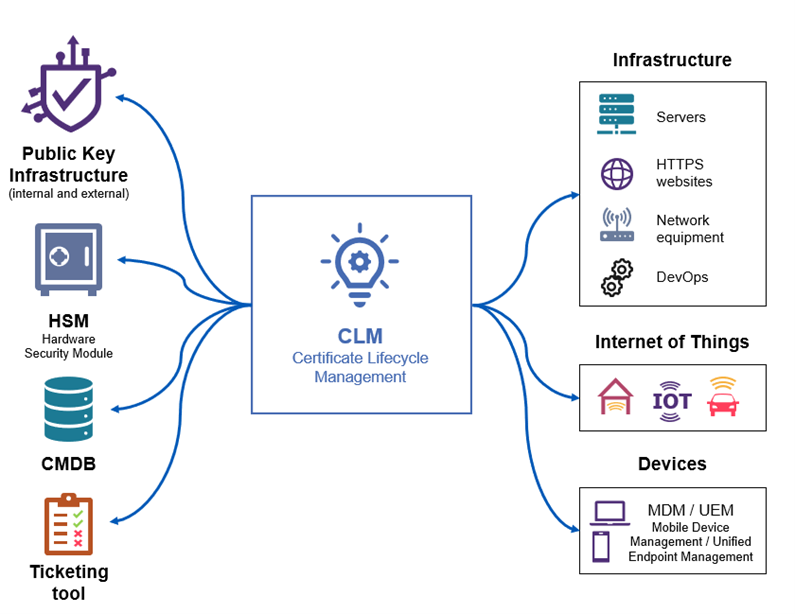
Manual management of tens (or even hundreds) of thousands of electronic certificates poses numerous challenges. This type of management is highly resource-intensive, relies on repetitive tasks, and is prone to human errors. It is not uncommon for certificates to slip through the cracks of teams and go unrenewed, or simply remain undeclared within the IT system (shadow IT). For all these reasons, an organization with a large fleet of electronic certificates should consider adopting a CLM solution.
CLM solutions offer many features to facilitate and ensure the reliability of certificate lifecycle management. Some of these features include:
- Certificate discovery tools, allowing a company to have a comprehensive view of its certificate fleet (even for undeclared certificates).
- The use of protocols automating all certificate-related actions (mentioned above).
- Numerous connectors enabling clients to seamlessly integrate these solutions within their IT systems.
- Governance and rights management modules for certificates.
- Alerting capabilities serving as a safety net for teams.
The “Zero Trust” philosophy, often requiring securing communications between services through mutual authentication using electronic certificates (with the increasingly frequent use of microservices architectures, the explosion of non-human accounts, etc.), tends to increase the number of electronic certificates within organizations. Utilizing dedicated certificate lifecycle management tools rather than manual tracking can reduce certificate-related incidents by 90% and decrease incident processing time by 50%, according to Gartner[2].
For more details on CLM solutions, you can read Wavestone’s article dedicated to this subject here.
The implementation of a CLM solution signifies a step forward in securing infrastructures, but more importantly, it can be leveraged towards crypto agility (the ability to quickly replace or update encryption algorithms or protocols to address evolving threats). Crypto agility is a theme that we should expect to encounter more and more frequently in the medium term, largely due to the development of quantum computers.
And what’s next? Technological challenges ahead, such as post-quantum cryptography
While organizations strive to adopt robust IAM strategies, considering current technological threats is no longer sufficient. The impending topic of quantum computing (even if it seems still a few years away from now) is set to disrupt all our encryption practices, necessitating early anticipation of measures to be implemented for the 2030 decade. The use of quantum computers and their famous qubits (which can simultaneously take on values of 0 or 1) already allows for much more efficient cryptographic calculations than traditional computers.
It is important to note that symmetric cryptography is not as much at risk from quantum threats, and increasing the size of encryption keys will allow this encryption mode to resist quite effectively. However, classic RSA and Elliptic Curve asymmetric cryptography is truly threatened: key exchange, authentication, and digital signature which rely on that classic asymmetric cryptography are already at risk for specific use cases. The Shor’s algorithm could enable a quantum computer to break RSA 2048-based encryption in a matter of hours.
Post-quantum cryptography is currently focusing on solutions to adapt encryption to the future capabilities of quantum computers. ‘Store Now, Decrypt Later’ which means that we can decrypt in 10 years what is captured now, even encrypted, or the capability to modify (in 10 years) the author or the content of a digital signature are risks that should already be considered today, especially with the time needed to handle the migration to post-quantum algorithm. In 2022, NIST published a list of 4 such encryption algorithms, resistant to quantum computers: CRYSTALS-Kyber for general encryption, CRYSTALS-Dilithium, FALCON, and SPHINCS+ for electronic signature. These algorithm should be confirmed during 2024.
The main current recommendation to ensure the transition to post-quantum encryption is to perform hybrid encryption, i.e., to use both classical and post-quantum encryption algorithms to secure communications. While this issue is not yet at the heart of current IAM challenges, it is important to monitor its evolution, especially since some major vendors are already entering the market and introducing a new term: QCaaS (Quantum Computing as a Service).


