The increasing maturity of technologies associated with the use of digital certificates
The use of digital certificates on information systems has been around for over 20 years. It is a proven practice based on standardised technologies and regulations governing several of its use cases. A digital certificate can be considered as a “digital” identity card of its owner, using asymmetric cryptography to authenticate its owner and enable them to perform data encryption and digital signature operations. A digital certificate may belong to several types of holders and serve to cover various use-cases.
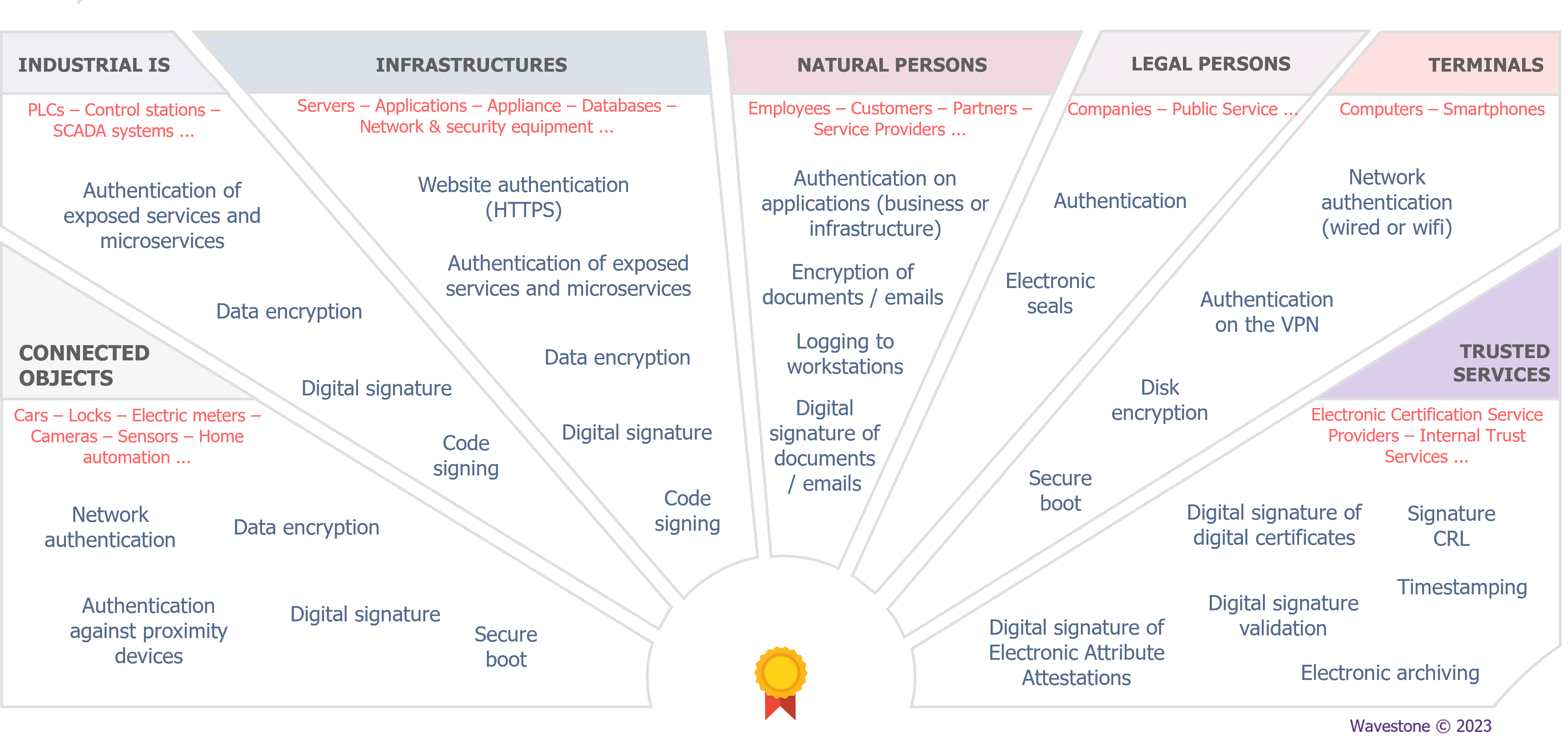
Historically, digital certificates were used in limited areas within an information system, mainly for two reasons:
- First, the use of cryptography, particularly asymmetric, reduces equipment performance (primarily using computing capacity).
