The name might have changed but the goal remains the same: designing a cyber master plan has evolved considerably in the last 15 years. Large companies no longer have questions about the Framework and NIST has established itself as the market leader. One should take advantage of this “moment” to create aspiration, enthusiasm, real team spirit in the sector.
Defining a cybersecurity strategy in a large company
The name is not always the same: master plan, security model, action plan, roadmap but the basic idea is always to set a set of projects that will allow to converge towards a 3-4 year security target, shared and understandable by the top management. 15 years of master plans means 15 years of introductions based on accelerating the threat, tightening regulations, accompanying transformations; the reasons for establishing a cyber strategy are still globally the same. The method for designing a cyber master plan has evolved considerably.
10-15 years ago, life was simple.
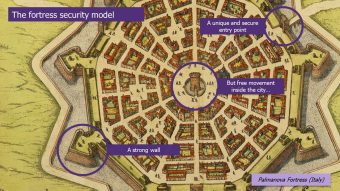
A master plan could be constructed in a few interviews with the ISSR and his team, “according to experts”. To provide a logic, consultants would base themselves on a pictorial model such as a fortified castle or an airport, which served as a pretext for setting up the fundamentals and explaining the choices. The attacks still seemed remote, the cyber was less dispersed than today and all the master plans were more or less the same. With a little hindsight, these cyber strategies above all had a great real role in raising awareness / training top management, who were gradually involved in the choices and discussions.
In 2021, the context has changed a lot. It is no longer enough to say “expert opinion”: some major accounts are now investing hundreds of millions of euros a year in cybersecurity, and executive committees are demanding more evidence of the effectiveness of the strategy deployed. All the more so since the “fundamentals” (patching, bastion, etc.) are now supplemented by an arsenal of measures, each more specific than the last, which raise questions about the relevance of a single strategy for a large company. It is clear, for example, that between a retail bank focused on the leakage of customer data and an investment bank fearing unavailability of certain trading channels, the priorities are different. The current crisis is certainly likely to reinforce this trend: strategies must now be much more finely tuned to the business lines.
A pragmatic and agile strategy, aligned with business priorities
The first months of work are always devoted to the method that will bring rigour and credibility with management and regulators. Very concretely, it is a question of defining the company’s Cyber Framework and a method enabling each entity to define its Target Profile (target to be reached on the Framework). Differentiated strategy for each entity.

Large companies no longer have questions about the Framework and NIST has established itself as the market leader. The 5 functions (identify, protect, detect…) speak volumes to management and above all its popularity favours the Benchmark. The frameworks chosen do not matter anymore, as long as they are based on a market reference. It should be noted that most companies do not hesitate to specify controls to make them more pragmatic: EDR, SOAR, AD security, anti-fraud; the Framework simply acts as a library of potential controls on which the company will base its strategy.
In large companies, the Group often imposes a first level of security for all, corresponding to the pursuit of fundamentals: SOC, bastion, patching, etc. Most systemic attacks still exploit these weaknesses, and the risk of inter-entity propagation must be managed in a cross-functional manner. This common target is quite similar from one company to another and is generally established on the basis of benchmarks provided by the consulting market. More challenging, each entity is then led to define its own target, according to its own stakes. Beware, the mapping and weighting mechanism between the Framework controls and the risk mapping can be complex. The key is often to get out of the cyber sector and work jointly with the Risk Department.
The must-haves of the moment: AD and IAM security

The figures resulting from the cyber strategies of major French companies are important: 10-20M of investment on average per year in the industrial sector, and up to 100-150M per year for Financial Services. Each strategy is different but recent feedback shows that budgets are fairly evenly balanced between 4 types of projects:
- Security foundations (patching, awareness, director security, etc.)
- Protection of sensitive environments (LPM, AD security, data protection, etc.)
- Zero-trust convergence (inventories, IAM, risk-based authentication, compliance, etc.)
- Cyber-resilience (detection, crisis management, reconstruction, business continuity, etc.).
A few years ago, the NCS and the LPM were definitely emerging as the top priority topics. Today, they are very much in competition with Active Directory security and AMI.
Cyber strategy is an essential tool for setting the course, federating actions, and involving management. However, establishing a multi-year master plan is a great opportunity to get teams on board around a common goal. Some security departments have grown from a few dozen people to several hundred or even thousands in the space of a few years, and many employees are currently looking for a meaning in their role. One should take advantage of this “moment” that is the creation of the strategy to create aspiration, enthusiasm, real team spirit in the sector. It is the ideal moment to multiply the work groups, involve as many employees as possible, adopt a transparent approach, have the top management challenge the teams; in short, turn this strategy construction into a sector event.


