The multiple perks of establishing a cyber budget management
For the past few years, companies have seen their cybersecurity budgets significantly increasing; according to the latest Gartner reports, they have increased by 51% since 2018. Chief Information Security Officers (CISOs) are now being asked to control cybersecurity costs and report to management as well as the regulator.
However, this increase in corporate IT security budgets has not always been followed by prudent budgetary management in the past. Learning from that, companies are now launching initiatives to monitor and collect cybersecurity cost data to better understand their evolution and make better informed strategic decisions, improving security while optimizing resource allocation. However, setting up budget management is a complex process that must meet specific objectives.
To what extent is the installation of a cybersecurity budget management system a key issue for the CISOs of large companies? – Our experience with our clients has proved that collecting cybersecurity budgets and implementing their management is often a valuable process and that reports resulting from such exercises are valuable governance tools. In this first section, we will examine the benefits of regular and industrialized cost collection and its true purposes.
Effectively driving cybersecurity budgeting
The final budget report is a strategically important governance tool key to achieving operational excellence and helps establish whether the company’s cybersecurity budget is being used effectively.
Budgetary steering is also an integral component of budget management and allows us to verify that the investments are aligned with the main risks the company is facing. For example, a company might find that its investments in a NIST benchmark topic are particularly low. In addition, if audits show that the level of security is insufficient in this area, then the conclusion is clear: it is necessary to devote more resources to this area. Therefore, budget reports are one of the elements that better facilitate quantitative investment decision making.
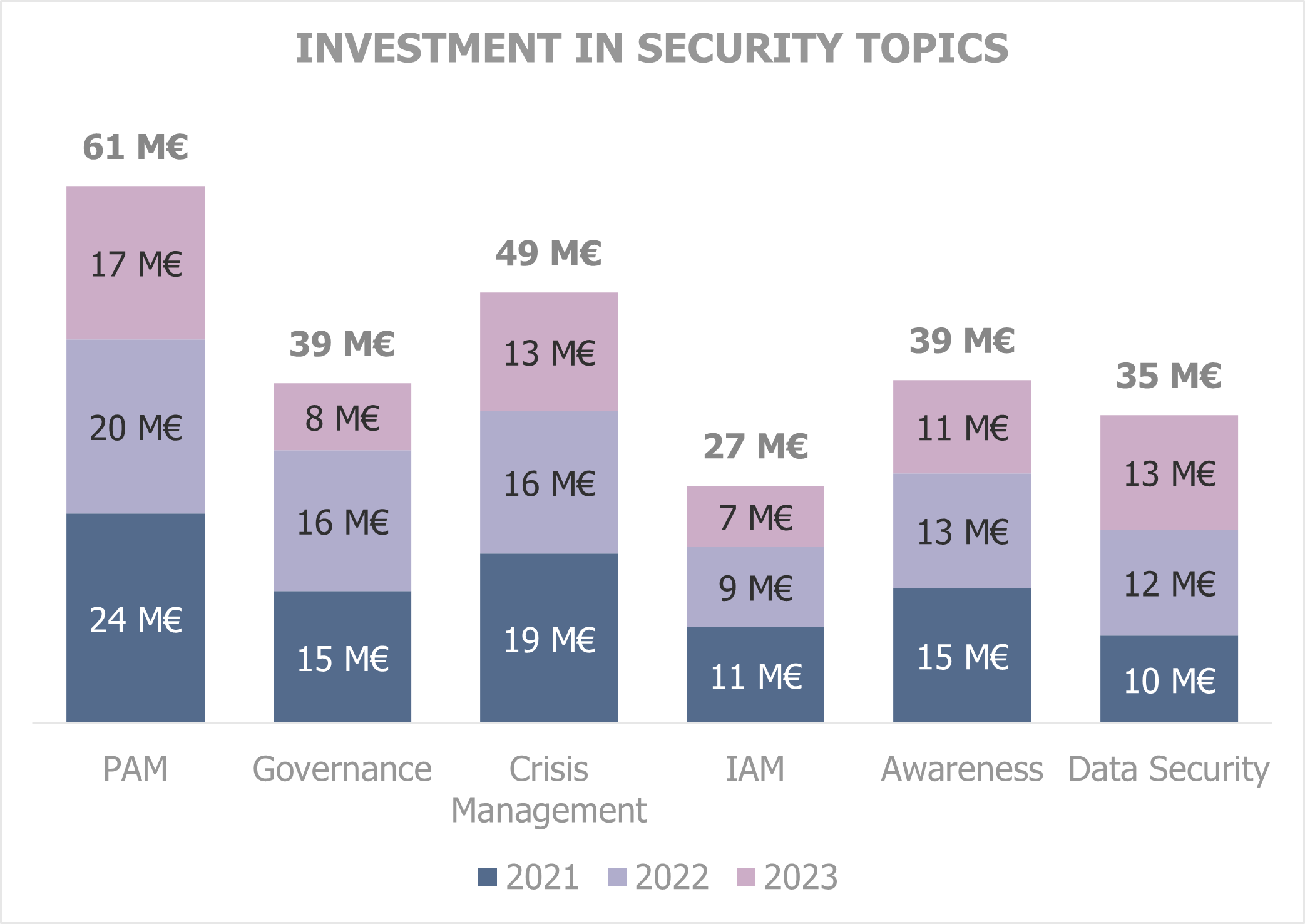
Example of a data visualization element from a budget report showing budgets by NIST activities. In this example, the chart highlights low investments in the “Identity and Access Management” area. If operational indicators show that the company’s maturity level is low, then it will be clear that the company has an incentive in making greater investments in this area.