- Secondly, the level of cyber threats in the past was relatively low compared to the current level.
Thus, the use of digital certificates was not always justified regarding information system security challenges and the hardware resources required to avoid performance degradation.
For several years, technological developments have significantly improved the performance of computers, thereby enabling the use of digital certificates for an increasing number of holder types, and to cover increasingly diverse use cases to address the growing level of cyber threats and protection needs. At the same time, there is also improvement in maturity of technologies associated with the use of digital certificates, such as PKI systems that issue digital certificates, cryptographic hardware to secure private keys (e.g. Hardware Security Module (HSM), smartcards, etc.), or even more specific software to better manage certain use cases (e.g. Card Management System (CMS), Key Management System (KMS) etc.).
The emergence of Certificate Lifecycle Management (CLM) products
The growth of both usage and the number of digital certificates in recent years have highlighted new issues for several stakeholders within an organization: operations teams, who deploy digital certificates on infrastructure components or business applications and manage their lifecycle; security teams and architects, who are responsible for defining and enforcing digital certificate usage policies within the organization and preventing deviations; and the business units that use certificates on their applications, which may experience availability issue if certificates are expired. These issues are exacerbated by current strong evolution in technological environment, that challenges the maturity of existing infrastructures (particularly PKI) and gives rise to a new family of products, the “Certificate Lifecycle Management” tools, to complement existing products in this area.
The following three chapters detail the issues and difficulties that CLM solutions attempt to address.
The difficulty of managing digital certificates
Let’s take an example of an operations team in charge of several servers or applications. To obtain a digital certificate for a server, this team has to create a request to their organization’s PKI following associated processes, and then install it on the relevant equipment. For every 1 to 3 years, they have to remember to renew it before it expires by repeating the certificate request process with the PKI. Multiply this by the thousands of infrastructure digital certificates that may exist within large organizations, and there will be following consequences:
- Teams spending a lot of time requesting and installing digital certificates on equipment, especially if the processes require multiple approvals to meet internal or external compliance requirements.
- Teams not well trained with the usage of digital certificate , with a high risk of error in installed certificates, at best delaying service implementation and at worst introducing security vulnerabilities to target equipment.
- A very high risk of forgetting to renew a certificate before it expires, causing a disruption to the related service. The level of impact will depend on the service and can potentially reach the highest level for an organization.
Based on our experience working with our clients, the risk of forgetting to renew certificates is very common. For example, Microsoft forgot to renew a certificate for Microsoft Teams in 2020, causing service downtime for about 3 hours(1).
Cyber risk associated with improper use of digital certificates
Security teams and architects define and implement compliance rules regarding the use of digital certificates and associated processes. To comply with these rules, operations teams may find managing the lifecycle time-consuming, thus they may not always follow the certificate request processes from their organization’s PKI:
- Either by bypassing them to obtain certificates from the “official” PKI in a sneaky way, with fewer security checks on the legitimacy of the request, and fewer traceability elements for audit purposes;
- Or by installing “rogue” certificates, self-signed or obtained from a “non-official” PKI/Certification Authority, with the risk of introducing technical vulnerabilities to the information system that could be exploited by an attacker.
During our audit assignments for our clients, we often discover the use of “unofficial” certificates that are very difficult to identify exhaustively. This lack of control over digital certificates used in an information system represents a challenge for security teams to manage cyber risk and deploy appropriate security solutions.
A fast-evolving technological environment
As mentioned earlier in this article, for several years now the use of digital certificates has become more widespread, and the products on the market have become more matured. The regulatory framework (e.g. eIDAS(2)) has followed this trend by regulating several trust services based on the use of digital certificates (e.g. electronic signature, timestamping etc.).
