DORA, in a nutshell
The European Union published the Digital Operational Resilience Act, or “DORA”, on December 27th, 2022, and it entered into force on January 16th, 2023. It sets new rules for financial entities and their ICT third-party service providers in terms of ICT resilience. Compliance to the text will be mandatory starting January 17th, 2025.
The Digital Operational Resilience Act aims at simplifying and improving the resilience of financial service organisations by establishing a robust regulatory framework and oversight body. As previously shared in details, in our article Decrypting DORA: what does it mean for resilience of financial organisations?, it introduces requirements across five pillars:
- ICT risk management
- ICT-related incident management, classification and reporting
- Digital Operational resilience testing
- Managing of ICT third-party risk
- Information and intelligence sharing (optional)
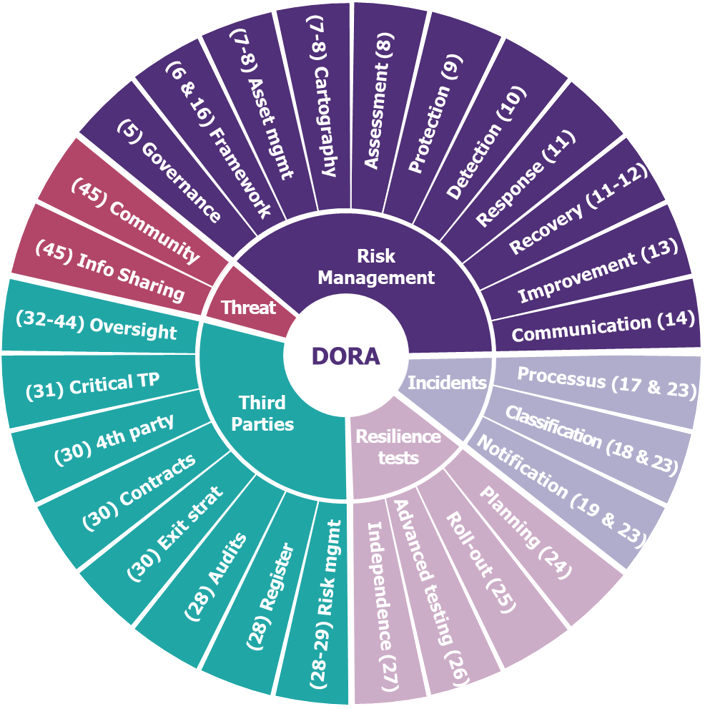
Main DORA topics and articles applying to financial entities
(article references between brackets)
When analysing the content of the regulation and while taking into account the current maturity of the financial sector, the complexity largely differs depending on the topic addressed. As ICT frameworks are already a best practice widely adopted within the financial services sector, the effort will mainly focus on bringing more consistency across the organization. Similarly, ICT-related incident management has already integrated within its processes and tools numerous regulatory constraints in terms of classification and notification. Consequently, integrating the DORA requirements should not present major difficulties.
Nevertheless, meeting the requirements to be compliant will still have its challenges… And opportunities!
An ambitious regulation that puts the finger on known fragilities
The first challenge for many organisations will be to onboard the top management in the initiative. As DORA appoints them as accountable for monitoring, approving, reviewing, and setting the direction in terms of operational resilience, their involvement is key to the success of a potential program. Early onboarding will allow to gain precious time in identifying and validating critical functions in the scope, prioritizing the main threat scenarios, and set the pace on the topic. However, this will imply for the teams to carefully think about the proper and comprehensible KPIs and KRIs to report on the operational resilience level of the organization. As much as possible, give them quickly an overview of the regulation content and their expected role in this context!
The second challenge will be to raise the bar in terms of third-party risk management. Large organisations often have hundreds, if not thousands of third-party providers implying a fastidious sorting to focus on the most critical. Third-party operational resilience risk management mainly relies today on integrating steps within the purchasing processes and, in the end, including specific clauses within the contracts. DORA asks for more with responsibility falling on financial services to make sure third-party compliance to these requirements are met. It also requires working on potential exit strategies and joint testing where relevant. This step up may define a shift in how business is done with suppliers in the future and should be anticipated by the concerned third parties to be able to provide proofs of their operational resilience risk management.
Finally, testing is a crucial point and a challenge within DORA. Organisations will need to structure and regularly test their resilience to continually assess risks and the suitability of their resilience strategies. It requires to gain a strategic vision on the topic, which rarely pre-exists as the tests are often managed in silos (vulnerability tests, penetration tests, business continuity tests…). In this context, they will also need to ensure the proper coverage of their critical functions over the years within the testing approach. Organizations are also expected to conduct threat-led penetration tests in live production every three years at least and potentially including ICT third-party providers.
Overcoming these challenges will not be an easy journey. It is key to start working on these topics quickly as they will ask for true changes for the concerned organizations. Obviously, a detailed gap analysis with the regulation requirements is a good starting point.
Resilience first, compliance second?
Clearly, a regulation such as DORA brings along opportunities for those who will try to see beyond the compliance constraints.
First, the regulation introduces a holistic approach to ICT risk management that could bring more consistency across the organizations. It could constitute a first step in putting together a unified framework, allowing a better assessment of the organization’s ICT risks and simplifying overall reporting to the top management. It could also initiate the idea of a converged governance on ICT risk management gathering cybersecurity, business continuity and IT service continuity.
Second and foremost, it is a unique opportunity to work on your real resilience level by asking yourself complex questions. If you were to face a no-IT situation tomorrow, would your organization survive? Would your existing capabilities fully cover the needs that such situation asks for? And are you confident that your resilience solution would work on D-day?


