The ISO 27001 and ISO 27002 standards provide a set of requirements and best practices to organize and implement an Information Security Management System (ISMS) within any organization.
The success of these standards has been widely observed both in France and on an international scale for many years and shows no signs of decline. For instance, the 2022 ISO annual survey showed a 19% increase in ISO 27001 certifications worldwide from 2020 to 2021, and a 44% increase in France.
After nearly 10 years of effective and loyal service from their previous major version, dating from 2013, the third edition of the ISO 27001 and ISO 27002 standards was published in 2022. What changes have been made and how does this affect our analysis of the Information Security landscape?
The first obvious change reflects the evolution of the “Information Security” field over the decade: “cybersecurity” and “privacy” are now part of the standards’ titles:
- ISO/IEC 27001:2022 Information security, cybersecurity, and privacy protection — Information security management systems — Requirements
- ISO/IEC 27002:2022 Information security, cybersecurity, and privacy protection — Information security measures
The evolution of security measures (Annex A): the main change in ISO 27001
The new edition of the ISO 27001 standard presents very few alterations in its body: the few changes mainly clarify or make explicit some clauses of the standard without changing their content.
Some changes will require limited alterations to the ISMS, such as:
- The explicit obligation to document the objectives of the ISMS and to monitor their achievements (clauses 6.2 d) and g))
- The need to plan ISMS changes (clause 6.3): this clause could be covered, for example, by extending the ISMS improvement management process to any ISMS change, or by relying directly on the organization’s change management process
- The reinforcement of the obligation to control externally provided processes that contribute to the application of the selected requirements or to the achievement of the ISMS objectives, by extending it to externally provided products and services (clause 8.1)
- The possibility of choosing which expectations of “interested parties” (customers, management, employees, etc.) the ISMS must meet (clause 4.2 c)): the standard now allows the exclusion of certain expectations. This clause thus allows the prioritization of certain expectations or choice between mutually exclusive expectations. This change will probably require increased transparency towards the interested parties to inform them of the decisions taken. It should be noted that the management review will now have to take into account changes of the interested parties’ expectations (clause 9.3.2 e)), in addition to the feedback from interested parties previously required.
Nevertheless, the main evolution of the ISO 27001 standard is Annex A. This annex provides a catalog of security measures – the measures being detailed in the new version of ISO 27002 -, which provides additional information and implementation recommendations for each of them.

Updates to this Annex A can thus be studied in the new version of ISO 27002.
A modernized version of ISO 27002, which is easier to use
The update of ISO 27002 is simplified, modernized, and easier to use.
First, the standard benefits from a simplified organization: previously divided into 14 chapters (some with somewhat convoluted titles…), security measures are now grouped into 4: organizational measures, people-related measures, physical measures, and technological measures.
This edition also gives rise to a (new) reduction in the number of security measures, from 114 to 93 (133 measures were included in the initial version from 2005). The content of the measures globally remains close to the previous version, but they have been reorganized. The changes are summarized below:

Note that Annex B details the correspondence between the requirements of the old and new versions of the standard: this will be a very useful tool for organizations in the transition phase (at least for updating the risk management plan and the statement of applicability).
11 new measures have been added to the standard, addressing some of the shortcomings of the previous version as well as alterations in recent years:
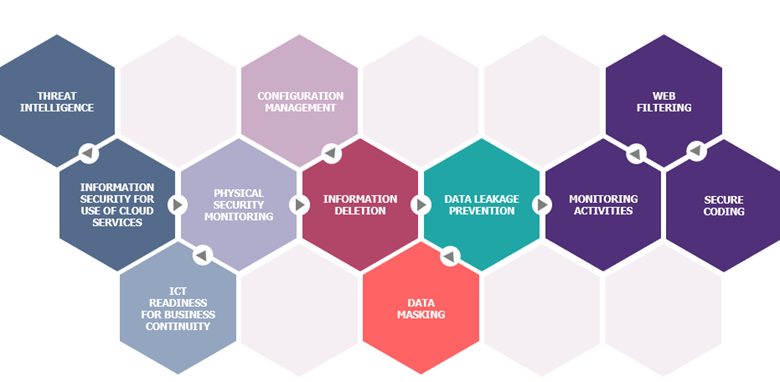
- Three measures reinforce data protection: the deletion of non-essential or expired information (Information Deletion), prevention of information leakage (Data Leakage Prevention) and the masking of sensitive information (Data Masking). It should be noted that the standard neither obliges nor limits the application of these measures to personal data: each organization is free to choose whether or not to apply these measures according to its risk assessment and to apply them to the categories of information that are appropriate to its context.
- The operational resilience component has also been strengthened by four measures: the integration of intelligence on threats related to information security (Threat Intelligence), monitoring of abnormal behavior on information systems to detect security incidents (Monitoring Activities), monitoring of physical access and intrusion detection (Physical Security Monitoring) and the integration of digital operational resilience for organizational business continuity (ICT Readiness for Business Continuity).
- A single measure dedicated to the security of cloud services (Information Security for use of Cloud Services) has been introduced, inviting organizations to define a process for managing these services from subscription to termination, integrating their chosen security measures.