Today, some more recent technological trends are making the use of digital certificates even more essential, while introducing new constraints:
- The increasing use of microservices architectures, especially in “Zero Trust” deployments, requires securing communications between these services using mutual authentication with digital certificates. The number of these certificates therefore continues to grow within information systems, which increases the difficulties outlined in the previous two chapters.
- Continuous Integration/Continuous Development (CI/CD) practices and the automation of deployments using “DevOps” tools are also increasingly adopted by information system departments. These approaches require end-to-end automation of service deployment, including certificate installation. To address this constraint, it is essential to rely on technologies that automate the certificates lifecycle management and interface with PKI solutions.
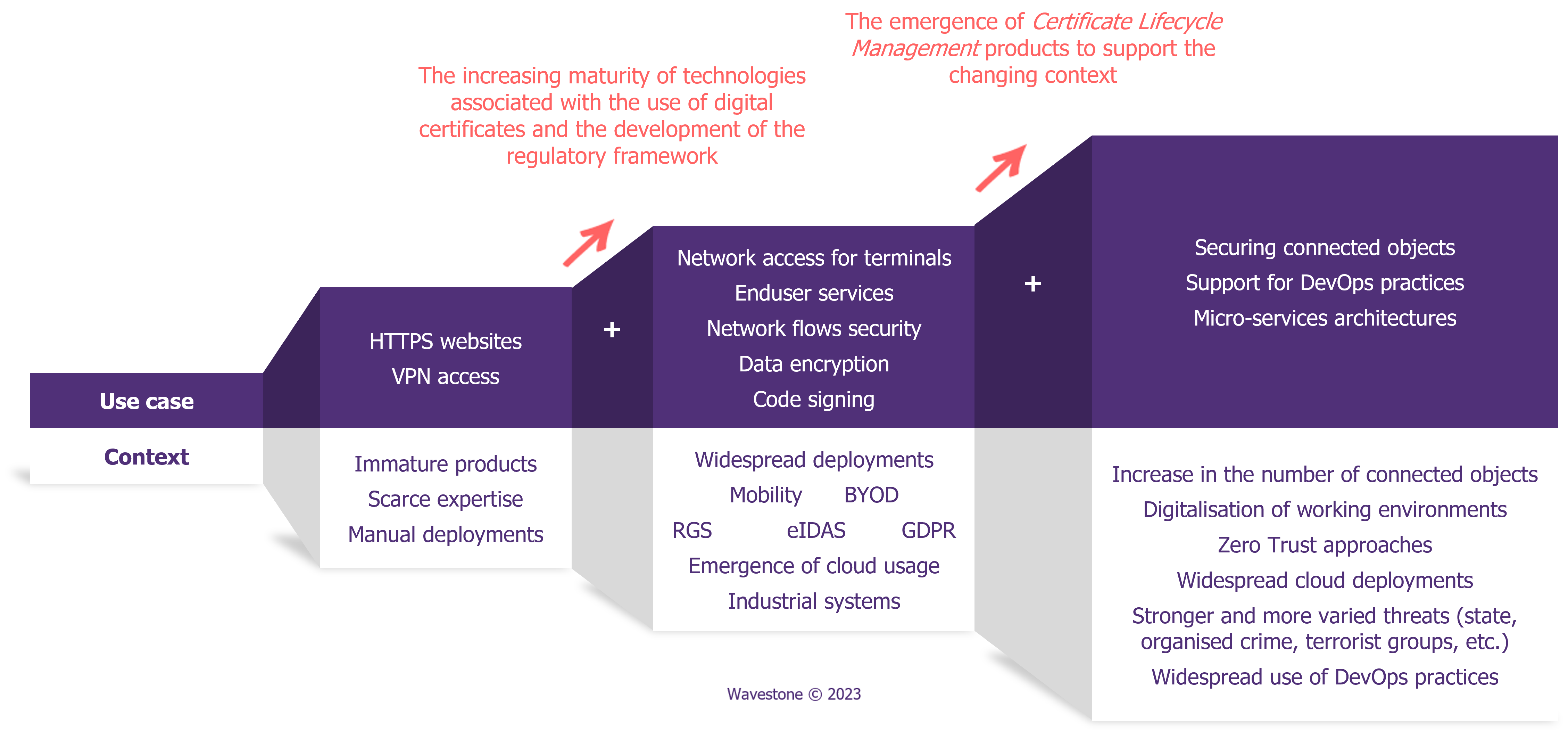
With these findings in mind, CLM solution is here to help saving time for teams managing digital certificates, improving efficiency, enhancing the security level of the information system, reducing service interruptions on business applications and offering innovation opportunities to development teams.