In addition, the Group level data is very useful to the group members when they are shared across the peer set. It offers them an internal benchmark that enables them to view their position relative to their peers. CISOs of the various corporate entities will therefore be able to exchange information directly with each other, share best cybersecurity practices and identify the best operational models implemented by their peers.
Taking optimized decisions to achieve operation excellence
Budget management helps identify opportunities for optimization at entity or group level in order improve cybersecurity effectiveness.
The budget report is an asset for bettering the management of human resources dedicated to cybersecurity. For example, it makes it possible to estimate the ratio of internal labour resources to external resources and to make the necessary adjustments i.e., after reading the budget report, management could launch a labour internalization initiative if it realizes that the proportion of external staff is too high. It can also modify the geographical distribution of human resources in order to better meet the security requirements of corporate entities in different countries and to gauge the onshore/offshore distribution.
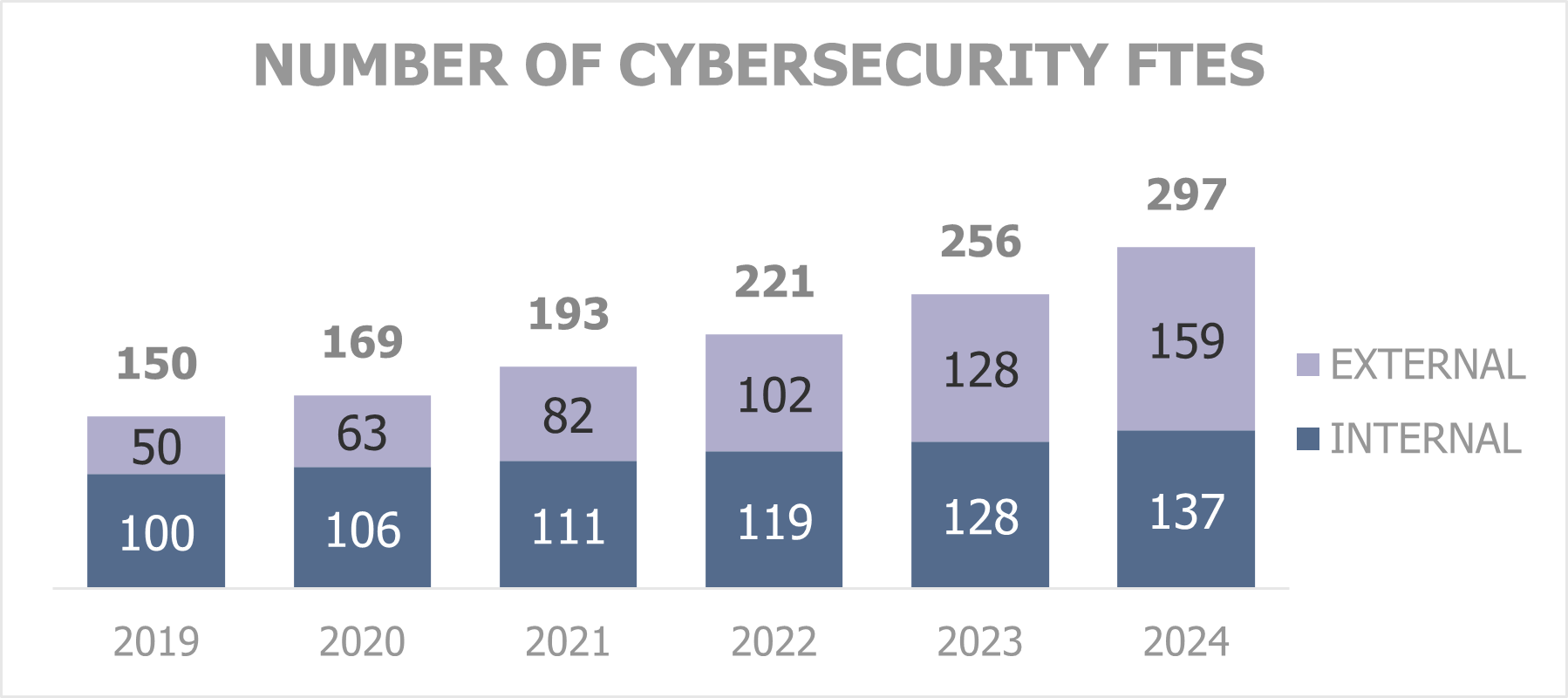
Example of a data visualization element from a budget report showing the number of cybersecurity employees. In this example, the graph reveals a risk that the share of interns is too low to keep the expertise in-house. It might therefore be worthwhile to launch an insourcing plan.
Consolidating the cybersecurity budget provides an opportunity to make savings, automate or mutualize activities. Budget management can then result in decisions to consolidate contracts as well as rationalize and/or automate processes in order to keep control of cybersecurity costs.
Due diligence and externally conducted audit compliance
When a company’s cyber budget is under scrutiny by regulatory authorities, it will be necessary to have a dedicated collection process to be able to provide a reliable breakdown of IT security costs. Properly conducted budget collection will allow the creation of analytical data and deliverables that will serve as the basis for accurate and informed responses. For example, the European Central Bank has asked some banking organizations to present details of the human resources dedicated to IT security to monitor the preparedness of European banks for cybersecurity risks.