- The three complementary measures strengthen IS protection at different levels:
- A measure related to the hardening and protection of configurations (Configuration Management)
- A measure related to the security of developments (Secure Coding)
- A measure aimed at defining a filtering policy for Internet access (Web Filtering)
Another major new feature (only present in ISO 27002) to facilitate the appropriation and use of the standard, is the implementation of a description of each measure, which presents five attributes that can contain one or more values among the following:
- Type of security measure: #Preventive, #Detective and #Corrective
- Information security properties: #Confidentiality, #Integrity, #Availability
- Cybersecurity concepts: #Identify, #Protect, #Detect, #Respond, #Recover
- Operational Capabilities: #Governance, #Asset_management, #Information_protection, #Human_resource_security, #Physical_security, #System_and_network_security, #Application_security, #Secure_configuration, #Identity_and_access_management, #Threat_and_vulnerability_management, #Continuity, #Supplier_relationships_security, #Legal_and_compliance, #Information_security_event_management, #Information_security_assurance
- Security domain: #Governance_and_Ecosystem, #Protection, #Defense, #Resilience
For example, the new Threat Intelligence metric covers the three security criteria #Confidentiality, #Integrity and #Availability.
These attributes facilitate analysis beyond a simple chapter-by-chapter approach, and thus provide real value: for example, the cybersecurity concepts correspond to the dimensions of the NIST (National Institute of Standards and Technology) Cybersecurity Framework (CSF), an internationally recognized standard widely used by organizations. The reconciliation of ISO 27002 and NIST CSF measures will thus be possible, meeting the constraints of many organizational functions (regulatory, audits, reporting, etc.).
The operational capabilities are the closest to the 14 chapters of the previous version of the standard: these operational capabilities can thus facilitate the organization of the IS Security Policy and the associated repository by limiting the impacts on a repository aligned with the previous version.
Overall, these attributes offer greater flexibility to organizations that can now build their security repository more freely according to their contexts and requirements.
Transitioning to the 2022 version
For organizations already certified to ISO 27001, the transition effort will be linked to changes in security measures, as the alterations to the ISO 27001 content require only a limited investment. However, the following actions will need to be undertaken:
- Update the ISMS Manual:
- Clarify interested parties’ expectations and which ones are addressed by the ISMS
- Update the ISMS improvement management process to include ISMS change management
- Insert a process summary diagram to show the interactions between processes
- Document the security objectives and implement indicators to monitor their achievements
- Ensure that performance and efficiency criteria are defined for each process
- Ensure that externally provided products and services are included in the ISMS (or integrated into it, as appropriate)
- Include in the management review the changes of interested parties’ expectations, by identifying those that are covered by the ISMS
In order to address the evolution of these measures, the next update of organizations’ information security risk assessments and risk treatment plans should measure the compliance of the ISMS with the new measures and organize and plan the implementation of any new measures selected. The statement of applicability will then have to be reorganized and updated to integrate the new measures.
The IS Security Policy (including the associated repositories: charters, directives, processes, procedures, standards…) will also have to evolve to consider the evolution of ISO 27001 Annex A. The use of attributes and Annex B of ISO 27002 will facilitate this change for all organizations.
In terms of timing, as ISO 27001:2022 was published in October 2022, organizations can now require ISO 27001:2022 certification. However, it is still possible to apply for ISO 27001:2013 certification until October 2023. From November 2023 onwards, any new certification will be based on the 2022 version of the standard.
For ISMS which are already certified ISO 27001, the transition period is 3 years maximum to switch to the 2022 version.
The specific case of organizations certified as Health Data Hosts (HDS)
Since April 1st, 2018, organizations based in France and hosting personal health data according to the conditions detailed in Article L1111-8 of the French Public Health Code must have a Health Data Host (HDS) certification, requiring as a prerequisite an ISO 27001 certification.
As the standard has not changed since it came into effect, the HDS certification requirements are still based on the 2013 version of the ISO 27001 standard. The call for comments made at the end of 2022 on the draft of the new HDS standard nevertheless integrates the new version of ISO 27001 (although the table of reference documents still points to ISO 27001:2013). The future HDS certification standard, which is expected to come into effect in April 2023, will therefore be based on the new version of the ISO 27001 standard.
It should be noted that the evolution of the HDS standard will also clarify some of the hard points of HDS certification mentioned in our previous articles, such as the scope of application of activity 5 “Administration and operation of the information system containing health data”.
Conclusion
These new versions of the ISO 27001 and ISO 27002 reference standards thus enable information security measures to be adapted to recent changes in the field, so that organizations can benefit from the most up-to-date arsenal for dealing with their information security risks.
While a growing number of regulations are based on these standards, such as the obligation of ISO 27001 certification for Health Data Hosts in France or for Essential Services Operators in Belgium, this new version allows organizations to reinforce their level of maturity without forcing them to make loss-making investments during the transition phase. These investments will be mainly focused on the consideration of new security measures relevant to the treatment of the organization’s security risks.