Services provided by CLM products
To address these issues and the growing demand for effective certificate lifecycle management, several vendors have developed so-called CLM (Certificate Lifecycle Management) solutions. A CLM solution is a software designed to help organizations automating the lifecycle of their fleet of certificates. These solutions first provide tools to discover digital certificates deployed on the information system and provide effective reporting in a unified interface. This feature is very useful for discovering “unofficial” certificates. CLM solutions can also interact with numerous PKI environments to consolidate certificate management under a single tool. They offer various dashboards and features enabling organizations to have an overview of their certificates, to handle them (e.g. applying renewal and automation policies, alerts on non-compliant certificates etc.), and they use connectors to integrate themselves into organizations’ existing needs and workflows (DevOps, ticketing, etc.). CLM solutions, therefore, position themselves at the centre of the IS to achieve maximum efficiency on tracking digital certificates.
Using dedicated management tools, rather than manual tracking, for certificate lifecycle management can reduce certificate-related incidents by 90% and reduce incident processing time by 50%, according to Gartner(3).
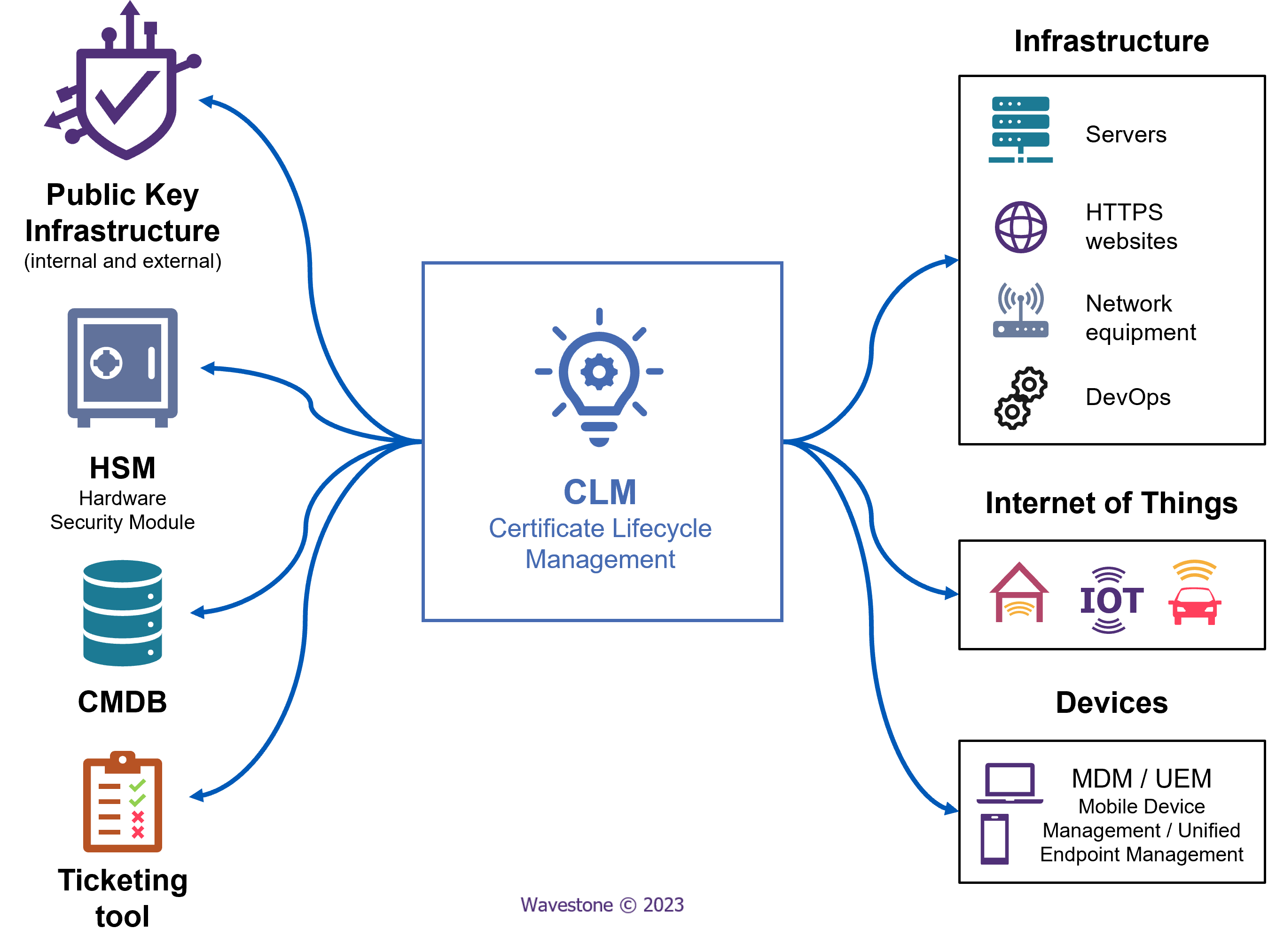
To choose the most suitable CLM solution for an organization, as they do not offer the same functional coverage, the following four areas must be evaluated:
- Certificate discovery: any use of a CLM solution begins with the discovery of certificates present on the organization’s information systems. These discoveries have several objectives: gathering of all an organization’s certificates in a common interface regardless of the issuing certification authority, discovering unknown certificates that were not previously tracked, collecting information on each certificate to identify the proportions of compliant and non-compliant certificates, and visualising the certificate fleet in the form of dashboards highlighting all important information (e.g. number of certificates, upcoming expirations, compliance with chosen security rules etc.). The discovery of server certificates can be done in two ways to adapt to the potential security measures implemented within an IT system: a centralized discovery scan from the CLM solution with incoming network flows into the organization’s servers, or a decentralized discovery scan relying on the installation by an employee on each server that will perform a local search and report data back to the CLM solution (outgoing network flows from servers only).