Furthermore, a synthetic view facilitates communication with certainty on the state of budgets and expenses dedicated to security to any interested third party. For example, the American bank JP Morgan Chase explained in its April 2019 letter to shareholders that cybersecurity was one of its major concerns. The bank announced spending more than $600 million a year on IT security and employs 3,000 people in the area.
Finally, knowing one’s budget is also important when purchasing cyber insurance, to prove the resources invested into cybersecurity. Furthermore, during a merger and acquisition, the resources invested in cybersecurity are often considered in the valuation of a corporate entity.
Therefore, it seems particularly useful for large companies to have a process for collecting cybersecurity costs as it allows decision-makers to be aware of the amounts spent by the group on information systems security and to steer the strategy. However, the construction of a relevant budgetary report depends on the prior implementation of an extensive, methodical, and standardized data collection process. The next part of this series will detail the framing and implementation of a budget steering process.
Sources
[1] « Gartner Forecasts Worldwide Information Security Spending to Exceed $124 Billion in 2019 », august 2018, https://www.gartner.com/en/newsroom/press-releases/2018-08-15-gartner-forecasts-worldwide-information-security-spending-to-exceed-124-billion-in-2019
[1] « Cybersecurity spending trends for 2022: Investing in the future », december 2021, https://www.csoonline.com/article/3645091/cybersecurity-spending-trends-for-2022-investing-in-the-future.html
[2] « Cybersecurity for the financial sector », https://www.ecb.europa.eu/paym/pol/shared/pdf/qa_cybersecurity.pdf
[2] « Face au risque de cyberattaque, la BCE demande aux banques d’être prêtes», february 2022, https://www.latribune.fr/entreprises-finance/banques-finance/banque/face-au-risque-de-cyberattaque-la-bce-demande-aux-banques-d-etre-pretes-903841.html
[3] « CEO Letter to shareholders », august 2019, https://www.jpmorganchase.com/content/dam/jpmc/jpmorgan-chase-and-co/investor-relations/documents/ceo-letter-to-shareholders-2018.pdf