- Automation and connectors: the main goal of a CLM solution is to allow its users to avoid manual management of certificates, as it is time-consuming, resource-consuming, and prone to human errors. Once discovery scans are completed, an organization can use various tools to create workflows that automate the certificate lifecycle. For example, it is possible to automatically renew all certificates from a chosen certification authority by replacing them with certificates issued by another authority, which would be very useful during a PKI migration. CLM solutions can also automate certificate revocation at the end of their lifecycle, as well as the request and installation of the next certificate. The automated management of a large fleet of certificates necessarily involves a configuration phase that can take time, but the benefits in saving time, resource, and enhancing security justify this investment. To achieve this, CLM solutions integrate via connectors with many PKIs on the market, infrastructure components using digital certificates, or CMDBs. Connectors also enable CLM solutions to interact with ticketing tools, MDM or UEM solutions for terminal management, and to manage certificates in DevOps environments (e.g. Terraform, Kubernetes, Docker etc.).
- Governance: organizations can create compliance rules regarding certificates and their issuance modes. These rules aim to control future certificate issuance and help identifying existing certificates that do not comply with them (e.g. self-signed certificates, small key size, untrusted certification authority etc.). All these rules are fully customizable. CLM solutions also allow segregation of rights according to roles (administrators, users, auditors, etc.), geographic zones, teams, or any other attribute.
- Alerting: This is an important aspect of CLM solutions because automating a fleet of certificates takes several months (or even years). Alerting allows certificates with workflows not yet automated to be processed and thus serves as a safety net in case of renewal is forgotten. Alerts can take different forms, for example notifications within the solution, emails sent to administrators, notifications on Teams/Slack, opening tickets on ServiceNow or Jira. To identify the recipient of alerts, solutions can rely on the information collected by the PKI during the initial request for certificates, cross-reference certificate information with that of a CMDB, or use AI features to “guess” the team or person to notify when precise information cannot be found in available data sources.
The CLM solutions market is growing rapidly, with the new features being added regularly, and more areas being covered. It would not be surprising if this type of solution were to manage the cryptographic key lifecycle in general, beyond just digital certificates, and thus complete the current KMS solutions as they do today with PKI solutions.

The CLM solutions market is currently experiencing significant growth
The CLM solutions market consists of both historical players (often already being active in areas such as PKI or machine identities and offering a wide range of services outside of CLM solutions) and emerging players that can be classified as pure players, who have started to develop their CLM service in recent years and for whom this segment represents most of their activities. Below is a list of actors that are often found on the market (presented in alphabetical order):
Appviewx: an American company founded in 2004 based in New York. In addition to its CERT+ certificate lifecycle management solution, Appviewx offers a Cloud PKI and IAM service.
DigiCert : an American company created in 2003 based in Lehi, Utah. Digicert is a public certification authority that provides electronic certificates and PKI services to organizations. To complement its PKI offering, Digicert has launched its certificate lifecycle management solution: CertCentral.
Digitalberry: a French company founded in 2014 based in Marseille. The company’s CLM solution, Berrycert, was released in 2021. Digitalberry also offers a data traceability solution based on the blockchain and a security key management solution. Digitalberry is part of the 2020(4) and 2021(5) French cybersecurity start-up radar developed by Wavestone in collaboration with Bpifrance.
Entrust: an American company founded in 1994 based in Minneapolis, Entrust is a historical player in the PKI field. Entrust’s Certificate Hub is a solution dedicated to certificate lifecycle management. This solution is added to other digital security solutions available on-premise and as a Service: PKI, HSM, KMS, IAM; and also to Entrust’s physical and digital passport and identity document issuance solutions.
Evertrust: a French company founded in 2017 based in Paris, Evertrust released the first version of its CLM solution called Horizon in 2018. They also offer an internal certification authority (Stream) and an OCSP responder services. Evertrust is part of the 2021(5) and 2022(6) French cybersecurity start-up radar developed by Wavestone in collaboration with Bpifrance.
Keyfactor: an American company founded in 2001 based in Cleveland. Keyfactor left its PKI consulting segment in 2014 to become a solution provider, including Keyfactor Command which is the company’s CLM solution. In 2021, Keyfactor acquired Primekey to complement its offer with a PKI solution.
Sectigo: an American company created in 1998 based in Roseland, New Jersey. Sectigo is a public certification authority that provides certificates and PKI services to organizations. Sectigo has developed its CLM solution called Sectigo Certificate Manager to offer complementary services to its PKI business.
Venafi: an American company founded in 2000 based in Salt Lake City. Venafi offers the TLS Protect solution to manage an organization’s certificate lifecycle. Venafi also offers PKI, KMS, and code signing services.
Conclusion
Regardless of the industry, any organization reaching a certain size will face the increasing number of digital certificates to manage and the associated risks in terms of management and security.
It is therefore important to address this issue as soon as possible in order to evaluate how to take advantage of a CLM solution, to improve the security level of its information system and to simplify the day-to-day work of its teams, as shown by Wavestone’s CISO radar which highlights the use of these products in the “trending” category(7).
Bibliography
(1) https://www.theverge.com/2020/2/3/21120248/microsoft-teams-down-outage-certificate-issue-status
(2) https://www.riskinsight-wavestone.com/2016/10/eidas-route-vers-europe-de-confiance-numerique/
(3) https://www.gartner.com/en/documents/3969998
(4) https://www.wavestone.com/fr/insight/radar-2020-startups-cybersecurite-francaises/
(5) https://www.wavestone.com/fr/insight/radar-startups-cybersecurite-2021/
(6) https://www.wavestone.com/fr/insight/radar-startups-cybersecurite-2022/
(7) https://www.wavestone.com/fr/insight/radar-rssi-2023/


